This post also appeared on LinkedIn.
The ransomware event at Colonial Pipeline highlights the need for major cyber improvements across the public and private sectors. It was likely the impetus behind the Biden Administration issuing the much-anticipated Executive Order on Improving the Nation’s Cybersecurity on May 12. This executive order offers aggressive actions and goals towards improving the cybersecurity posture of the national infrastructure.
My initial reaction: THANK YOU!
The Executive Order was under development for some time and certainly isn’t only about Colonial Pipeline or the SolarWinds crises. It’s a reaction to the growing gap between public infrastructure cybersecurity postures and the possible damage from cyber threats to public health, services, and safety.
Ransomware is a growing problem everywhere. In the past four days, we’ve seen Ireland’s health service IT systems taken down by ransomware, and—after stating that it was dropping insurance reimbursement for ransomware extortion payments—AXA Partners was hit as well.
The executive order promotes game-changing strategies and specific measures for fighting the risk and damage from cyber threats in the United States.
Sharing threat intel
We still don’t know the details of the attack vector, timeline, or indicators of compromise (IOC) for the Colonial Pipeline breach. That’s a problem. Sharing threat intelligence is critically important for several reasons, but the most important one is that knowing the tactics, techniques, and procedures (TTPs) helps incident responders uncover attacks that otherwise wouldn’t have been detected and implement preventive measures.
The Cybersecurity and Infrastructure Security Agency (CISA), which includes the National Cybersecurity and Communications Integration Center (NCCIC) and Hunt and Incident Response Team (HIRT) teams, have dedicated experts ready to manage and assist with events like this. The Colonial Pipeline is a critical infrastructure, and CISA’s mission is specifically to address cyber issues affecting national security.
EO Section 2, “Removing Barriers to Sharing Threat Information,” highlights the importance of CISA’s role and the need to report breaches in an accurate and timely manner.
While the FBI attributed the attack to DarkSide—a group known for exploiting public-facing services—there are still many unanswered questions. We do know that DarkSide exfiltrated nearly 100GB of data and threatened to publish it on the Internet, in addition to encrypting it and making it unusable. This is known as a “double-extortion attack” in that it provides the attacker with more ransom leverage: “We’ll give you the key to unlock your on-premises data, but if you think you can just restore the data via backups, we’ll release that data into the wild.”
Zscaler’s ThreatLabz team recently published a detailed report focused on the increase of double extortion ransomware.
It’s time to make the shift
Given DarkSide’s modus operandi, we can assume they got their foothold at Colonial via a remotely exploitable vulnerability in a public-facing application.
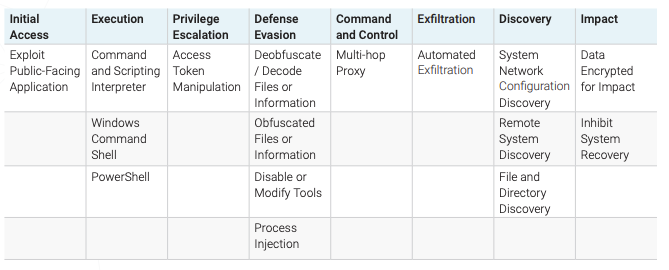
Figure 1: Darkside - MITRE ATT&CK Tactics and Techniques
But there are many different vectors (phishing, driveby download, malicious USB drive, etc.) that could lead to the same result. Modernizing cybersecurity infrastructure, security posture, and standards compliance across public and private entities—especially when both work together to manage critical infrastructure—is an immediate priority. The new executive order calls for strengthening incident detection, response, and mitigation to reduce the likelihood that a single security incident doesn’t become a significant security event.
Organizations must shift from legacy network-centric security to successfully combat today’s threats: attackers are likely targeting you right now. Zero Trust architectures prevent cyberattacks from propagating laterally across an organization’s IT infrastructure (a fact I highlighted recently). Section 3 of the executive order, “Modernizing Federal Government Cybersecurity,” is a crucial component. It explains how the move to cloud (IaaS, PaaS, SaaS) technologies, remote work, hybrid cloud/on-premises environments, and IT systems that process data or operate machinery (like IoT/OT devices) requires significant investments in zero trust-based solutions to modernize cybersecurity capabilities.
