/ O que são ameaças internas?
O que são ameaças internas?
Ameaças internas são riscos de segurança cibernética que se originam dentro de uma organização, geralmente envolvendo funcionários, prestadores de serviço ou outros indivíduos confiáveis que têm acesso a dados sigilosos, sistemas ou redes. Essas ameaças podem ser intencionais (como um funcionário roubando deliberadamente informações confidenciais) ou não intencionais, quando uma pessoa bem-intencionada acidentalmente expõe ativos críticos por meio de negligência, erro humano ou práticas de segurança inadequadas.
Principais conclusões: visão geral de ameaças internas
- As ameaças internas se originam internamente e podem ser categorizadas em riscos maliciosos, acidentais, negligentes ou de terceiros.
- A arquitetura de segurança zero trust é crucial para mitigar ameaças internas.
- A Zscaler fornece soluções avançadas como Risk360™, ITDR™ e Deception™ para identificar e eliminar proativamente essas ameaças.
Tipos de ameaças internas: riscos internos maliciosos, acidentais, negligentes e de terceiros
As ameaças internas vêm de várias formas, cada uma delas apresentando desafios únicos à postura de segurança de uma organização. Essas ameaças têm o potencial de contornar defesas tradicionais como firewalls ou explorar pontos fracos em implementações de VPN, o que as torna especialmente perigosas nos ambientes altamente conectados de hoje, em que a conectividade e o acesso confiável podem inadvertidamente ampliar os riscos.
Ameaças internas maliciosas
Insiders maliciosos são indivíduos dentro de uma organização que intencionalmente comprometem a segurança para ganho pessoal ou por despeito. Um exemplo clássico é um funcionário descontente que rouba propriedade intelectual ou vende credenciais de acesso para criminosos cibernéticos. Essas ameaças geralmente são motivadas por incentivos financeiros, queixas emocionais ou desejo de vingança, o que as torna particularmente difíceis de detectar.
Como essas pessoas já têm acesso legítimo a dados sigilosos, elas podem facilmente explorar esse acesso se controles de segurança adequados não estiverem em vigor. Prevenir ameaças internas maliciosas requer monitoramento constante, gerenciamento rigoroso de acesso e análise comportamental para detectar atividades incomuns antes que o dano seja causado.
Exemplo: Edward Snowden, um ex-prestador de serviços da NSA, é um dos exemplos mais conhecidos de um insider malicioso. Snowden vazou informações confidenciais sobre programas globais de vigilância operados pela NSA e seus parceiros. Suas ações tiveram motivações ideológicas e não ganhos financeiros, mas elas destacam os danos que um único infiltrado pode causar.
Ameaças internas acidentais
Ameaças internas acidentais ocorrem quando funcionários, sem saber, abrem a porta para ataques cibernéticos. Exemplos cotidianos incluem ser vítima de golpes de phishing, definir incorretamente as configurações de segurança ou compartilhar acidentalmente arquivos confidenciais com terceiros não autorizados. O erro humano é uma das causas mais comuns de ameaças internas, e sua frequência destaca por que confiar apenas em defesas de perímetro não é mais suficiente.
A mitigação de ameaças internas exige estratégias proativas, como treinamento frequente em segurança, conformidade dos funcionários com protocolos de cibersegurança e integração de soluções zero trust.
Exemplo: em 2017, um funcionário perdeu acidentalmente uma unidade USB contendo detalhes de segurança sigilosos relacionados às operações do Aeroporto de Heathrow. A campanha, que incluía informações sobre medidas de segurança, cronogramas de patrulha e detalhes de viagem da Rainha, foi descoberta por um membro do público. Felizmente, não ocorreu nenhuma violação grave, mas o incidente destacou como ações internas acidentais, como extravio de dados sigilosos, podem levar a riscos de segurança significativos.
