A scary proposition for organizations and consumers alike is the possibility of being hit by a ransomware campaign. Ransomware threats have been known to spread through targeted spam campaigns, compromised WordPress sites, or Exploit Kits. The purpose of this attack is to encrypt all files on the victim's system and extort the user for money to gain access to their sensitive files. Attackers leverage anonymizer networks such as TOR to cover their tracks when accepting any payment from their victims.
In this blog, we cover a campaign involving CryptoWall 3.0 ransomware. The attack campaign that we are monitoring involves malicious executable files disguised as JPEG image files. The URL format for these downloads adheres to the following patterns:
The malware performs a POST request to the following domains relaying the data from the victim's system to one of the following Command & Control (C&C) servers:
These beaconing activities take place for the duration of the compromise to C&C servers seen around the world.
In this blog, we cover a campaign involving CryptoWall 3.0 ransomware. The attack campaign that we are monitoring involves malicious executable files disguised as JPEG image files. The URL format for these downloads adheres to the following patterns:
http://[domainname]/images/[one|two].jpg
Nameserver used: ns[1-4].dervoilrtd.org
Nameserver used: ns[1-4].dervoilrtd.org
Sample URLs serving CryptoWall 3.0
- dorttlokolrt[.]com/images/one[.]jpg
- dorttlokolrt[.]com/images/two[.]jpg
- indsertgamert[.]org/images/one[.]jpg
- indsertgamert[.]org/images/two[.]jpg
- davis1[.]ru/images/one[.]jpg
- davis1[.]ru/images/two[.]jpg
- downs1[.]ru/images/one[.]jpg
- downs1[.]ru/images/two[.]jpg
- ellison1[.]ru/images/one[.]jpg
- ellison1[.]ru/images/two[.]jpg
- manning1[.]ru/images/one[.]jpg
- manning1[.]ru/images/two[.]jpg
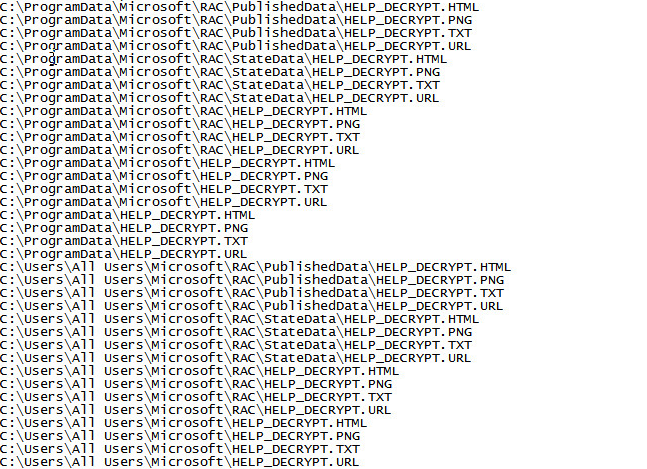
The downloaded file deletes the original copy of itself and begins encrypting all the victim's files using an asymmetric encryption method. For each file it encrypts, it leaves behind a HELP_DECRYPT.[PNG|HTML|TXT|URL] file to instruct the victim on how to recover their files.
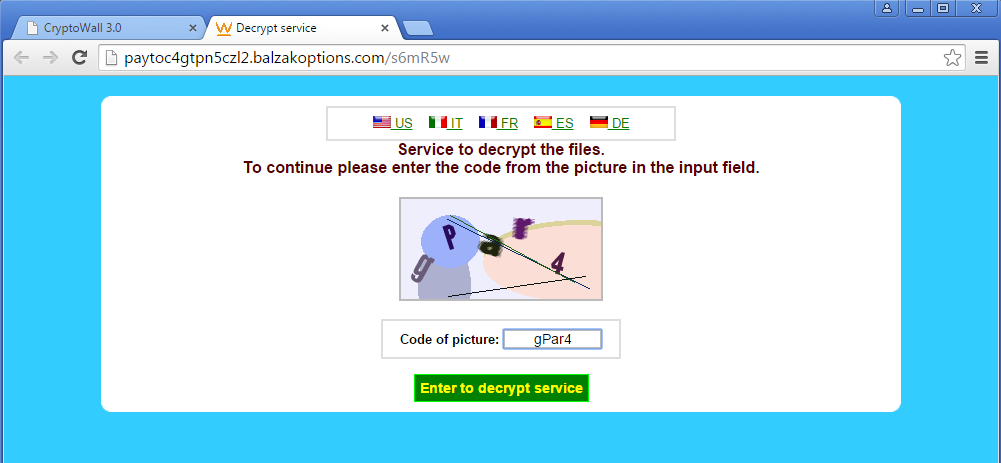
Following a successful infection cycle, the end-user will be shown a pop-up of the HELP_DECRYPT file to make sure that the victim is fully aware of the attack on their system. The instructions contain a TOR link to recover their now encrypted sensitive files. Following the links from the HELP_DECRYPT file leads to a Decryption Service page performing a CAPTCHA check to ensure it's a human on the other end.
