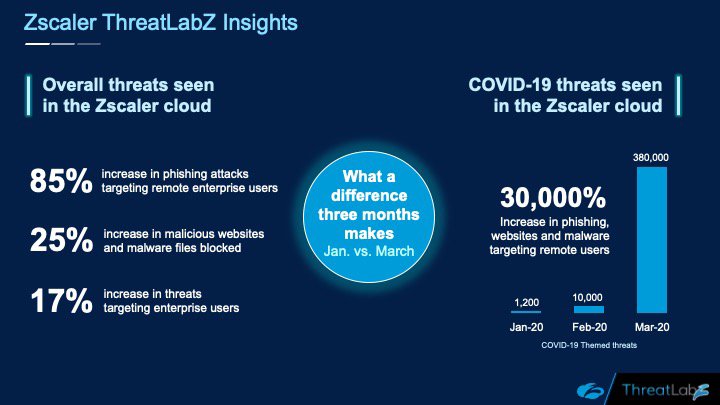
No, that is not a typo. Since January, we have seen an increase of 30,000% in phishing, malicious websites, and malware targeting remote users—all related to COVID-19. In January, we saw (and blocked) 1,200 such attacks. How many did we see in March? 380,000!
As we discussed in a recent webinar, which is now available on-demand, bad actors love to take advantage of major news and events, popular brands, the hottest games—anything trending around the world—to give their malware a better chance of success. And, sadly, they are not above preying on peoples’ fears and uncertainty, which explains the explosion in attacks and scams related to COVID-19.
Let’s take a look at some of the ways cybercriminals have been adjusting their campaigns to take advantage of the pandemic.
It starts with newly registered domains
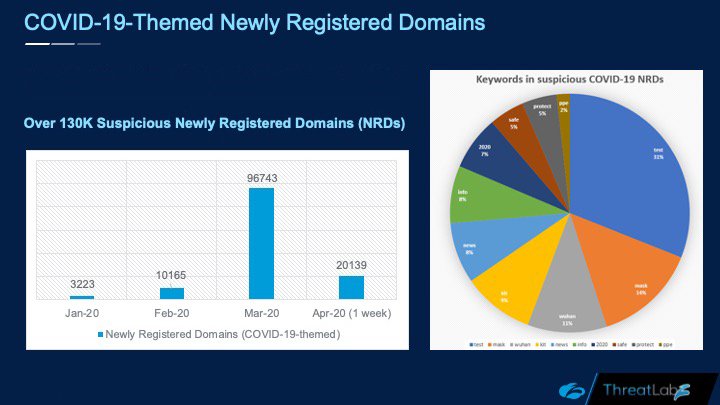
Since the outbreak, we have seen more than 130,000 suspicious newly registered domains (NRDs). Cybercriminals register new domains to take advantage of words and themes associated with current events, and to evade detection from reputation blocklists. Because the domains are new, they won’t appear on any list of suspicious websites.
The keywords for the NRDs we’ve seen include those commonly connected to COVID-19 including test, mask, Wuhan, kit, and more.
Phishing campaigns target corporations and consumers
Phishing attacks based around COVID-19 targeted corporations as well as consumers. On the corporate front, spear-phishing emails were designed to look as if they were coming from the recipient’s corporate IT team or payroll department. They even used a CAPTCHA screen to appear more legitimate, and to avoid detection by security crawlers.