Ameaças internas negligentes
Insiders negligentes são funcionários que não seguem as práticas de segurança recomendadas, seja por descuido ou falta de conscientização. Isso pode ser algo tão simples quanto compartilhar senhas, usar dispositivos não autorizados ou ignorar protocolos básicos de segurança. Embora não sejam maliciosos, esses comportamentos criam vulnerabilidades sérias que os invasores podem explorar.
Para mitigar os riscos representados por insiders negligentes, as empresas precisam aplicar políticas de segurança rígidas e responsabilizar os funcionários por segui-las.
Exemplo: em 2020, um funcionário do Facebook violou as políticas da empresa ao armazenar dados de folha de pagamento não criptografados em seu laptop pessoal. Infelizmente, o laptop foi roubado, expondo informações sigilosas de aproximadamente 29 mil funcionários. Embora não houvesse nenhuma indicação de que os dados foram mal utilizados, esse ato negligente de manuseio incorreto de informações sigilosas poderia ter levado a consequências sérias.
Ameaças internas de terceiros
Ameaças internas de terceiros vêm de prestadores de serviço, fornecedores ou parceiros que têm acesso aos sistemas ou dados de uma organização. Embora esses colaboradores externos sejam essenciais para as operações, eles introduzem vetores de risco adicionais. Se um sistema terceirizado for comprometido ou as credenciais de um prestador de serviço forem roubadas, os invasores podem obter acesso a informações sigilosas, muitas vezes sem serem detectados.
Exemplo: a violação de dados da Home Depot ocorreu porque invasores obtiveram acesso aos sistemas da empresa por meio de credenciais roubadas de um fornecedor terceirizado. Essa violação comprometeu 56 milhões de números de cartão de crédito e destaca os riscos que terceiros representam quando controles de acesso adequados não são implementados.
Gerenciar esses riscos requer estender princípios de privilégio mínimo a usuários terceirizados, garantindo que eles recebam a menor quantidade de acesso necessária e sejam monitorados continuamente ao interagir com sistemas internos. Empregar controles de acesso rigorosos e avaliações de segurança frequentes de parceiros terceirizados pode reduzir significativamente essa ameaça.
Sinais de alerta e indicadores de ameaças internas
Detectar ameaças internas exige vigilância em diversas camadas de segurança. Alguns sinais de alerta importantes incluem:
Indicadores comportamentais
Funcionários que exibem padrões de acesso incomuns, como fazer login em sistemas que normalmente não usam, transferir grandes quantidades de dados ou realizar atividades fora do horário comercial, podem sinalizar possíveis ameaças internas. Esses comportamentos muitas vezes se desviam das normas estabelecidas e exigem um exame mais detalhado.
Monitoramento da presença digital
Monitorar o comportamento digital por meio da análise de comportamento do usuário (UBA) e sistemas de gerenciamento de informações e eventos de segurança (SIEM) é fundamental. Essas ferramentas ajudam a identificar anomalias na atividade do usuário, como locais de login inesperados, tentativas de aumentar privilégios, picos repentinos no acesso a dados sigilosos ou grandes transferências de dados, o que pode indicar intenção maliciosa ou credenciais comprometidas.
Preocupações com a segurança física
As ameaças internas também podem se manifestar no ambiente físico, com funcionários ou prestadores de serviço tentando obter acesso não autorizado a áreas seguras. Isso pode envolver contornar controles de segurança física, seguir outras pessoas sem autorização ou usar credenciais roubadas para entrar em zonas restritas.
Como o zero trust ajuda
Integrar uma abordagem zero trust pode mitigar os riscos representados por ameaças internas. Por meio de monitoramento e verificação contínuos, o zero trust garante que até mesmo usuários internos sejam autenticados e autorizados em cada etapa. Isso limita a movimentação lateral e minimiza os danos que um insider pode causar, pois seu acesso é restrito e constantemente examinado. A implementação de mecanismos de detecção robustos permite que as equipes de segurança identifiquem e neutralizem ameaças antes que elas comprometam sistemas críticos.
