Zscaler ThreatLabZ has been tracking the usage of malicious RTF documents that leverage CVE-2017-8570 and more recently CVE-2018-0802 vulnerability exploits to install malicious payload on the victim machine. In this blog, we'll share our analysis of a campaign leveraging these two exploits to deliver LokiBot.
These malicious documents spread by using phishing emails to trick users into opening and executing them.
Fig 1: Malicious documents weaponized with exploits to infect target machine
An example of a phishing spam email with an attached malicious RTF document is shown below.
Fig 2: Phishing spam email with attached malicious RTF document
In case of the LokiBot spreading campaign we saw that these documents were either weaponised with CVE-2017-8570 or CVE-2018-0802 exploit paylods.
The workflow of both exploits is shown in the below.
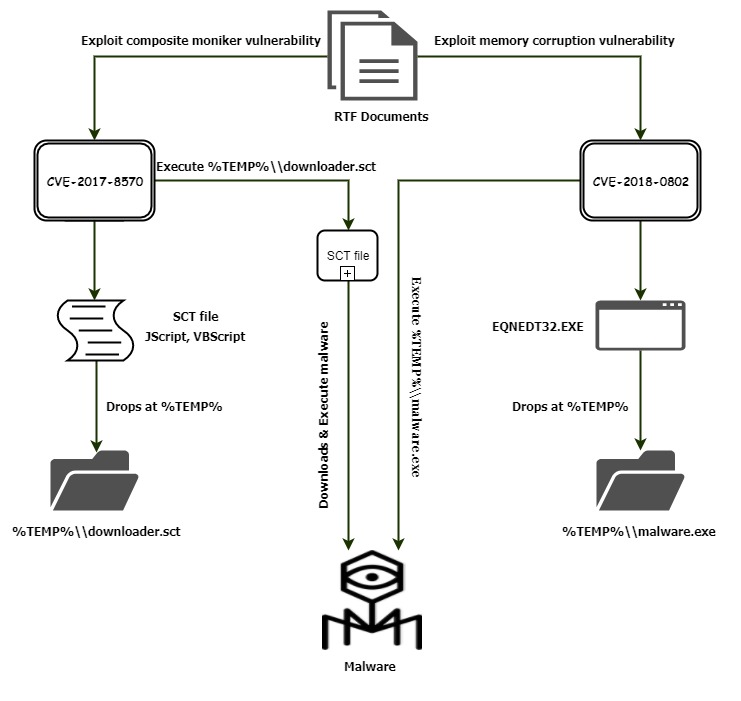
Fig 3: Workflow of CVE-2017-8570 and CVE-2018-0802
CVE-2017-8570
This exploit bypasses the Microsoft patch for CVE-2017-0199. It makes use of a composite moniker in the RTF file to execute a Windows Script Component (WSC) file or scriptlet on the victim’s machine. A scriptlet is a XML file wrapping a script like VBScript, JavaScript, etc.
The RTF document uses a Packager.dll trick to drop an SCT file into the %TEMP% directory and execute it using the escalated privilege that the vulnerability provides.
The document has two objdata encoded and embedded in it, as shown below.
Fig 4: Objdata1 “Package” ActiveX control
01050000 02000000 = OLE object
08000000 = Length of following string
5061636B 61676500 = ActiveX name “Package”
CB060000 = Data length of following binary data
Upon executing the RTF file, the embedded SCT file is dropped in the %TEMP% directory with the name V2BRUIICCL75CPT.sct.
This SCT file will be executed by a second objdata in the RTF document.
Fig 5 : Objdata2 “OLE2Link” leveraging composite moniker
The RTF has a composite moniker, file moniker, and new moniker working together.
The byte sequences shown in the Fig 5 are the binary representation of following CLSID.
{00000309-0000-0000-C000-000000000046} = Composite moniker
{00000303-0000-0000-C000-000000000046} = File moniker
{ECABAFC6-7F19-11D2-978E-0000F8757E2A} = New moniker
After the file moniker CLSID, there is a length field followed by the file path, which is going to execute the new object persisted in “%TMP%\V2BRUIICCL75CPT.sct”.
In short, this object will execute the file by using composite moniker in the RTF document.
The dropped SCT file looks like the screen capture below.
Fig 6: %TEMP%\\V2BRUIICCL75CPT.sct
This SCT file is dropped and executed by the RTF document. The SCT file has JavaScript, which downloads malicious executable price.exe from juanjoseriffo[.]com/ed/price.exe, saves it to %APPDATA% with name windowsis.exe, and executes it.
CVE-2018-0802:
This exploit is a CVE-2017-11882 patch bypass vulnerability of type stack overflow. This vulnerability will only work on systems updated with CVE-2017-1182 patch.
The logic behind this loophole is similar to the remote code execution vulnerability (CVE-2017-11882) using office embedded formula editor EQNEDT32.EXE.
Fig 7: RTF file exploiting CVE-2018-0802
The first object data of the document file is using Packager.dll to drop the file into the %TEMP% directory. The malicious executable file, having the length 0x000868B6, will be dropped in the %TEMP% directory with the name price.exe.
