Zscaler Blog
Get the latest Zscaler blog updates in your inbox
ThreatLabz Coverage Advisory: Ivanti’s VPN Vulnerabilities Exploited by Hackers, New Zero-Days Pose Critical Risk
Introduction
Ivanti, an IT management and security company, has issued a warning about multiple zero-day vulnerabilities in its VPN products exploited by Chinese state-backed hackers since December 2023. The initial disclosure involved two CVEs (CVE-2023-46805 and CVE-2024-21887) allowing a remote attacker to perform authentication bypass and remote command injection exploits. Ivanti released a patch which was immediately bypassed by two additional flaws (CVE-2024-21888 and CVE-2024-21893) that allows an attacker to perform privilege escalation and server-side request forgery exploits.
The Cybersecurity & Infrastructure Security Agency (CISA) released an initial advisory as well as an emergency directive (ED-24-01) setting the timeline for mitigating the original two issues by 11:59PM EST January 22, 2024. In the wake of the two new vulnerabilities being discovered and no patches available, CISA issued a supplemental direction to the emergency directive instructing Federal Civilian Executive Branch agencies to disconnect all instances of Ivanti Connect Secure (ICS) and Ivanti Policy Secure (IPS) solutions no later than 11:59 PM EST February 2, 2024 from agency networks.
Recommendations
For CVE-2023-46805 and CVE-2024-21887
- Apply the patch: Ivanti released a patch to address the initial two vulnerabilities. Users are advised to apply this patch promptly to secure their systems.
- Factory reset before patch: Ivanti recommends users to perform a factory reset on their appliance before applying the patch. This precautionary step aims to prevent potential threat actors from gaining upgrade persistence in the environment.
For CVE-2024-21888 and CVE-2024-21893
- CISA supplemental direction (ED-24-01): CISA instructed federal agencies to disconnect all instances of Ivanti Connect Secure (ICS) and Ivanti Policy Secure (IPS) solutions from agency networks. Although the CISA guidance mandates this for FCEB agencies, CISA highly recommends all organizations to follow the recommended steps.
- Apply the patches as they become available following the recommended guidance.
For all discovered issues
- Prioritize segmentation of all potentially impacted systems from enterprise resources to reduce the blast radius.
- Continue threat hunting activity for all devices connected to and from the impacted Ivanti products.
- Monitor identity management services and authentication anomalies.
- Actively audit privileged accounts that were recently created or updated.
- Rotate certificates, keys, and passwords for all connected or exposed systems and applications.
Attribution
UTA0178, China’s government-backed hacking group motivated by espionage, is believed to be responsible for exploiting vulnerabilities in ICS VPN. The same group was attributed to the attacks concentrating on the Philippines using the MISTCLOAK, BLUEHAZE, and DARKDEW malware families.
How It Works
The attackers were observed exploiting two vulnerabilities CVE-2023-46805 (an authentication-bypass vulnerability with a CVSS score of 8.2) and CVE-2024-21887 (a command-injection vulnerability found in multiple web components with a CVSS score of 9.1) to gain access to ICS VPN appliances. Initial activity was observed as early as December 3, 2023. They were mostly living off the land but some tools were also deployed.
Tools used by the threat actor include:
- PySoxy tunneler and BusyBox to enable post-exploitation activity
- ZIPLINE Passive Backdoor
- THINSPOOL Dropper
- LIGHTWIRE
- WIREFIRE, BUSHWALK, and CHAINLINE Web Shells
- WARPWIRE
Attack Chain

Figure 1: Diagram depicting the attack chain
Possible Execution
- Initial Exploitation: The attackers performed mass scanning for vulnerable devices and potential automated exploitation.
- Persistence: The attackers deployed different variations of web shells on the targeted devices after successful exploitation. After gaining an initial foothold, the attacker could steal configuration data, modify existing files, download remote files, and reverse tunnel from the devices. In addition, the attackers backdoored configuration files and deployed additional tools.
- Reconnaissance: The attackers performed reconnaissance of the internal systems and applications through proxied connections.
- Credential Stealing: The attackers injected a custom JavaScript-based malware, called WARPWIRE, into a login page used by the users to capture and exfiltrate plaintext credentials.
- Lateral Movement: The attackers used lateral movement using compromised credentials to connect to internal systems via RDP, SMB, and SSH.
- Evidence Wiping: The attackers were observed wiping logs and even restoring the system to a clean state after deploying their payloads.
