Zscalerのブログ
Zscalerの最新ブログ情報を受信
購読する
Strengthen your enterprise security posture with MITRE ATT&CK mapping to Cloud Browser Isolation controls
Defending an enterprise against modern-day attacks remains an increasingly difficult challenge that requires, among other things, advanced technologies and innovative approaches for thwarting an adversary’s goals. To help address those challenges, MITRE Corporation developed ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) framework. This serves as a knowledge base of commonly observed adversarial behaviors to support the efforts of threat intelligence functions, with adversary emulation and defensive gap analysis.
In this article, you'll learn why Zscaler Cloud Browser, natively integrated within the Zscaler Zero Trust Exchange (ZTE), is needed as another critical layer of defense to strengthen your organization’s security posture as well to mitigate various TTPs as highlighted in the ATT&CK framework.
Zscaler Cloud Browser Isolation
Zscaler Cloud Browser Isolation, natively integrated within the ZTE platform, detonates the web content and isolates any associated zero day threats in an air-gapped cloud container. It also enforces clipboard, upload/download, read-only, and print controls along with turbo streaming safe graphical representation (no active content, scripts or code) to the user’s favorite browser for a near-native web experience.
The built-in document processing technology can allow the productivity related files (.docx, .pptx, .vsdx, .rtf etc.) to be safely viewed within isolation (via ‘protected storage’) or downloaded as sanitized files (CDR - Content Disarm and Reconstruction). Files are deconstructed in order to remove any potentially malicious components such as VBA macros, scripts, and active content. Moreover, any QR codes are disarmed as well, this effectively thwarting any steganography attacks.
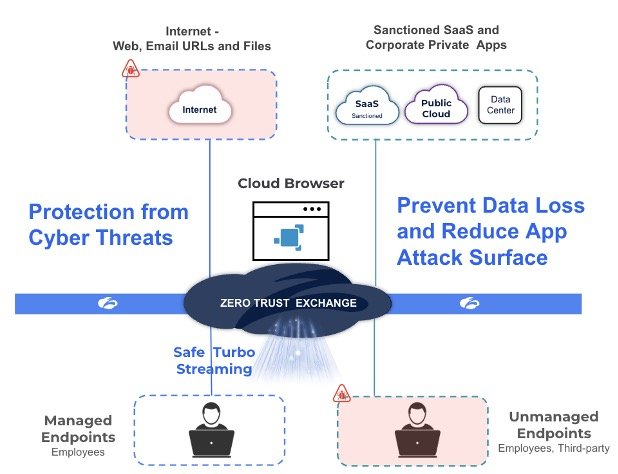
Zscaler Cloud Browser Isolation also allows employees, contractors and third-parties to safely access SaaS and private web applications from any unmanaged device without the need for an agent (not requiring VDI or changing end-user browser) while enforcing comprehensive data protection controls. This architecture also provides application protection. Private web apps are hidden from the internet by the Zero Trust Exchange, reducing their attack surface. Moreover, Cloud Browser obfuscates the application headers and hides away the application’s anatomy, (protocol, OS versions, software components, etc.), further shrinking the attack surface by stopping attackers from using malware-infected, unmanaged devices to exploit these apps.
ATT&CK mapping to Cloud Browser controls
Tactics represent the "why" of an ATT&CK technique or sub-technique. It is the adversary's tactical goal: the reason for performing an action.
Techniques represent 'how' an adversary achieves a tactical goal by performing an action.
The tactics can as well be mapped to the Zscaler cyber kill chain taxonomy: Attack Surface, Compromise, Lateral Movement and Data Exfiltration.
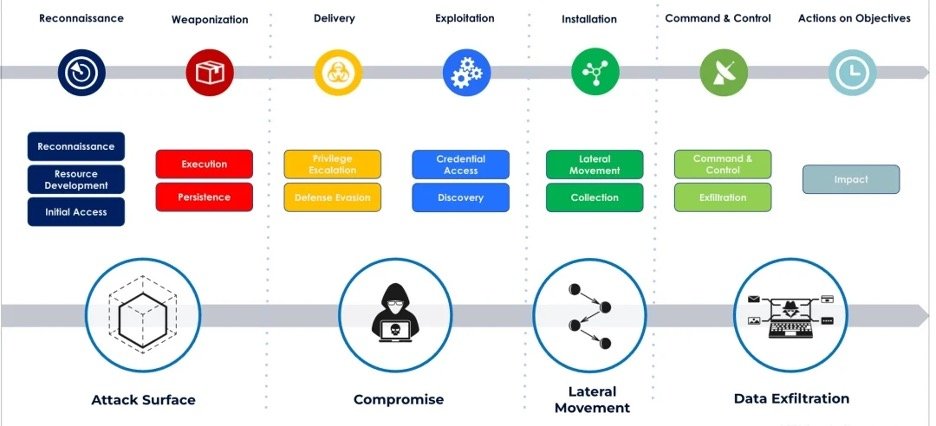
Here are some of the prominent TTPs mitigated through Cloud Browser, natively integrated with ZTE, controls.
