Churning through our logs, we recently observed a significant rise in the number of transactions involving the Nuclear Exploit Pack, which has been in the news for quite some time now. In the past week, we stumbled upon thousands of transactions involving the Nuclear Exploit Pack infestation.
We could see the whole exploit chain in our logs and the exploit kit was hosted mainly originating from the following IPs:
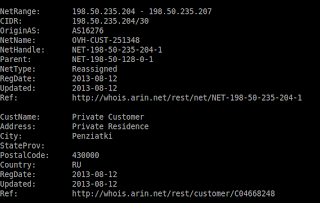
198[.]50[.]235[.]204
198[.]50[.]235[.]203
198[.]50[.]235[.]174
198[.]50[.]235[.]152
198[.]50[.]235[.]36
Whois information on this net block range shows that these IPs are hosted in Russia (no surprises here!).
A few transactions were also found at the IP: 158[.]255[.]6[.]117 (this may be related to a campaign posted by @malwaremustdie).
Some sample referral URLs, which lead to the exploit kit are shown below: fouce[.]paroyourjob[.]info
bluesevs[.]likedating[.]info
datzone[.]onlinesdating[.]info
www[.]jornaiserevistas[.]com
www[.]noticiasaominuto[.]com
www[.]johnjones1[.]com
goodzdatin[.]work4wheelsa[.]info
www[.]tyleroralsurgery[.]com
kempmeek[.]com
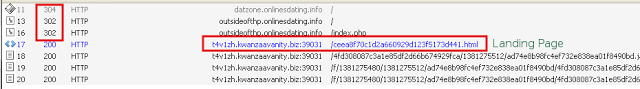
Upon examining one of these infected sites, a typical Nuclear Exploit pack pattern was observed. A series of 304/302 redirects that finally leads to the exploit kit landing page as shown below.
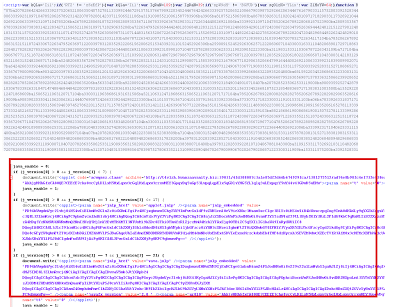
The landing page contained an obfuscated JavaScript payload that was deobfuscated to get the original JavaScript plugin detection and applet/pdf injection code. It was similar to what we typically see from the. Blackhole Exploit Kit.
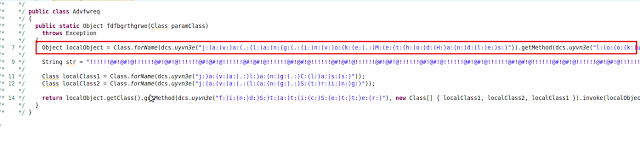
The applet is used to make a call to the malicious jar file which uses CVE-2013-2460, as shown here. The following screenshot, shows the JAR file exploiting the vulnerability. The JAR file then downloads and invokes the malicious executable. a recent VT report shows a poor detection ratio for the JAR file. We managed to collect 19 malware samples that were dropped by this exploit kit. Most of them were Spyeye/Zbot drops, Ransomware, W32.Caphaw, Injection Trojan, Proxy Trojan, Keylogger, Spam Bot etc. The following reports detail the malware found:
https://www.virustotal.com/en/file/36eec2b80586211f14bd7f9af3dc68afec629fc9f3071933e959570ac58d87be/analysis/1382745996/
https://www.virustotal.com/en/file/beb0f5929f886a505b31a98f6ae9b4b02bb303088f1c8ecd74ef6516189e4248/analysis/1382746009/
https://www.virustotal.com/en/file/45b3e40cb392489251dec6b24f575c4281570f427b83a6d4d983c86ace35fc7e/analysis/1382746036/
https://www.virustotal.com/en/file/4b708d1ee0d0bac61825ed9ede005978a5610d60fce27b69c2b862fd65e2c07e/analysis/1382746051/
https://www.virustotal.com/en/file/f2219983385daa9d1fadb144088f84d154775dca3002f82e855897f7e8b40d04/analysis/1382746068/
https://www.virustotal.com/en/file/2bb3bc2ebf299d853ddff54c142849882dfa6fc9fa32620cf2ddd01507606e8e/analysis/1382746101/
