Blog de Zscaler
Reciba en su bandeja de entrada las últimas actualizaciones del blog de Zscaler
SuscribirseThreatLabz Discovers 117 Vulnerabilities in Microsoft 365 Apps Via the SketchUp 3D Library - Part 2
Introduction
In Part 1 of this series, we’ve demonstrated how ThreatLabz reverse engineered the SketchUp 3D library in Microsoft 365 as well as the SKP file format. Furthermore, we developed two effective fuzzing harnesses.
Microsoft published CVE-2023-28285 and CVE-2023-29344 (in April and May of 2023, respectively) to address the vulnerabilities identified by the Zscaler ThreatLabz research team. The ThreatLabz research team analyzed the patch for CVE-2023-29344 and discovered a bypass, which in turn, led to Microsoft addressing the vulnerabilities through CVE-2023-33146. In this blog, we examine how it was possible to bypass CVE-2023-29344. In addition, we analyze real-world case studies to gain further insight into how these vulnerabilities impact security.
How to Bypass CVE-2023-29344
Watch the video
In the following video, we show how CVE-2023-29344 can be bypassed, which led to the release of CVE-2023-33146.

How to Bypass CVE-2023-29344
Read the write-up
In May of 2023, the patch for CVE-2023-29344 was released and was intended to fix all vulnerabilities located in FreeImage. The patched version of MSOSPECTRE.DLL is 16.0.16327.20240, as shown in the figure below.
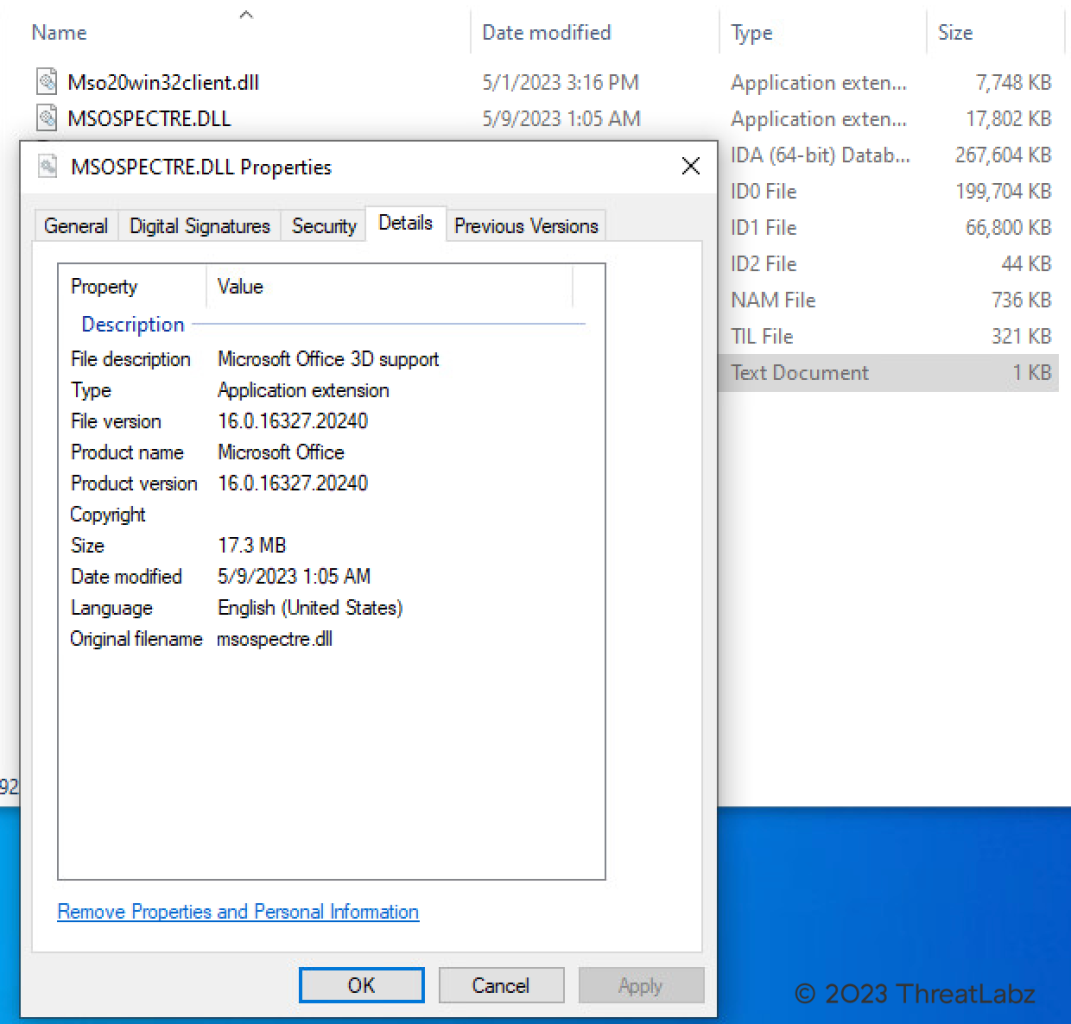
Figure 1: The patched version of MSOSPECTRE.DLL for CVE-2023-29344
First, let’s explore the details of the patch for CVE-2023-29344.
