Overview
The majority of Internet traffic is now encrypted. With the advent of free SSL providers like Let’s Encrypt, the move to encryption has become easy and free. On any given day in the Zscaler cloud, more than half of the traffic that is inspected uses SSL. It is no surprise, then, that malicious actors have also been using the SSL protocol in their activities over the last several years. The increasing use of SSL creates problems for organizations that are unable to monitor SSL traffic, as they must rely on less-effective techniques like IP and domain blocking in an attempt to identify and block threats.
In this report, we will outline trends we have seen in the use of SSL in the malware lifecycle and in adware distribution, based on a review of traffic on the Zscaler cloud from August 2016 through January 2017. What follows is a graphic illustrating our findings, and an analysis of recent activities.
Malicious SSL Activity
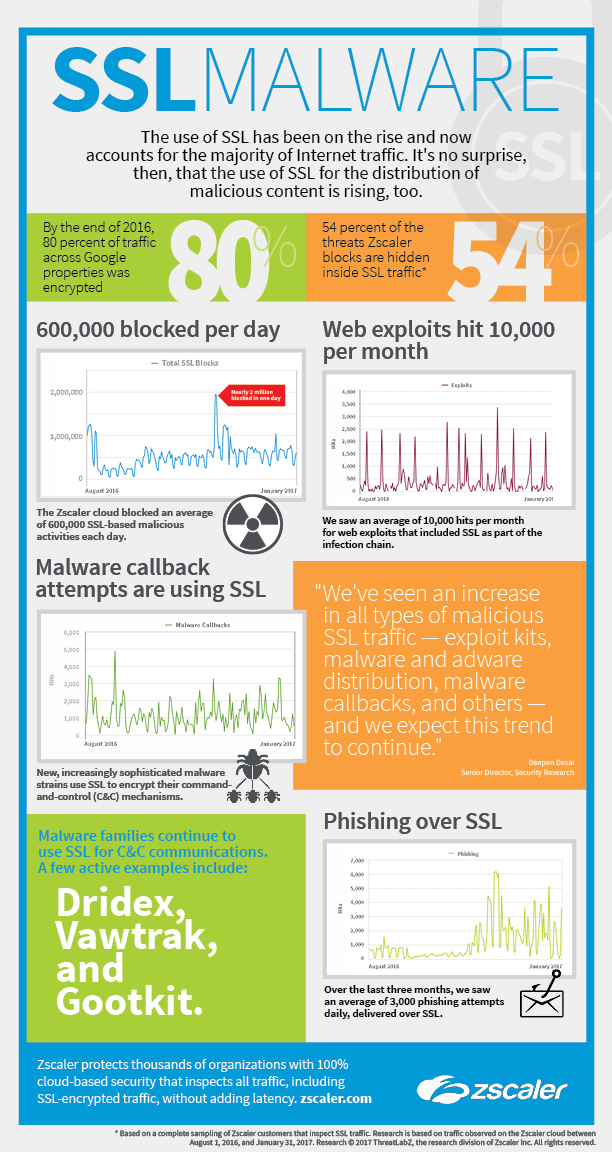
During the six-month period, the ThreatLabZ research team observed that the Zscaler cloud blocked an average 600,000 malicious activities each day that used SSL, including exploit kit traffic, malware and adware distribution, malware callbacks, and other malicious traffic.
