Cybercriminals keep coming up with new ways to steal and profit from personal user data. Because mobile devices are so prevalent, and so capable, they are becoming the targets of a variety of cyberattacks that were previously limited to computers.
One such attack technique is SMS phishing—SMiShing—in which attacks are delivered via text messages. With SMiShing, mobile users receive links to phishing websites through SMS or chat applications, with text messages luring users to click on links and enter their personal information.
Zscaler ThreatlabZ is seeing more of these SMiShing attacks use “Punycode” to make phishing URLs look like legitimate website URLs. This technique is called a homograph attack. The attacker tries to deceive users by replacing one or more characters in the URL with similar-looking characters from another character script.
The following displays hits that we have seen over last three months for phishing activity on mobile devices targeted with Punycode URLs.
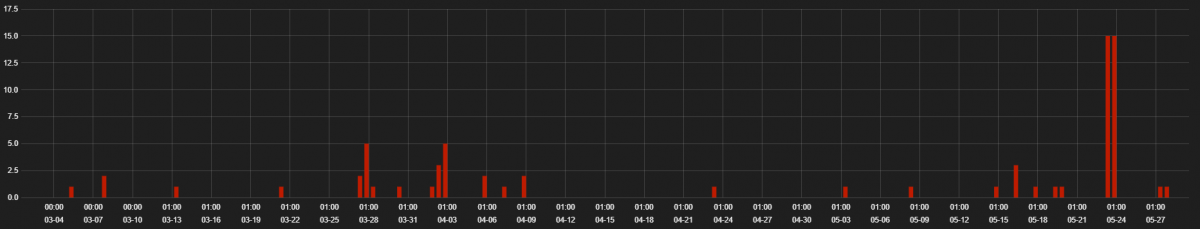
Figure 1: Hits seen for SMiShing activity targeting mobile devices with Punycode URLs from March 1 to May 28, 2018.
Let’s look at a recent example that shows a WhatsApp message pretending to be a link to a Jet Airways offer of free air tickets. The link is designed to look like the actual jetairways.com website, but it is using a homograph attack, in which look-alike characters are used to trick the victims.
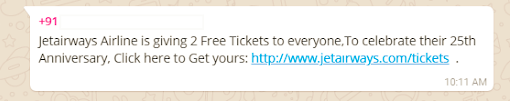
Figure 2: WhatsApp message on a group pretending to be a link for free tickets.
If you look closely at the character “i” in the URL domain label, you can see that it is a homograph from the Latin character set. More precisely, it is a Unicode Character “Latin small letter dotless I” (U+0131) that replaces the letter “i” in “airways.”
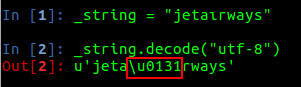
Figure 3: Decoding the homograph domain label.
If the user clicks this link on an iPhone, it opens the Safari web browser and tries to load the phishing website. Notice that the URL looks like jetairways.com; it is difficult to detect that it is not the true site.
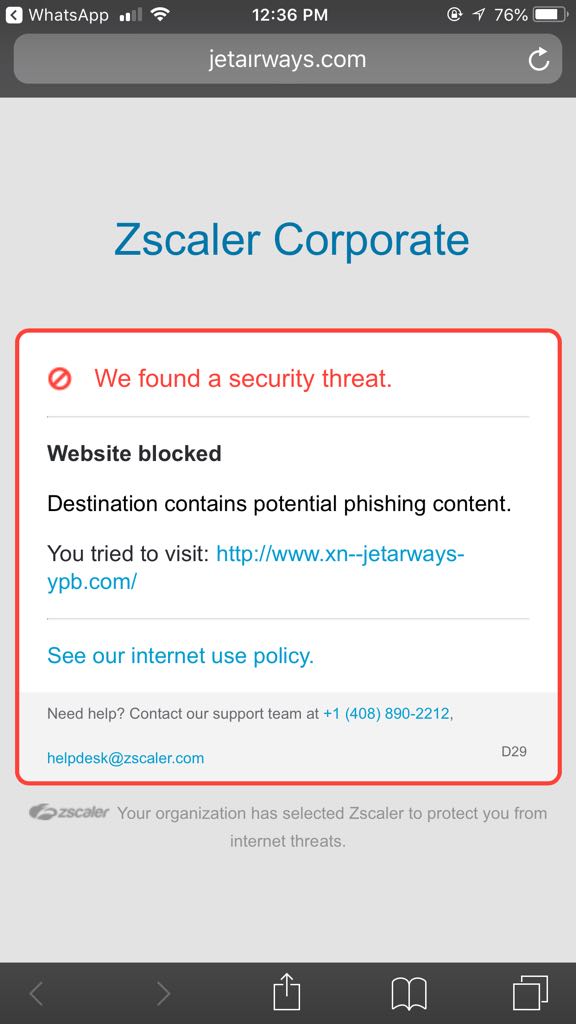
Figure 4: Safari Browser on iPhone showing URL in original IDN (Internationalized Domain Name) format.