The figure below shows the comparison of SketchUpModelReader::ReadModel before and after the patch.
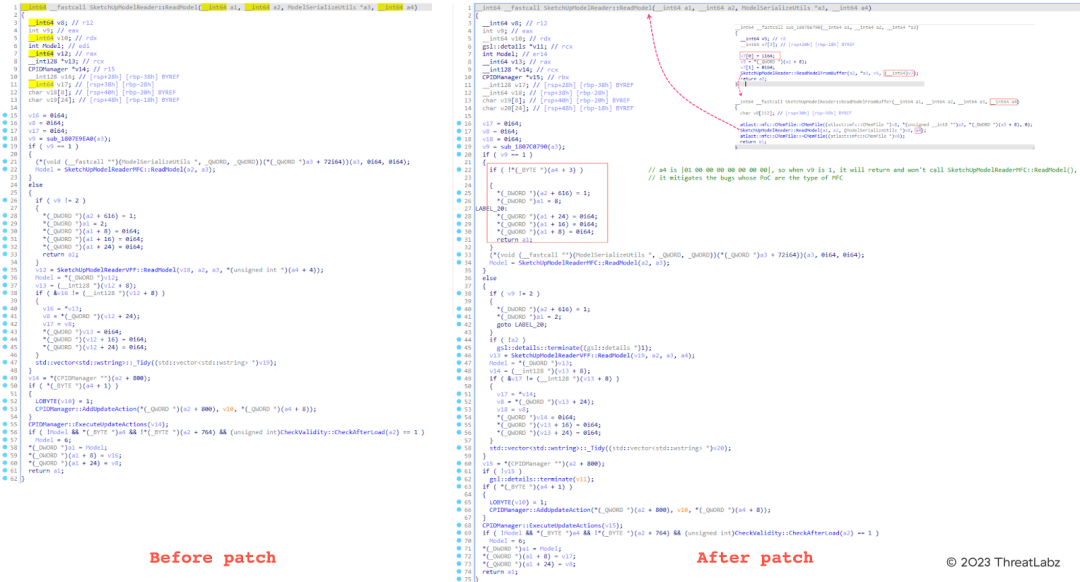
Figure 2: The comparison of SketchUpModelReader::ReadModel before and after the patch.
This patch introduced some code changes to disable support for SKP files with the MFC type. This is because all vulnerabilities in FreeImage were reported to Microsoft through the SKP files with the MFC type. Accordingly, Microsoft fixed these vulnerabilities by disabling support for SKP files with the MFC type, rather than fixing the underlying issues within the FreeImage library. As a result, this patch is incomplete, because these vulnerabilities in the FreeImage library could still be triggered using SKP files with the VFF type.
Next, let’s take a look at the process of bypassing the patch for CVE-2023-29344.
The figure below shows a Proof-of-Concept (PoC) crafting template for an SKP file with the VFF type, which includes a SketchUp header, a VFF header, and an embedded zip file. All data related to SketchUp 3D models are stored within a zip file.
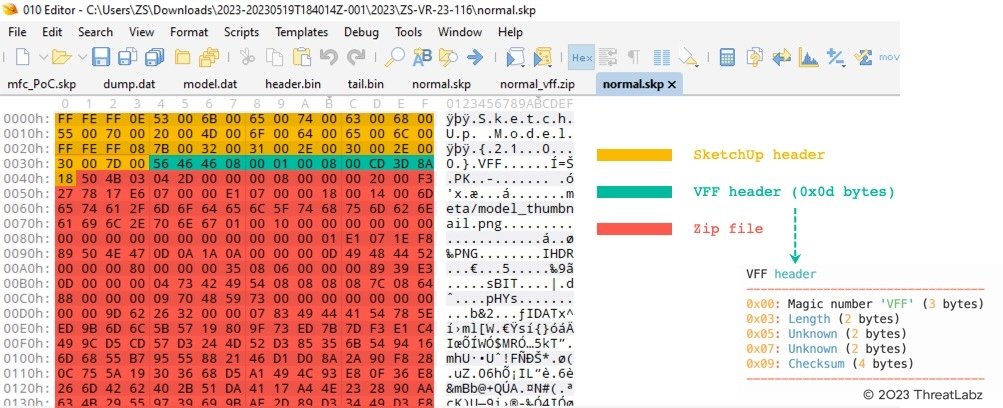
Figure 3: A PoC crafting template for SKP file with the VFF type
We extract the part of the zip file within an SKP file and then analyze it using the zip template in 010 Editor. The result of the parsing operation reveals an image stored within the materials folder.