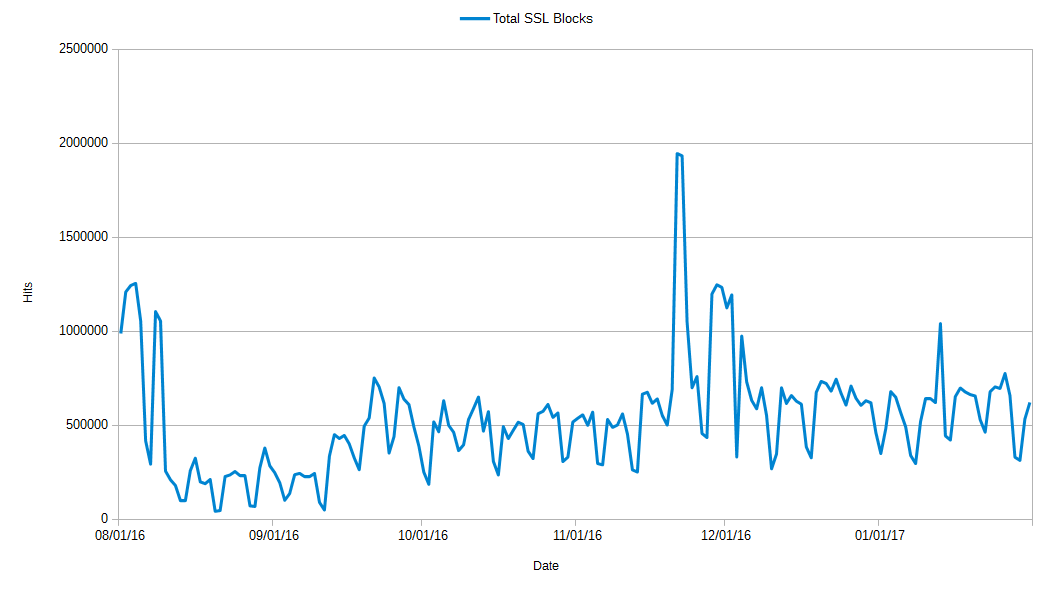
Figure 1. Total SSL blocks, August 2016 – January 2017
In our cloud, we observed an overall increase in malicious SSL traffic in nearly all categories — a trend we expect to continue — with periodic spikes, such as those in early August and late November, when SSL malware blocks reached nearly two million a day.
Browser Exploits and Payload Delivery
Exploit kit (EK) authors are more frequently including SSL in the infection chain at some point. Previous malvertising campaigns have been observed in which EKs took advantage of SSL-enabled advertising networks to inject malicious scripts into legitimate webpages. EK authors may also abuse services that provide free SSL certificates to add HTTPS support to their maliciously controlled domains. This maneuver enables them to bypass the SSL integrity checks built into modern web browsers.
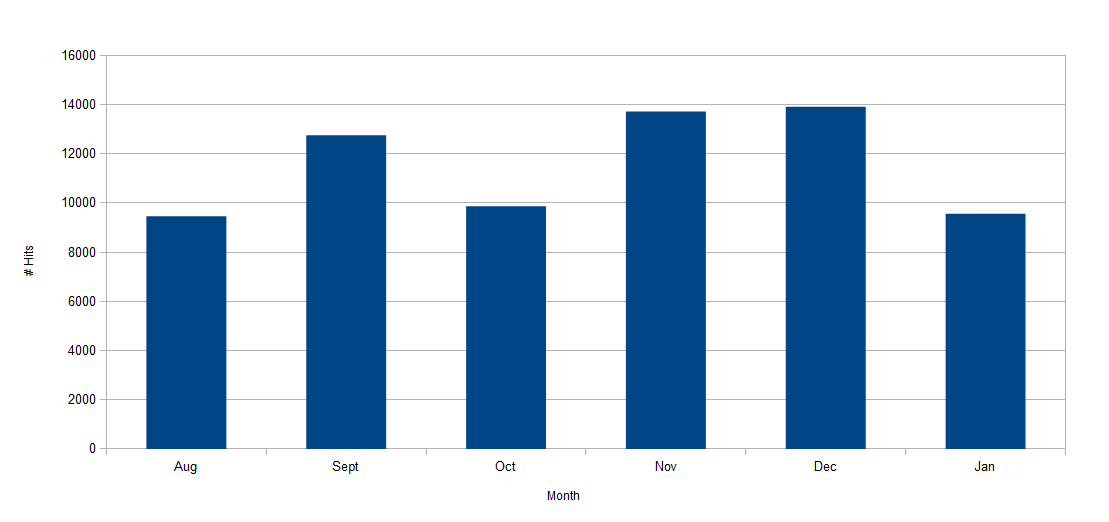
Figure 2. SSL web exploit monthly total hits, August 2016 – January 2017
Figure 3. SSL web exploit blocks, August 2016 – January 2017
During the observation period, we saw an average of 10,000 hits per month for web exploits that included SSL as part of the infection chain.