Not all browsers treat IDN URLs equally, in the image below we see that Google Chrome on an Android phone shows the user the URL in Punycode format.
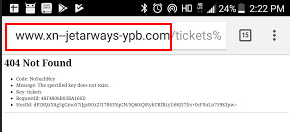
Figure 5: Google Chrome browser on an Andorid phone showing the URL in Punycode instead of IDN format.
The Web browsers decide whether to display the IDN or Punycode format based on conditions like the presence of certain characters which can spoof the separators like "." or "/", determining whether all characters come from same language, if characters belong to allowable combinations or by checking if the domain belongs to explicitly allowed TLDs. The algorithm for this is detailed here. Google Chrome has also adopted a similar set of rules as followed by Mozilla Firefox as detailed here. Browsers can make these decisions based on restriction levels as classified here.
The different behavior to IDN domain labels by common web browsers is seen below.
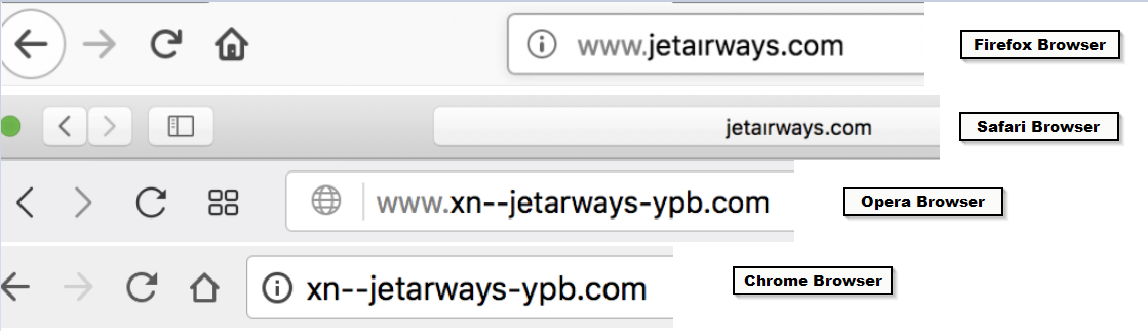
Figure 6: Different behavior seen for IDN domains on common browsers.
Coming back to our current example, if we check the domain history for this domain on Domaintools it shows that the domain was newly registered within the last two weeks.
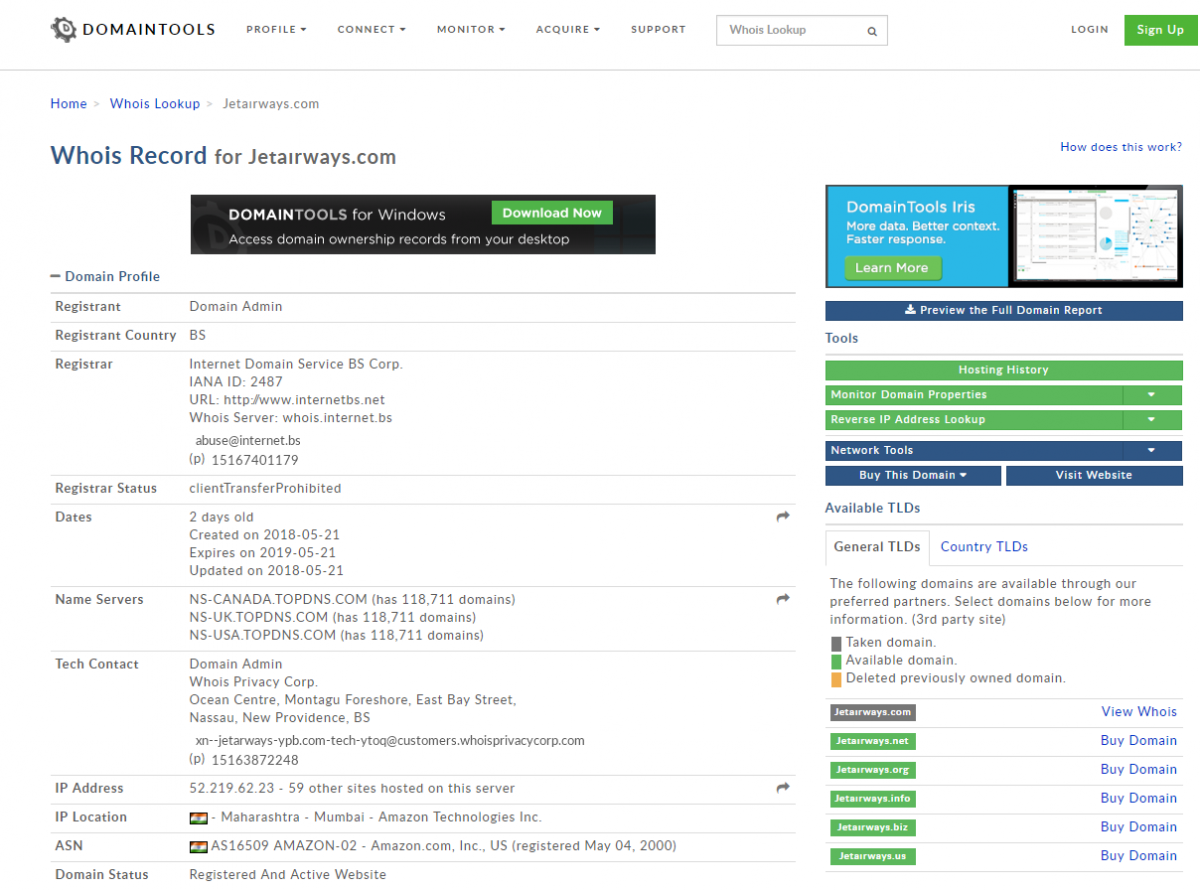
Figure 7: Domain registration information.