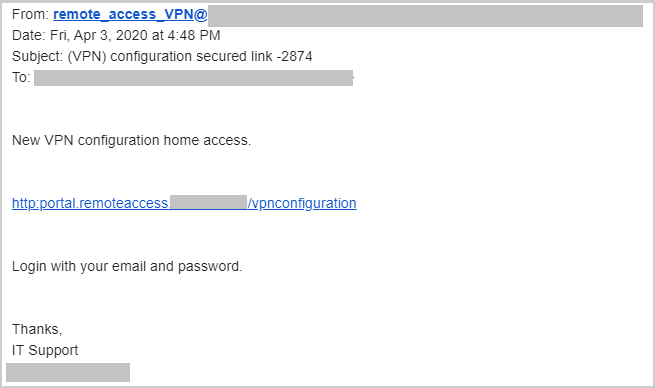
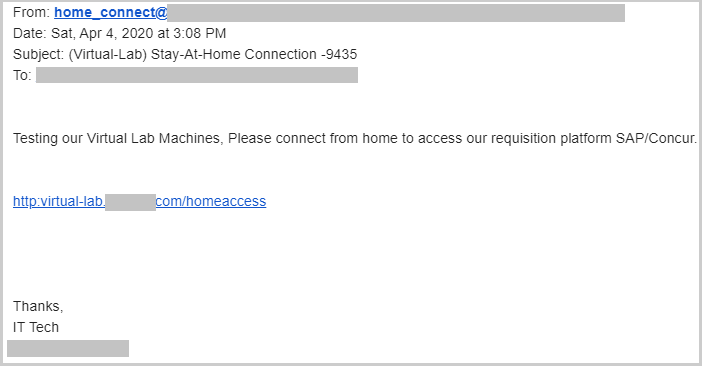
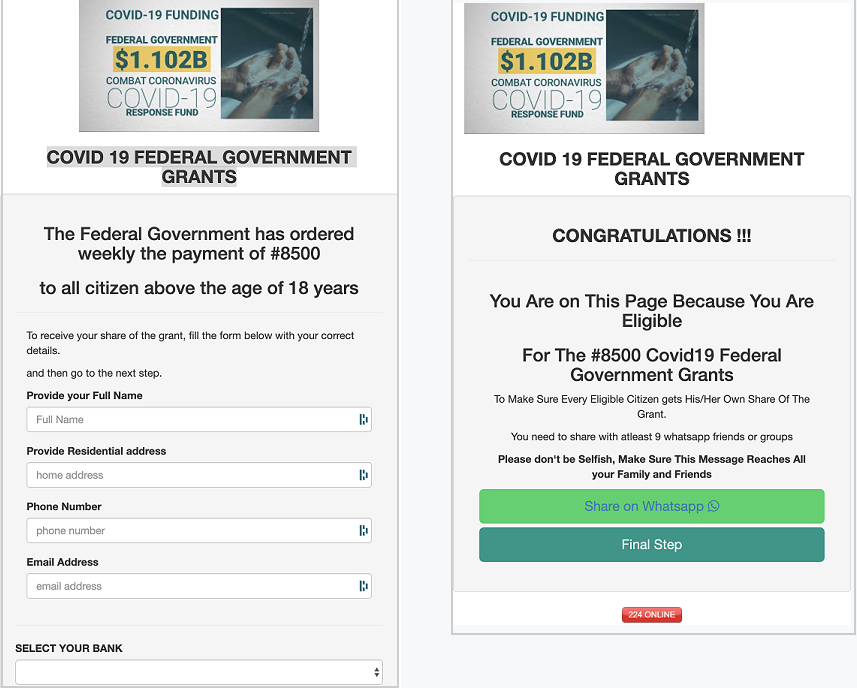
On the consumer side, we saw malicious emails asking for personal information as a way to help individuals get their government stimulus money, and we saw those soliciting donations for COVID-19-based causes. In many cases, these sites are designed to trick the user into providing personal information or corporate credentials.
Weaponized PowerPoint document targets users in Brazil
One scam included a PowerPoint file that supposedly contained a list of hotels that had been affected by COVID-19. However, once the user opened the file, a multistage remote access Trojan (RAT) was loaded onto the victim’s computer and would collect information about the system and log keystrokes and send all that information to a command-and-control server. This scam was targeting users in Brazil.
Malware campaigns target at-home users
As social-distancing orders and lockdowns began to spread around the world, many people found themselves working from home and taking classes online for the first time, and many of those turned to the virtual private network (VPN) for security and privacy. This, of course, led to cybercriminals developing a fake VPN software campaign designed to trick users into downloading and installing malware by masquerading as a legitimate VPN client.
JavaScript skimmers target healthcare, pharmacy, and grocery sites
We continued to see the skimmer gang Magecart remain active in the wild. We have blocked several instances of skimmer code infections on healthcare, pharmacy, and grocery sites as an increasing number of individuals resort to online shopping for daily essentials during the pandemic.
