Phishing is an attempt to steal personally identifiable information, such as Social Security numbers, credit card details, date of birth, and other sensitive data. Typically, phishing targets a user with an email containing a link to a website that imitates a legitimate website the user might visit. As users have become savvier about their online practices, the developers of phishing sites have upped their game, too, and many of the sites we see are carefully designed to look like the sites they’re imitating, and clever tactics are used to trick potential victims.
In this blog, we will share some insights from phishing activities blocked across the Zscaler™ cloud. We’ll cover the top brands and categories we are seeing targeted by phishing campaigns, recent examples of campaigns, and some of the tactics being used by threat actors to be more successful.
Types of phishing
There are different types of phishing activity, including:
Spear phishing, in which the phishing attempt is targeted against certain organizations or individuals working for specific companies.
SMiShing, also known as SMS phishing, which involves a message (SMS communication) that targets victims and entices them to click on URLs hosting phishing websites.
Whaling, in which threat actors target high-profile individuals, such as senior executives in a company, most often to gain internal company information that is not public knowledge.
What brands are being targeted?
While it might be easier to spoof the sites of lesser-known brands, where differences wouldn’t be so apparent, the actors trying to steal personal information need to impersonate popular sites for maximum return, raising the odds of snaring a victim. Their phishing sites often feature the biggest brands, and they use a variety of tricks to evade detection, which we’ll describe in this report. Some of the most commonly targeted brands we’ve seen in the recent phishing campaigns can be seen below:
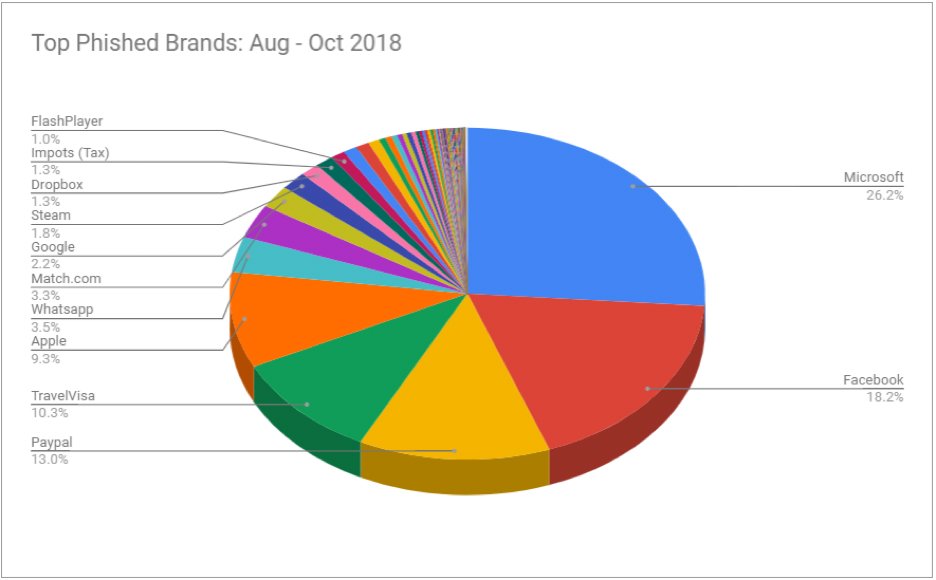
Fig. 1: Top phished brands in the Zscaler Cloud
Microsoft tops the list partly because of Microsoft’s multiple enterprise web properties, such as OneDrive, Office 365, Outlook Web Access, among others, being targeted by the threat actors. Microsoft was followed by Facebook and PayPal in the list. In addition to the known brands, it was interesting to see phishing campaigns targeting Travel Visa portals (Canadian Visa and Australian Visa, for example) included in our top five most targeted brands. The attackers in this case were most likely interested in phishing for sensitive immigration information, such as passport details, date of birth and national identification numbers.
