Foreword: First, to the IT security leaders who spent countless hours responding to the need to secure a new, remote workforce during the pandemic - congratulations for what I’m sure, for many of you, was one of the most challenging and significant accomplishments of your career.
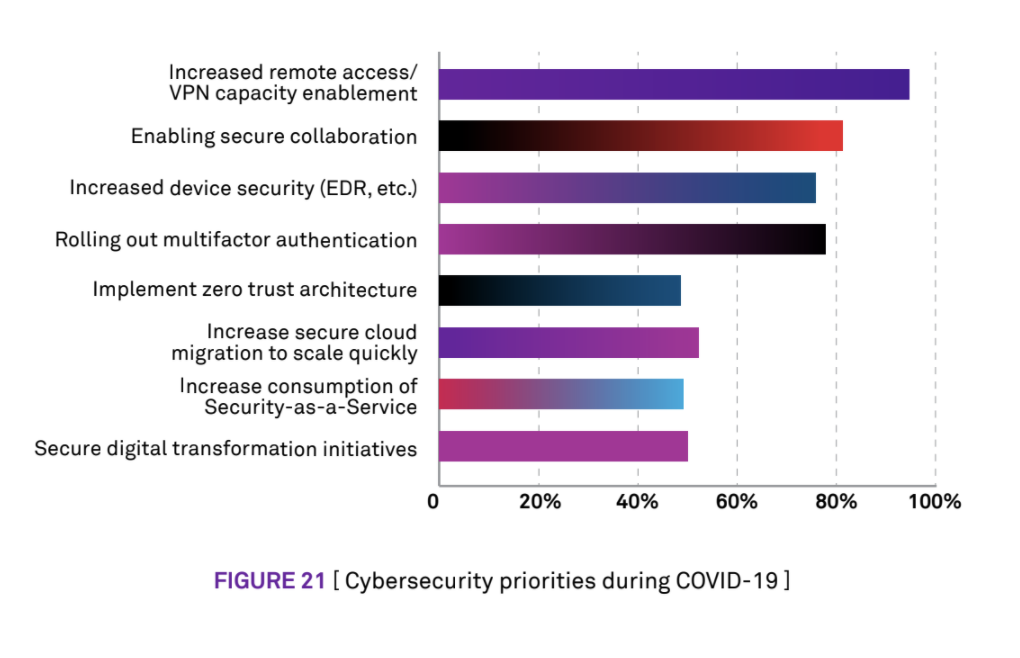
When Zscaler first began to hear from companies about the need to enable a mobile workforce, we anticipated two things would happen. First, many organizations would look for a quick, short-term solution to the problem and scale up their use of remote access VPN. In fact, this can be seen from the data below provided by Wipro’s State of Cybersecurity Report 2020. See how more than 90 percent of organizations view increased VPN capacity as a top priority:
Second, we anticipated that quickly adapting to a remote workforce would lead to what would be the largest attack surface in the history of security. As the use of VPN technology adoption skyrocketed, so too did the number of internet-based exploits looking to capitalize on the fact that they are used to connect users to the corporate network. In fact, there are now almost 500 known vulnerabilities on the CVE database actively targeting VPN. Some examples of VPN-based exploits include:
- Social Engineering Attacks – as we saw at Twitter in 2020
- Microsoft Exchange Server Exploits
- Ransomware – for example, Sodinokibi, which affected several large businesses
- Attacks on the U.S. government from Nation-States (i.e., China)
Each of these exploits poses a considerable threat to a business. To combat them, companies are now looking to embrace zero trust architectures as a means of connecting users to business applications, therefore eliminating the need for VPN and avoiding placing users onto the corporate network or exposing resources to the internet.
The companies that had already begun their zero trust journey benefited greatly, as they already had the foundation technologies in place to protect their data, ensure least-privilege access, and deliver the experience their users needed when it mattered most. They simply scaled up their zero trust services.
A new cloud landscape makes zero trust critical
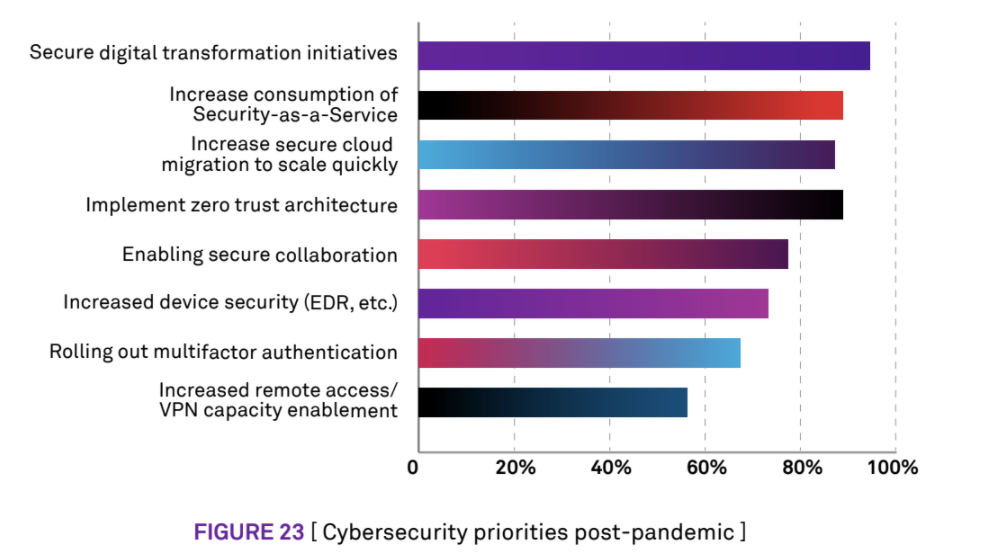
Business continuity in 2020 taught us that location no longer matters when it comes to the productivity of employees, and that the rise of a new, hybrid workforce has accelerated transformation to cloud services that can better enable business growth and competitiveness. This has opened up new avenues for cloud-delivered security technologies that were designed to connect users, who are now working from anywhere, to critical business applications. This is why the adoption of zero trust architectures has grown by leaps and bounds, and is expected to continue, due to the fact that more than 80 percent of IT leaders say it’s a priority post-pandemic, per Wipro’s research.