https://www.virustotal.com/en/file/0d7feaa9595c23828b1d1e7ca898da9a694b151b0a8c87350e001e8f8b7e3fb8/analysis/1382746122/
https://www.virustotal.com/en/file/42d8cb1b05b6d9ed5adabfb2f3184738378b4bbf72b39139bab37de764e99b4a/analysis/1382746135/
https://www.virustotal.com/en/file/d671fd25f75323d74621c6c9e520dd84f64b2ed2588a58838e65283e9067b8c9/analysis/1382746303/
https://www.virustotal.com/en/file/fecdc7eb44508a80e548955945737e2739ec2a6f9f8c4c05d35869a73f82ec2c/analysis/1382746155/
https://www.virustotal.com/en/file/288fae8c7a7f34e36e1ace80fd73392cffc83e53dfdb1961252296692499463e/analysis/1382746167/
https://www.virustotal.com/en/file/b94e93b4b25b1ff7d0dbc8aa3f6c5af80ee0afc4005eddb52d364a59ab8e308a/analysis/1382746305/
https://www.virustotal.com/en/file/8b543c1cce54aec0b6c4b85102bb2a5ffa7f10e69dab19a8812d7b069e84ee5d/analysis/1382746188/
https://www.virustotal.com/en/file/5f84ab5ac0548d2257084e6542d7fd5678bf3f8175f0b8c6e9098a3187f7e4bb/analysis/1382746200/
https://www.virustotal.com/en/file/cbb32fba48f0029b1e6191130b0e68fe44c8364303badd8fc485a1c4d7bf4fc7/analysis/1382746211/
https://www.virustotal.com/en/file/233d56bd1d40608c6302760b4920a4b9daf60df7e32f23fd9f5210603dcb313a/analysis/
https://www.virustotal.com/en/file/2d7df365e65a9415611411aa44c8ed6d7439bfa3c2dfbf21afaff3fd520a79e3/analysis/1382746237/
https://www.virustotal.com/en/file/02e440ccb37a82b3fea48c03849af40ed9110069b555b50f3fa79945dd7caa08/analysis/1382746252/
https://www.virustotal.com/en/file/93167da47833a257ac2d231e10d0b8f8d1f33c4727521fb5bcf6a189522f3e0f/analysis/1382746259/
Java, software that runs on over one billion devices and is even used to authorize/authenticate tokens in banking applications, continues to be exploited. The Nuclear Pack follows this same pattern, as the authors have taken a recent Java CVE and crafted it into the exploit kit. It is always advisable to disable java on your computer to prevent falling victim to an attack that leads to credential leakage, information theft and becoming a bot. Stay safe and happy Browsing!
We could see the whole exploit chain in our logs and the exploit kit was hosted mainly originating from the following IPs:
198[.]50[.]235[.]204
198[.]50[.]235[.]203
198[.]50[.]235[.]174
198[.]50[.]235[.]152
198[.]50[.]235[.]36
Whois information on this net block range shows that these IPs are hosted in Russia (no surprises here!).
A few transactions were also found at the IP: 158[.]255[.]6[.]117 (this may be related to a campaign posted by @malwaremustdie).
Some sample referral URLs, which lead to the exploit kit are shown below:
bluesevs[.]likedating[.]info
datzone[.]onlinesdating[.]info
www[.]jornaiserevistas[.]com
www[.]noticiasaominuto[.]com
www[.]johnjones1[.]com
goodzdatin[.]work4wheelsa[.]info
www[.]tyleroralsurgery[.]com
kempmeek[.]com
Upon examining one of these infected sites, a typical Nuclear Exploit pack pattern was observed. A series of 304/302 redirects that finally leads to the exploit kit landing page as shown below.
