A few days back, there was a post on a forum about malware warnings displayed when visiting: www[dot]latax[dot]gov[dot]cn
Upon analysis of the page, it appears that this GOV.CN page is hosting a page exploiting the Internet Explorer 0-day vulnerability (CVE-2010-0249). The same vulnerability exploited to compromise Google, Adobe, and other vendors in an attack dubbed 'Operation Aurora.'
Here is a snippet of the GOV.CN source, building the shellcode variable:

There is a slight deviation to the way that the shellcode is constructed (visible in above image) from some of the other variants that we have seen. Though, it uses the same exploit structure as past variants, including the ev1() and ev2() function names.
The ev1() function is used to dereference the previously declared event object: and attack the vulnerability
and attack the vulnerability
 using the ev2() function to load the shellcode into memory and call the previously dereferenced object:
using the ev2() function to load the shellcode into memory and call the previously dereferenced object:
 The JavaScript loads the shellcode and exploits the vulnerability, which downloads the payload v.exe from the same GOV.CN domain.
The JavaScript loads the shellcode and exploits the vulnerability, which downloads the payload v.exe from the same GOV.CN domain.
VirusTotal identifies 12/41 Anti-Virus engines detect the v.exe payload. It is a variant of the Chinese based Hupigon Backdoor, which F-Secure lists some of its features as:
The Hupigon malware kit is described as being "maintained in a very professional fashion with a highly developed User Interface (UI)." Screenshot below:

This is just one example of this IE 0-day impacting GOV.CN sites; I have seen a few other reports of this. While there are several other examples of malware being hosted on GOV.CN domains, for example,
The question is: are these CN Government sponsored for the purposes of potentially spying on its citizens, or have GOV.CN websites been infiltrated by hackers? In either case, browse safe, and if you are using IE 6, please upgrade or consider a different browser.
 | Translates: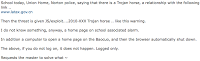 |
Upon analysis of the page, it appears that this GOV.CN page is hosting a page exploiting the Internet Explorer 0-day vulnerability (CVE-2010-0249). The same vulnerability exploited to compromise Google, Adobe, and other vendors in an attack dubbed 'Operation Aurora.'
Here is a snippet of the GOV.CN source, building the shellcode variable:

There is a slight deviation to the way that the shellcode is constructed (visible in above image) from some of the other variants that we have seen. Though, it uses the same exploit structure as past variants, including the ev1() and ev2() function names.
The ev1() function is used to dereference the previously declared event object:
 and attack the vulnerability
and attack the vulnerability using the ev2() function to load the shellcode into memory and call the previously dereferenced object:
using the ev2() function to load the shellcode into memory and call the previously dereferenced object: The JavaScript loads the shellcode and exploits the vulnerability, which downloads the payload v.exe from the same GOV.CN domain.
The JavaScript loads the shellcode and exploits the vulnerability, which downloads the payload v.exe from the same GOV.CN domain.VirusTotal identifies 12/41 Anti-Virus engines detect the v.exe payload. It is a variant of the Chinese based Hupigon Backdoor, which F-Secure lists some of its features as:
• It allows others to access the computer
• Allows for recording with the user's webcam
• Can make the user's computer to attack various servers
• Send victim's computer messages
• Has rootkit functionality so it has a stealth component that hides files
• Create logs from keystrokes, steals passwords, and sends this information to remote servers
• Allows for recording with the user's webcam
• Can make the user's computer to attack various servers
• Send victim's computer messages
• Has rootkit functionality so it has a stealth component that hides files
• Create logs from keystrokes, steals passwords, and sends this information to remote servers
The Hupigon malware kit is described as being "maintained in a very professional fashion with a highly developed User Interface (UI)." Screenshot below:

This is just one example of this IE 0-day impacting GOV.CN sites; I have seen a few other reports of this. While there are several other examples of malware being hosted on GOV.CN domains, for example,
- .wscz.gov.cn
- .zhepb.gov.cn
- .jssalt.gov.cn
- .xfgh.gov.cn
- .laspzx.linan.gov.cn
- .zsjs.nmfc.gov.cn





