/ What Is DevSecOps?
What Is DevSecOps?
DevOps vs. DevSecOps
DevOps and DevSecOps both use automation and continuous processes to establish collaborative development cycles. DevSecOps emerged as a response to criticism that DevOps failed to appropriately emphasize cybersecurity.
In the DevOps methodology, developers and IT operations teams work together to create an agile, streamlined deployment framework. DevSecOps aims to automate key security tasks by embedding security controls and processes in the DevOps workflow. DevSecOps practices extend the DevOps culture of shared responsibility to include security practices.
Why Is DevSecOps Important?
Short for development, security, and operations, DevSecOps helps enterprises integrate security across application development by implementing security controls at each stage of the development life cycle. Finding and fixing security issues as early as possible helps save costs, avoid rework, and reduce risk by ensuring cloud workloads are secure before they’re deployed.
What Is the Purpose of DevSecOps?
DevSecOps helps streamline modern development environments and supports secure digital transformation. Enterprises are adopting cloud native services, employing automation, and refining iterative development processes. Devs often rely on reusable code and open source components. On top of that, sensitive data has become highly regulated.
Alongside the evolving threat landscape, all this complexity puts pressure on security teams as they cope with finite expertise, resources, and tools.
DevSecOps drives more efficient security practices, offering deep visibility enriched with full context and integration into devs’ tools and processes, paired with unified security across cloud infrastructure, confidential data, and applications.
Fundamentally, DevSecOps processes help deliver secure software, stopping security issues before they start in the software delivery process by:
- Finding and fixing issues early in development to avoid costly breaches, vulnerabilities, and compliance violations down the line
- Taking an integrated approach to life cycle security by streamlining processes between teams to avoid friction and reduce risks
- Integrating security into the continuous integration/continuous delivery (CI/CD) pipeline instead of leaving it until the end
- Helping Devs and DevOps understand how their releases and changes affect security to speed up development/iteration while staying secure
As part of addressing these challenges, DevSecOps delivers an array of benefits. Let’s look at those next.
What Are the Benefits of DevSecOps?
1. Shift Security Left and Accelerate Innovation
With automated security controls embedded in popular IDEs and DevOps tools, developers can easily meet the requirements of DevSecOps environments. These controls help devs identify, investigate, and remediate code vulnerabilities early in development with best practices and guided remediation.
2. Reduce Costs and Complexity
An effective DevSecOps strategy consolidates multiple functions—such as CSPM, CIEM, CWPP, and infrastructure as code (IaC) and vulnerability scanning—in a single CNAPP solution. It also helps your teams find and fix issues earlier in the development process, which reduces rework and patching, saves time and money, and reduces your risk of a breach.
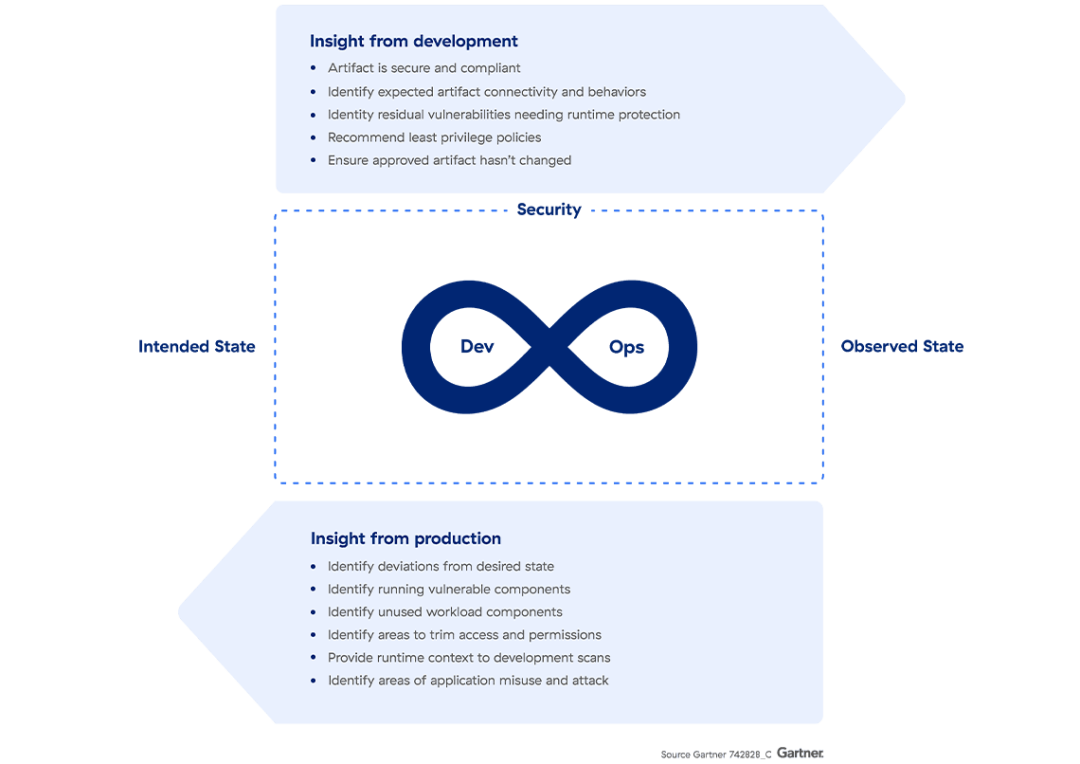
Figure 1: Bidirectional feedback
Source: Gartner, Innovation Insight for Cloud-Native Application Protect Platforms
