Zscaler Blog
Get the latest Zscaler blog updates in your inbox
Subscribe
Why Spending Millions on Firewalls and VPNs Doesn't Stop Breaches
For decades now, organizations have spent massive amounts of money purchasing security appliances. They’ve acquired dozens upon dozens of solutions, racked and stacked an endless amount of hardware, and filled their data centers to the brim.
In particular, the go-to tools and de facto standards for cybersecurity in recent history have been the firewall and the VPN (virtual private network). Over time, both of these security staples have grown in sophistication, capacity, and functionality. They have also evolved in terms of form factor, going from on-premises hardware appliances to virtual appliances that can be deployed in a cloud.
And yet, despite all the money invested into firewalls and VPNs, breaches continue to occur. Even the world’s most security-conscious, heavily regulated organizations that have the most advanced cloud firewalls still experience breaches. News headlines continually tell victims’ stories.
So, why is this? If organizations are spending millions on firewalls and VPNs, why do they still get breached? Read on to find out.
Firewalls, VPNs, and architectural risks
To put it bluntly, it is because organizations rely on firewalls and VPNs that they keep getting breached. If these two tools are present, it is a clear indicator of what an organization’s underlying security methodology is. That’s because firewalls and VPNs are core parts of what is known as perimeter-based or network-centric architecture.
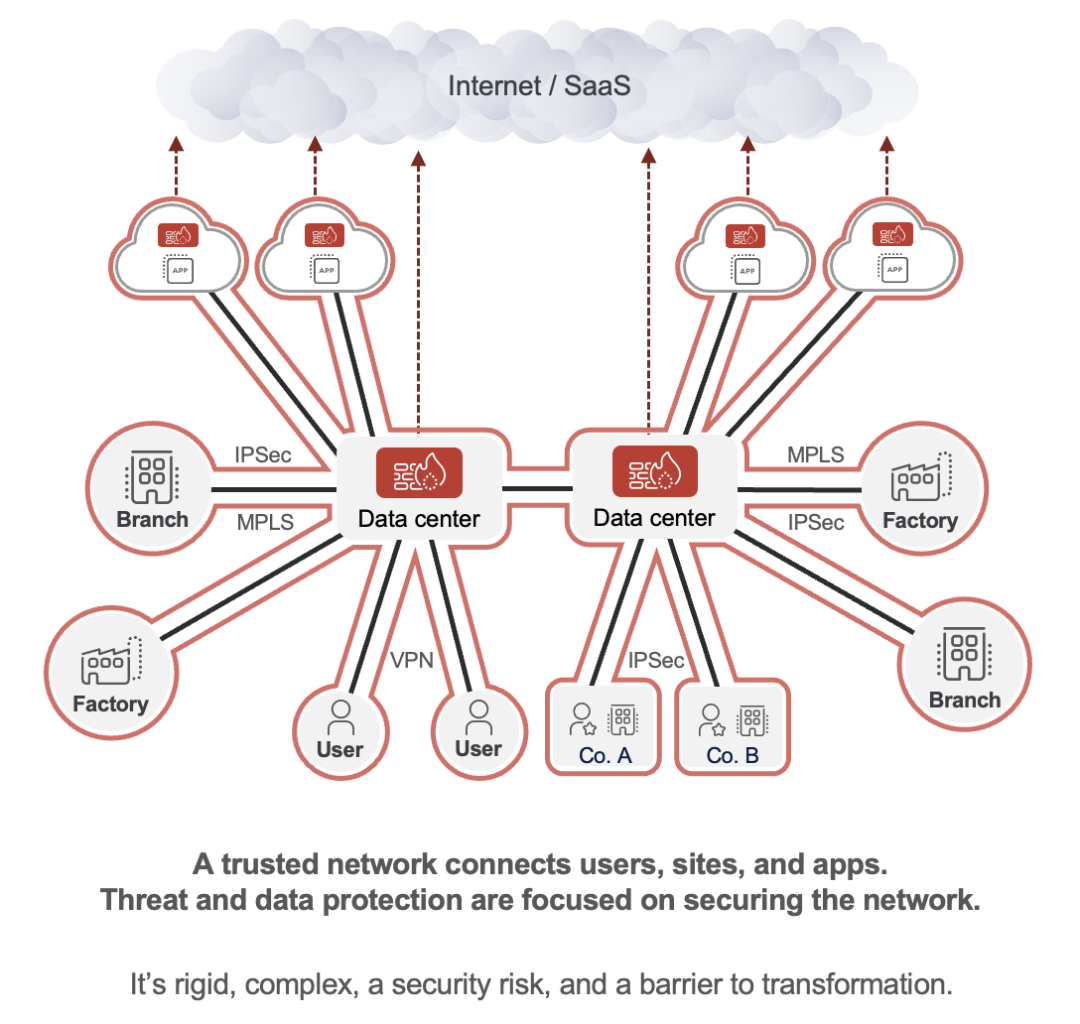
Figure 1: Firewall-and-VPN-based architecture
With this type of architecture, everything revolves around the network. That’s because it is through network access that users, devices, workloads, and other entities get to access the apps and resources they need. As a result, the network is continually extended to growing numbers of entities and locations in order to ensure they can access the network and, ultimately, the resources on the network. Given today’s remote users, cloud applications, and more, this state of affairs becomes very complex very quickly.
