Zscaler Blog
Get the latest Zscaler blog updates in your inbox
4 Reasons Your Firewalls and VPNs Are Exposing Your Organization to Breaches
While it may have been acceptable in years gone by, leaning on firewalls and VPNs for security now only serves to increase risk for the modern organization. That’s because the use of these tools inherently means the use of hub-and-spoke networks and castle-and-moat security models. These old-school architectures were focused on providing access to, and securing, the corporate network as a whole—the aim was to keep good things “in” and bad things “out.” Naturally, this approach was designed for a time when users, apps, and data all resided on premises, and things rarely moved beyond the network perimeter.
This is no longer the case today. Whether organizations are just beginning to undergo digital transformation or already have cloud applications and hybrid workers firmly in place, relying on tools like firewalls and VPNs actually exposes them to breaches. Want to know how? Read on to learn the four key reasons.
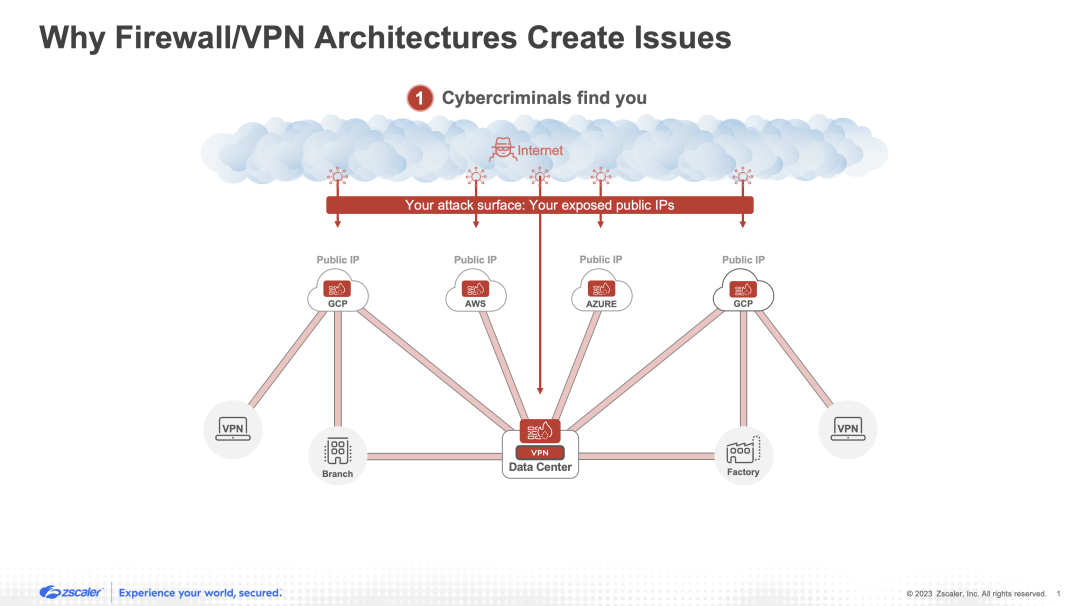
1. They expand your attack surface
As organizations with yesterday’s architectures grow, they invariably extend their hub-and-spoke networks to more branch offices, factories, cloud-based resources, remote users, and more. To secure this endlessly expanding network, firewalls and VPNs are typically seen as the go-to tools for establishing a “safe” perimeter (i.e., for building a “moat” around the “castle”). Unfortunately, this solution creates a significant problem.
Firewalls and VPNs have public-facing IP addresses that sit on the public internet. This is by design so that the intended, authorized users can traverse the web and find the entry points into the network. However, these front doors can be found by anyone, including cybercriminals who are eager to bash them in. As organizations grow and deploy more and more of these tools, they are inevitably giving attackers more and more targets. In other words, using firewalls and VPNs drastically increases your attack surface.
