Insider threats aren’t uncommon in cybersecurity—in fact, reality shows us quite the opposite. More than two thirds of attacks and data loss incidents originate from insiders, malicious or negligent. Insider risk is difficult to mitigate because, unlike external attackers, insiders already have the necessary credentials and permissions to access sensitive data and intellectual property. They often come in the form of compromised service accounts, with the belligerent(s) looking to intentionally harm the organization, but an insider threat can also stem from a user or users who have unintentionally left the business susceptible to attack. The insider threat landscape has evolved in recent years, with new types of actors, such as nation states and supply chain partners, and new risks arising from remote work and cloud adoption. If left unchecked, compromised or malicious insiders can cause large-scale data breaches and greatly harm an organization or organizations.
The question becomes: how will you know when your users are accessing sensitive data with malicious intent?
Understanding Insider Threats – Privilege Escalation, Lateral Movement, and Data Exfiltration
Users access valuable data as part of their job, whether through cloud services or a company’s infrastructure. If a user is accessing such data on a remote device, it can be much harder to track. If such privilege is left unsupervised, insiders can exploit system or application errors to gain access to unauthorized resources. This is called privilege escalation, and it’s hard to detect with traditional tools.
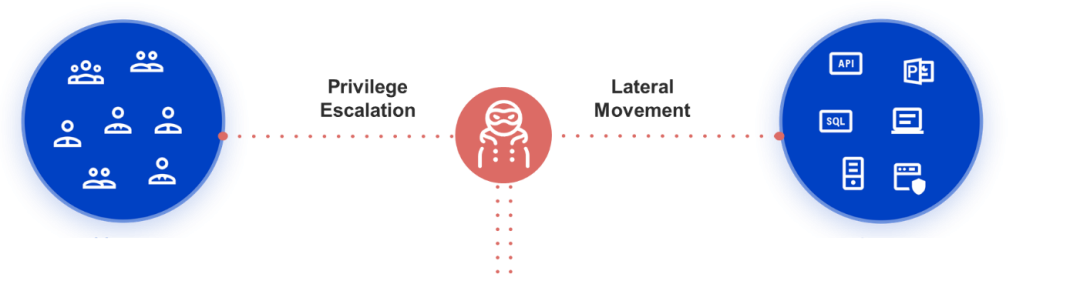
Figure 1 – Using privilege escalation, an attacker can move horizontally, gaining access to other user or service accounts, or vertically, gaining greater access via power users or administrators to gain access to the crown jewels and exfiltrate data
In order to prevent such an incident, a security analyst would need to understand a user’s normal activity in order to identify potentially malicious activity. This can be a challenging task, even with behavioral analytics, because many users and entities have multiple accounts and may work on different networks.
Zscaler Deception™ uncovers risky users, detects and disrupts insider attacks
Traditional security solutions focus on protecting organizations from external threats, but Zscaler uses Active Deception technology to help detect hard-to-seek insider threats. The Zscaler zero trust platform audits every person or device that requests access to systems and resources, regardless of whether the requestor is an insider or an outsider. In doing so, Zscaler zero trust addresses security’s dark horse: trusted devices. As part of a zero trust architecture, Zscaler Deception fences users and applications with decoys. Users are armed with lures on endpoints, decoy files, and decoy users in the Active Directory. On the application side, Deception comes with decoy servers, databases, and internal apps.
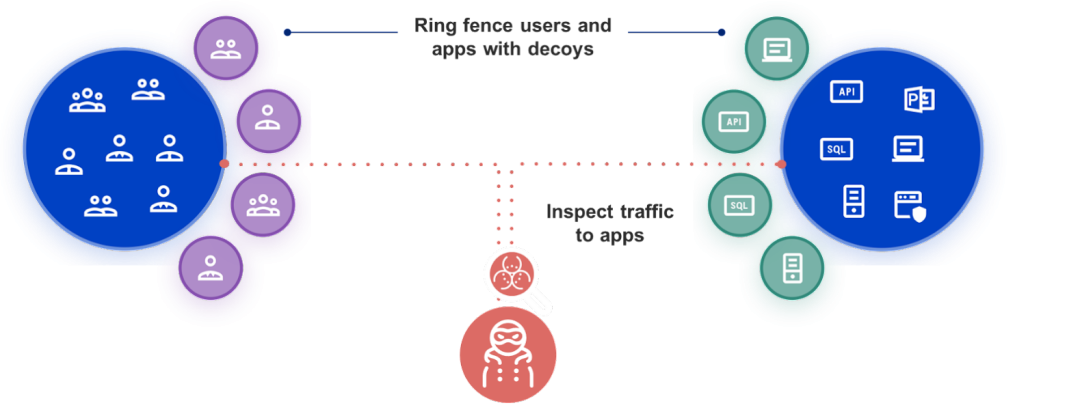
Figure 2: Secure your data with Zscaler Deception
With decoys, malicious insiders are tricked into revealing themselves using a series of schemes, credentials, and data. Decoys have no real production value and exist for the sole purpose of intercepting attacks. The decoy systems imitate production assets and interact with attackers, capturing their every move while feeding them false information. These fake assets are never used in normal business operations, so any activity involving them is almost always an indication that an attacker has gained initial access to your infrastructure. The deception technology adds an element of surprise as decoys are invisible to normal users and the location of the decoys is only known to a small group of people, so the insider won't know about it or where it's being deployed. Plus, since no one knows they exist and they’re strategically planted in places where only an attacker would know to look, any interaction with a decoy is a high confidence indicator of a breach.