Several new websites (especially local grocery shops) have been quickly put together during this pandemic to support online orders. Unfortunately, not all of them are set up in a secure manner, which has resulted in some of these sites becoming compromised and injected with skimmer code. When a user attempts to purchase anything through one of these compromised websites, the JavaScript skimmer code will dynamically add a form on the payment page to capture site information, credit card data, and the user’s personal information. We have covered Magecart campaigns in the past here.
Mobile users are targets, too
Bad actors are also targeting mobile users with phishing and mobile malware using COVID-19 lures. One malicious website we saw portrays itself as a download site for an Android app that tracks the spread of coronavirus across the globe and alerts the user of nearby COVID-19 patients. In reality, the app is ransomware, which locks out the victim and demands ransom to unlock the device.
Another scam asks users to install an Android application package (APK) to receive a “Corona Safety Mask.” Instead, it simply installs an SMS Trojan that collects all of the user’s contacts and sends SMS messages to all those contacts with a download link in an effort to spread itself to more users.
Throwback: we even saw a Nigerian 419-style scam
We saw COVID-19-themed attacks across several different threat categories, including the decades-old Nigerian 419 scam.
In this case, a COVID-19-themed scam email arrives from “an American doctor” taking care of a prominent Chinese businessman/politician who contracted the virus and is very sick. The doctor now needs your help in getting the patient’s money out of China before he dies and the money gets into the wrong hands, including the government.
The crisis will end, but the threats will persist. Protect your enterprise.
The many uncertainties presented by COVID-19 challenge businesses to find new ways to ensure their employees’ digital health no matter where they work. With the ongoing crisis, threat actors are quickly updating their tools, techniques, and procedures to exploit global uncertainty and target the employees of large enterprises.
There is a growing security concern that once the pandemic is over, there will be thousands of machines physically returning to the corporate network after being on unsecured home networks for months. If any of these machines became compromised, they can offer attackers a beachhead into the corporate networks—which is exactly how many large-scale breaches get their start. The risk underscores the importance of always-on security that provides identical protection no matter where users connect—the kind of security delivered by a secure access service edge (SASE) and zero trust network access (ZTNA) architecture.
Help your employees help your organization avoid attacks
Each user in every organization must develop a heightened state of awareness, as cybercriminals will continue to use the current global crisis as an opportunity to target and compromise end-user systems. If users are unsure about something they see online or receive in their inbox or SMS, they should be instructed to reach out to IT security teams for help.
It is critical to teach every user the following best practices:
- Stick with reputable sources for COVID-19 information
- Be wary of requests for emergency funds via email (call the sender to confirm, even if it appears to be from a known contact)
- Do not open links or attachments from unknown sources
- Enable two-factor authentication
- Patch operating systems and apply security updates
- Activate SMS/email notifications for any financial transactions
How can Zscaler help?
Zscaler was founded on the notion that cloud and mobility would disrupt traditional network and security architectures. We set out to secure this new world with a security cloud, built from the ground up to ensure fast, reliable, and secure access to apps—across any network, on any device, and from any location. Our purpose-built multitenant cloud architecture simplifies your network infrastructure, improves security and the user experience, and reduces costs. Those are just some of the reasons why more than 400 of the Forbes Global 2000 organizations have chosen to secure all their traffic through Zscaler.
The Zscaler cloud footprint includes more than 150 data centers on six continents, and your company’s networking and security policies follow users no matter where they connect to the internet. They will be routed to the closest Zscaler data center, enabling consistent security policy enforcement and a fast user experience whether they are in the office or traveling or working from home. There is no need to backhaul traffic to the corporate HQ network to perform security inspection as your security stack lives in the cloud.
On any given day, the Zscaler cloud processes more than 100 billion transactions from more than 4,000 enterprise customers. Of all that traffic, we block an average of 5.5 billion transactions due to security or policy violations. We perform 120,000 security updates daily in the cloud, which includes signatures, domains, URLs, file hashes, and other intelligence. The scalability of the Zscaler cloud architecture allows us to perform security scans at scale with SSL inspection enabled.
If you want to learn more about any of the threats I covered earlier, please watch our webinar titled COVID-19 Cyberattacks: What You Need to Know.
And, as always, the Zscaler ThreatLabZ team is continually monitoring the Zscaler cloud to identify new, emerging threats and to keep our customers safe.
Deepen Desai is VP of Security Research at Zscaler