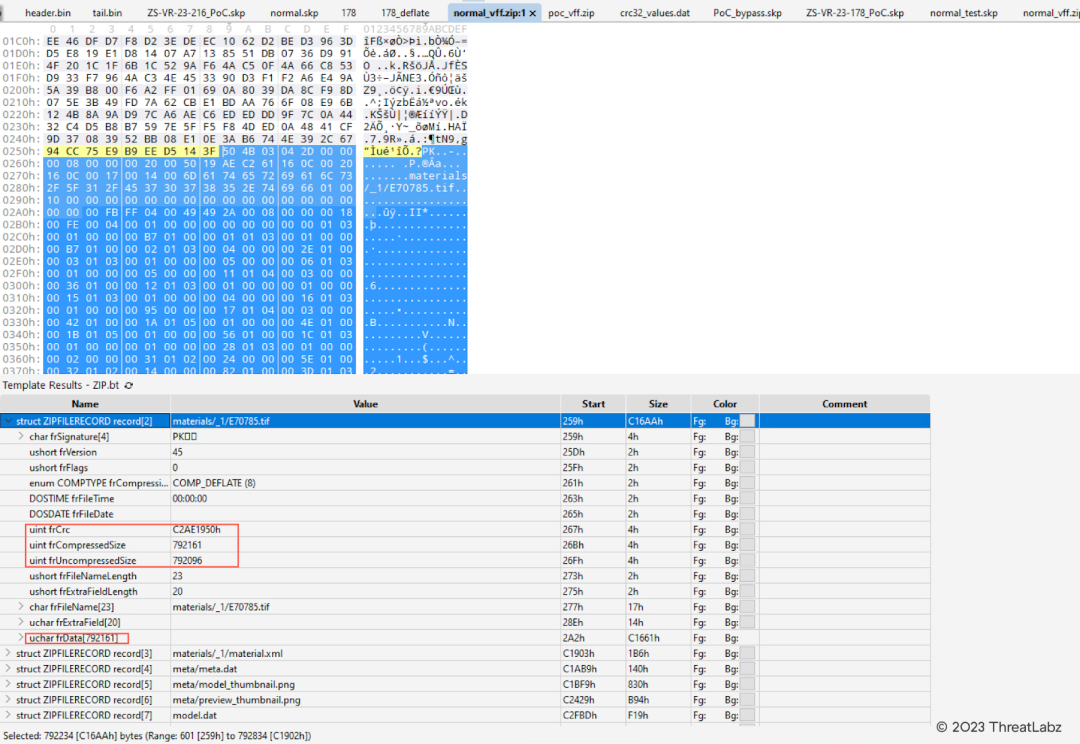
Figure 4: Analyzing the zip file embedded in the SKP file using the ZIP template in 010 Editor
Craft a new PoC.
- Compress the abnormal image file using the Deflate algorithm.
zlib.compressobj(compresslevel, zlib.DEFLATED, -zlib.MAX_WBITS, zlib.DEF_MEM_LEVEL, 0).compress(data)
- Calculate the new CRC32 for the uncompressed image data. We can use 010 Editor’s CRC32 tool or Windows built-in CRC utility.
- Update the fields frCrc, frCompressSize, frUncompressSize, and frData (compressed image data)
- Update the field deHeaderOffset for each dirEntry, and also update the fields deCrc, deCompressSize, and deUncompress in struct ZIPDIRENTRY dirEntry[4] materials/_1/E70785.tif. Update the field erDirectoryOffset in the struct ZIPENDLOCATOR endLocator
- Combine the SketchUp header, VFF header, and the modified zip file into a complete SKP file.
- Finally, we need to re-calculate the checksum in the VFF header. We uncovered a specific algorithm responsible for computing this checksum. Figure 6 shows a pseudo-code representation of this algorithm.
