Whether you call it SSL, TLS, or HTTPS, you’re talking about what has become the single greatest means for harboring the transmission of malware: encryption. Zscaler operates a globally distributed cloud security platform, and we have found that more than half of all internet traffic sent through our cloud is encrypted. Some of that traffic still uses the older Secure Sockets Layer (SSL) protocol, while a higher percentage uses the newer Transport Layer Security (TLS) protocol. Sessions for both are invoked with the “HTTPS” website address prefix in your browser. Because Zscaler examines the contents of all encrypted traffic to detect malicious payloads, we have discovered that encryption is frequently used to mask malware and evade security detection tools. In this security brief, we’ll present some of the statistics and trends that our researchers have compiled regarding major malware families, and we’ll describe actions you can take to protect your organization against these threats.
The Rising Use of Encryption for Malware
Encryption has always been used to protect sensitive data transmitted through the internet, but its use has increased to the point where most traffic today is encrypted. Google reported that by the end of 2016, 80 percent of traffic sent across its properties was encrypted.
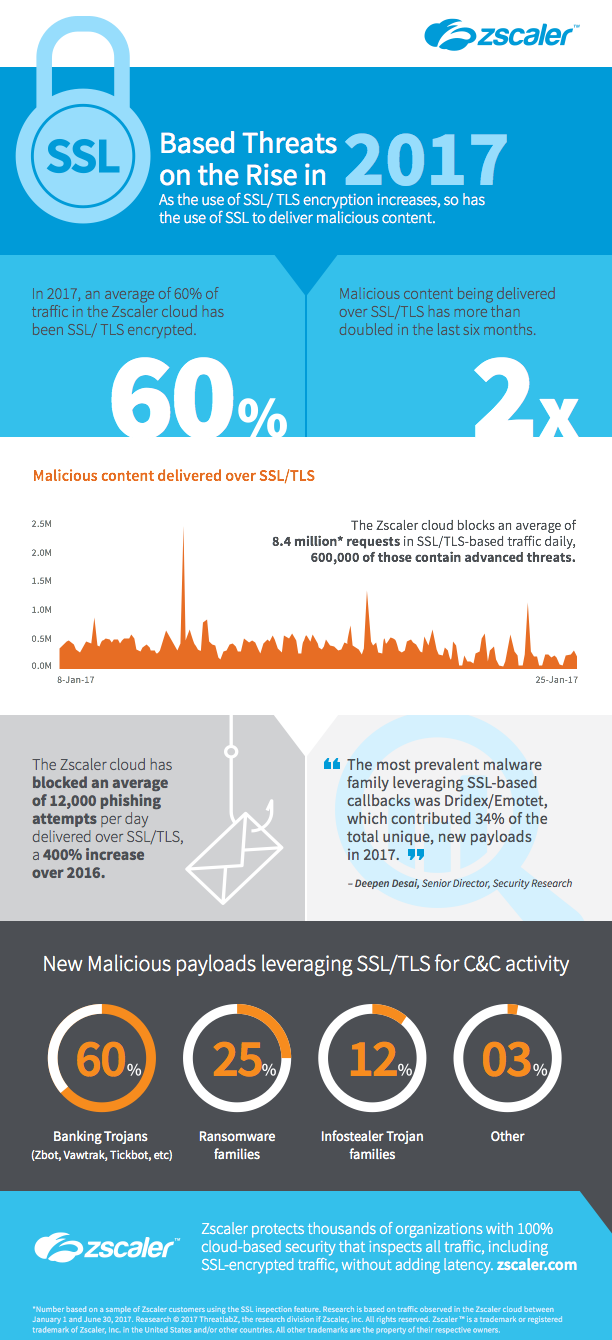
While encryption is effective for protecting data, it also is effective for hiding malicious payloads. During 2017, an average of 60 percent of the threats detected in the Zscaler global cloud had been encrypted with SSL/TLS, and we’ve been blocking an average of 600,000 encrypted malicious activities every day. In the last six months, we’ve observed that encrypted malicious content has more than doubled.
Current Trends in Encrypted Malware
1. Attack types vary
Among the 600,000 encrypted incidents blocked each day by the Zscaler cloud, we have seen a variety of attack types hidden within SSL/TLS packets. They primarily include:
- Exploit kits
- Malware
- Adware
- Malware callbacks
2. Web exploits abuse public trust
Cybercriminals continue abusing public trust to accomplish their goals, which are primarily profit driven. For example, the attack type using SSL/TLS-enabled advertising networks injects malicious scripts into legitimate websites. When users visits a legitimate website that serves the infected advertisements, they unwittingly fall prey to malware, which can steal their personal information or corrupt their data.
Cybercriminals are also abusing free SSL/TLS providers. The free certificates enable HTTPS support on the attackers’ malicious domains, allowing them to bypass SSL/TLS integrity checks in web browsers. This configuration also creates problems for organizations that are unable to monitor SSL traffic, as they must rely on less effective techniques like IP and domain blocking in an attempt to identify and block threats delivered from such domains.
Zscaler is currently detecting an average of 10,000 web exploits delivered over SSL/TLS each month.
3. Phishing continues to evade network perimeter tools
Hackers are posting phishing pages on legitimate domains that they have compromised. Many of these legitimate sites support SSL/TLS, and there are very few network security solutions that can support inspection of encrypted packets at scale. During 2017, Zscaler has blocked an average of 12,000 phishing attempts per day delivered over SSL/TLS, an increase of 400 percent over 2016.
4. Malware families are using SSL/TLS for callback activity
The use of encryption has increased the sophistication of callback design. It used to be rare to see SSL/TLS used for command-and-control (C&C) activity. But since encryption is now ubiquitous, attackers have decided to join the party and hide inside encrypted packets. Anonymity services like TOR also help to hide C&C servers. Botnets are also using SSL/TLS more frequently, including the use of self-signed certificates along with the names and corresponding information of real companies. The prevalence of this scheme is on the rise. During 2017, Zscaler has blocked an average of more than 5,000 C&C attempts over SSL/TLS per day.
5. Distribution of malware families using encryption for C&C
C&C communication is a critical function for malware, and cybercriminals are relying on encryption more than ever to hide the implementation of an attack. Figure 1 shows the distribution of malware families using encryption for C&C activity, based on unique, new payloads that have been seen in Zscaler Cloud Sandbox during 2017.






