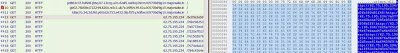
We recently found a number of compromised pages following the structure of fake search engine pages. The following sites have been seen to redirect to malicious content:
- hymedoraw[dot]com/search[dot]php
- awerdeall[dot]com/search[dot]php
- index-html[dot]com/
- joomla-green[dot]com/
- bestcool-search[dot]com/
- joyo-search[dot]com/
- megas-search[dot]com/
- speeds-search[dot]com/
- sample-data[dot]com/
- lazy-summer[dot]com/
- tundra-search[dot]com/
- death-tostock[dot]com/
- adoncorst[dot]com/search[dot]php
- demo-content[dot]com/
- enable-bootstrap[dot]com/
- rospecoey[dot]com/search[dot]php
- aranfleds[dot]com
- adoncorst[dot]com/search[dot]php
- malpithia[dot]com/search[dot]php
- noutademn[dot]com/search[dot]php
- click2[dot]systemaffiliate[dot]com/filter/?keyword=Area+Rugs+Cleaning+hotels+for+sale+by+owner
- b7b6o[dot]y2ff[dot]3b1f767u[dot]dc[dot]3d478d[dot]t97a2as[dot]pdf0q[dot]zf1[dot]eaq6907579[dot]hatentries[dot]in/?17657271747b7e747c2539646e6463727a7671717e7b7e7663723974787a
- click2[dot]systemaffiliate[dot]com/filter/?keyword=backhoes+for+sale+Granite+Counter+Tops
- nd4e61i[dot]0fedz[dot]i9390[dot]11f[dot]b8e0[dot]c1i[dot]51aa8a5x[dot]b22n[dot]z1037n6z[dot]rulesreturning[dot]in/?3f4d5a595c53565c540d114c464c4b5a525e59595653565e4b5a115c5052
- click2[dot]systemaffiliate[dot]com/filter/?keyword=direct+tv+dallas+tx+financial+services+companies
- kfb39c[dot]ec526[dot]k149t[dot]13f44d[dot]gfb9820[dot]q5c[dot]c778eg[dot]c47b0v3diz2[dot]backedmisuse[dot]in/?1567707376797c767e273b666c666170787473737c797c7461703b767a78
- click2[dot]systemaffiliate[dot]com/filter/?keyword=business+processes+management+Metaire+Construction+Management+Service
- a19602cr[dot]773a9be[dot]bd407edi[dot]m602f890[dot]wfd6b[dot]eay836h7h[dot]bytessounds[dot]in/?3a485f5c595653595108144943494e5f575b5c5c5356535b4e5f14595557
- click2[dot]systemaffiliate[dot]com/filter/?keyword=michelin+tire+Shingle+Roofer
- 0eeda91z[dot]w8cb575d[dot]b8[dot]s247[dot]maf35794i[dot]q9b[dot]yc79p[dot]b[dot]y7siiy61xy[dot]bytessounds[dot]in/?295b4c4f4a45404a421b075a505a5d4c44484f4f404540485d4c074a4644
- click2[dot]systemaffiliate[dot]com/filter/?keyword=compact+suv+internet+hosting+company
- u0b49r[dot]b9l[dot]r76783b2i[dot]ce01s[dot]k25o[dot]8f3t[dot]w32[dot]1d1dl[dot]u63g[dot]s45t[dot]xk6z4x0ok4[dot]isessentially[dot]in/?3f4d5a595c53565c540d114c464c4b5a525e59595653565e4b5a115c5052
- click2[dot]systemaffiliate[dot]com/filter/?keyword=hotel+prices+Air+Duct+Cleaning+Service
- za46[dot]1375623[dot]e53cb4[dot]2014[dot]50ebd[dot]t1c06f[dot]61[dot]y7f8vkub0[dot]safelyinstall[dot]in/?16647370757a7f757d2438656f6562737b7770707f7a7f7762733875797b
- click2[dot]systemaffiliate[dot]com/filter/?keyword=supercuts+coupons+sales+presentation+equipment
- 01e717[dot]i06917c[dot]36f5[dot]j056[dot]m66a[dot]176f3f[dot]5ej[dot]p6e[dot]h2xb793w17[dot]safelyinstall[dot]in/?285a4d4e4b44414b431a065b515b5c4d45494e4e414441495c4d064b4745