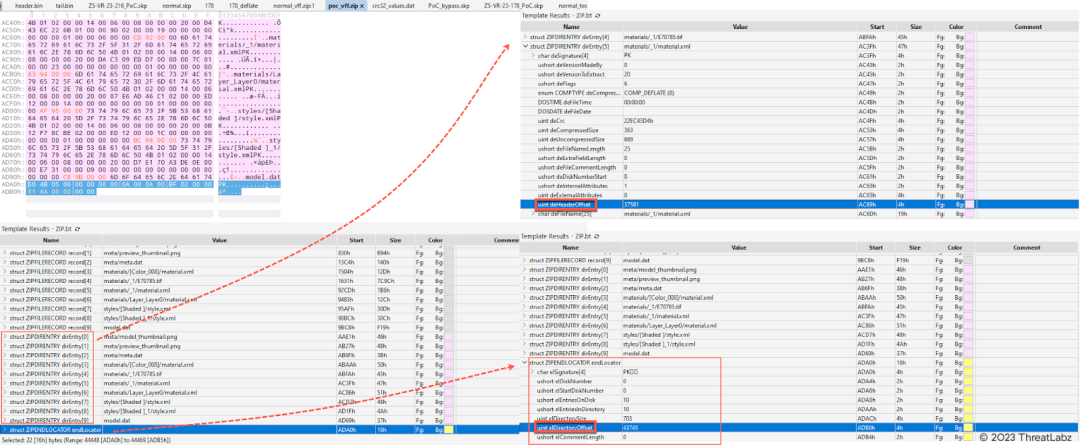
Figure 5: The parsing result in 010 Editor
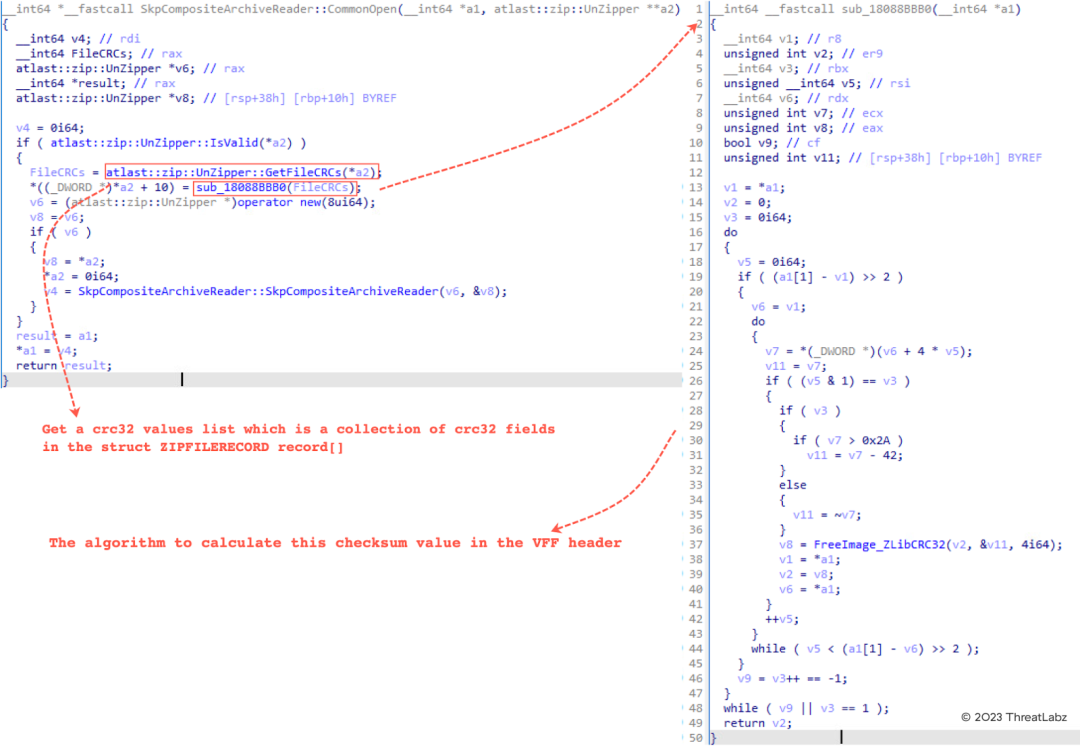
Figure 6: The specific algorithm responsible for computing this checksum in a VFF header
So far, we’ve elaborated on the steps of crafting the new PoC to bypass the patch for CVE-2023-29344. With this approach, we reproduced 97 unique vulnerabilities in Microsoft 365 apps updating to the patch of CVE-2023-29344. Microsoft assigned CVE-2023-33146 for this discovery which bypassed the original patch.
Finally, Microsoft disabled the ability to insert SketchUp files in Office documents in the patch for CVE-2023-33146.

A screenshot of the Microsoft update
Real-World Cases
Microsoft Office SKP file parsing `CVertex` object use-after-free vulnerability
The figure below shows a use-after-free vulnerability that is associated with the parsing of an abnormal SKP file in Microsoft Office.