The top five most commonly targeted application categories we saw in the recent phishing campaigns include:
Communications (41.4%)
Social media (18.3%)
Finance (16.7%)
Travel (12.4%)
Dating (3.4%)
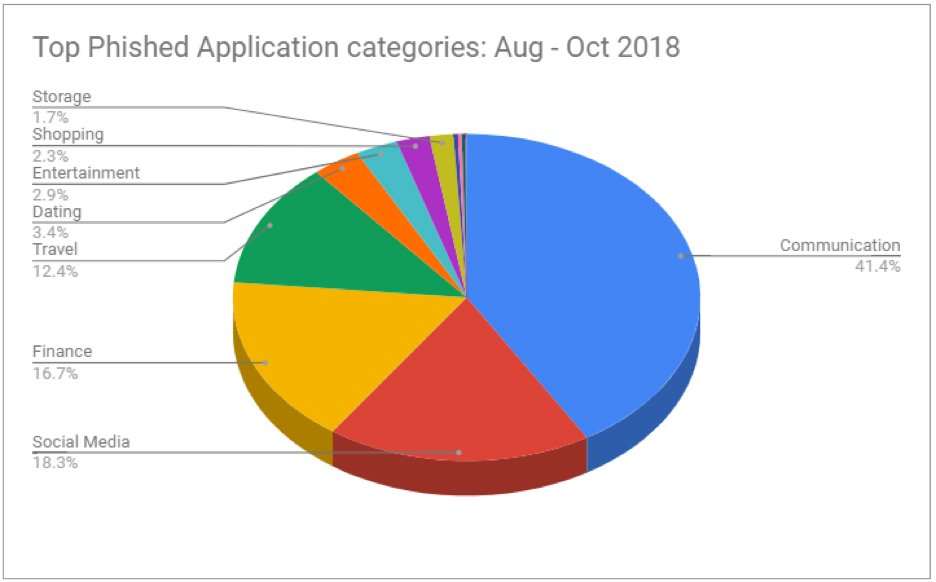
Fig. 2: Top phished site categories in the Zscaler Cloud
Delivery of phishing content
The majority of the phishing campaigns start with an email or message containing a link to a site hosting the phishing page. If the user clicks on the link, the phishing page is delivered. We have seen an increasing number of phishing attempts being delivered over an encrypted channel (HTTPS) -. We believe this increase is most likely due to the availability of domain validated (DV) SSL certificates. These certificates are easy to obtain from free SSL cert providers like Lets Encrypt as well as commercial Certificate Authorities. Multiple commercial CAs also offer free DV SSL certs with shorter validity periods with the expectation that the client will purchase a paid certificate once those expire. However, these offers provide a safe haven for cybercriminals who often leverage these short-term certs to deliver malicious content and then discard them.
About 65 percent of all phishing content we’ve seen in the past three months was over HTTP and the remaining 35 percent was over HTTPS. This represents a 300 percent increase in phishing content being delivered over HTTPS since 2016.
A look at recent phishing examples:
Chalbhai campaign
We continue to see a known phishing campaign using the tag chalbhai in its form statements. This campaign has been targeting users with phishing pages that mimic American Express, Microsoft Office, and Adobe, seasonal campaigns like fake IRS and TurboTax webpages during tax season and more recently holiday shopping season pages. A sample of this tag being used on a Wells Fargo phishing page is shown below.
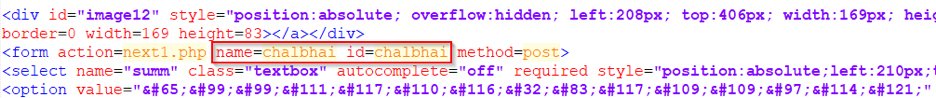
Fig. 3: Chalbhai tag shown in the source code
Usage of compromised sites
Below is an example of a legitimate site that is compromised and the attacker has hosted multiple phishing sites on the compromised domain. The screenshot shows the open directory found on the compromised web server.
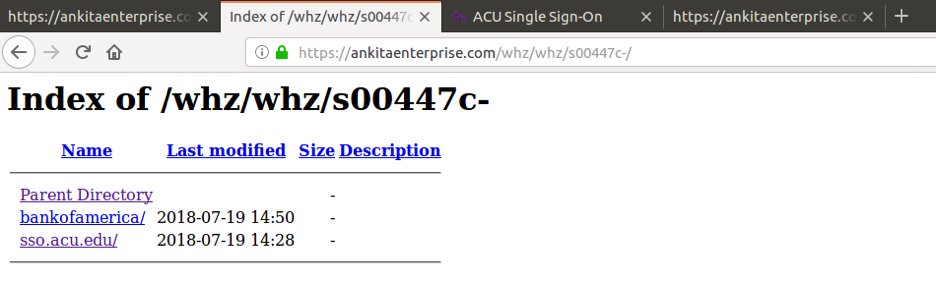
Fig. 4: Compromised web server
The two screenshots that follow are phishing pages designed to look like pages of legitimate websites, including a single sign-on page for Abilene Christian University and a Bank of America page.