The full cycle of this phishing attack can be seen in the screenshot below,
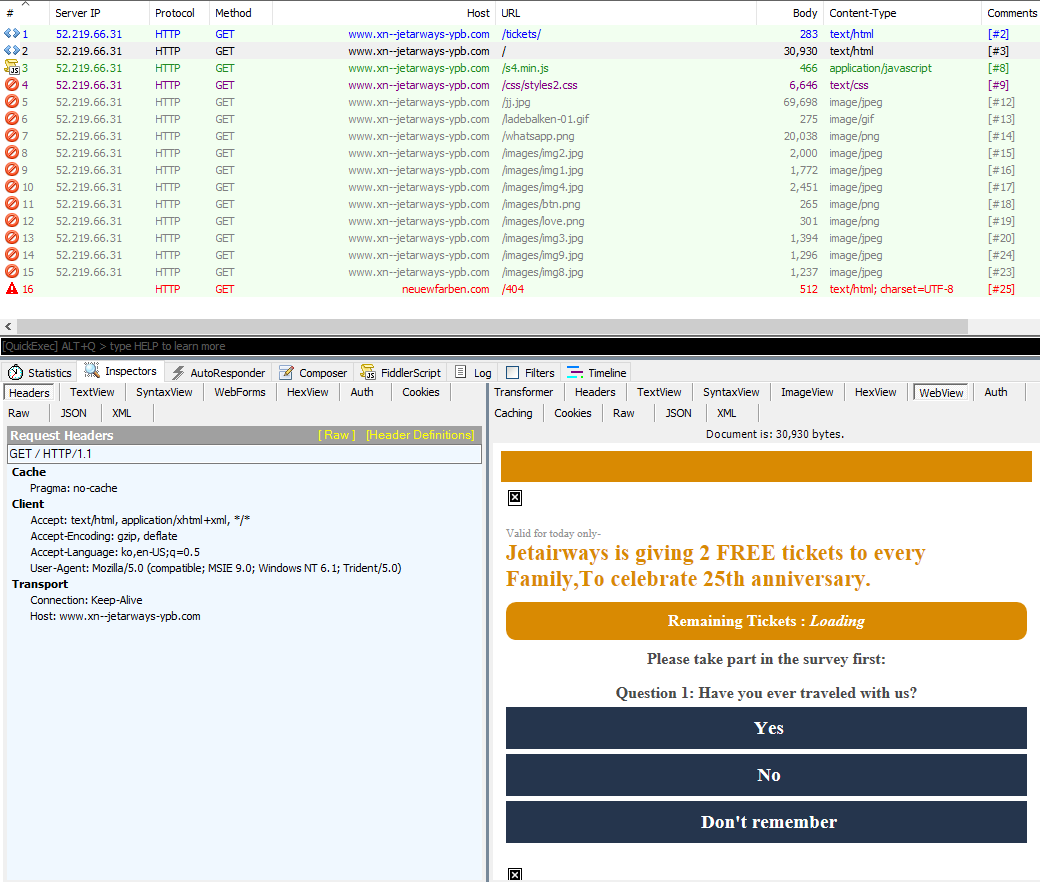
Figure 8: Phishing cycle showing a screenshot of phishing webpage.
We can see that after being served the phishing page, the victim is redirected to another domain, newuewfarben[.]com, which can be used to serve malware. At the time of testing, this URL was inactive.
Conclusion:
SMiShing has been on a rise in year 2018 and the addition of homograph technique will continue to make it more effective against unsuspecting mobile users. Web browsers have implemented protections against homograph attacks, but because of the legitimate use of Punycode characters, it becomes very difficult for the developers to implement a foolproof fix. Attackers leverage this to work around the rules and create homographs which are displayed as IDNs despite being malicious in nature.
Zscaler ThreatLabZ is actively monitoring such attacks, to ensure that Zscaler customers are protected.
How can users protect themselves?
Users should exercise caution before clicking on any links shared via SMS or IM application, even when they are from trusted contacts. The IDN format display is controlled by the browsers design and end users have limited control over how the URL is being displayed. The primary and most effective option would be to make use of password managers which check the URLs before entering the passwords into the website, this reduces the chances of users entering credentials to a homograph URL phishing website. The secondary check would be to carefully observe the URLs to spot any obvious character switches.