Phishing
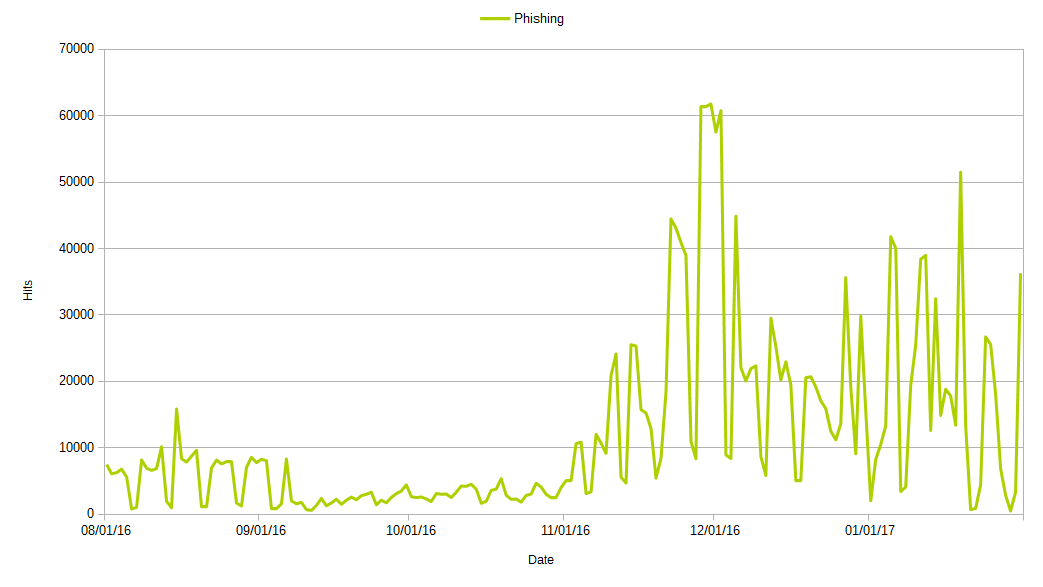
Figure 4. Phishing blocks, August 2016 – January 2017
Phishing campaigns have been increasingly using SSL in their attacks. Many phishing attacks involve hosting the phishing page on a legitimate domain that has been compromised. Since the number of legitimate sites that support SSL is constantly increasing, so are the number of SSL-enabled phishing attacks. This rise presents a significant threat, because organizations, in an attempt to thwart ransomware and other phishing schemes, have implemented security hardware solutions to detect and block phishing, but few of them support SSL inspection.
Malware Families That Use SSL
Several years ago, it was rare to see malware using SSL to encrypt command-and-control (C&C) mechanisms. As malware design has become more sophisticated, and with the near ubiquity of SSL on the Internet, it made sense for malware authors to begin using SSL to hide their activities. Some malware families have gone further, using anonymity services such as Tor to hide the location of their C&C servers, connecting to (otherwise legitimate) HTTP Tor gateways via SSL.
Botnets typically use self-signed SSL certificates, frequently using the names and information of real companies to try to appear legitimate. The SSL Blacklist (https://sslbl.abuse.ch/) is a project that tracks the SSL certificates used by malware authors.