Like CVE-2017-11882, the actual data for this vulnerability is in the equation native stream of the OLE object, which is shown in the below image.
Fig 8: Equation native stream of OLE object in RTF document
The dropped file %temp%\price.exe will be executed via the Microsoft Windows command shell.
LokiBot:
The malicious executables dropped by the RTF documents, leveraging the above two exploits, are from LokiBot family. LokiBot is a malware capable of stealing user's private data including stored credentials and cryptocurrency wallets. The stolen information is relayed back to the Command & Control (C&C) server. The LokiBot malware payloads seen in this campaign were compiled using Borland Delphi and were UPX packed.
Upon execution, the malware copies itself to the startup folder at “%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup.” to ensure persistence on system reboot.
After that, the sample reads the machine GUID from the registry key HKEY_LOCAL_MACHINE\SORTWARE\Microsoft\Cryptograpy\MachineGuid using RegOpenKeyEx and RegQueryValueEx Functions.
Fig 9: Obtaining machine GUID
Once the machine GUID is obtained from the registry, LokiBot calculates the MD5 hash of the machine GUID by calling CryptAcquireContext, CryptCreateHash, CryptHashData, and CryptGetHashParam APIs.
The sample trims the MD5 hash of the machine GUID to 24-charachters and creates a mutex with this name as seen below.
Fig 10: Mutex creation
The purpose of mutex is to ensure that only one payload of LokiBot is running on the infected system.
Information Stealing module
Once installed, Lokibot is capable of stealing stored credentials and other private information from the following applications:
- Mozilla Firefox
- Opera
- Apple Safari
- Internet Explorer
- Google Chrome
- Chromium
- Easy FTP
- DeluxeFTP
- WinSCP
- Outlook
- CheckMail
- Filezilla
- NetDrive
- myFTP
- Putty
- 360 Browser
- KeePass, and more
LokiBot creates a hidden directory in %APPDATA% where the directory name is string extracted from 8th through 13th characters of the Mutex name. It creates four files in the hidden directory at the running time, all of which are named using string extracted from 13th through 18th characters of the Mutex name.
Fig 11: Files created by LokiBot
File descriptions:
.exe - Copy of malware that will execute every time when user logs in
.hdb - Database of hashes of data that has been sent to C&C server
.kdb - Keylogger data that has to be sent to C&C server
.lck - Lock file created to prevent resource conflicts