Consequências comerciais das ameaças internas: riscos financeiros, reputacionais e legais
As ameaças internas podem devastar as organizações de diversas maneiras, muitas vezes mais prejudiciais do que ataques externos. Abaixo estão algumas das consequências mais significativas que as empresas enfrentam quando ameaças internas se materializam.
Perdas financeiras
A consequência mais imediata e tangível de uma ameaça interna é a perda financeira. Seja devido ao roubo direto de ativos, à perda de propriedade intelectual ou ao custo de resposta a uma violação de dados, as organizações geralmente pagam um preço alto quando um insider é comprometido. De acordo com a IBM, o custo médio de uma violação de dados em 2024 foi de US$ 4,88 milhões, e incidentes internos podem ser ainda mais custosos quando se considera a complexidade de detecção e remediação. Além disso, o tempo de inatividade e as interrupções operacionais causadas por violações internas podem impactar severamente a receita, agravando ainda mais as perdas.
Danos à reputação
Além do impacto financeiro direto, as ameaças internas podem manchar gravemente a reputação de uma empresa. Quando dados de clientes são expostos ou detalhes comerciais sigilosos são vazados, os consumidores perdem a confiança rapidamente. Um bom exemplo é a violação de dados da Target em 2013, que levou à exposição de 40 milhões de números de cartão de crédito e prejudicou gravemente a credibilidade da varejista. Os clientes geralmente veem as violações como um sinal de práticas de segurança ruins, levando à perda imediata de negócios e à erosão da marca a longo prazo. Mesmo depois que os problemas técnicos forem resolvidos, reconstruir a confiança pode levar anos, se for possível.
Questões legais e de conformidade
As organizações também estão expostas a riscos legais e regulatórios significativos quando ocorrem ameaças internas. Regulamentações como GDPR, HIPAA e CCPA impõem requisitos rigorosos sobre como as empresas devem proteger dados sigilosos. O não cumprimento, seja intencional ou por negligência, pode resultar em multas e sanções pesadas. Por exemplo, sob o GDPR, as organizações podem ser multadas em até 20 milhões de euros ou 4% do seu volume de negócios global anual, o que for maior. Além das penalidades financeiras, as empresas também podem enfrentar ações judiciais das partes afetadas, aumentando ainda mais os custos e prolongando os danos.
As consequências das ameaças internas ressaltam claramente a necessidade de uma arquitetura zero trust, que enfatiza a verificação contínua e limita a movimentação lateral dentro de uma rede. Isso é fundamental para mitigar os riscos representados por ameaças internas. Ao assumir que nenhum usuário (interno ou externo) deve ser considerado inerentemente confiável, as organizações podem impor controles mais rigorosos e monitorar comportamentos anormais, reduzindo a probabilidade de que um insider possa causar danos generalizados.
Estratégias de mitigação para ameaças internas
Mitigar efetivamente as ameaças internas requer uma abordagem multifacetada que combine tecnologia, política e educação. Ao implementar uma estratégia abrangente, as organizações podem detectar, conter e prevenir proativamente possíveis incidentes internos antes que eles se agravem.
Implementação de um programa de ameaças internas
Criar um programa de ameaças internas (ITP) é um passo fundamental para lidar com riscos. Um ITP bem estruturado ajuda as organizações a gerenciar sistematicamente vulnerabilidades relacionadas a insiders. As principais etapas incluem:
- Avaliação de riscos: identifique e priorize os ativos, dados e sistemas mais vulneráveis a ameaças internas.
- Criação de políticas: desenvolva políticas claras e aplicáveis que descrevam comportamentos aceitáveis, controles de acesso e protocolos de relatos de incidentes.
- Monitoramento do comportamento dos usuários: implemente o monitoramento contínuo da atividade dos usuários, com ênfase em funcionários ou prestadores de serviço de alto risco.
- Planejamento de resposta a incidentes: estabeleça um plano de resposta formal que inclua procedimentos de investigação, estratégias de contenção e protocolos de comunicação.
- Avaliação periódica: audite e atualize com frequência o programa para adaptá-lo às ameaças emergentes e às necessidades comerciais em evolução.