Zscaler deceives endpoint threats by sending lures to attackers that lead them to the Zscaler decoy systems, away from production systems. An alert notifies the security advisor of the attacker’s presence, and the telemetry collected enables the SOC team to analyze behavior, scan the network for threats, or block access. It’s highly unlikely for deception alerts to be false positives. So, by fencing users and applications with decoys, we can detect adversaries that have bypassed existing defenses and are attempting to escalate privileges and move laterally.
Minimise Insider attacks: Zscaler Deception is aligned to MITRE Attack Framework
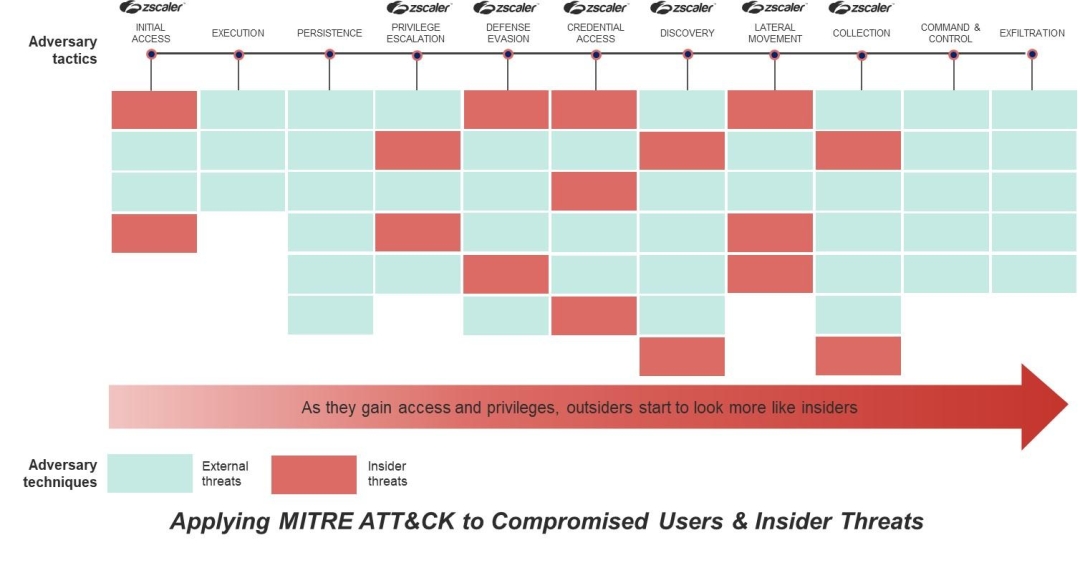
Zscaler Deception covers 99% of MITRE Engage activities , a framework for applying the state of the art in active defense, deception, and adversary engagement operations. It was developed by the team at MITRE, based on a decade of experience applying active defense principles to defend their network. When considering the MITRE ATT&CK framework, for which there is a basic abstract table below, we typically view deception technology used upfront as an additional layer of protection. But throughout the framework, there are ways to set traps, set early and obvious signals, and frustrate adversaries. In the figure labelled below are tactics (in columns). Those with Zscaler symbols on top signify where Deception can provide utility. To learn more, read our whitepaper, Adopting Mitre Engage with Zscaler Deception .
Concluding Thoughts
While there is no silver bullet for preventing confidential data from being exposed, organizations can take steps to minimize the risk insider threats present.
Deception uses an adversary's mindset against them, changing the game for the defense and allowing them to ‘beat the odds’ against more advanced threats. Zscaler Deception helps you to capture these threats and restrict their ability to locate targets or move laterally. Identify, misdirect, and isolate external and internal threats that have gained a foothold in your zero trust environment. Zscaler Deception seamlessly integrates with Zscaler as well as other third-party security solutions such as SIEM or SOAR to automatically stop active attackers with response actions.
Read more about our Deception technology here.





