Zscaler + Endpoint
Zscaler works with endpoint and mobility solution partners to enable end-to-end zero trust access control, threat detection, and response as well as ensure compatibility with various mobile device agents.
Mobile and unified endpoint management
It takes time and resources to translate disjointed data points and intelligence into real actionable insights.
Ineffective technology
Access without context
Fragmented data
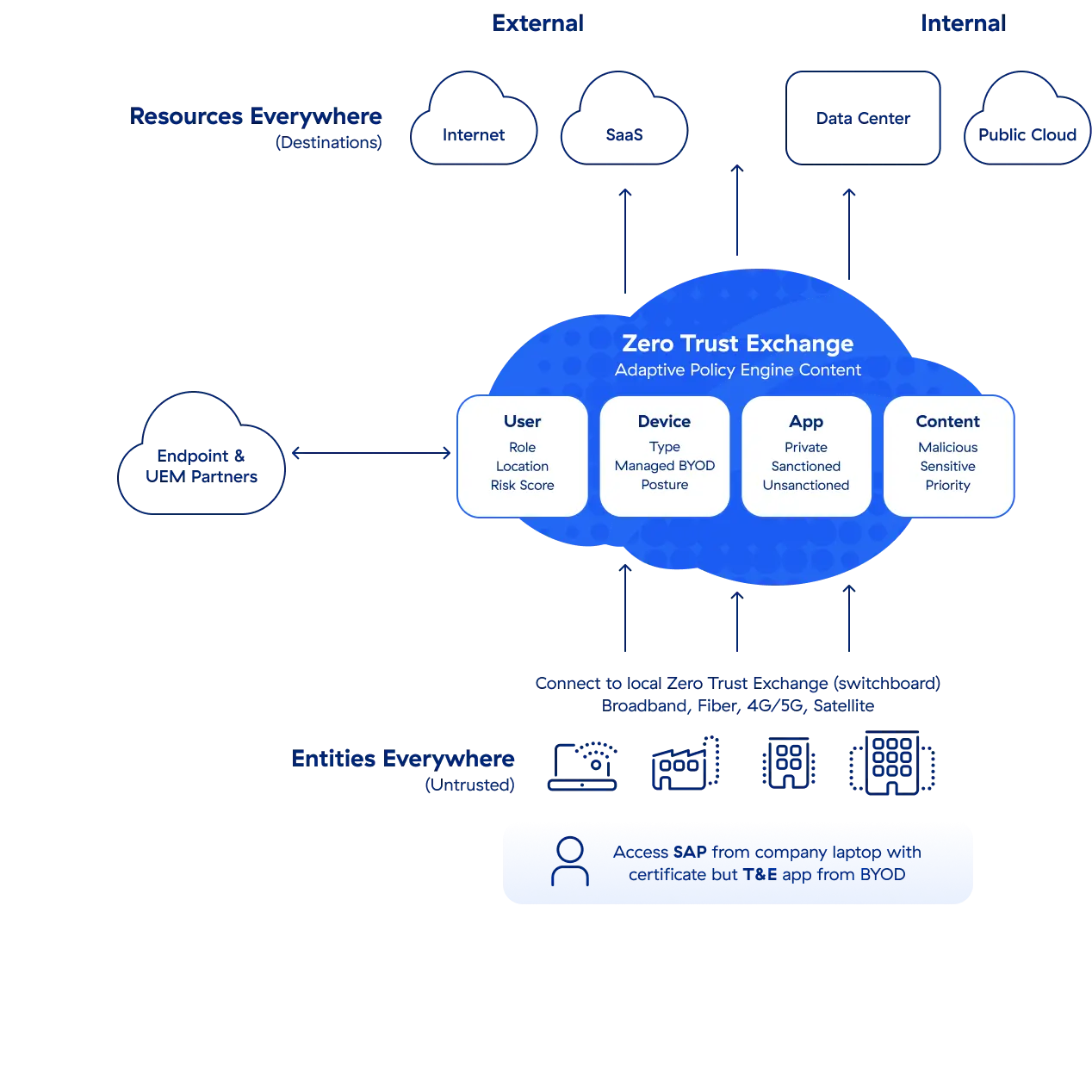
Zero trust with endpoint security
We integrate with industry-leading endpoint solution partners to provide zero trust access control based on device posture as well as enhance detection, investigation, and response capabilities—no matter where users and apps are—through telemetry and intelligence sharing. We support compatibility between Zscaler Client Connector and various mobility management agents for devices.
Endpoint security
Zscaler works with endpoint security innovators to enable end-to-end threat detection, intel sharing, remediation, and device posture-driven access control to all on-premises and cloud apps.
Comprehensive visibility with XDR
Our XDR alliances use integration and advanced AI/ML to provide high-fidelity threat intelligence and context for faster, more effective detection and response across platforms, enabling end-to-end visibility.
Enterprise mobility management
Zscaler integrates with value-added EMM partners to ensure seamless operations and policy controls for mobile and IoT security on devices.
Internet of Things (IoT)
Zscaler integrates with IoT-focused endpoint partners to ensure seamless operations and policy controls for IoT devices.
Endpoint OS
Zscaler works with Endpoint OS leaders to enable secure, cost-effective, and agentless solutions for remote and hybrid work on individual and shared workstations.

Improving protection and reducing support burden with Zscaler, CrowdStrike, and Okta

Deploying zero trust security in nine days with Zscaler

Realizing end-to-end zero trust transformation with CrowdStrike and Zscaler