- Evasion (Patch and Detection): In some instances, the attackers modified the integrity checker tool (ICT) to disable and prevent it from flagging any modifications or additions on the system as a measure to evade detection. The ZIPLINE tool used by the attackers is capable of bypassing ICT detection by adding itself to the exclusion_list used by the ICT tool. Moreover, as the attacks were discovered and publicized, the attackers quickly adapted by modifying the tools to evade detection. As a result, new variants of the initial-attack are being observed in more recent attacks.
How Zscaler Can Help
Zscaler’s cloud native zero trust network access (ZTNA) solution gives users fast, secure access to private apps for all users, from any location. Reduce your attack surface and the risk of lateral threat movement—no more internet-exposed remote access IP addresses, and secure inside-out brokered connections. Easy to deploy and enforce consistent security policies across campus and remote users.
Zscaler Private Access™ (ZPA) allows organizations to secure private app access from anywhere. Connect users to apps, never the network, with AI-powered user-to-app segmentation. Prevent lateral threat movement with inside-out connections.
- Deploy comprehensive cyberthreat and data protection for private apps with integrated application protection, deception, and data protection.
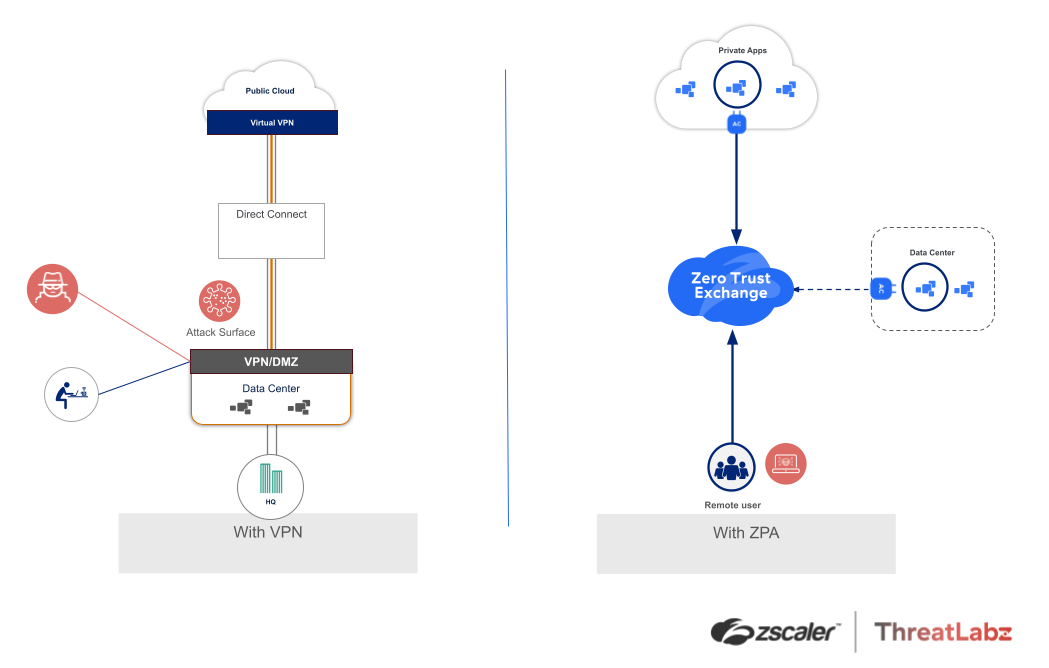
Figure 2: VPN vulnerabilities open doors to cyber threats, protect against these risks with Zero Trust architecture.
Zero trust is a fundamentally different architecture than those built upon firewalls and VPNs. It delivers security as a service from the cloud and at the edge, instead of requiring you to backhaul traffic to complex stacks of appliances (whether hardware or virtual). It provides secure any-to-any connectivity in a one-to-one fashion; for example, connecting any user directly to any application. It does not put any entities on the network as a whole, and adheres to the principle of least-privileged access. In other words, with zero trust, security and connectivity are successfully decoupled from the network, allowing you to circumvent the aforementioned challenges of perimeter-based approaches. Zero trust architecture:
- Minimizes the attack surface by eliminating firewalls, VPNs, and public-facing IP addresses, allowing no inbound connections, and hiding apps behind a zero trust cloud.
- Stops compromise by leveraging the power of the cloud to inspect all traffic, including encrypted traffic at scale, in order to enforce policies and stop threats in real-time.
- Prevents lateral threat movement by connecting entities to individual IT resources instead of extending access to the network as a whole.
- Blocks data loss by enforcing policies across all potential leakage paths (including encrypted traffic), protecting data in motion, data at rest, and data in use.