In light of the above, when it comes to reducing cyber risk, organizations focus on the mantra, “Keep the bad things out and the good things in.” In other words, build a secure perimeter around the network, hence the nomenclature “perimeter-based architecture” as well as “castle-and-moat security.” As a result, cyberthreat and data protection efforts inevitably amount to defending the network—which is a tall task as the network continually expands to accommodate remote work, cloud apps, and more.
Despite firewall-and-VPN-based architecture being seen as the default for security, the approach has significant weaknesses that increase the risk of cybersecurity incidents:
- It expands the attack surface through endless network extension and the public IP addresses of firewalls and VPNs, both of which provide attack targets for cybercriminals.
- It enables compromise through hardware and virtual appliance scalability challenges that make it difficult to inspect encrypted traffic and stop the threats therein.
- It permits lateral threat movement by connecting users, devices, and workloads to the network as a whole, allowing them to access its various connected resources.
- It fails to stop data loss in encrypted traffic (because of the aforementioned scalability challenges) as well as other, modern data leakage paths like SaaS apps.
In addition to the above, the regular cadence of firewall and VPN vulnerabilities that expose organizations to an even greater degree of risk highlight the need to retire these appliances—whether they are hardware or virtual. For example, consider the CVEs of one vendor in December 2023, the CVEs of another vendor in April 2024, or the other high-profile CVE that also came to light in April 2024.
Costs, costs, and more costs
Sadly, the costs of firewalls and VPNs are not limited to their price tags, making the ratio of cost to value even more discouraging for these breach-enabling tools. Beyond the initial technology or infrastructure costs, there are five other ways they waste resources:
- They increase complexity and, as a result, decrease operational efficiency and increase management overhead.
- They complicate IT integration during M&A, leading to scope creep, delaying time-to-value, and fostering cost overruns.
- They fail to prevent data breaches, generating costs associated with remediation, fines, brand damage, and customer churn.
- They slow down the end user experience through backhauling and latency, impeding productivity for workers.
- They consume massive amounts of electricity, leading to sky-high power bills and expanding organizations’ carbon footprints.
For an in-depth look at each of these costs, you can click the links above or download our comprehensive white paper.
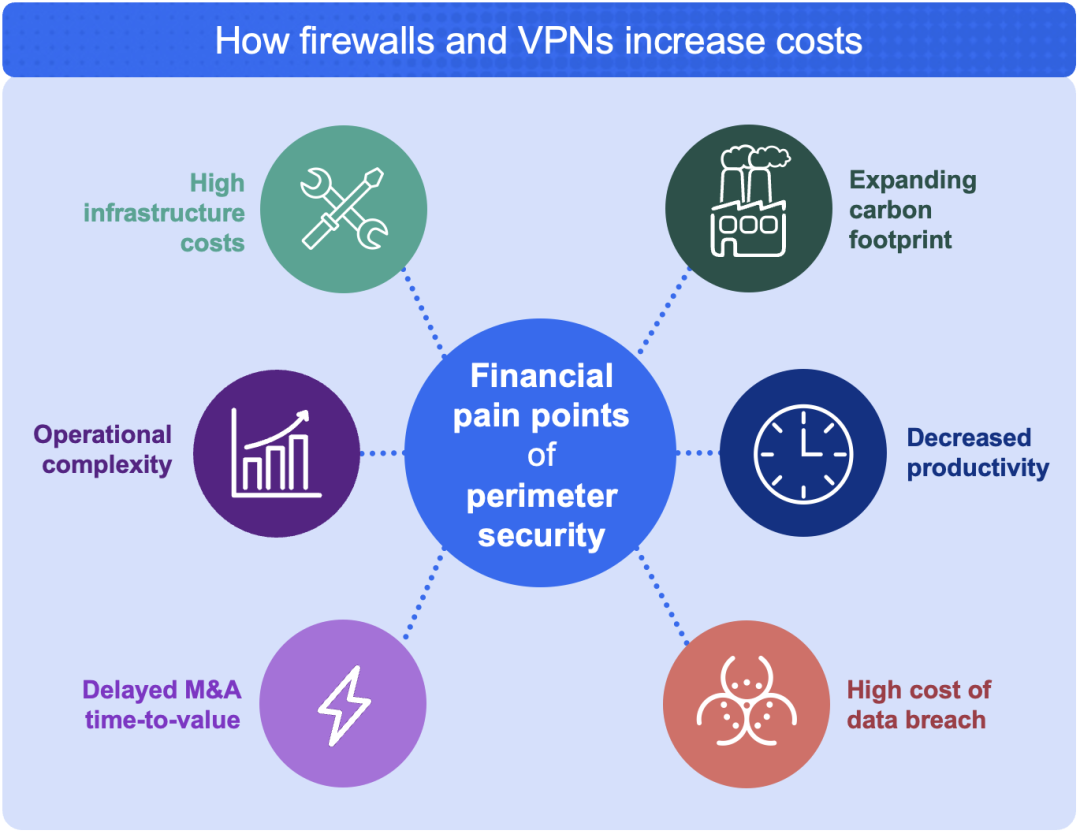
Figure 2: The six key ways firewalls and VPNs increase costs
The panacea to these problems
To summarize this blog so far, organizations are burdened with significant costs by firewalls, VPNs, and perimeter-based architectures that are unable to protect them properly against cyberthreats and data loss. These are problems that cannot be solved by doubling down on the status quo. Instead, organizations need to think differently, retire firewalls and VPNs, and embrace a fundamentally different architecture that can systematically reduce risk. In other words, organizations need to implement zero trust.
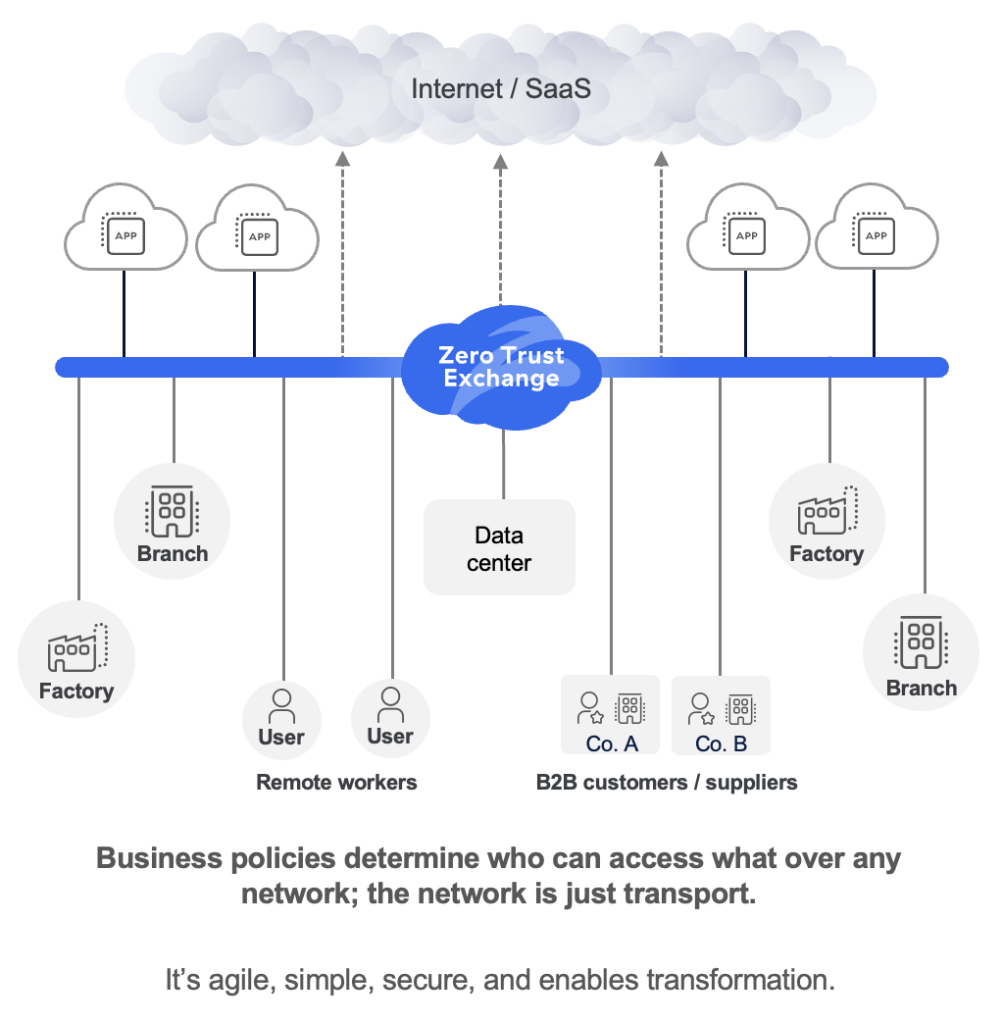
Figure 3: Zero trust architecture
Zero trust architecture is inherently distinct from the network-centric architectures of yesteryear. With zero trust, security and connectivity are decoupled from the network. Instead of demanding continuous network extension, a zero trust cloud delivers secure connectivity as a service at the edge (from as close to the end user as possible). Users are given access directly to applications and not to the network as a whole.