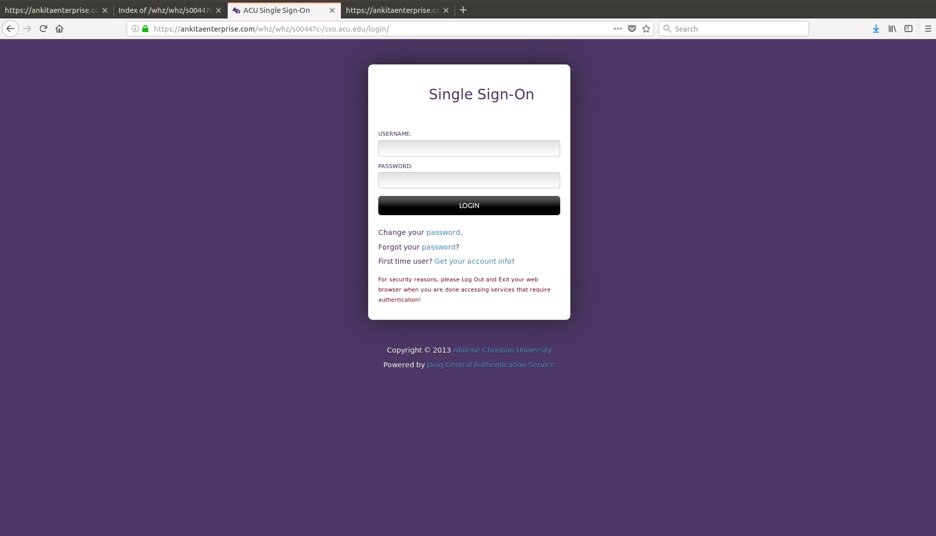
Fig. 5: Faked SSO for Abilene Christian University
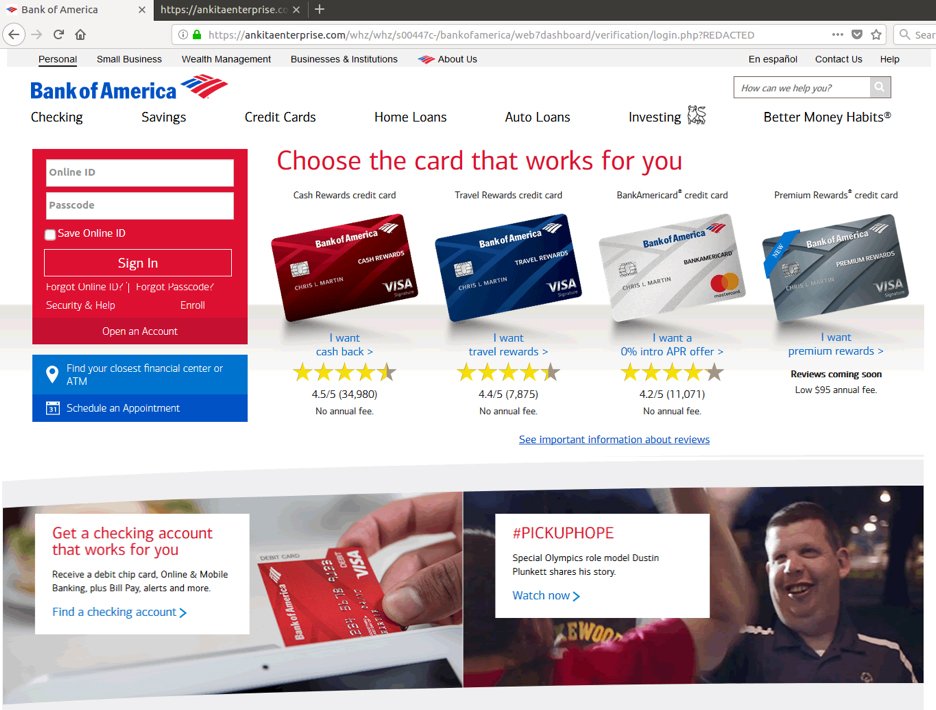
Fig. 6: Faked Bank of America page
If the user falls for these phishing pages, the credentials are harvested and posted to the attacker controlled location.
