Introduction
We have covered Dridex Banking Trojan being delivered via various campaigns involving Office documents with malicious VBA macros in the past. However, over the past two weeks we are seeing these malicious VBA macros leveraged to drop Kasidet backdoor in addition to Dridex on the infected systems. These malicious Office documents are being spread as an attachment using spear phishing emails as described here. The malicious macro inside the Office document is obfuscated as shown in the code snapshot below -
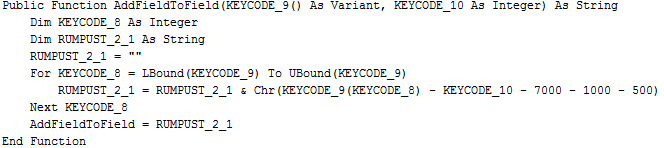 |
| Macro code |
The macro downloads malware payload from the hardcoded URL. We have seen following URLs used in different document payloads that we captured for this campaign:
- armandosofsalem[.]com/l9k7hg4/b4387kfd[.]exe
- trinity.ad-ventures[.]es/l9k7hg4/b4387kfd[.]exe
- 188.226.152[.]172/l9k7hg4/b4387kfd[.]exe
In this blog, we will provide a detailed analysis for the Kasidet variant that we spotted in this campaign.
Kasidet Analysis
Installation:
Kasidet installs itself into %APPDATA% folder. It creates a new folder there with the name "Y1FeZFVYXllb", this string is hardcoded in the malware. The same string is used as mutex name and in creating a Registry key for ensuring persistence upon system reboot.
AntiVM Check:
Kasidet tries to detect analysis systems during execution through following checks.
Checking Dubugger through "IsDebuggerPresent" and "CheckRemoteDebuggerPresent" Windows APIs. It also checks for the following popular sandbox related strings:
User Name: "MALTEST", "TEQUILABOOMBOOM", "SANDBOX", "VIRUS", "MALWARE"
File Name: "SAMPLE", "VIRUS", "SANDBOX"
It tries to detect wine software by checking if kernel32.dll is exporting "wine_get_unix_file_name" function or not. It detects Vmware, VirtualBox, QEMU and Bochs by checking for following registry entries:
| Vmware | "SOFTWARE\\VMware, Inc.\\VMware Tools" | |
| "HARDWARE\DEVICEMAP\Scsi\Scsi Port\Scsi Bus\Target Id\Logical Unit Id", "Identifier" , Vmware" | ||
| "HARDWARE\DEVICEMAP\Scsi\Scsi Port\Scsi Bus\Target Id\Logical Unit Id", "Identifier" , "VBOX" | ||
| VirtualBox | "HARDWARE\\Description\\System", "SystemBiosVersion" , "VBOX" SOFTWARE\\Oracle\\VirtualBox Guest Additions" "HARDWARE\\Description\\System", "VideoBiosVersion" , "VIRTUALBOX" | |
| QEMU | "HARDWARE\DEVICEMAP\Scsi\Scsi Port \Scsi Bus \Target Id \Logical Unit Id ", "Identifier" , "QEMU" "HARDWARE\\Description\\System" , "SystemBiosVersion" , "QEMU" | |
| Bochs | "HARDWARE\\Description\\System" , "SystemBiosVersion" , "BOCHS” | |
Information Stealing capabilities:
Kasidet uses following two methods for stealing information from the victim's machine:
1. Memory Scraping – This allows Kasidet to steal credit card data from the memory of Point-Of-Sale (POS) systems. It scans the memory of all the running processes except the operating system processes listed below:
System
smss.exe
csrss.exe
winlogon.exe
lsass.exe
spoolsv.exe
devenv.exe
The stolen information is relayed back to the attacker using following URI format –
d=1&id=
2. Browser Hooking – This allows Kasidet to steal data from Web browsers. It can inject code into FireFox, Chrome, and Internet Explorer (IE). Browser names are not saved in plain text and instead this variant uses the same hash function as used by Carberp malware to encrypt the browser names. The following APIs are hooked in the web browser for stealing sensitive data:
| Browser | API |
| FireFox | PR_Write |
| Chrome | WSASend |
| IE | HttpSendRequestW , InternetWriteFile |
The stolen information is relayed back to the attacker using following URI format –
ff=1&id=
The information stealing feature of this Kasidet variant were deactivated if the system locale or GeoUserID corresponds to Russia.