Uma arquitetura de segurança zero trust
Um modelo de segurança zero trust reduz significativamente o risco de ameaças internas ao impor controles de acesso rigorosos e verificar continuamente as identidades dos usuários. Ao adotar uma abordagem de “nunca confiar, sempre verificar”, o zero trust limita a movimentação lateral dentro da rede de uma organização, garantindo que os usuários tenham acesso somente aos recursos de que precisam, quando precisam. Essa arquitetura também se integra a soluções de monitoramento, fornecendo visibilidade em tempo real sobre o comportamento dos usuários e revogando automaticamente o acesso caso atividades suspeitas sejam detectadas. A implementação do zero trust pode reduzir significativamente a superfície de ataque, tornando-se uma ferramenta poderosa de mitigação contra ameaças internas
Programas de treinamento e conscientização
Instruir os funcionários sobre a importância da segurança cibernética e da prevenção de ameaças internas é crucial. Programas de treinamento bem executados garantem que toda a equipe, desde executivos até funcionários iniciantes, entendam os riscos e suas responsabilidades. O treinamento deve abranger as práticas recomendadas, como reconhecer tentativas de phishing, proteger credenciais privilegiadas e relatar atividades suspeitas. Campanhas de conscientização também podem destacar estudos de caso do mundo real que ilustram os danos que ameaças internas podem causar, reforçando a importância da vigilância.
Soluções de monitoramento e detecção
Ferramentas avançadas de monitoramento são um componente essencial para a mitigação de ameaças internas. Soluções de gerenciamento de acesso privilegiado (PAM) limitam e rastreiam as ações de usuários com privilégios elevados, reduzindo o risco de invasores desonestos ou negligentes. Os sistemas de prevenção contra perda de dados (DLP) monitoram transferências ou vazamentos de dados não autorizados, garantindo que informações sigilosas permaneçam dentro da organização. As soluções de análise de comportamento do usuário (UBA) usam aprendizado de máquina para detectar padrões de comportamento anômalos que podem indicar intenção maliciosa, como tempos de acesso incomuns ou picos de download de dados. Juntas, essas ferramentas fornecem uma defesa em camadas contra atividades internas.
A Zscaler protege contra ameaças internas
A Zscaler oferece um conjunto abrangente de soluções para proteger organizações contra ameaças internas, combinando tecnologias de ponta, análises em tempo real e princípios de zero trust. Com a Zscaler Cyberthreat Protection, as ameaças internas são mitigadas por meio da detecção de ameaças com tecnologia de IA, inspeção de TLS/SSL em linha e ferramentas como proteção avançada contra ameaças, isolamento do navegadore sandbox na nuvem para evitar perda de dados e movimentação lateral.
O Zscaler Risk360™ capacita ainda mais as organizações ao quantificar riscos com insights práticos, fornecer relatórios prontos para a diretoria e priorizar a correção com base em fatores de risco granulares. Essas soluções garantem que as ameaças internas sejam identificadas, avaliadas e mitigadas proativamente. Para interromper as ameaças internas antes que elas aumentem, o Zscaler ITDR™ (detecção e resposta a ameaças de identidade) oferece monitoramento contínuo de sistemas de identidade, detectando ataques como Kerberoasting e escalonamento de privilégios, ao mesmo tempo em que fornece orientação de correção para configurações incorretas de identidade.
Além disso, o Zscaler Deception™ implementa iscas para detectar comportamento malicioso de pessoas internas e movimentação lateral de ameaças, garantindo a detecção precoce e a contenção de ações desonestas. Juntas, essas soluções formam uma estrutura zero trust unificada para proteger dados sigilosos e sistemas críticos contra ameaças internas.