After all the target applications have been profiled for stored credentials, LokiBot prepares harvested data and sends it to the C&C server.
Fig 12: POST request to C&C server
Fig 13: First data sent to C2 server
The information transmitted by LokiBot contains system information, application data, Windows credentials, cryptocurrency wallet, keylogger data, screenshots etc. It will send a request every 10 minutes to the C&C server requesting C&C commands, and the malware acts in accordance with the C&C commands.
Zscaler Protections:
Microsoft released security updates for CVE-2017-8570 and CVE-2018-0802.
Zscaler detects these malicious RTF documents as “CVE-2017-8570” and “CVE-2018-0802”.
Zscaler detects LokiBot payloads as “Win32.PWS.Lokibot”.
The Zscaler Cloud Sandbox report for this threat can be seen below.
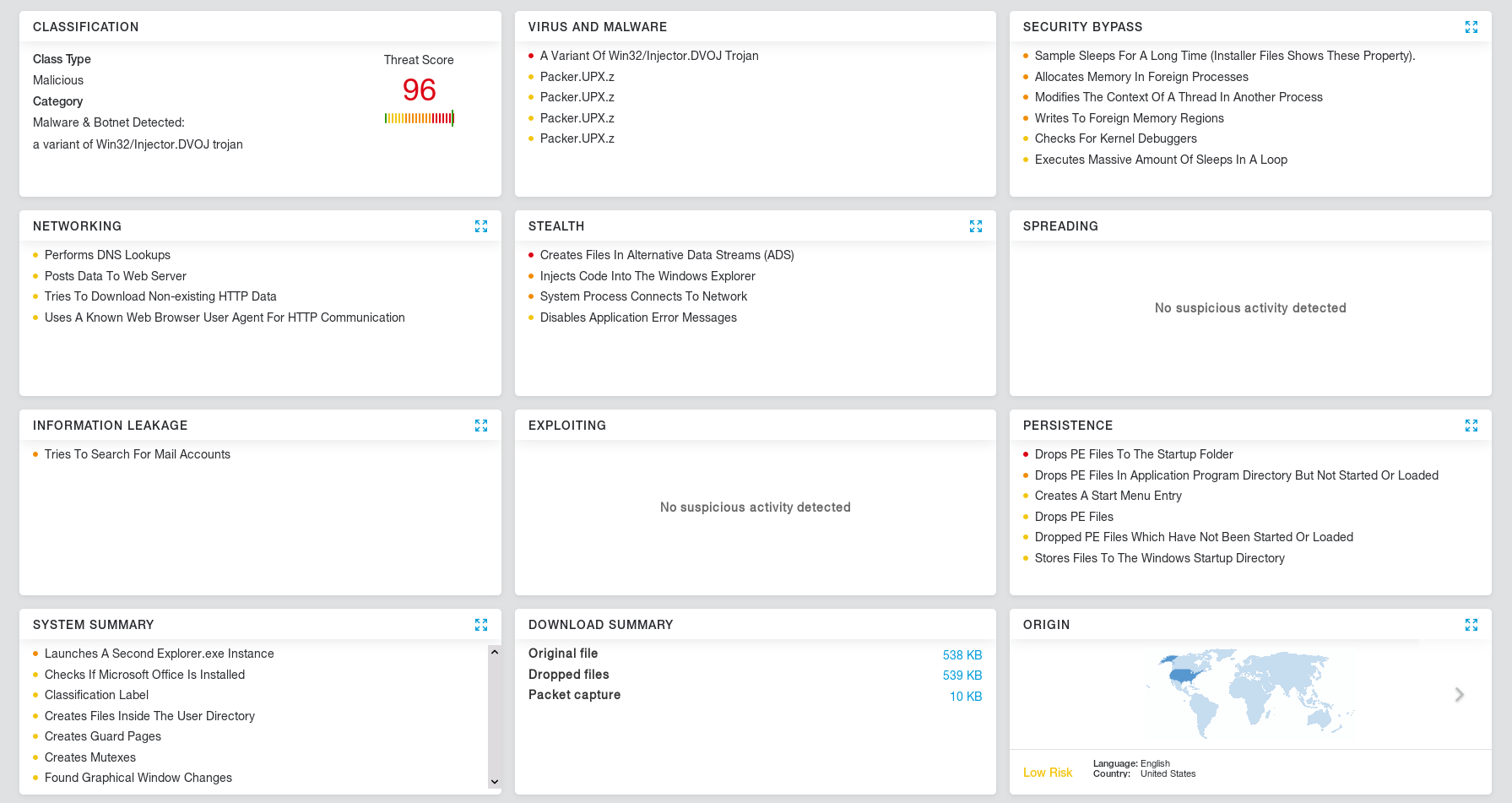
Fig 14: Zscaler Cloud Sandbox LokiBot report
IOCs:
MD5 : [CVE-2017-8570 & CVE-2018-0802]
A63D162C20A1ACA48F70FAAE80A0F1DE
B94D468D389F65C2BA48ECEF422EF7BA
1C633806DE81C9181DA572CE40E32254
9D76516A8212641A83B62DD152AED8D9
98AF7F0B4B7DB96AC2A18786D50C6979
C0A2F49FA6FF98FBDAE0A9B21E40D6D3
C33B99043E9C3FC4E8E678365D7F1C7D
3F54763388A88AA66CF3FCE564B9B12F
F1B3A174A2849605694372C6010AEB87
E1921789F0A834A1183D73542D53BB9D
FA45C8D1FBAE6E160CB848497717CB53
MD5 : [LokiBot]
C2471F6F9736994942D50D176DDC4E6D
558B7CBE06972081568F8F634E0226FB
FC8E0D4BBF779D6AFCC4FD3E1213BB5D
FF6DBE6B48CF118DF6449A1BA62D3F7F
E90AB350B42205B06E33441A6B782659
4195192B66A50FD0641019F634D2C86C
EAF119844AEDA0E40A87995786D5C44C
AC26ECE0774DB979D672890F4C2F6F88
CEF9679A154D5290C0BD58B6CE765982
ABD6554A587CAF338AB4CD514EA2D3FF
Network:
juanjoseriffo[.]com/ed/price.exe
sariraatjgaye[.]com/edu/fre.php
31.3.230[.]31/bin/chi.exe
grernont[.]com/Chisom/five/fre.php
b.reich[.]io/pjrazz.exe
b.reich[.]io/vncqoy.exe
b.reich[.]io/ymqrza.exe
192.189.25[.]114/dew1/fre.php
192.189.25[.]17/guy2/fre.php
fiebiger[.]us/222.exe
umumi[.]xyz/222.exe
umumi[.]xyz/js2.exe
adimm[.]xyz/onyem/fre.php
umumi[.]xyz/shaq1.msi
umumi[.]xyz/zu/fre.php
adimma[.]xyz/ben66.msi
adimma[.]xyz/benji/fre.php
klk[.]host/2018/iy.exe
klk[.]host/2018/li.exe
klk[.]host/2018/pa.exe
klk[.]host/iykesettings/settings/settings/settings/settings/settings/fre.php
20dollars[.]co/assetss/css/images/open/eric.exe
extrainformativo.com[.]au/wp-content/themes/travelify/library/font/Gen/fre.php
lemonwood.co[.]za/wp-admin/css/colors/blue/main/shoe.exe
kbfvzoboss[.]bid/alien/fre.php

