Network communication:
Kasidet contains a hardcoded list of Command & Control (C&C) server locations. It uses CryptStringToBinary API call to decrypt the embedded C&C URLs as seen below:
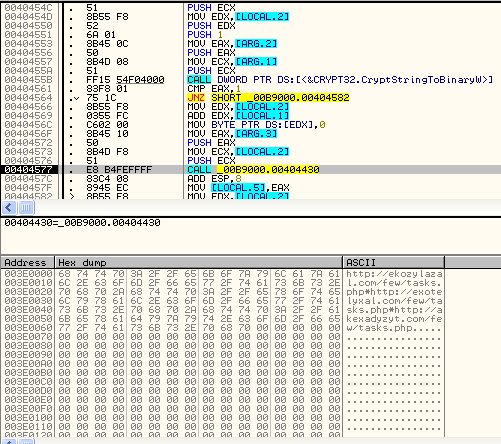 |
| Kasidet C&C list |
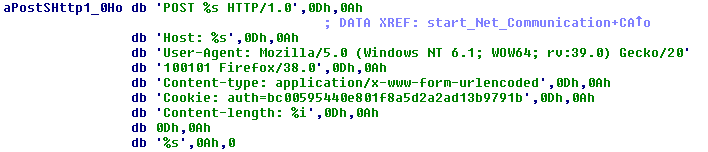 |
| Kasidet Hardcoded HTTP fields |
C&C Server will not return required data if HTTP header fields are different. The server sends a fake 404 response code and html data stating that page is not found but the C&C commands will be hidden in the response HTML comment tag as seen below:
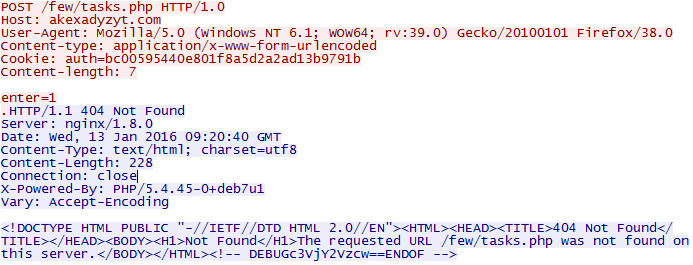 | |
|
Kasidet will request for additional commands from the C&C server with the following POST request:
 |
| Kasidet request for additional commands |
| Variable | Descriptions |
| cmd | Command. It is hardcoded in the malware payload as '1'. |
| id | MachineGuid value fetched from Software\Microsoft\Cryptography registry key |
| name | System Name |
| os | Operating system version |
| p | Process elevation status |
| av | Antivirus installed on the infected system |
| v | Version of the bot. It is hardcoded in the malware. Current version that we analysed is 4.4 |
| w | Flag that indicates whether the system locale and UserGeoID is Russia |
Like browser names, all the command strings are also encrypted using a hash function. Below are some of the important commands:
| Command Hash | Description |
| 0x0E587A65 (rate | It is used in sleep function |
| 0x89127D3 | DDOS using HTTP protocol |
| 0x0B37A84B6 | Start keylogging and screen capture threads |
| 0x89068E8h | Download and execute additional component. This file can be DLL, EXE or VBS. |
| 0x4A9981B7 | Search for given process name in current running processes in the system |
| 0x8D26744 | Find given file in system and upload to the server |
| 0CAB1E64A | Drop setting.bin file, change firewall settings to download and execute plugin component |
| 0x10E6C4 | Execute given command using windows cmd.exe |
Conclusion
Malicious Office document file is a popular vector for malware authors to deliver their payloads. Dridex authors have leveraged this technique for over a year and it was interesting to see the same campaign and URLs being leveraged to deliver Kasidet payloads. While this does not establish any links between the two malware family authors, it reaffirms the fact that a lot of the underlying infrastructure and delivery mechanisms are often shared by these cyber criminals.
ThreatLabZ is actively monitoring this threat and ensuring signature coverage for Zscaler customers.
Analysis by - Abhay Yadav, Avinash Kumar and Nirmal Singh