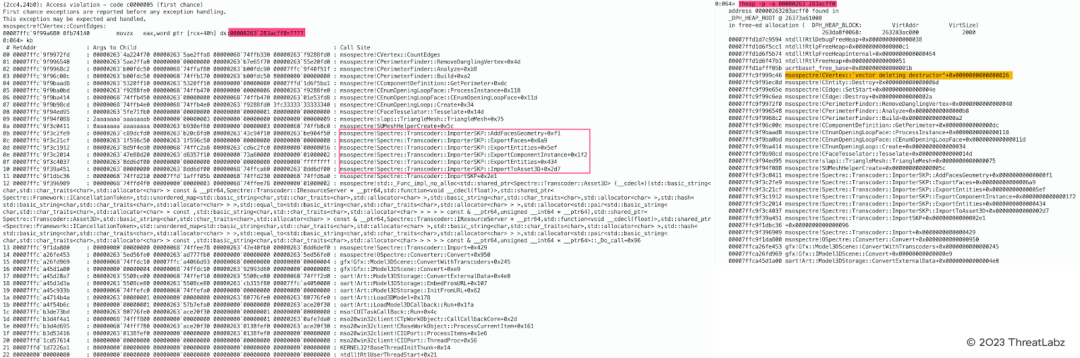
Figure 7: Microsoft Office SKP File Parsing `CVertex` object Use-After-Free Vulnerability
Microsoft Office SKP file parsing TIFF image integer overflow vulnerability
The figure below shows an integer overflow vulnerability that is associated with the parsing of an SKP file containing an abnormal TIFF image in Microsoft Office. This vulnerability ultimately results in a crash within the memcpy function.
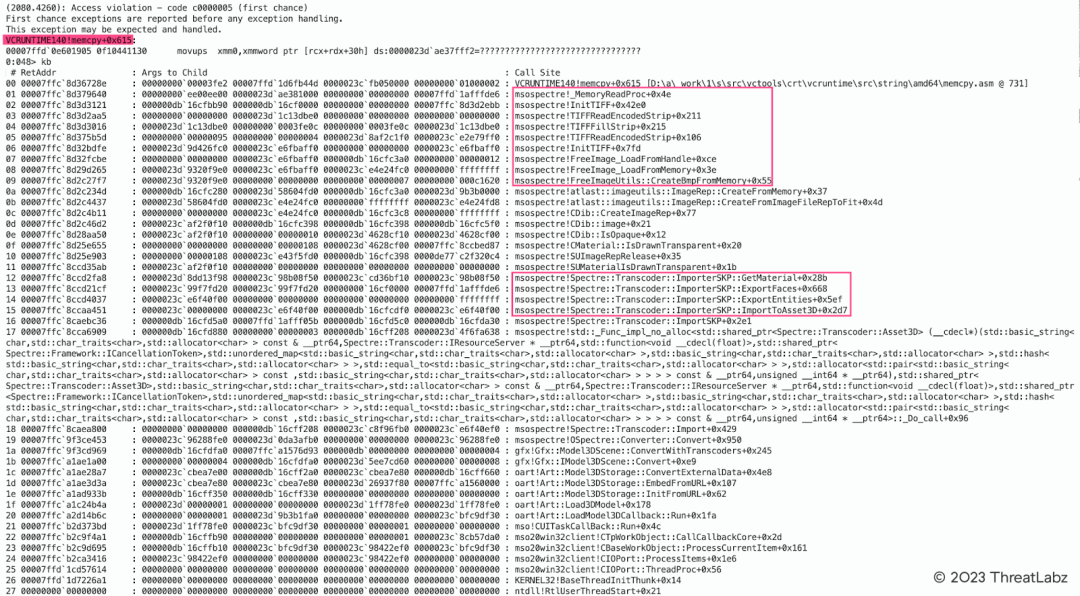
Figure 8: Microsoft Office SKP File Parsing TIFF Image Integer Overflow Vulnerability
Microsoft Office SKP file parsing uninitialized memory vulnerability
The figure below shows an uninitialized memory vulnerability that is associated with the parsing of an abnormal SKP file in Microsoft Office. This vulnerability potentially results in remote code execution.