Neil MacDonald, Charlie Winckless, 25 August 2021
3. Gain Complete Coverage and Control
DevSecOps provides complete visibility and coverage with granular controls to help secure native apps, cloud infrastructure, and confidential data. Effective DevSecOps tools help identify and correlate issues, events, and hidden attack vectors as well as generate real-time alerts, recommendations, and remediation guidance.
4. Enhance Collaboration and Communication
Development, security, and operations teams tend to work in silos. DevSecOps brings them together on one platform so that every component and configuration in the stack is compliant, patched, and configured securely. Better communication and collaboration help your security team implement guardrails for devs to incorporate in their work, reducing cross-team friction.
How Does DevSecOps Work?
Modern CI/CD tooling allows security checks to be baked into the DevOps process at Code, Check-in, Build, Test, Deploy, and Monitor. CNAPPs enable security teams to implement gates and guardrails that can be integrated into any DevOps pipeline, enabling visibility for every software, DevOps, and security engineer. This is called a DevSecOps pipeline.
Your security team can integrate security gates at various stages of the CI/CD process:
- Code: Integrate IaC scanning abilities here to give developers visibility and guidance on following secure coding standards.
- Check-in: Scan every pull and change request for vulnerabilities and data leakage to ensure code is clean and compliant before it enters build and test.
- Build and Test: Scan for open source vulnerabilities and licenses, alongside with functional and unit testing, to protect intellectual property rights and prevent zero-day vulnerabilities.
- Artifacts: Once code is pushed to the central registry, enable vulnerability scanning, auditing, and access scanning to prevent zero days, unauthorized access, and rogue or unsigned packages.
- Deploy: Once certified and signed images from the registry are deployed for testing, simulate attacks on the application and project the exploitable risks it may contain.
- Monitor: Continuously collect, process, and correlate runtime signals across various building blocks of the application in order to develop and deploy security guardrails to prevent further issues.
Read The Role of Security in DevOps Architecture to learn more.
What Are the Challenges of Implementing DevSecOps?
Managing Environmental Complexities
Most enterprises rely on multiple public clouds. Using only individual providers’ native security controls leads to limited visibility, security silos, inconsistent security, and fragmented reporting. Meanwhile, DevOps environments combine various platforms, coding languages, and open source components. Within these environments, credentials, tokens, and SSH keys are openly shared among apps, containers, and microservices.
Security teams need granular controls to address complex environments without impacting performance.
Moving Beyond Point Solutions
DevOps teams need a comprehensive view of their environment and risks to resolve issues and deliver secure code. Many security teams use multiple single-purpose tools to provide that coverage, and then instead of focusing on delivering great software, must cope with correlating results from these disparate tools, determining remediation priorities, and suffering alert fatigue.
