This blog is an overview of the latest threat research conducted by ThreatLabZ, Zscaler’s security research team. The full report is available here.
While SSL/TLS encryption is the industry standard for protecting data in transit from prying eyes, encryption has, itself, become a threat. It is often leveraged by attackers to sneak malware past security tools that do not fully inspect encrypted traffic. As the percentage of traffic that is encrypted continues to grow, so do the opportunities for attackers to deliver threats through encrypted channels.
To better understand the use of encryption and the volume of encrypted traffic that is inspected, our research team, ThreatLabZ, analyzed encrypted traffic across the Zscaler cloud for the first nine months of 2020, assessing its use within specific industries. The study we conducted also set out to analyze the types of attacks that use encryption and the extent of the current risk.
Our 2020 report shows that SSL-based threats remain prevalent and are becoming increasingly sophisticated. Our findings, some of which are highlighted below, show that traffic moving through encrypted channels can no longer be trusted simply by virtue of a digital certificate—the padlock icon on your browser does not guarantee security.
Attackers are preying on people’s trust of brands like Microsoft, Google, Netflix...
Our research showed that attackers have rapidly increased registration of malicious domains, which contributed to the 260 percent increase in SSL-encrypted threats in 2020 when compared to last year.
Netflix credential phishing site over HTTPS
Cybercriminals use “domain squatting” and “homograph attacks” to imitate popular, legitimate web pages with pixel-perfect replicas. Their ultimate goal is obvious: prey on the trust of big brands to deliver malware and steal login credentials (such as banking information) and other sensitive personal information. For example, links to registered domains along the lines of gmali.com and app1e.com could be clicked on by someone not paying close attention and these sites can look nearly indistinguishable from the legitimate ones. And, as these domains leverage SSL/TLS encryption by default, they could easily bypass traditional security controls.
They abuse AWS, Google Drive, OneDrive, and Dropbox to deliver encrypted threats
Cloud-based file-sharing services are powerful tools for boosting employees’ collaboration and productivity. These services securely share files and information, with the SSL-encrypted content generally bypassing security controls. While good for performance, bypassing security can open a backdoor into many enterprises. By the end of the analysis period, we found that malicious content delivered with encryption from file-sharing services represented 30 percent of all malicious SSL traffic.
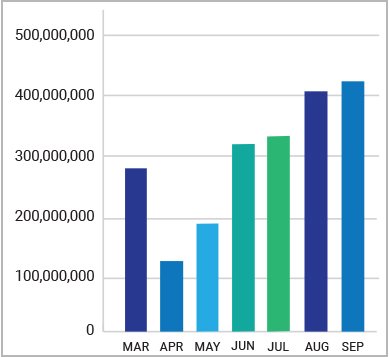
Advanced threats blocked over TLS/SSL from top cloud storage services
Attacks can be initiated by creating file-sharing URLs to malicious content hosted in services like Google Drive or Dropbox as part of an email phishing campaign. This approach removes the need to attach infected files to emails, which users have been trained to treat with suspicion. Because the content is hosted on a legitimate file-sharing site, it comes with a level of trust—and infected users can quickly spread the attack by sharing the link across the organization.
Encrypted ransomware attacks continue to rise
Ransomware, malware that encrypts a host’s device or an organization’s data or network in exchange for a ransom payment, remains a significant threat. After successfully stealing and encrypting an organization’s data, today’s attackers may threaten to leak the data if no payment is made. Ransomware attacks delivered over SSL-encrypted channels is the next evolution of this highly destructive attack vector because it makes the attacks harder to detect. We saw a 500 percent increase in ransomware over encrypted channels between March and September 2020.
Telecom companies and healthcare institutions have been hit the hardest because they tend to pay the ransoms due to the sensitive nature of their data. Ransomware families including FileCrypt/FileCoder variants, Sodinokibi, Maze, and Ryuk have been the most prevalent in our research.
Healthcare organizations bear the brunt of SSL-based attacks
Cybercriminals, showing no limits to their depravity, have increased their attacks on the healthcare sector during the pandemic using advanced threats over encrypted channels. Our research found that healthcare was targeted by 25.5 percent of SSL-encrypted threats. While costly, threats hidden in encryption can have even more dire consequences, particularly when they affect the delivery of healthcare.

Advanced threats blocked over encrypted channels by industry
Protecting your organization against SSL threats
It’s important to recognize that SSL traffic is not necessarily secure traffic. Just as the use of encryption has increased, so has its use among adversaries to hide their attacks. The need to inspect encrypted traffic is greater than ever.
- Decrypt, detect, and prevent threats in all SSL traffic with a proxy-based architecture and cloud-native performance.
- Quarantine unknown attacks and stop patient-zero malware with AI-driven quarantine that holds suspicious content for analysis, unlike firewall-based passthrough approaches.
- Provide consistent security for all users and all locations to ensure everyone has the same great security all the time, whether they are at home, at headquarters, or on the go.
- Instantly reduce your attack surface by starting from a position of zero trust, where lateral movement can’t exist. Apps are invisible to attackers, and authorized users directly access needed resources, not the entire network.
To learn more about the evolving SSL threat landscape and what your organization can do to inspect all traffic and stay protected, download and review the full ThreatLabZ report.