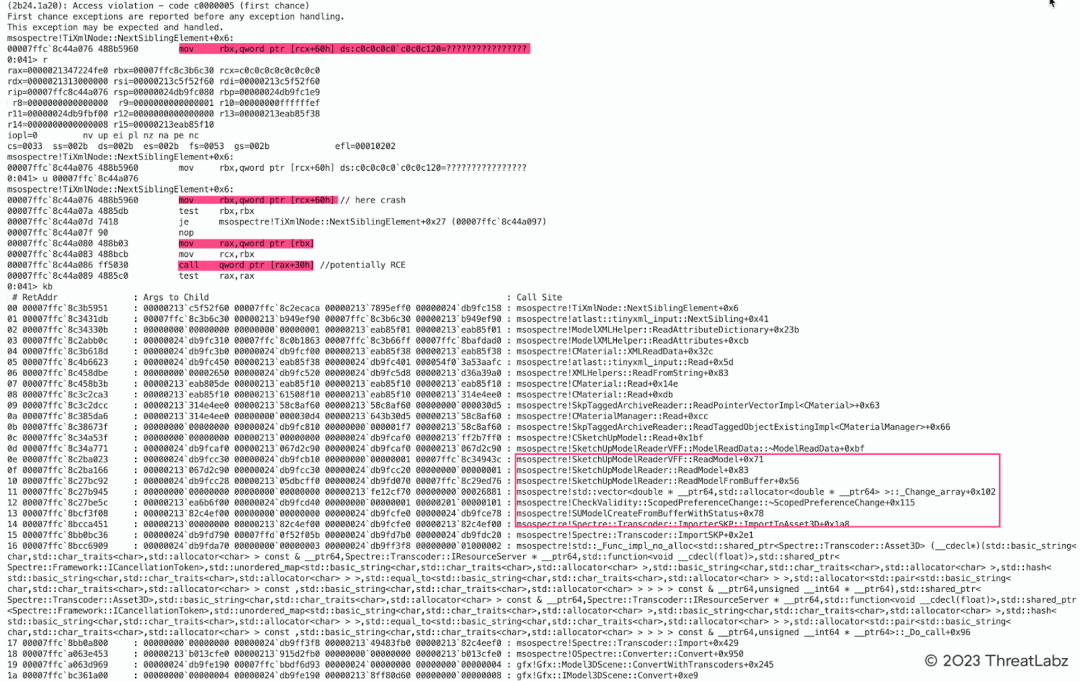
Figure 9: Microsoft Office SKP File Parsing Uninitialized Memory Vulnerability
Microsoft Office SKP File parsing BMP image out-of-bounds write vulnerability
The figure below shows an out-of-bounds write vulnerability that is associated with the parsing of an SKP file containing an abnormal BMP image in Microsoft Office.
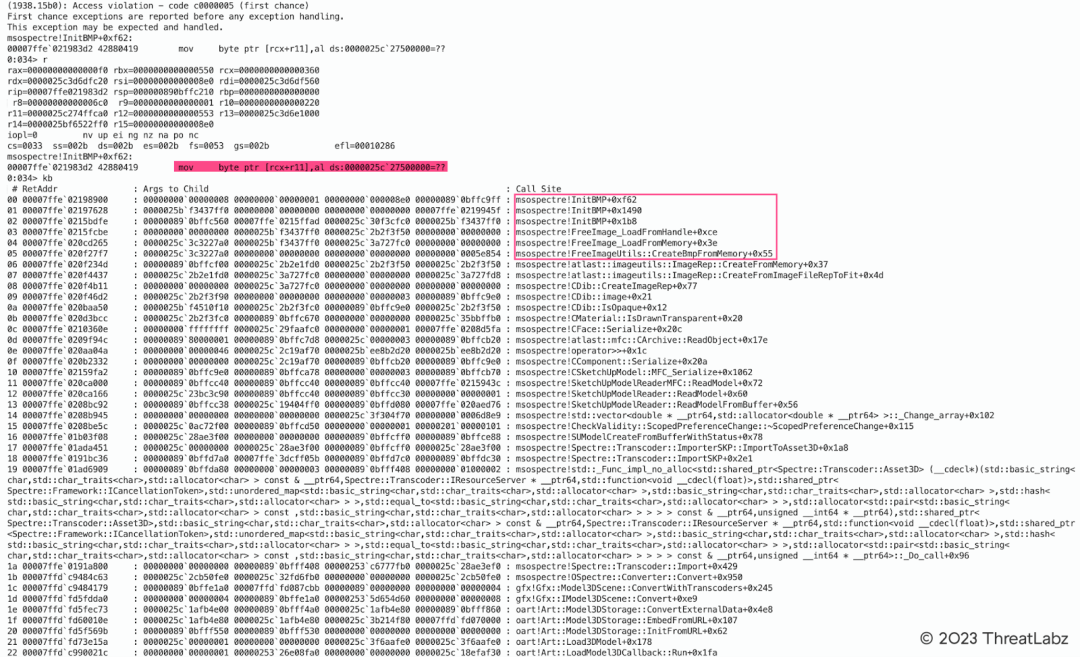
Figure 10: Microsoft Office SKP File Parsing BMP Image Out-of-Bounds Write Vulnerability
Microsoft Office SKP File parsing PICT image out-of-bounds write vulnerability
The figure below shows an out-of-bounds write vulnerability (CVE-2023-29344) that is associated with the parsing of an SKP file containing an abnormal PICT image in Microsoft Office. The PoC file for this vulnerability is an SKP file with the MFC type.
