Driving secure digital transformation is a challenge in the best of times. But when the winds of economic conditions shift, strategic IT leaders face increased obstacles in achieving cost efficiency while maintaining a robust security posture. IT teams are continually pushed to do more with less, budgets are cut, and resources eliminated.
Unfortunately, their legacy security architectures that use firewalls and VPNs only serve to make the situation worse. Let’s take a closer look at four challenges of perimeter security that inhibit an organization's ability to successfully provide future-ready protection and deliver superior economic value, and how to overcome them.
Challenge 1: Cost and complexity
For the last 30 years, organizations have been building castle-and-moat security architectures for defending their network perimeters and everything inside them. These perimeter models leveraging firewalls and VPNs worked well when users, data, and applications resided on premises. Today, however, users are working from everywhere. Applications and data are becoming hyper-distributed across disparate data centers, clouds, SaaS applications, and the internet.
This dramatically expands the attack surface and pushes firewalls, VPNs, and other point product appliances beyond their useful limits. Attempting to force fit these legacy architectures to support a hybrid workforce necessitates large capital expenditures and extensive management overhead. Unfortunately, this approach only provides a temporary, costly band-aid because firewalls and VPNs are not designed for the scale, service, or security requirements of modern business.
Challenge 2: Productivity
Using these perimeter- and network-based approaches to protect a user base that increasingly works outside of the corporate network negatively impacts productivity and collaboration. Think about SaaS tools like Microsoft 365 and ServiceNow, or collaboration tools like Zoom and Teams. To secure this traffic, legacy architectures leverage VPNs and MPLS to backhaul traffic to a data center and route it through a centralized security stack before sending the traffic to its destination, only to route traffic back over that same path to return to the end user.
This approach introduces unnecessary bandwidth demands and maintenance expenses and creates a choke point that increases latency and brings productivity to a screeching halt. Users are left frustrated and looking for ways to circumvent the system.
Challenge 3: The rising costs of cybercrime
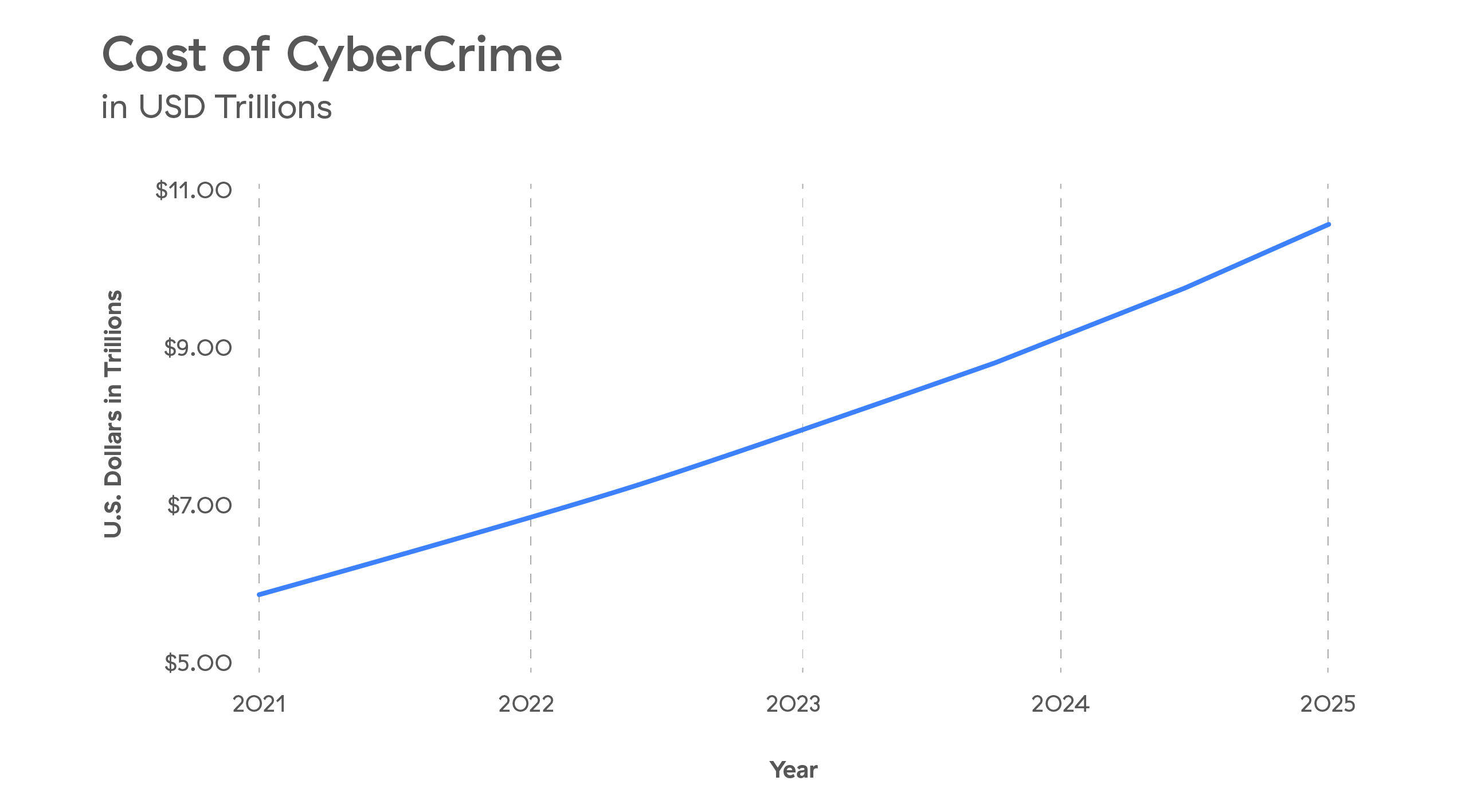
As if the first two challenges weren’t enough, organizations are facing unprecedented cyberthreats and, as a result, a rapid increase in the cost of cybercrime. In 2021, global cybercrime damages reached $6 Trillion USD, and it’s expected to grow 15% per year, reaching $10.5 Trillion by 2025.
The costs of experiencing, responding to, and mitigating a cyberattack impact an organization with operational disruption and downtime, direct losses tied to remediation, brand damage, and revenue loss. Regrettably, perimeter architectures are unable to defend properly against today’s cyberthreats.
Challenge 4: Delayed realization of M&A value
Mergers and acquisitions can present game-changing opportunities for organizations, but, according to Harvard Business Review, 70% of M&A transactions never deliver upon their expected deal value. Why? Integrating legacy networks, castle-and-moat security infrastructure, resources, and applications across the two combining entities—not to mention granting employees access to the appropriate assets—is an extremely complicated, technically challenging, and time-consuming process. As a result, the M&A process is often laden with unforeseen costs and delays in the ability to begin value-creation activities.
Overcoming the challenges
For IT leaders tasked with protecting the organization from threats while driving value in a difficult economic climate, these challenges may seem insurmountable at first. But overcoming them is certainly possible with a zero trust architecture. The Zscaler Zero Trust Exchange delivers a modern, unified approach to securing today’s cloud-first, hybrid workplaces.
It reduces cost and complexity while minimizing the risk of cyberattacks and breaches—so an organization can endure and even thrive in trying economic times. To examine these challenges in detail and learn how a true zero trust architecture can help you overcome them, read our white paper, “The One True Zero Trust Platform: Delivering Unparalleled Security and Superior Economic Value with the Zscaler Zero Trust Exchange.”