Retiring point solutions in favor of a holistic approach means getting buy-in from your teams on taking the leap.
Navigating Cross-Team Operational Challenges
Rapid release cycles can lead to mistakes like configuration errors, which can turn into major security risks. In traditional waterfall development, security testing happens after the development stage, before the application goes into a production environment. This can be time-consuming, and security teams often can’t keep up because of limited expertise, budget, and resources.
You’ll need to focus on training and filling knowledge gaps among your teams as you move to DevSecOps.
Fostering Collaboration and Communication
The biggest hurdle to DevSecOps culture is your teams’ security culture. DevOps teams are under pressure to keep up speed, and they’re used to security slowing them down. They often have limited knowledge of security and risk mitigation best practices, compliance requirements, and the consequences of violations. Security teams, on the other hand, are mostly concerned with securing apps, code, infrastructure, and data.
In other words, diverging goals can make it difficult for your teams to work together. You need to unify their goals and show them the long-term, cross-team benefits of DevSecOps.
Read The Top Challenges Faced by Organizations Implementing DevSecOps to learn more.
What Are the Steps to Implementing DevSecOps?
So, in practical terms, how do you make DevSecOps happen? Start with these five steps:
1. Outline a Unified Approach
To keep commits and releases on track without sidelining security, you need to make your security, operations, and development teams aware of each other’s processes, and you need clearly defined security and compliance requirements. Keeping your devs informed about security best practices, violations, incidents, and guidance helps with timely remediation.
2. Adopt a “Shift Left” Strategy
Security has to start early in development, not get tacked on at the end. Implementing security policies for code analysis helps devs deliver secure code. Integrate a security solution in your developers’ existing workflows that supports different languages and IDEs. This will help the team find and fix issues before they reach production.
3. Assess Vulnerabilities
Developers regularly install and build upon third-party code dependencies, which can come from unknown or untrusted sources. Security must be plugged into an existing CI/CD pipeline to perform critical review as well as scan early and often for security vulnerabilities.
4. Manage Threats
Exploits and attacks are constantly evolving, and continuous monitoring can save you from a breach. Your security team should use automated security checks to scan and monitor your cloud environments and apps for attacks or leaks as well as identify, investigate, prioritize, and remediate threats or vulnerabilities.
5. Continuous Compliance Assurance
DevOps environments constantly shift as new code is created or existing source code is changed. Integrated automated compliance validation and reporting throughout DevOps processes will help your teams move faster, and reliable controls will ensure compliance and simplify regulatory audits.
Zscaler Posture Control for DevSecOps
To effectively secure your apps and data in the cloud, you need continuous automated risk assessment and security tightly integrated into your apps and infrastructure. A traditional security approach, with static and siloed security tools, can’t keep today’s mission-critical applications, sensitive data, and infrastructure safe.
Zscaler Posture Control™ helps implement DevSecOps in the enterprise, delivering a centralized approach to securing cloud infrastructure, sensitive data, and native applications deployed across multicloud environments while reducing complexity, cross-team friction, and overhead.
Core Capabilities
- Comprehensive coverage in one platform: Reduce complexity and overhead by replacing multiple point products with a unified platform that helps your team identify critical issues to focus on first.
- Advanced threat and risk correlation: Improve SecOps efficiency with smart policies and controls that detect risky misconfigurations or activities that can become dangerous attack vectors.
- Cloud estate, risk, and compliance discovery: Identify risks and noncompliance earlier across your multicloud footprint and IDEs. Maintain workflows via native integration with popular IDEs and DevOps tools.
- Deployable in minutes, no agents required: Take an API-based approach to protect all workloads and data across multicloud environments without forcing your devs to install agents.
- Full life cycle cloud security: Find and fix security issues early in dev, before they hit production. Monitor, alert, and block deployment processes when critical issues are found.
- Data protection for public clouds: Identify and protect sensitive data at rest or in motion with DLP and threat scanning engines alongside advanced data recognition and classification.
- Continuous compliance assurance: Automatically map cloud security posture to major industry and regulatory frameworks to provide automated, continuous compliance reporting.

