Shaadi.com

Price : Free
Category : Social
Platform : iOS and Android
Updated : Mar. 9, 2015 (Android), Mar. 10 2015 (iOS)
Version : 4.2.2 (Android), 4.2.1 (iOS)
Size : 8.28 MB (Android), 17.7 MB (iOS)
Language : English
Vendor : People Interactive (I) Pvt. Ltd.
Background:
Shaadi.com is the world's largest matrimonial website, active since 1995. This matrimonial site permits individuals to post their profiles and responses including horoscope, caste, language and religion. Shaadi.com provides applications designed for the two main mobile platforms – iOS and Android.
Application Chart (information retrieved from Appannie & xyo.net):
|
|
Android
|
iOS
|
|
Global Ranking
|
15
|
92
|
|
Category Ranking
|
12 (Social)
|
24 (Social networking)
|
|
Total number of Downloads
|
~1 million
|
~0.3 million
|
|
Rating
|
3.9/5
|
2.7/5
|
A new user is required to register by providing an email address and a password, along with basic personal details. After registering the account, the user can surf profiles created by others. The application also provides a chat facility.
Vulnerability - Cleartext username/password
 |
| Login screen |
The current version of the Shaadi.com application has a serious security flaw. It has been verified that both the iOS and Android versions of the application transmit the username and password via HTTP in cleartext. This flaw allows an attacker to capture the credentials sent by a user to the application server and thus compromise the user's account, which may lead to compromise of user's personal data. The service also provides premium accounts to paid customers.
The application was tested on both the Android and iOS platforms. The vulnerability has been confirmed on Android (v4.2.2 - latest version, updated on Mar. 9, 2015) and iOS (v4.2.1 - latest version, updated on Mar. 10, 2015).
Vulnerability in iOS version
When a user tries to register for an account on the Shaadi.com application, an HTTP request is generated. In the request the userid, password and mobile number of the user is sent in cleartext as seen below:
Account Registration
[-]http://www.shaadi.com/registration/user/?regmode=app&OS=native-iphone
Method: POST
Host: www.shaadi.com
User-Agent: native-iphone|4.1.0
Request Body: form_referral_url=&form_url=http%3A%2F%2Fwww.shaadi.com%2Fregistration%2Fuser%3Fregmode%3Dapp%26appver%3D4.1.0%26os%3Dnative-iphone%26deviceid%3D---%257C---&form_name=MOB_DR_SEO_REG1&frompage=From+Reg+Page&go=&olmt_home_regpage=&hid_year=&oscode=2&email=fnzscalerlnzscaler%40gmail.com&password1=p%40ssword123&postedby=Self&first_name=fnzscaler&last_name=lnzscaler&gender=Male&day=01&month=01&year=1994&community=No+Religion&mother_tongue=Konkani&countryofresidence=USA&contact_tel_number=Landline+No.
Similarly, when an already existing user tries to login to his account by providing his username and password, these credentials are also being sent in cleartext. Below is the traffic capture when a user tries to login to an existing account:
Login
[-]http://www.shaadi.com/native-apps2/user/[email protected]&password=p@ssword123&appver=4.1.0&os=native-iphone&deviceid=---%7C---
Method: GET
Host: www.shaadi.com
User-Agent: Shaadi/462 CFNetwork/711.1.16 Darwin/14.0.0
Server Response: {"status":"200","data":{"sid":"7B16D793AFF0443EE1320F85EFD1B4C51425446439","abc":"0CE03847FB4B0C981EB552E34E1C96B61425446522|ZSH82845405|","premium":false,"gender":"Male","age":"21","memberstatus":"ToBeScreened","memberlogin":"ZSH82845405","photograph_status":"photo_request","update_available":false,"has_notification":"N","has_chat_notification":"N","content_settings":{"eoi":"Y","acc":"Y","msg":"Y","nf1":"N","dr":"Y"},"display_name":"SH82845405","username":"SH82845405","email":"[email protected]","use_connect":1,"upgrade_message":"UPGRADE TO PREMIUM","support_telephone":"1860-200-3456","payment_telephone":"1860-200-3456"},"expdt":"20150403002202","banner_images":{"banner_search_results":{"title":"Become a Premium Member & connect directly via","subtitle":"EMAIL, CHAT & PHONE","details":"","version":"","img":"http:\/\/img.shaadi.com\/community\/images\/app\/banner_search_results_male_free_high.png"},"banner_accepted":{"title":"Upgrade to Premium & start chatting with your Accepted Members!","subtitle":"","details":"","version":"","img":"http:\/\/img.shaadi.com\/community\/images\/app\/banner_accepted_free.png"},"banner_inbox_single":{"title":"1 Member like your profile!","subtitle":"Become a Premium member & write back to them today","details":"","version":"","img":"http:\/\/img.shaadi.com\/community\/images\/app\/banner_inbox_single_male_free_high.png"},"banner_inbox_multiple":{"title":"#count# Members like your profile!","subtitle":"Become a Premium member & write back to them today","details":"","version":"","img":"http:\/\/img.shaadi.com\/community\/images\/app\/banner_inbox_multiple_male_free_high.png"}}}
Vulnerability in Android version
Account Registration
[-]http://www.shaadi.com/registration/user/?regmode=app&OS=native-android
Method: POST
Host: www.shaadi.com
User-Agent: Mozilla/5.0 (Linux; Android 5.0.2; Nexus 7 Build/LRX22G) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/37.0.0.0 Safari/537.36
Request Body: form_referral_url=&form_url=http%3A%2F%2Fwww.shaadi.com%2Fregistration%2Fuser%3Fregmode%3Dapp%26os%3Dnative-android%26deviceid%3D--%7C--%26appver%3D4.1.3&form_name=MOB_DR_SEO_REG1&frompage=From+Reg+Page&go=&olmt_home_regpage=&hid_year=&oscode=1&email=vulapps%40zscaler.com&password1=p%40ssword1234&postedby=Self&first_name=fnzscaler&last_name=lnzscaler&gender=Male&day=10&month=10&year=1985&community=Spiritual+-+not+religious&mother_tongue=Marathi&countryofresidence=USA&contact_tel_number=Landline+No.
Login
[-]http://www.shaadi.com/registration/user/login-submit
Method: POST
Host: www.shaadi.com
User-Agent: Mozilla/5.0 (Linux; Android 5.0.2; Nexus 7 Build/LRX22G) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/37.0.0.0 Safari/537.36
Request Body: go=&email=vulapps%40zscaler.com&password=p%40ssword123&autologin=0&autologin=Y
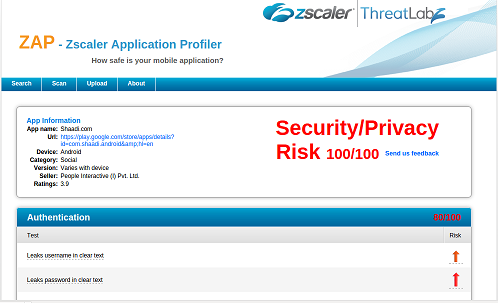 |
| ZAP in action - Android |
 |
| ZAP in action - iOS |
The list of mobile applications in Google Play and the iTunes App Store that send out sensitive information in cleartext continues to grow. Therefore, it is extremely important to keep separate passwords for different applications and never use the password of your financial applications anywhere else.
Credit: Lakshmi Devi.