Additionally, zero trust architecture overcomes countless other problems associated with firewalls, VPNs, and perimeter-based architectures by enhancing user experiences, decreasing operational complexity, saving your organization money, and more.
Zscaler ThreatLabz recommends our customers implement the following capabilities to safeguard against these type of attacks:
- Safeguard crown jewel applications by limiting lateral movement using Zscaler Private Access to establish user-to-app segmentation policies based on the principles of least privileged access, including for employees and third-party contractors.
- Limit the impact from a potential compromise by restricting lateral movement with identity-based microsegmentation.
- Prevent private exploitation of private applications from compromised users with full in-line inspection of private app traffic with Zscaler Private Access.
- Use Advanced Cloud Sandbox to prevent unknown malware delivered in second stage payloads.
- Detect and contain attackers attempting to move laterally or escalate privileges by luring them with decoy servers, applications, directories, and user accounts with Zscaler Deception.
- Identify and stop malicious activity from compromised systems by routing all server traffic through Zscaler Internet Access.
- Restrict traffic from critical infrastructure to an “allow” list of known-good destinations.
- Ensure that you are inspecting all SSL/TLS traffic, even if it comes from trusted sources.
- Turn on Advanced Threat Protection to block all known command-and-control domains.
- Extend command-and-control protection to all ports and protocols with the Advanced Cloud Firewall, including emerging C&C destinations.
Best Practices
Follow CISA Directives
Timely compliance with CISA’s Emergency Directive on Ivanti Vulnerabilities is critical for minimizing the impact of these vulnerabilities.
Implement zero trust architecture
Enterprises must rethink traditional approaches to security, replacing vulnerable appliances like VPNs and firewalls. Implementing a true zero trust architecture, fortified by AI/ML models, to block and isolate malicious traffic and threats is a critical foundational step. Prioritize user-to-application segmentation where you are not bringing users on the same network as your applications. This provides an effective way to prevent lateral movement and keep attackers from reaching crown jewel applications.
Proactive Measures to Safeguard Your Environment
In light of the recent vulnerabilities affecting Ivanti, it is imperative to employ the following best practices to fortify your organization against potential exploits.
- Minimize the attack surface: Make apps (and vulnerable VPNs) invisible to the internet, and impossible to compromise, ensuring an attacker can’t gain initial access.
- Prevent initial compromise: Inspect all traffic in-line to automatically stop zero-day exploits, malware, or other sophisticated threats.
- Enforce least privileged access: Restrict permissions for users, traffic, systems, and applications using identity and context, ensuring only authorized users can access named resources.
- Block unauthorized access: Use strong multi-factor authentication (MFA) to validate user access requests.
- Eliminate lateral movement: Connect users directly to apps, not the network, to limit the blast radius of a potential incident.
- Shutdown compromised users and insider threats: Enable inline inspection and monitoring to detect compromised users with access to your network, private applications, and data.
- Stop data loss: Inspect data in motion and data at rest to stop active data theft during an attack.
- Deploy active defenses: Leverage deception technology with decoys and perform daily threat hunting to derail and capture attacks in real-time.
- Cultivate a security culture: Many breaches begin with compromising a single user account via a phishing attack. Prioritizing regular cybersecurity awareness training can help reduce this risk and protect your employees from compromise.
- Test your security posture: Get regular third-party risk assessments and conduct purple team activities to identify and harden the gaps in your security program. Request that your service providers and technology partners do the same and share the results of these reports with your security team.
Conclusion
In conclusion, Ivanti’s VPN products face severe security threats due to multiple zero-day vulnerabilities exploited by state-backed hackers. The initial disclosure revealed critical CVEs allowing unauthorized access and remote command injections. Following Ivanti’s patch release, two additional flaws enabling privilege escalation were swiftly exploited by the threat actors.
CISA has responded with an advisory and emergency directive, setting deadlines for mitigating the original issues. With the discovery of new vulnerabilities and the absence of patches, CISA issued a supplemental directive, mandating Federal agencies to disconnect Ivanti ICS and IPS solutions from networks by 11:59pm EST, February 2, 2024.
Was this post useful?
Disclaimer: This blog post has been created by Zscaler for informational purposes only and is provided "as is" without any guarantees of accuracy, completeness or reliability. Zscaler assumes no responsibility for any errors or omissions or for any actions taken based on the information provided. Any third-party websites or resources linked in this blog post are provided for convenience only, and Zscaler is not responsible for their content or practices. All content is subject to change without notice. By accessing this blog, you agree to these terms and acknowledge your sole responsibility to verify and use the information as appropriate for your needs.
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.