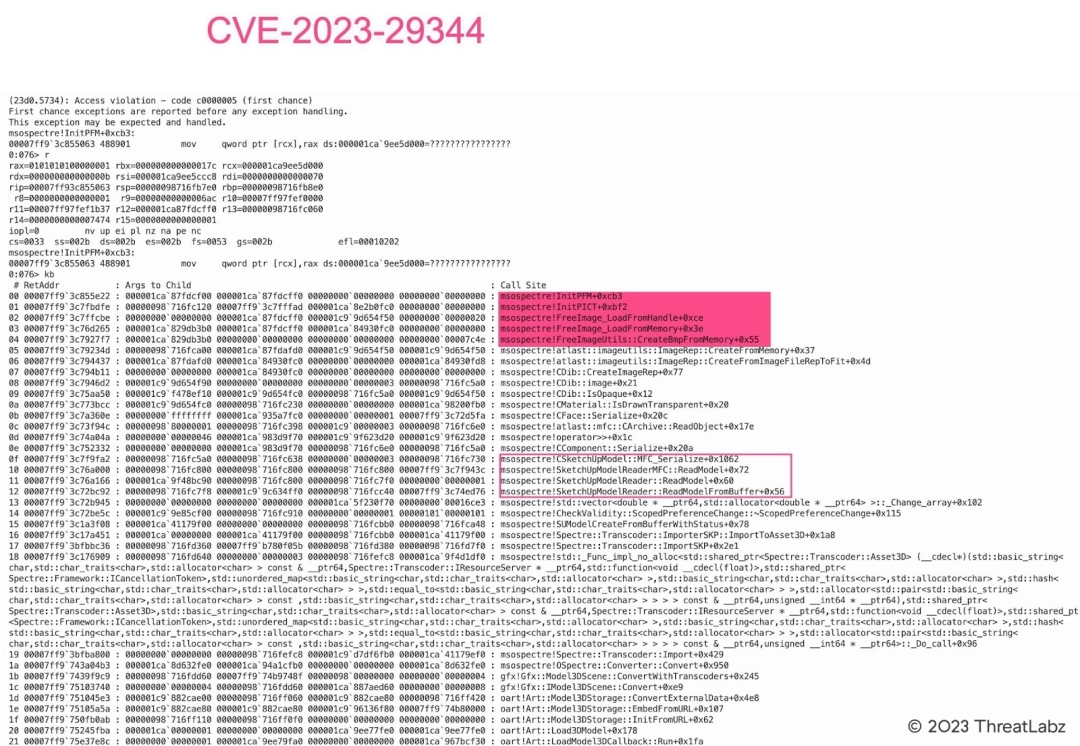
Figure 11: Microsoft Office SKP File Parsing PICT Image Out-of-Bounds Write Vulnerability (PoC with MFC type)
In Figure 12, we observe the bypass of CVE-2023-29344 using an SKP file with the VFF type.
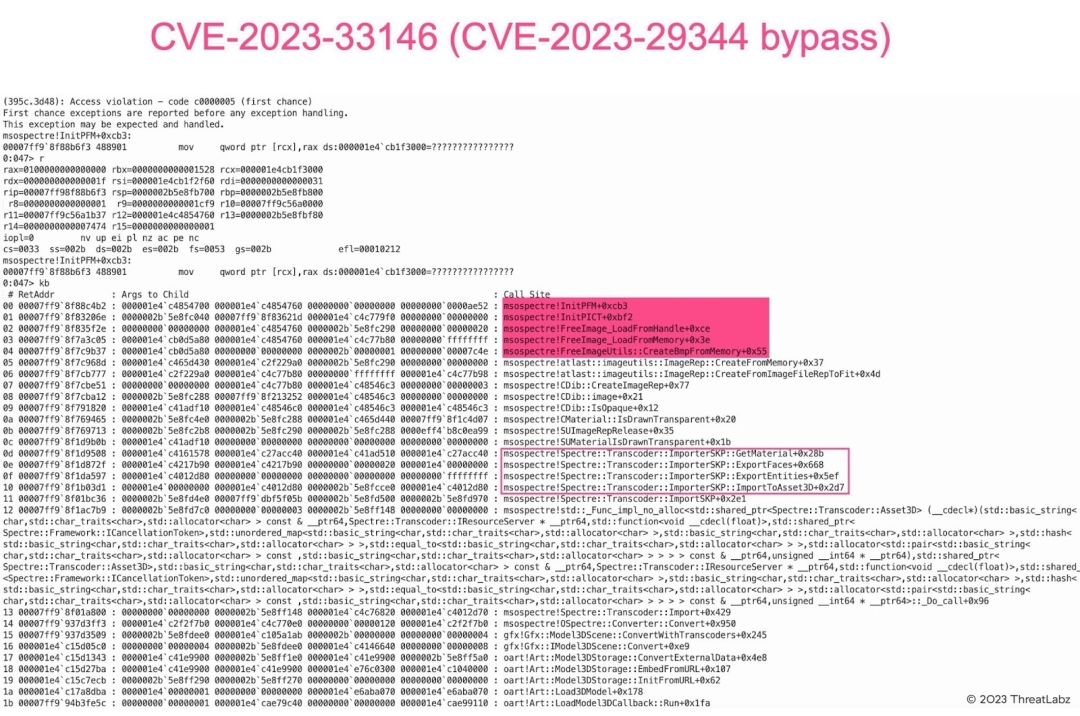
Figure 12: Microsoft Office SKP File Parsing PICT Image Out-of-Bounds Write Vulnerability (PoC with VFF type)
Conclusion
In this two part series, we’ve walked you through the process of reverse engineering the Office 3D component, and we’ve also explored how to create two effective fuzzing harnesses, one for SketchUp and the other for FreeImage. The results have been highly effective. We discovered 117 unique vulnerabilities within the Office 3D component in Microsoft 365 apps in approximately three months. These security vulnerabilities demonstrate the importance of performing security code audits and blackbox fuzzing for third-party libraries before they are introduced into a new or existing product.