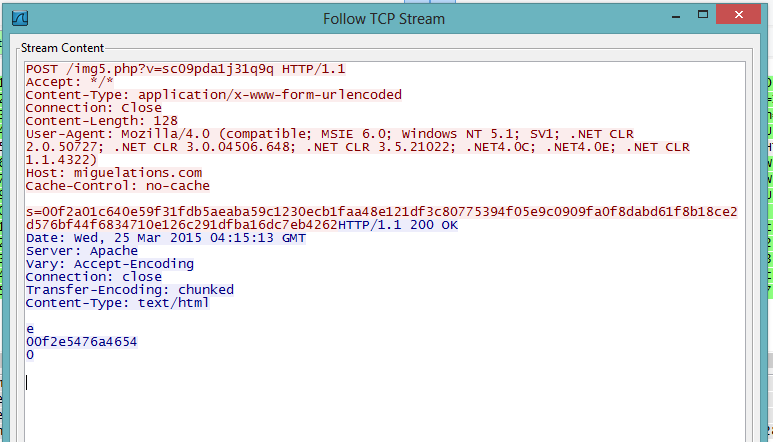
The malware performs a POST request to the following domains relaying the data from the victim's system to one of the following Command & Control (C&C) servers:
- alkhatip[.]com
- aseanian[.]com
- bijouxbjx[.]com
- buildtrue[.]com
- corporatemonks[.]com
- eturedesigns[.]com
- futong8[.]com
- geiliyou[.]com
- houseofstarz[.]com
- hscompany[.]net
- ineshworld[.]com
- iuliasalaria[.]org
- judora-ng[.]com
- leutezentrum[.]com
- miguelations[.]com
- ocarma[.]org
- ocvitcamap[.]com
- ouarzazateonline[.]com
- ruanlianjie[.]net
- sapacmold[.]com
- spark-leds[.]com
- trillyo[.]com
- ubikate[.]mx
- weapex[.]com
- www[.]ebouw[.]nl
- www[.]getserved[.]nl
- www[.]multiposting[.]nl
- www[.]ubikate[.]mx
 |
| /img[/d].php?[a-z]=[string] |
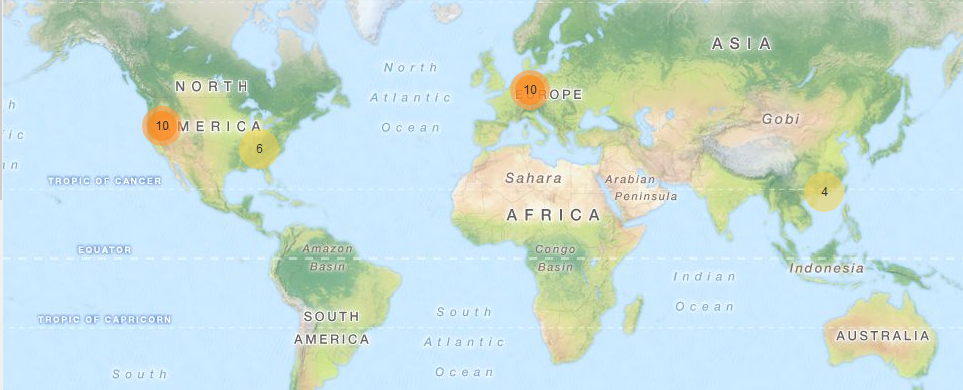 |
| Unique C&C locations |
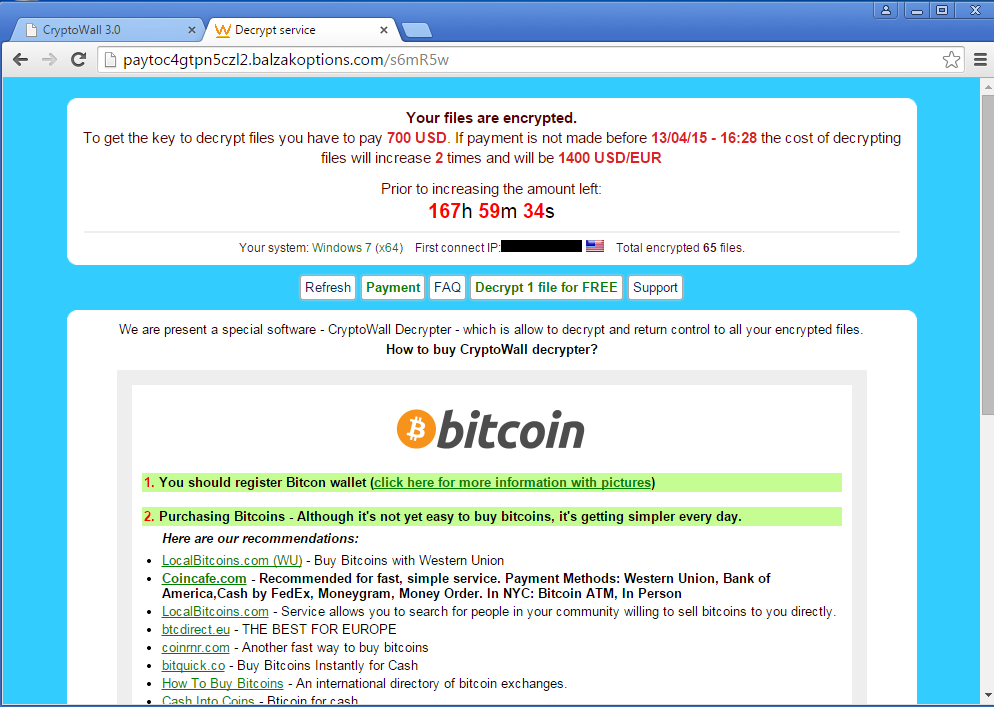
Once infected, CryptoWall 3.0 puts the victim on an extortion countdown. The ransom amount doubles at each threshold set by the attacker. The attacker's preferred currency is in Bitcoin, but the victim is offered numerous methods of payment.
Ransomware continues to be a highly profitable attack vector. This particular campaign spreads through numerous methods, but the resulting payload is consistent whether the victim is attacked through spam, a compromised website or via an exploit kit. While security vendors try their best to ensure coverage against this malware family, the most effective defense for the end user is to adopt a preventative approach of taking regular backups of sensitive files.