Evasion and Anti-Analysis Techniques
1. Use of images instead of content
The phishing websites are usually cloned copies of the legitimate sites. The difference in the case of Bank of America is that the faked page is almost entirely made up of a single image with a simple credential login form. This helps to evade engines running heuristics on the page source code.
2. Preventing access to page source
A simple anti-analysis technique used by scammers is disabling the right click functionality to prevent users from checking the page source. This can be seen in the phishing page below, which is pretending to be an Adobe Online document.
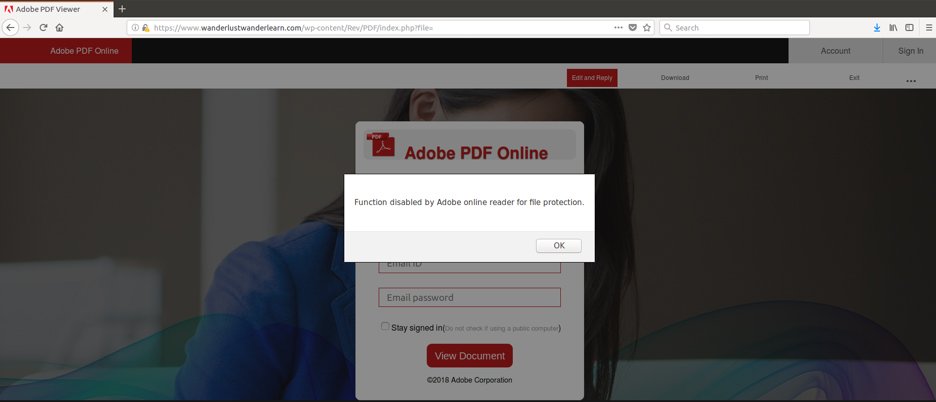
Fig. 7: Malicious Adobe Online document
3. Filtering based on User IP address, Host Names, and User Agent strings involved in the request
We’ve also observed malicious actors trying to fingerprint and serve phishing content based on the user’s IP address, host names, and user agents. We can see an example in the snippet below where the attacker is maintaining a list of IP addresses, hostnames and User-Agent strings known to be used by security researchers and analysts while attempting to get the phishing. If any request to the phishing site arrives from one of the known IP addresses or hostnames, or has one of the listed User-Agent strings then the phishing page will not be served. This tactic helps the attacker to keep the phishing page content undetected for a longer duration.
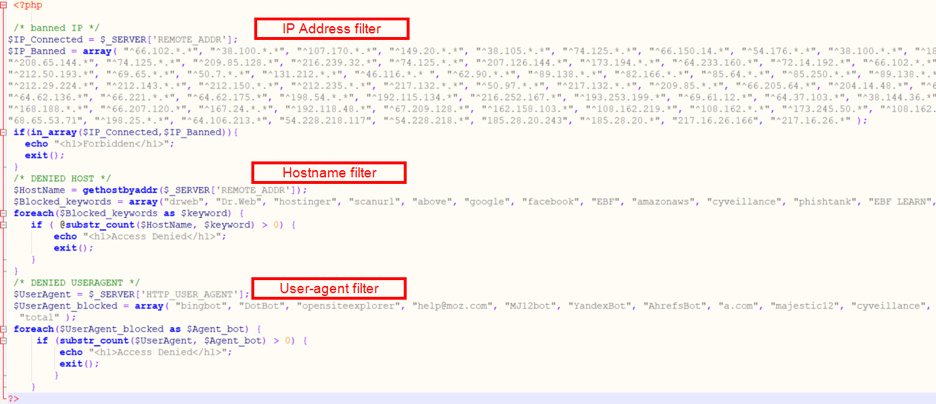
Fig. 8: Banned source IP addresses, hostnames and User-Agent strings
4. Exfiltrating information as an image instead of content
We have also seen multiple instances of phishing attacks that prompt users to verify their identity by asking them to upload a copy of their ID, as shown in the code below.