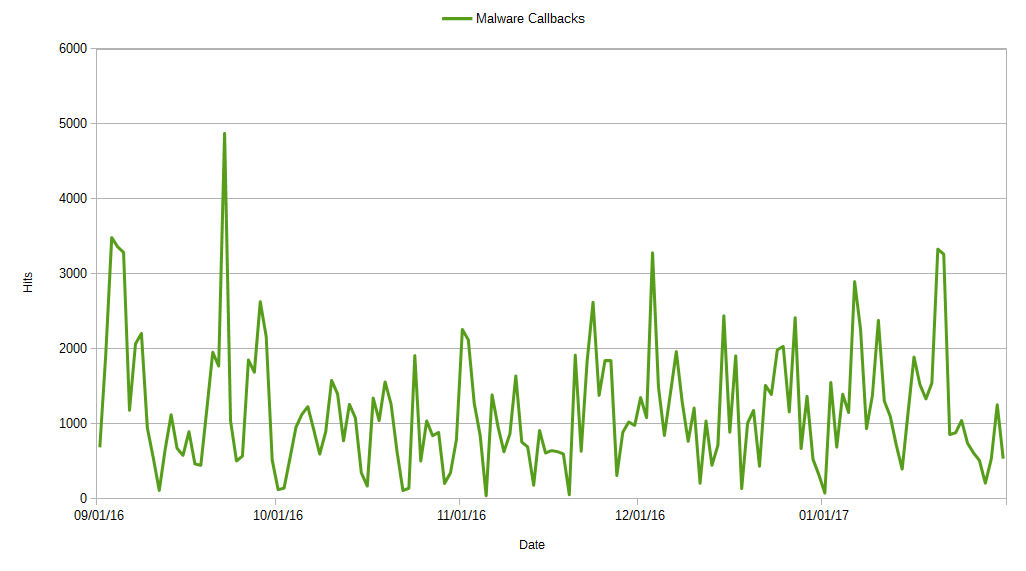
Figure 5. Malware callbacks over SSL, September 2016 – January 2017
Corresponding with the increase in malicious payload deliveries in November 2016, we also observed an increase in blocked malicious SSL traffic during that time.
In our analysis, we came across many malware families that were using SSL for malicious purposes. Some of the recent and notorious malware families actively using SSL are:
Dridex/Dyre/TrickLoader
The Dridex, Dyre, and TrickLoader banking Trojans are capable of communicating to the C&C servers via SSL using its own SSL certificate. These family previously used the common browser hooking technique for callbacks, but the latest versions can perform redirects via local proxy or local DNS poisoning to fake websites, controlled by the attacker.
Vawtrak
Vawtrak is a well-crafted piece of malware supporting the VNC and SOCKS proxies, screenshot and video capturing, and extensibility with regular updates from C&C servers. Vawtrak samples contain code for downloading and validating SSL certificates and are capable of initiating an HTTPS connection. The malware contains a list of HTTPS-secured hosts that contain updated lists of live C&C servers.
Gootkit
Gootkit is a stealth banking trojan with backdoor and spyware capabilities that uses fileless infection and communications over SSL. Gootkit intercepts user data via web injections into HTTPS traffic.
Adware
A common function of adware is to inject unwanted advertisements into web traffic. These advertisements can also lead to malicious infections, as exploit authors frequently take advantage of less-scrupulous advertising networks to distribute exploit redirect scripts. Securing web traffic with SSL/HTTPS prevents this distribution in most cases. Adware installed on a client machine would not be able to perform a man-in-the-middle attack with a self-signed certificate due to the HTTPS safeguards included in modern browsers.
However, in several notable cases, major adware distributions have circumvented these safeguards to inject advertisements into HTTPS traffic. The two most high-profiles examples are the Superfish and PrivDog adware distributions, which were first abusing SSL in 2015. Both of these adware programs install a self-signed root CA certificate onto the victim’s computer, and intercept all web traffic in order to inject advertisements into web pages. PrivDog in particular was a serious concern because it did not validate SSL certificates on its end of the proxy, allowing users to inadvertently navigate to websites with invalid SSL certificates, exposing them to additional threats.
Adware variants have also started to host their files on HTTPS sites. We came across a family of adware called InstallCore, which was doing this kind of activity. InstallCore is a Potentially Unwanted Application (PUA) that installs a program to display and/or download unwanted advertisements and toolbars, and tracks a computer's web usage to feed the victim undesired ad pop-ups; some versions can even hijack a browser’s start or search pages, redirecting the user to a different site or search engine.
