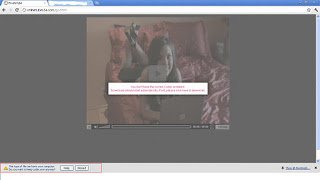
Convincing users to download malicious software using fake AV pages is not a new attack vector, but has been a very successful one. Julien has previosuly blogged about how fake codecs are starting to replace fake AV pages. I recently encountered an interesting example employing both fake AV and fake codecs in a single attack. When a victim visits a page, they are presented with a warning message stating “You don’t have the correct Codec installed. Download should start automatically, if not, please click here to download”. Here is the screenshot of the page:
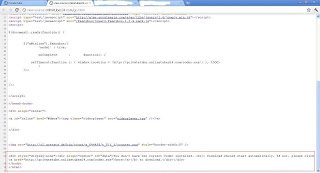
The page is loaded from “hxxp://onlinetubes24.com/go.html”. Let’s take a look at the HTML source of the page to identify the malicious code.
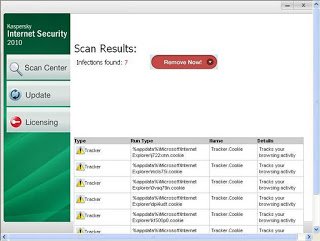
As you can see, it downloads an exe from “hxxp://privatetube.onlinetubes24.com/codec.exe". If the victim runs “codec.exe”, it starts a fake antivirus scan and delivers a report such as the following:
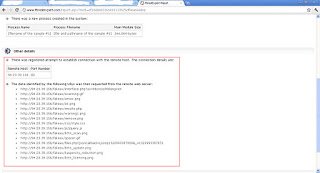
The above screenshot is typical of a fake AV attack and displays several fictitious threats being detected on the victim’s computer. Every time you run this exe file, different threats are allegedly detected . Once installed, the victim is asked to activate or buy the full version of this fake AV. This exe file downloads it’s content from a remote web server hosted at “94.23.39.156”. The ThreatExpert report for this IP address details the network activity performed by this malware.
The VirusTotal results for the fake security software in this example show that it is detected by only 20/42 popular AV vendors. You can find some tips to stay away from such attacks in a separate blog post.
Make sure you are downloading real codecs, not fake ones!
Pradeep