As security leaders look to embrace these architectures, they need to first understand what zero trust means and be sure to avoid the misconceptions that often surround the topic. They should note that the term “zero trust” has been around for more than 10 years. The problem was that it was always based on the notion of network connectivity—connect a user to a network where the applications lie and then segment the network with internal firewalls to minimize lateral movement. This was complex to manage and implied trust of users by allowing remote users to VPN onto the network via tunnel, and in-office employees to access the network simply because they were already working from HQ or a branch office. This is the opposite of zero trust.
Zero trust is about beginning with the notion of trusting no one, and only establishing trust by first relying on context - the identity of the user, and the business policies defined by IT - to provide access to specific apps, never the network itself. As the user leaves the company or the health of the user device they are connecting from changes, the business policies then adapt to minimize risk to the business. These capabilities are key to enabling the success of the business now and in the future.
It’s also important to realize that not all zero trust services are the same. Some are hosted as fully cloud-delivered services that are managed by the security vendor. Others are deployed as on-premises gateways hosted and managed by the customer themselves. Architecture matters more than ever.
Powering business with zero trust
The good news is that with zero trust, security leaders now have the rare ability to actually drive the secure transformation of their business, rather than get swept up in the change. Here is what I mean by that:
- Organizations must move to the cloud for agility and remove IT friction - The adoption of SaaS apps (O365, Salesforce, Box, etc.), collaboration apps (i.e., Microsoft Teams and Zoom), and the move to public cloud (Azure, AWS, Google, etc.) are all natural tailwinds for transformation. It also explains why more than 80 percent of businesses expect to increase the consumption of security-as-service technologies post-COVID-19. Cloud-delivered zero trust services will become the preferred option for businesses going forward since they offload the management of security infrastructure to the vendor and ensure scalability and availability as part of their service level agreement (some even have a five nines SLA). These services were designed to connect users to the applications they need using brokers with points of presence all across the globe - even if the app is running on-premises or on a public cloud platform. There are also no appliances to manage or network infrastructure to set up that would slow down the move to cloud.
- Businesses must ensure that access to apps is rooted in zero trust - The ability to use identity and defined business policies to connect authorized users directly to applications ensures that the business never has to place users onto its network. This means that no network resources ever need to be exposed to the internet. It also means that access to applications is always secure. This makes it easier for the business to embrace cloud, and, when combined with the ability to use device posture as a criterion for access to an application, the 70+ percent of businesses who view device security as a priority going forward, will be overjoyed.
- Users must have the ability to work from anywhere - Because zero trust access is always based on identity and business policies, and the cloud service automatically selects the fastest access path, the physical location of the user no longer matters. The same user working in the office has the same exact access experience when working from home. This is good news for the IT security teams using zero trust services today, as the same technologies they have invested in in the remote world can still be used once offices begin opening back up.
Shifting zero trust from theory into practice
Knowing where to begin is always the hardest part of embracing something new. Below are some tips to consider when it comes to your zero trust implementation:
- Build your zero trust blueprint - Make sure to include an identity provider, access service, endpoint security solution, and SIEM solution in your plans. There is no “god” zero trust solution. Each of these are key ecosystem players that are designed to integrate with each other using APIs.
- Determine what your existing attack surface looks like today - ask the zero trust vendor you are considering to run a free assessment to determine if your network environment is currently exposed to the internet.
- Discover any Shadow IT applications running in your environment - there is a good chance that there are SaaS apps or private apps being used today that you are unaware of. Make sure your security vendor has the ability to help you discover each type.
- Choose an initial set of users - Select a set of employees or third-party users that will benefit most from this zero trust plan. These could be C-levels who are often important for any key decisions around IT, or partners who need access to your business applications (they often present the greatest user risk to your business)
- Choose an initial set of applications - Focus on the business applications that currently present the greatest risk to your organization. For many, it’s their crown jewel private applications.
Download your copy of Wipro’s State of Cybersecurity Report now.
Are you Ready to Seize the Zero Trust Moment?
Join us to learn how the latest Zscaler innovations will enable you to accelerate business transformation by embracing zero trust. Learn more about the event: https://info.zscaler.com/seize-the-zero-trust-moment