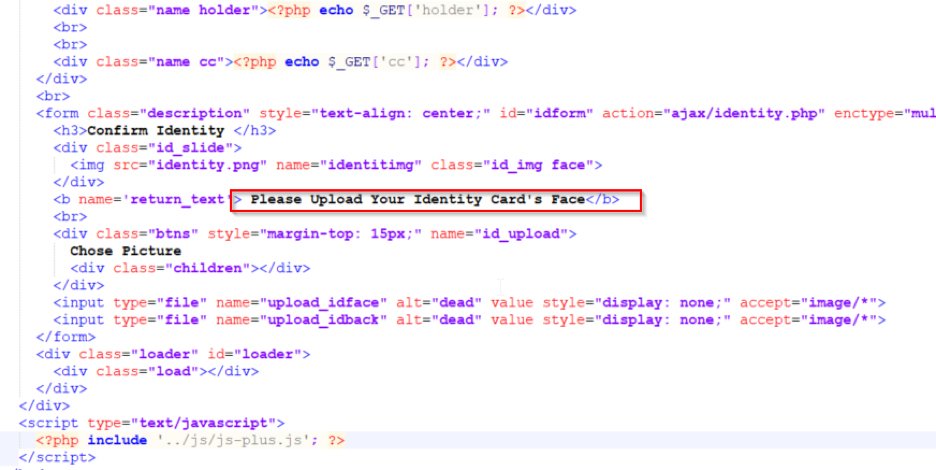
Fig. 9: Coded to prompt users to upload identification card
The sensitive user information in this case is being stolen in the form of an image which will bypass content based data loss prevention engines.
5. Encrypted Phishing
We have also seen a few phishing pages that use encryption to hide the source code in an attempt to evade detection by security engines. One such example, for a faked PayPal page, is shown below.
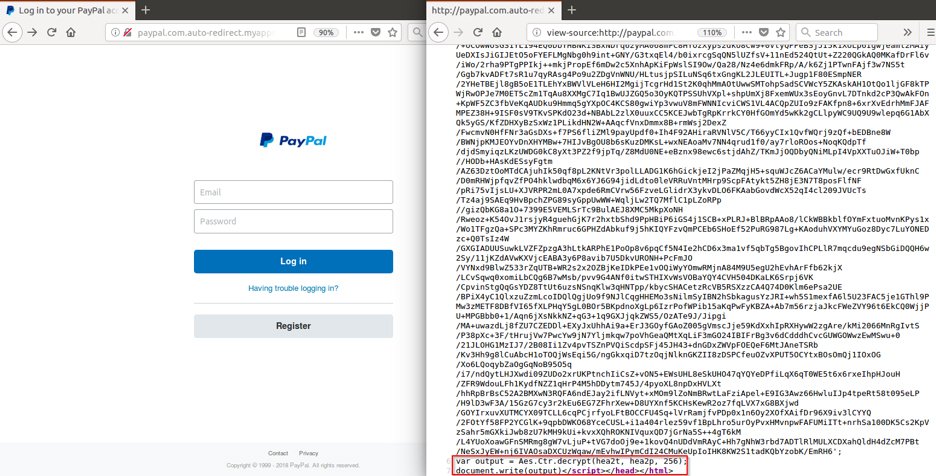
Fig. 10: Encrypted source code for a phishing page
6. Punycode based hostnames
We have also seen attempts to use punycode, in which threat actors use homograph techniques to construct a URL that looks like a legitimate URL, but uses characters in non-English language character sets to trick the user. (See our Punycode blog for examples of this technique.). This technique makes it difficult for reputation based engines to keep up.