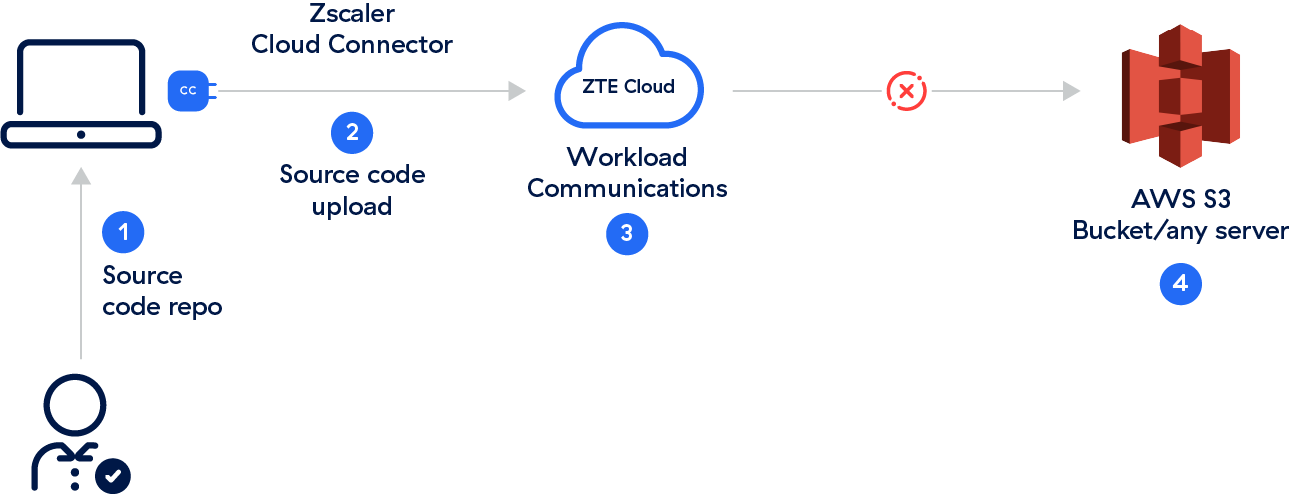
Principais recursos da proteção contra ameaças internas da Zscaler:
- Zscaler Cyberthreat Protection: oferece detecção de ameaças orientada por IA, inspeção de TLS/SSL e ferramentas como sandbox na nuvem e isolamento do navegador para prevenir e detectar atividades maliciosas.
- Zscaler Deception™: implanta iscas e chamarizes que imitam ativos reais para detectar e interromper a movimentação lateral e atividades maliciosas internas de forma eficaz.
- Zscaler Risk360™: fornece uma pontuação de risco abrangente e insights práticos para investigar e corrigir problemas específicos.
- Zscaler ITDR™: oferece monitoramento contínuo de identidade para detectar ataques como DCSync, DCShadow e escalonamento de privilégios, com alertas em tempo real e correção de configurações incorretas.
- Uma arquitetura zero trust unificada: garante acesso de privilégio mínimo, minimizando a superfície de ataque e as oportunidades de ameaças internas.
Ao integrar essas soluções, a Zscaler fornece proteção incomparável contra ameaças internas com uma abordagem proativa e zero trust.
Saber mais e explorar recursos
Perguntas frequentes
Perguntas frequentes
Utilize ferramentas de monitoramento de atividades do usuário, implemente análises comportamentais e realize auditorias frequentes. Treinar funcionários sobre conscientização sobre segurança cibernética também ajuda a identificar ações incomuns que podem sinalizar ameaças internas antes que elas aumentem.
Equilibrar a confiança dos funcionários com o monitoramento é desafiador. As ameaças internas geralmente passam despercebidas devido aos seus privilégios de acesso, tornando essencial impor controles de acesso rigorosos e promover uma cultura de responsabilização.
Sim, setores como saúde, finanças e tecnologia enfrentam cada vez mais ameaças internas devido ao manuseio de dados sigilosos. Esses setores são alvos frequentes de insiders mal-intencionados e também de violações acidentais de dados.
As empresas podem mitigar as ameaças internas implementando modelos de segurança zero trust, monitoramento contínuo do comportamento dos usuários e programas extensivos de treinamento de funcionários.