InstallCore is often delivered by tricking the user into installing the Flash plugin or a Java update. In some cases, InstallCore is delivered by misdirected download buttons. These fake pop-ups of the Flash player or download buttons appear on content distribution sites, like torrent sites, or free software sites that work on HTTPS.
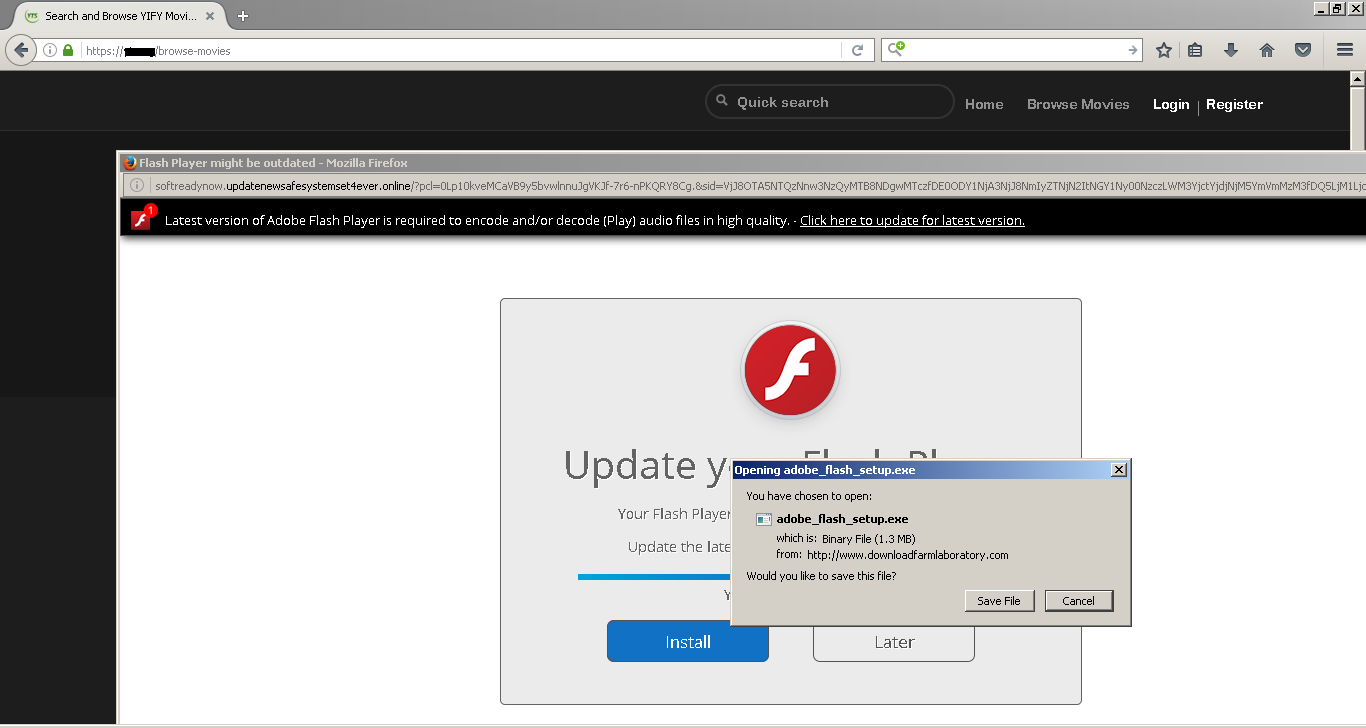
Figure 6. Fake Flash download pop-up
Conclusion
Due to the rising use of SSL encryption to hide exploit kits, malware, and other threats, it is important to have a security infrastructure that can detect and block these threats. The problem is that SSL inspection is compute-intensive, so even organizations whose security appliances support SSL inspection often disable this feature, as its use would slow traffic throughput to unacceptable levels. Dedicated appliances for SSL inspection are available, but their price puts them out of reach for many organizations. SSL inspection is built into the Zscaler security platform, which, due to its scale, can inspect all SSL traffic without latency.
Research by: Derek Gooley, Jithin Nair, Manohar Ghule