Mitigation
All users of Microsoft 365 apps are encouraged to upgrade to the latest version of the software. Zscaler’s Advanced Threat Protection and Advanced Cloud Sandbox can protect customers against these vulnerabilities as follows:
Appendix
The following vulnerabilities were discovered and reported by ThreatLabz while fuzzing the SketchUp library in Microsoft 365 applications.
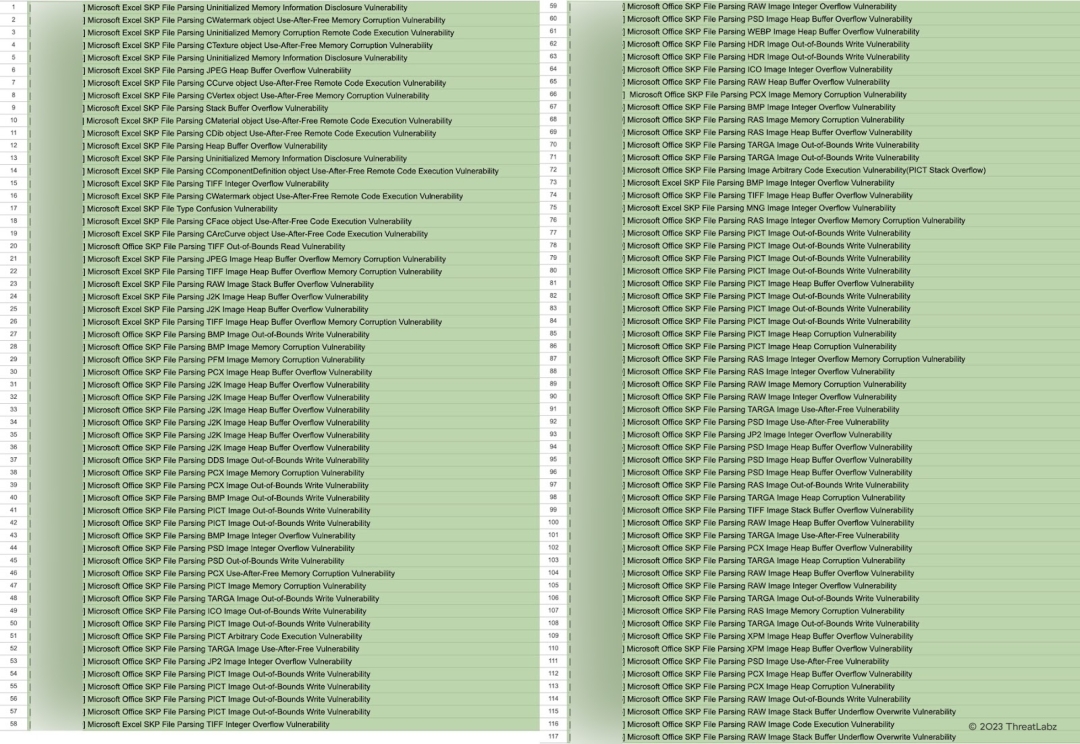
References
- https://www.adobe.com/creativecloud/file-types/image/vector/skp-file.html
- https://insider.microsoft365.com/en-us/blog/add-sketchup-files-to-office-creations
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-33146
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-28285
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-29344
- https://msrc.microsoft.com/blog/2023/04/congratulations-to-the-top-msrc-2023-q1-security-researchers/
- https://www.zerodayinitiative.com/advisories/published/2022/
- https://freeimage.sourceforge.io/
- https://sketchup.cgtips.org/
- https://www.g2.com/reports/grid-report-for-architecture-spring-2023.embed?featured=sketchup&secure%5Bgated_consumer%5D=2a23be4d-2a72-444a-9ad7-cdc55120636c&secure%5Btoken%5D=e98cea6efb6f05c7a9cf8335d15f112eadc67748340a634576f6bd49c2d718a0&utm_campaign=gate-1886690
¿Este post ha sido útil?
Reciba las últimas actualizaciones del blog de Zscaler en su bandeja de entrada
Al enviar el formulario, acepta nuestra política de privacidad.