- click2.systemaffiliate[dot]com/filter/?keyword=free+latest+accounting+software+Laptops
- of62b8a[dot]x43f292x[dot]a674q[dot]r5ec03a[dot]y01c9b[dot]f7367u[dot]cgh63008[dot]husbandhides[dot]in/?3f4d5a595c53565c540d114c464c4b5a525e59595653565e4b5a115c5052
- click2[dot]systemaffiliate[dot]com/filter/?keyword=marine+equipment+and+supply+company+real+esate+hotline
- g1812c47[dot]t6060f09l[dot]t74711a[dot]m69131[dot]l88[dot]z874f0h[dot]b88z8j4s31ji[dot]husbandhides[dot]in/?2b594e4d484742484019055852585f4e464a4d4d4247424a5f4e05484446
-
paypal-invest[.]net
-
paypal-invest[.]info
- paypal-invest[.]biz
Following the 302 redirect, Magnitude delivers both a malicious Flash payload as well as a highly obfuscated JavaScript payload (MS13-009 Microsoft Internet Explorer COALineDashStyleArray Integer Overflow exploit). Once the browser has been exploited, Magnitude proceeds to a new step in the infection cycle where the malware payload would normally be downloaded immediately following exploitation, we are now seeing a shellcode payload being served.
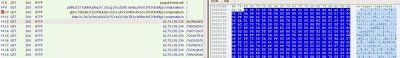 |
| Shellcode being served |
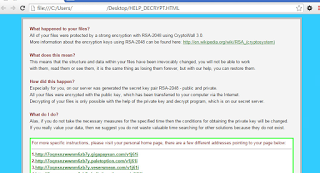
The shellcode is a simple payload that utilizes the Windows library ‘urlmon.dll’ to attempt to fetch a list of URLs contained within the shellcode. In the cases we have seen so far, only the first URL results in a payload (CryptoWall 3.0), while the others return no data.
This is a highly profitable ransomware payload that leverages Bitcoin transactions executed over the Tor Anonymizer to monetize the attack. Threat Actors utilize this method of collection because it can't be reliably traced back to the them. Victims are especially vulnerable to this type of extortion since very few people seem to backup their critical files such as documents and pictures.
ThreatLabZ has been actively monitoring this Magnitude EK activity and the image below illustrates the transactions we saw for this campaign:
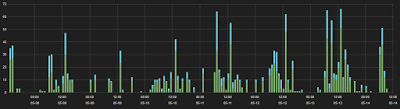 |
| The Green represents Payload activity; The Blue represents Landing Page activity. |
As with most threat actors, once they find a location that allows them to host their attacks they tend to stick with it. The lion's share of target IPs seen from our research show that Germany is the biggest hosting location for this activity.
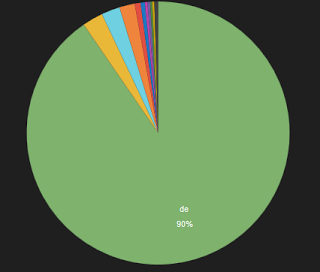 |
| Other countries seen to host this activity: NL (3%) US(2%) JP(2%) |
Conclusion
Exploit Kits are evolving to bypass standard security solutions that utilize basic URL filtering techniques. Attackers are utilizing various methods of infection, including malvertising and iFrame injection on compromised pages. Ransomware is a highly profitable, recording up to $33,000 per day at one point. The sophistication of these attacks are on the rise and security leaders need to keep apprised of this maturing illegal market.
Analysis done by Edward Miles & Chris Mannon