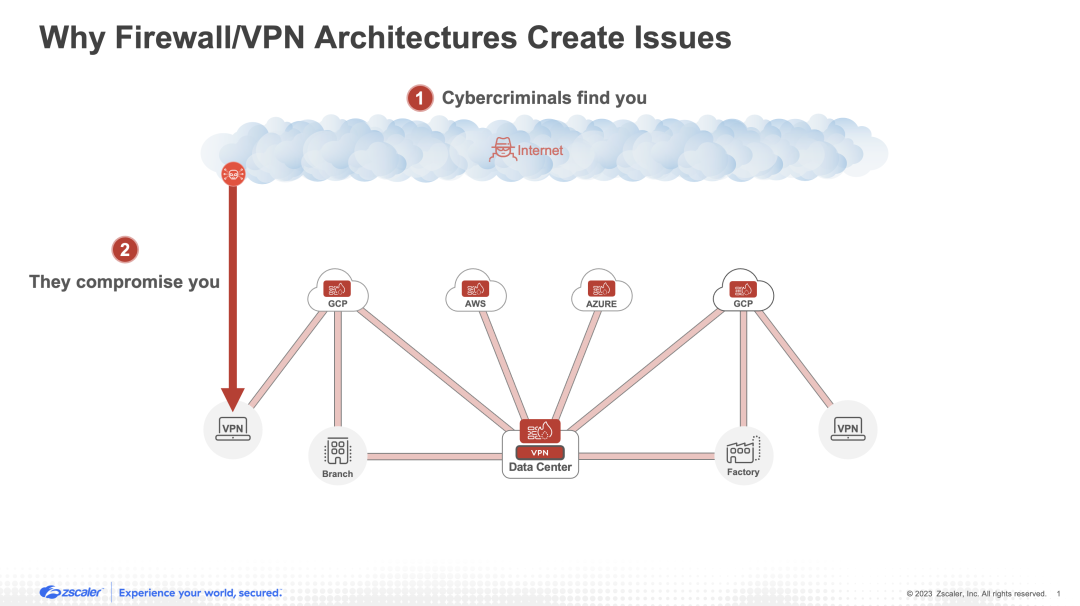
2. They fail to stop compromise
Successfully stopping cyberthreats from compromising an organization requires inspecting traffic for any and all malicious activity and enforcing real-time policies that block cybercriminals’ malicious tactics. However, this is an undertaking that requires extensive computing power and, as a result, calls for security solutions with massive scalability. Given the reality that over 95% of web traffic today is encrypted, and the fact that inspecting encrypted traffic is a particularly compute-heavy endeavor, these scalability requirements are more critical than ever.
Unfortunately, security appliances (whether hardware or virtual) struggle to stop compromise. That’s because they have fixed capacities to service particular volumes of traffic and cannot endlessly scale up to meet organizations’ ever-growing bandwidth demands for real-time content inspection and policy enforcement—especially when it comes to encrypted traffic. As a result, these tools often end up constituting a passthrough architecture that merely generates alerts once threats have already successfully breached the organization. Amassing more appliances to increase scalability is an endless cycle that ultimately wastes money and fails to solve underlying architectural problems.
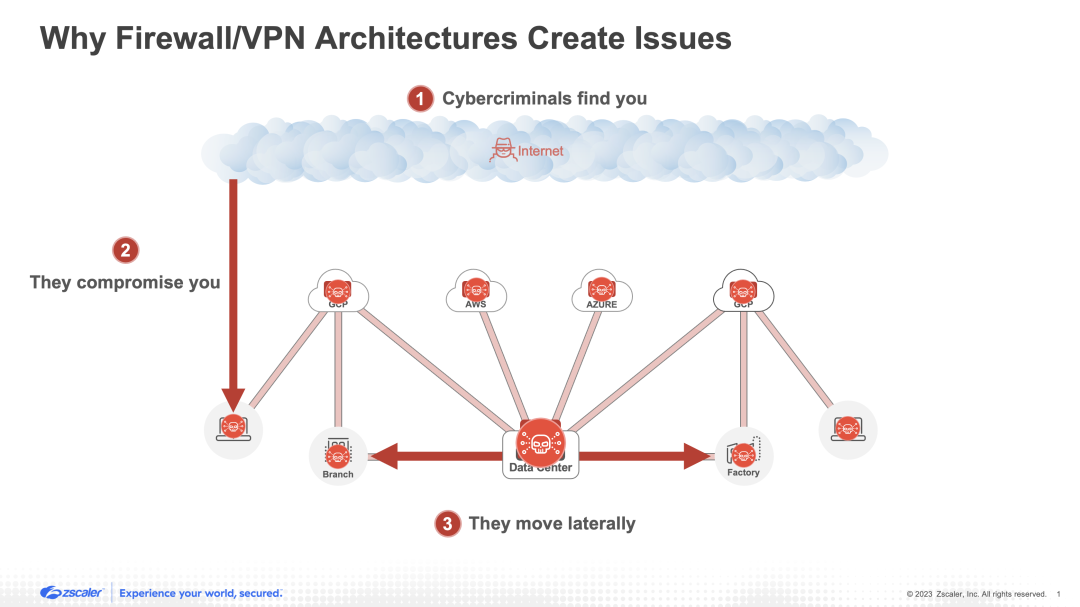
3. They allow lateral threat movement
When a threat successfully makes its way past an organization's defenses, the shortcomings of firewalls and VPNs become even more apparent. As mentioned earlier, the use of these tools indicates that an organization is relying upon a castle-and-moat style of security in an attempt to protect a highly interconnected hub-and-spoke network. In other words, defenses are concentrated on establishing a secure perimeter around the network, and there is little to no protection within the network itself. As a result, once a threat successfully enters the network, it is free to move laterally across connected resources, access what it wants, and balloon the effects of the breach. Attempting to deploy more and more tools like firewalls for microsegmentation is, once again, an endless chase that increases cost, complexity, and administrative burden, while failing to resolve the fundamental architectural weaknesses.
