Take a different approach to CTEM
Build a scalable continuous threat exposure management (CTEM) program that actually reduces risk. A holistic assessment of your attack surface enables you to manage risk across assets, data, identity, cloud, and SaaS.
The Problem
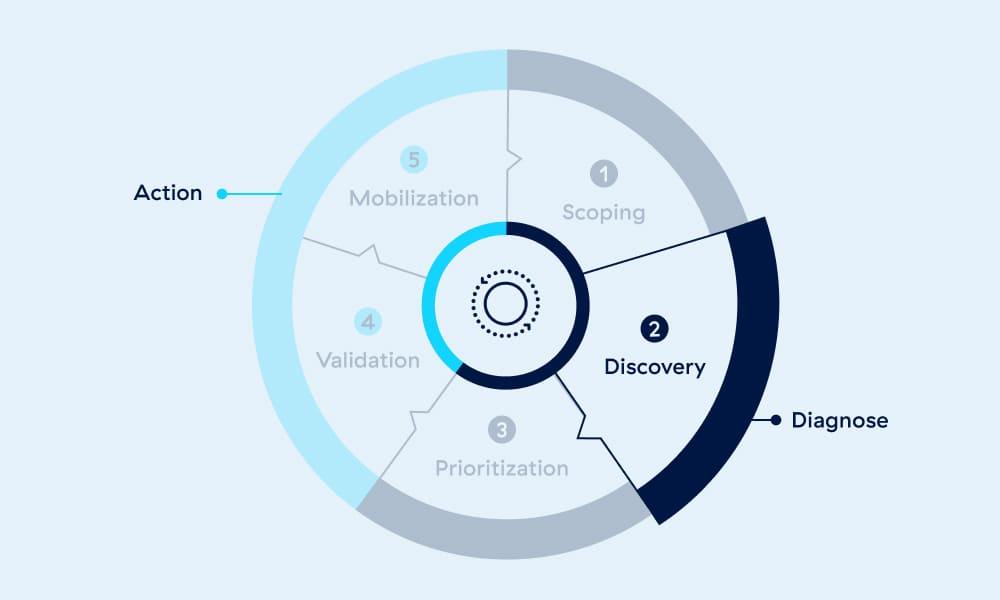
Amid evolving threats, traditional VM programs often fail to encompass the breadth of vulnerabilities or integrate mitigating controls into risk analysis. To address these gaps, Gartner recommends organizations adopt CTEM for a structured, iterative process to reduce exposures and enhance security posture.
Solution Overview
Driving the context to power your CTEM program
Exposure management is a cornerstone of proactive security, identifying and closing gaps before they become attack pathways. Zscaler Exposure Management solutions integrate asset risk, vulnerability prioritization, data security, SaaS posture, identity risk, threat hunting, and risk quantification to give you a clear view of your biggest gaps and the most efficient ways to address them.
Benefits
Holistic, continuous threat exposure management
Create a single view of asset “truth”
Ensure you have comprehensive, accurate, and context-rich asset inventory to fuel your CTEM initiatives.
Uncover all of your exposures
Bring exposures and findings across siloed security tools into one correlated, deduplicated view.
Prioritize your greatest risks
Identify your biggest exposures with contextual and customizable insights into your risk factors and mitigating controls.
Solution Details
Right-size your CTEM program's scope with no data limitations
Leverage any data point from any source system to inform risk, ensuring information is not limiting your CTEM scope. Plus, quickly assess your current security posture to identify gaps and integrate them into CTEM initiatives.

Key capabilities
Pull in risk data from anywhere to build a unified view of risk across your entire environment.
Rely on one source of contextualized data to fuel your most critical exposure management projects.
Seamlessly maintain your CTEM program as scope evolves, tools change, and new learnings emerge.
Discover all your assets and their exposures
Leverage our Data Fabric for Security to integrate feeds from numerous siloed security and IT tools. Harmonize, deduplicate, correlate, and enrich the data through our unique architecture to create a unified view of risk across your environment.
Key capabilities
Bring together all your asset information to create a holistic and accurate inventory.
See your entire external attack surface, including known and unknown assets.
Gather all your gaps and exposures from across siloed tools into one consolidated view.
Get an immediate view into the adjustments to your of Zscaler policies that would reduce risk.
Discover, classify, and protect sensitive data in your public cloud environments.
Close gaps and cloud configuration gaps as well as potential privileged access errors.
Achieve the greatest potential risk reduction with the least effort
A complete view of your assets and exposures helps you prioritize the most critical actions to reduce risk. We integrate your business context and mitigating controls to tailor the results to your unique risk profile. Rather than manually stitching together data from multiple tools, you get a focused, impactful action plan created automatically.

Key capabilities
Identify which security gaps and vulnerabilities to fix first, based on your unique environment.
Rely on pre-built risk calculations and adjust the weight of any risk factor or mitigating control based on your business needs.
Ensure the security controls you’ve deployed are factored into your risk calculation “math”.
Understand how attackers could exploit an exposed vulnerability
Validation helps security and risk management stakeholders better understand their vulnerabilities through methods like breach attack path simulation and pentesting. Zscaler Managed Threat Hunting provides 24/7 access to expert hunters who uncover anomalies, sophisticated threats, and signs of malicious activity that traditional tools might miss.

Key capabilities
Rely on a team of expert threat hunters to uncover early warning signs and prevent breaches.
Leverage red team pentesting results as a risk prioritization factor in your CTEM program.
Remediate gaps and measure your CTEM program’s success
Boost stakeholder engagement and buy-in by effectively communicating and assigning remediation priorities, automating custom workflows, providing detailed reports, and measuring ongoing risk.

Key capabilities
Utilize accurate asset and ownership details to assign remediations to the proper team.
Leverage bidirectional integrations to ticketing systems to ensure timely remediations are completed and tracked.
Easily create and distribute dashboards and reports on program status, based on your team’s KPIs, SLAs, and other metrics.
Track financial risk and compliance changes as part of reporting on your CTEM initiatives and successes.
Use Cases
Build an effective CTEM program without limits

Bring together all the data in your environment—no matter how obscure or custom the source—into an accurate, deduplicated, contextualized, and complete view of your assets and exposures.

Get a complete, accurate, and context-rich asset inventory to pinpoint misconfigurations and missing controls, and utilize automated workflows to close gaps.

Achieve accurate vulnerability analysis and risk-based prioritization with comprehensive asset visibility and context.

our platform
The Zscaler Zero Trust Exchange
Secure user, workload, and device communication between and
within the branch, cloud, and data center.
Zero Trust Everywhere
Secure Data
- Find, Classify, and Assess Data Security Posture
- Prevent Data Loss Across All Channels
Secure AI
- Secure the Use of Public AI
- Secure Private AI Apps and Models
- Secure Agent Communications
1. Gartner, Implement a Continuous Threat Exposure Management (CTEM) Program, Jeremy D'Hoinne, Pete Shoard, Mitchell Schneider, 11 October 2023.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.