Each agency must develop a plan to implement a zero trust architecture that aligns with NIST 800-207 and submit an implementation timeline.
But what is zero trust?
“Within 60 days of the date of this order, the head of each agency shall…develop a plan to implement Zero Trust Architecture.”
- The White House
I get to speak to cybersecurity leaders across many industries. I often ask what they think Zero Trust means. I hear a lot of different answers depending on context and concerns.
Zero Trust has evolved. It encompasses ten years of security best practices designed to protect the cloud services, software, and infrastructure that makes digital transformation a plausible reality. At its core, it means connecting users directly to applications on a least-privileged or default-deny basis.
Implementing “zero trust” access using traditional network-centric security capabilities is difficult to manage and maintain. Overseeing the access control lists (ACL) and firewall rulesets needed for applications to function without opening massive security holes is problematic for businesses needing agility and resilience.
Network-centric security technologies also don’t adequately prevent lateral movement. Why? Firewalls live at the perimeter of a network: Once you’re through, they don’t protect the rest of the systems. This means using internal firewalls, network segmentation, zones, VLANs, etc., to control internal traffic. Configuring, troubleshooting, and maintaining these rulesets often results in overly permissive access to internal applications. What’s the point of implementing network segmentation if holes in security rules allow NetBios/SMB or remote desktop protocol (RDP) to communicate bi-directionally with Active Directory (AD) and other core support services?
We must shift and abandon network-centric security approaches and embrace zero trust solutions to defend against today’s threats successfully.
The latest executive order includes a definition of Zero Trust architectures in Section 10, “Definitions,” and references the NIST Zero Trust Architecture standard (NIST 800-207). TIC 3.0 and NIST 800-207 guidance has opened the door for agencies to adopt modern, cloud-based zero trust security solutions that cover cloud technologies (IaaS, PaaS, SaaS), on-premise or hybrid environments, and IT systems that process data or operate machinery (OT devices).
Containment is critical
There is an invisible and never-ending chess match between cyber attackers and IT security. The more effective the cybersecurity capabilities are, the harder attackers work to develop new and more evasive attack techniques.
While phishing is the most common attack vector for threat actors to obtain initial access to an agency endpoint, another common attack vector is vulnerabilities in public-facing applications exposed to the internet. Whether it be a vulnerability on a VPN concentrator or within a web application, quickly containing an attack prevents lateral movement and mitigates the damage from a breach.
Again, I was pleased to see Section 7, “Improving Detection of Cybersecurity Vulnerabilities and Incidents on Federal Government Networks,” included in the executive order. It calls for a government-wide endpoint detection and response (EDR) capability.
The speed at which you can identify and contain a compromised endpoint, node, account, etc., determines the severity and extent of a breach. This isn’t possible unless you leverage EDR capabilities that use integrated AI/ML to facilitate automated responses.
The challenge ahead
The Colonial Pipeline attack and other events over the last few weeks are unfortunate and demonstrate weaknesses in the current state of our cybersecurity. But this is an excellent opportunity for those that understand the challenges to make a shift and implement the cybersecurity capabilities necessary to protect and defend enterprises and infrastructures from dangerous attacks effectively. The technology is ready. The real challenge is shifting the people’s mindset and company culture to embrace better cybersecurity and digital transformation.
The new Biden Administration executive order tells the nation that it’s time to modernize cybersecurity across the board and includes aggressive actions for what’s needed: abandon old thinking, modernize outdated security capabilities, and adopt zero trust architectures. To those who helped create the “Executive Order to Improve the Nation’s Cyber Security,” well done!
For the frontline cyberwarriors who selflessly dedicate their career to protect the mission, thanks for your dedicated service, and keep fighting the good fight!