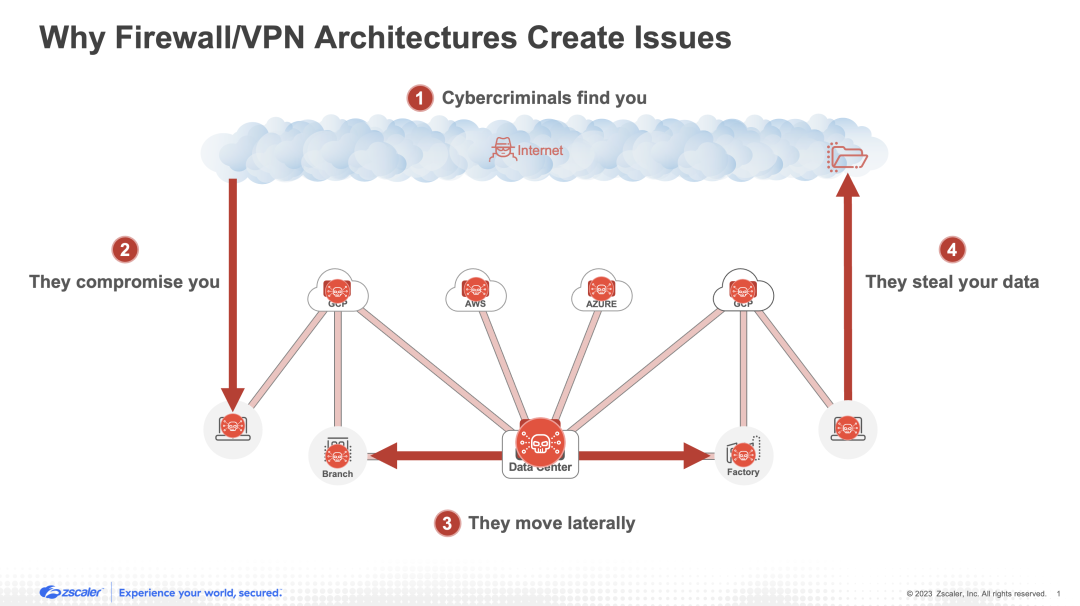
4. They fail to prevent data loss
Ultimately, a cybercriminal isn’t looking to breach an organization just for its own sake. Typically, there is a more specific goal in mind—and that goal is data. Stolen data can be sold for a hefty profit on the dark web, or, in the case of ransomware, used to extort an organization (or individuals) for money directly. Unfortunately (and for the same reasons explained in the “compromise” section above), standard firewall and VPN architectures struggle to inspect encrypted traffic, whereby sensitive data is commonly stolen. This is because SSL/TLS inspection is very resource intensive both for hardware and virtual appliances, which may lack the needed levels of performance and scalability. In addition to the above problem, legacy tools designed for the on-premises-only world are not capable of securing modern data leakage paths. Consider, for example, a SaaS application like Google Drive that allows data to be shared with risky parties, or an AWS instance with a misconfigured S3 bucket that publicly exposes sensitive information.
4 reasons to embrace a zero trust architecture
Zero trust is a fundamentally different architecture than those built upon firewalls and VPNs. It delivers security as a service from the cloud and at the edge, instead of requiring you to backhaul traffic to complex stacks of appliances (whether hardware or virtual). It provides secure any-to-any connectivity in a one-to-one fashion; for example, connecting any user directly to any application. It does not put any entities on the network as a whole, and adheres to the principle of least-privileged access. In other words, with zero trust, security and connectivity are successfully decoupled from the network, allowing you to circumvent the aforementioned challenges of perimeter-based approaches. Zero trust architecture:
- Minimizes the attack surface by eliminating firewalls, VPNs, and public-facing IP addresses, allowing no inbound connections, and hiding apps behind a zero trust cloud.
- Stops compromise by leveraging the power of the cloud to inspect all traffic, including encrypted traffic at scale, in order to enforce policies and stop threats in real time.
- Prevents lateral threat movement by connecting entities to individual IT resources instead of extending access to the network as a whole.
- Blocks data loss by enforcing policies across all potential leakage paths (including encrypted traffic), protecting data in motion, data at rest, and data in use.
And as if that wasn’t enough, zero trust architecture overcomes countless other problems of firewalls, VPNs, and perimeter-based architectures by enhancing user experiences, decreasing operational complexity, saving your organization money, enabling organizational dynamism, and more.
If you’d like to learn more, watch our webinar that serves as an introduction to zero trust and provides entry-level information about the topic.
Or, if you’d like to go a level deeper, consider registering for one of our interactive whiteboard workshops for free.
Was this post useful?
Disclaimer: This blog post has been created by Zscaler for informational purposes only and is provided "as is" without any guarantees of accuracy, completeness or reliability. Zscaler assumes no responsibility for any errors or omissions or for any actions taken based on the information provided. Any third-party websites or resources linked in this blog post are provided for convenience only, and Zscaler is not responsible for their content or practices. All content is subject to change without notice. By accessing this blog, you agree to these terms and acknowledge your sole responsibility to verify and use the information as appropriate for your needs.
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.