Anatomy of Scam Page creation
Let’s now take a look at how typical scam web pages are created to perform financial fraud and phish for sensitive information. Attackers copy website templates to create scam websites making the scam pages look very similar to the original as seen below:
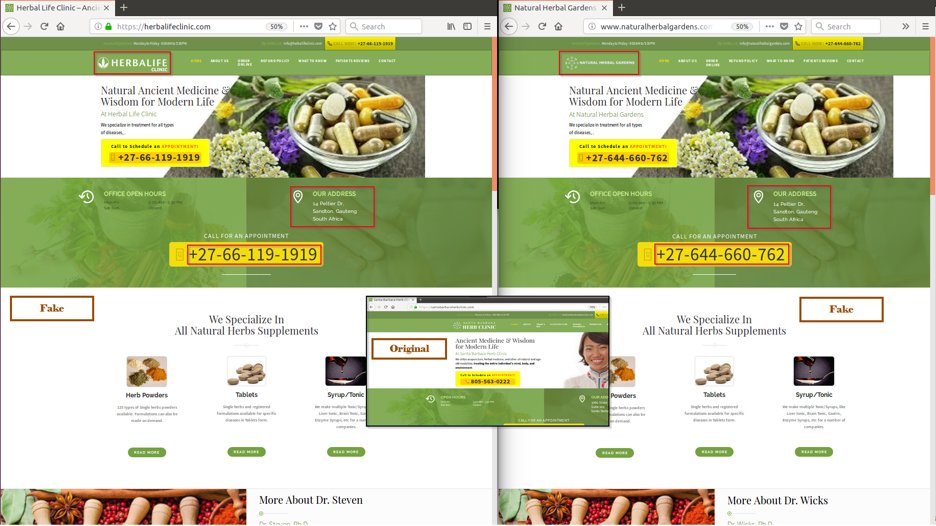
Fig. 11: Scam websites are built using templates to mimic legitimate sites
Most of the time, the fakes would include small changes to evade detection, like changing the names of the doctors on the following page but the site is identical otherwise.
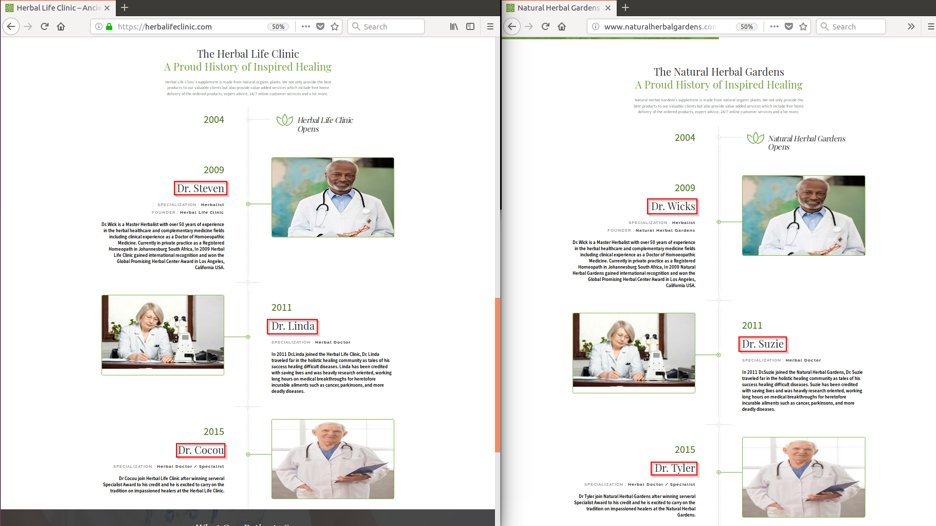
Fig. 12: Small changes that help attackers evade detection
The scam websites even have live chat support, which responds to queries and guides users through the payment process. The photos of doctors were taken from a royalty-free stock photography database. When checking the source code in the Fig 11 example, we found that the contents were copied from a legitimate site, santabarbaraherbclinic[.]com, and we can see the timestamp in the screenshot below.
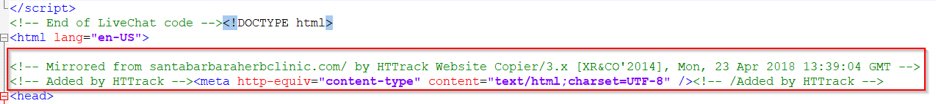
Fig. 13: Source code in scam website shows copied content from a legitimate site
Conclusion
Phishing attacks have been on the rise over the past few years. As the end users become more vigilant against clicking suspicious links, attackers have also upped the ante by evolving the way in which the phishing content is being delivered as well as tactics being leveraged to make the phishing pages stay undetected for longer period.
While in this blog we focused mainly on commodity phishing and scam pages, some of the tactics mentioned here are also commonly seen in many of the targeted phishing campaigns (Spearphishing, Business Email Compromise, etc). ZscalerTM ThreatlabZ actively tracks and ensures coverage against phishing campaigns.