Tactic | Technique(TTP name) | TTP Description | ZscalerKill Chain |
|---|---|---|---|
Initial Access | T1189Drive-by Compromise | A user's web browser is typically targeted for exploitation, but adversaries may also use compromised websites for non-exploitation behavior (acquiring Application Access Token) | Attack Surface |
Initial Access | T1190Exploit Public-Facing Application | The weakness in the system can be a bug, a glitch, or a design vulnerability. These applications are often websites, but can include services (like SSH), and others with Internet accessible open sockets, such as web servers | Attack Surface |
Initial Access | T1566Phishing | Adversaries may send phishing messages to gain access to victim systems. | Attack Surface |
Initial Access | T1566.001Spearphishing Attachment | Spearphishing attachment is different in that it employs the use of malware attached to email. | Attack Surface |
Initial Access | T1566.002Spearphishing Link | It employs the use of links to download malware contained in email, to avoid defenses that may inspect email attachments. | Attack Surface |
Initial Access | T1566.003Spearphishing via Service | It employs the use of third party services rather than directly via email channels. | Attack Surface |
Execution | T1059.007JavaScript (JS) | Adversaries may abuse various implementations of JS for execution. JS is commonly associated with scripts in webpages. | Attack Surface |
Execution | T1203Exploitation for Client Execution | Vulnerabilities can exist in software due to unsecure coding practices. Users will expect to see files related to the applications they commonly used to do work, so they are a useful target for exploit research and development | Attack Surface |
Execution | T1204User Execution | Users may be subjected to social engineering to get them to execute malicious code by, for example, opening a malicious file or link. | Attack Surface |
Execution | T1204.001Malicious Link | Clicking on a link may lead to other execution techniques such as exploitation of a browser or application vulnerability via Exploitation for Client Execution. | Attack Surface |
Execution | T1559Inter-Process Communication(IPC) | Adversaries may abuse IPC mechanisms for local code or command execution. IPC is used to share data, or synchronize execution. | Attack Surface |
Execution | T1559.001Component Object Model (COM) | Adversaries may use the Windows COM for local code execution. Through COM, a client object can call methods of server objects, which are typically binary DLL or EXE. | Attack Surface |
Execution | T1559.002Dynamic Data Exchange (DDE) | DDE is a client-server protocol for one-time and/or continuous IPC between applications. Once a link is established, applications can autonomously exchange transactions consisting of strings, warm links (notifications when data changes), requests for command execution. | Attack Surface |
Privilege Escalation | T1068Exploitation for Privilege Escalation | Security constructs such as permission levels will hinder access to information, so adversaries will likely need to perform privilege escalation to circumvent those restrictions. | Compromise |
Defense Evasion | T1218.001Compiled HTML File (.CHM) | Adversaries may abuse .CHM files to conceal malicious code. CHM files are commonly distributed as part of the Microsoft HTML Help.. CHM content is displayed using components of the IE browser loaded by the HTML Help exe | Compromise |
Credential Access | T1212Exploitation for Credential Access | One example of this is MS14-068, which targets Kerberos and can be used to forge Kerberos tickets using domain user permissions. Exploitation for credential access may also result in Privilege Escalation. | Compromise |
Lateral Movement | T1210Exploitation of Remote Services | Exploitation of a software vulnerability occurs when an adversary takes advantage of a programming error in a program, service, or within the operating system software or kernel itself to execute adversary-controlled code. A common goal for post-compromise exploitation of remote services is for lateral movement to enable access to a remote system. | Lateral Movement |
Exfiltration | T1567Exfiltration Over Web Service | Popular Web services acting as an exfiltration mechanism may give a significant amount of cover due to the likelihood that hosts within a network are already communicating with them prior to compromise. Firewall rules may also already exist to permit traffic to these services. | Data Exfiltration |
Exfiltration | T1567.001Exfiltration to Code Repository | Code repositories are often accessible via an API (ex: https://api.github.com). Access to these APIs are often over HTTPS, which gives the adversary an additional level of protection. | Data Exfiltration |
Exfiltration | T1567.002Exfiltration to Cloud Storage | Cloud storage services allow for the storage, edit, and retrieval of data from a remote cloud storage server over the Internet. | Data Exfiltration |
Command and Control | T1102Web Service | Popular websites and social media (such as those offered by Google or Twitter) acting as a mechanism for C2 may give a significant amount of cover due to the likelihood that hosts within a network are already communicating with them prior to a compromise. Web service providers commonly use SSL/TLS encryption, giving adversaries an added level of protection. | Data Exfiltration |
Command and Control | T1102.001Dead Drop Resolver | Adversaries may post content, known as a dead drop resolver, on Web services with embedded (and often obfuscated/encoded) domains or IP addresses. Once infected, victims will reach out to and be redirected by these resolvers. | Data Exfiltration |
Command and Control | T1102.002Bidirectional Communication | Those infected systems can then send the output from those commands back over that Web service channel. For example, the return traffic may take the form of the compromised system posting a comment on a forum, issuing a pull request to a development project, updating a document, or by sending a Tweet. | Data Exfiltration |
Command and Control | T1102.003One-Way Communication | Those infected systems may opt to send the output from those commands back over a different C2 channel, including to another distinct Web service. Alternatively, compromised systems may return no output at all in cases where adversaries want to send instructions to systems and do not want a response. | Data Exfiltration |
Next steps
MITRE ATT&CK framework is already incorporated in the Zscaler Risk360 product to enhance risk analysis for your specific environment as well as get tailored recommendations for implementing various controls.
Please reach out to us for more details on the Cloud Browser and the aforementioned MITRE ATT&CK mapping.