The landing page contained an obfuscated JavaScript payload that was deobfuscated to get the original JavaScript plugin detection and applet/pdf injection code. It was similar to what we typically see from the. Blackhole Exploit Kit.
The applet is used to make a call to the malicious jar file which uses CVE-2013-2460, as shown here. The following screenshot, shows the JAR file exploiting the vulnerability. The JAR file then downloads and invokes the malicious executable. a recent VT report shows a poor detection ratio for the JAR file.
https://www.virustotal.com/en/file/36eec2b80586211f14bd7f9af3dc68afec629fc9f3071933e959570ac58d87be/analysis/1382745996/
https://www.virustotal.com/en/file/beb0f5929f886a505b31a98f6ae9b4b02bb303088f1c8ecd74ef6516189e4248/analysis/1382746009/
https://www.virustotal.com/en/file/45b3e40cb392489251dec6b24f575c4281570f427b83a6d4d983c86ace35fc7e/analysis/1382746036/
https://www.virustotal.com/en/file/4b708d1ee0d0bac61825ed9ede005978a5610d60fce27b69c2b862fd65e2c07e/analysis/1382746051/
https://www.virustotal.com/en/file/f2219983385daa9d1fadb144088f84d154775dca3002f82e855897f7e8b40d04/analysis/1382746068/
https://www.virustotal.com/en/file/2bb3bc2ebf299d853ddff54c142849882dfa6fc9fa32620cf2ddd01507606e8e/analysis/1382746101/
https://www.virustotal.com/en/file/0d7feaa9595c23828b1d1e7ca898da9a694b151b0a8c87350e001e8f8b7e3fb8/analysis/1382746122/
https://www.virustotal.com/en/file/42d8cb1b05b6d9ed5adabfb2f3184738378b4bbf72b39139bab37de764e99b4a/analysis/1382746135/
https://www.virustotal.com/en/file/d671fd25f75323d74621c6c9e520dd84f64b2ed2588a58838e65283e9067b8c9/analysis/1382746303/
https://www.virustotal.com/en/file/fecdc7eb44508a80e548955945737e2739ec2a6f9f8c4c05d35869a73f82ec2c/analysis/1382746155/
https://www.virustotal.com/en/file/288fae8c7a7f34e36e1ace80fd73392cffc83e53dfdb1961252296692499463e/analysis/1382746167/
https://www.virustotal.com/en/file/b94e93b4b25b1ff7d0dbc8aa3f6c5af80ee0afc4005eddb52d364a59ab8e308a/analysis/1382746305/
https://www.virustotal.com/en/file/8b543c1cce54aec0b6c4b85102bb2a5ffa7f10e69dab19a8812d7b069e84ee5d/analysis/1382746188/
https://www.virustotal.com/en/file/5f84ab5ac0548d2257084e6542d7fd5678bf3f8175f0b8c6e9098a3187f7e4bb/analysis/1382746200/
https://www.virustotal.com/en/file/cbb32fba48f0029b1e6191130b0e68fe44c8364303badd8fc485a1c4d7bf4fc7/analysis/1382746211/
https://www.virustotal.com/en/file/233d56bd1d40608c6302760b4920a4b9daf60df7e32f23fd9f5210603dcb313a/analysis/
https://www.virustotal.com/en/file/2d7df365e65a9415611411aa44c8ed6d7439bfa3c2dfbf21afaff3fd520a79e3/analysis/1382746237/
https://www.virustotal.com/en/file/02e440ccb37a82b3fea48c03849af40ed9110069b555b50f3fa79945dd7caa08/analysis/1382746252/
https://www.virustotal.com/en/file/93167da47833a257ac2d231e10d0b8f8d1f33c4727521fb5bcf6a189522f3e0f/analysis/1382746259/
Java, software that runs on over one billion devices and is even used to authorize/authenticate tokens in banking applications, continues to be exploited. The Nuclear Pack follows this same pattern, as the authors have taken a recent Java CVE and crafted it into the exploit kit. It is always advisable to disable java on your computer to prevent falling victim to an attack that leads to credential leakage, information theft and becoming a bot. Stay safe and happy Browsing!