If you’d told me five months ago that today I would be solely working out of my home office in San Jose, California, I would have said you were crazy. As each month has passed, I have begun to realize that there is a very good chance this work situation might very well be the new normal. (I’ve been trying to hold out, telling myself: “It will all go back to normal soon.”) But, here I am, still working from home.

I'm sure many IT teams are feeling the same way. This sudden surge in remote work, leading to frantic calls to VPN vendors to buy more capacity and scale up ASAP—only to be told that they would need to wait 30, 60, or even 90 days just to get new appliances delivered—was thought to be a temporary, crisis-mode response. A blip.
And who could blame these IT leaders? Prior to our social-distanced world, only a fraction of companies had employees working remotely the majority of the time. Now everyone does.
The shift from crisis response to long-term access strategy is top-of-mind for every organization. What should I invest in? Should I still be using VPN? What about network appliances in general? How do I protect data now? What the he!! do we do?
Know this. Work-from-home (WFH) will become a less of an exception and more of a rule. Google is extending WFH until at least next summer, and Facebook just made a similar announcement, telling its employees to stay home through July 2021. A couple of weeks ago, Siemens announced its plan to allow 140,000 employees to work from anywhere. This new way forward will require a new approach to connecting users to business apps. Access needs to move beyond the classic network security perimeter (i.e., a VPN that connects an IP address to a network exposed to the internet) to the user’s location, to the device, and to where the application is running. No more implied trust, but rather zero trust delivered at the new edge.
The identity of the user is now critical. So is the posture of the device in use. The ability to scale remote connectivity services as you continue to hire will also be critical. This is why companies, such as Okta, Microsoft, CrowdStrike and, yes, even Zscaler, are becoming more widely adopted to enable remote work. These are all cloud-delivered access services that are tightly integrated to secure the new edge and, most importantly, are designed for this specific purpose.
So, where does the remote access VPN fit in this new world? Every day there is news about a new exploit: recently, 900 passwords to VPN servers leaked out. The image below illustrates a VPN password vulnerability that occurred when an attacker sent a uniform resource identifier (URI) to the VPN gateway in search of a particular resource.
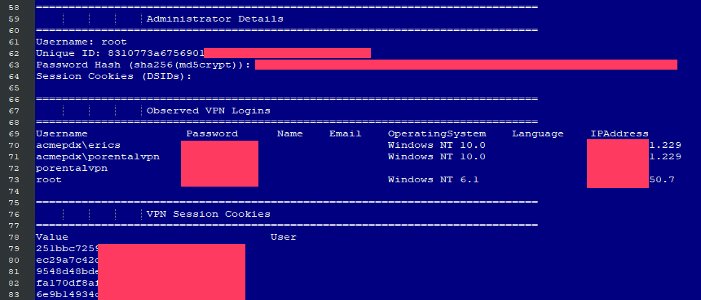
Image: ZDNet
A few customers asked about the benefits of Zscaler Private Access (ZPA) in regard to this kind of attack. My friend Lisa Lorenzin, who worked for a VPN vendor prior to Zscaler, said it best:
- First off, ZPA App Connectors don't have an inbound listener, so a hacker can't just scan the internet and find them, as was done here to the VPN servers.
- Second, we don't store user credentials at all, and we offer the option of admin SSO—so there is no way for an attacker to ever get user login credentials by hacking us, and hopefully not admin creds either.
- Third, we manage updates on our connectors, so there is no possibility for customers get hacked due to an 8-month-old vulnerability!!
- Fourth, the exploit was an attacker sending a specially crafted URI to the VPN gateway. Since ZPA App Connectors have no listener, they are not susceptible to that class of attack. And since ZPA Service Edges only accept connections from mutually authenticated TLS, an attacker wouldn't be able to send it to the broker either.
Even operational technology (OT) networks are now vulnerable to security attacks through VPN. We’re talking about the critical infrastructure in the oil and gas, water, and electric utilities industries.
This is because, with everything else IT has to worry about, it’s difficult to find time to administer VPN patches and updates. Since VPNs allow for access to network resources, hackers are targeting them as a means to gain access to critical data. The same tools IT has used for 20 years to help provide secure access to apps is now threatening their environments. It’s like a bad sequel to The Terminator movie series or something.
But there is a silver lining here. I’ve spoken with several IT leaders who have adopted a zero trust approach to providing remote users with access to business applications as an alternative to using a VPN. Robert Berkenpas from Mowi, the largest salmon producer in the world, is using this approach to ensure his employees are productive so they can help build a more environmentally friendly future for the industry. His IT team moved from being perceived as a cost center to business enabler. Marc De Serio, CTO at Henry M. Jackson Foundation, is using this zero trust approach to preserve the supply chain that helps military researchers battle COVID-19. Jay Tillson, head of architecture at TT Electronics, an electronics manufacturing company, architected a future that puts cloud and identity-based access at the forefront of its IT vision. (He’s going to be doing a live architecture session—be sure to watch it.)
My advice to you is to stop and think about what your long-term access strategy should look like. Ask yourself, what is the business asking of you? Think about the technologies that are critical to your success and the success of the organization.
You may find that your VPN isn’t suited for the job. And if you do, you wouldn’t be the only one.
Chris Hines is Director of Product Marketing for Zscaler Private Access