This is in keeping with the zero trust principle of least-privileged access, whereby users are granted access only to the resources they need, at the moment they need them. Countless contextual factors like user location, user behavior, device security posture, and requested app are used to determine whether access should be provided. Overall, this architecture overcomes the security weaknesses of firewalls and VPNs:
- It minimizes the attack surface by eliminating network extension as well as firewalls, VPNs, and their public IP addresses; the attack surface is hidden behind a zero trust cloud.
- It stops initial compromise through a high-performance cloud platform that can inspect encrypted traffic at scale, identify cyberthreats therein, and enforce policies that stop them.
- It prevents lateral threat movement across connected resources on the network by connecting users directly to apps instead of connecting them to the network as a whole.
- It blocks accidental and malicious data loss within encrypted web traffic as well as all other data leakage paths, including SaaS apps, cloud platforms, endpoints, and email.
But zero trust does more than just reduce risk—it also helps organizations save on the various costs of firewalls and VPNs. To see how, take a look at Figure 4 below or, once again, you can download our white paper.
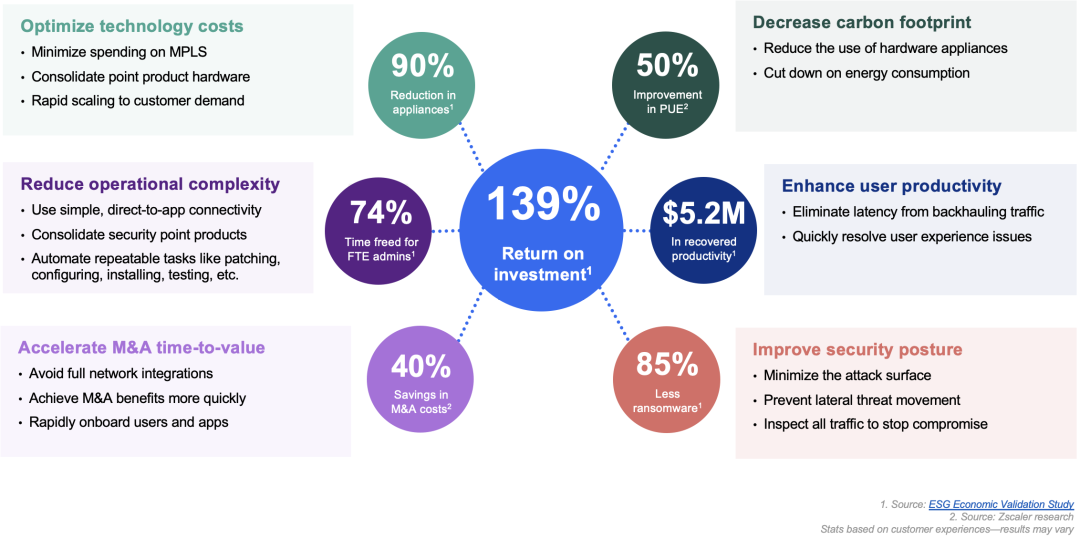
Figure 4: The economic advantages of Zscaler
Whether it’s reducing cyber risk and stopping data breaches or minimizing the costs associated with firewalls and VPNs, zero trust architecture gives organizations everything they need to succeed.
To read a more detailed explanation of the security weaknesses inherent in firewalls and VPNs, download our ebook, “4 Reasons Firewalls and VPNs Are Exposing Organizations to Breaches.”
To learn more about zero trust, register for one of the monthly renditions of our webinar, “Start Here: An Introduction to Zero Trust.”
Was this post useful?
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.




