
TOP STORY
CISO Monthly Roundup, January 2025: DeepSeek risks, new Xloader versions, and more
Feb 10, 2025
Insights from threats explored by the Zscaler ThreatLabz team in January.
This past month, the Zscaler ThreatLabz security research team detailed the risks in DeepSeek, analyzed Xloader, and revealed the latest obfuscation, specialization, and evasion techniques by LockBit, Clop, and Raspberry Robin.
DeepSeek: A CISO's Insight into Potential Security Weaknesses
The recent launch of DeepSeek, a large language model (LLM) developed by a Chinese AI company, sent shockwaves across the tech industry. The open source model is accessible globally and comes with its own set of risks. When it comes to LLMs, there are three groups - builders (small group given how expensive), enhancers, and adopters. The way I look at DeepSeek GenAI research is that it has significantly reduced the cost and potentially opened the doors for builders and enhancers to become more commoditized in future. We will see many more DeepSeek-like generative AI models and applications over the coming months.
The international buzz around DeepSeek has prompted me to reflect on the potential security implications an organization must consider in light of more DeepSeek-like generative AI models.
- Weak security controls: The widespread adoption and use of AI technologies necessitate a thorough examination of their potential impacts. DeepSeek's current security guard rails appear to be inadequate, posing significant risks to organizations. For instance, the model could enable an attacker to significantly increase the volume of their attacks by automating the creation of malicious scripts, keylogger code, vulnerability exploits, and phishing email templates.
- Data exfiltration and cybercriminal empowerment: Just like any major innovation, there is a growing concern that cybercriminals will also take advantage of DeepSeek models and research to develop more effective exploitation and data exfiltration techniques. Previous demonstrations have shown how a single prompt can instruct a rogue generative AI module to execute an entire attack chain, from external attack surface discovery to data exfiltration. Threat actors can exploit DeepSeek-like models to scan for public vulnerabilities, scrape social media for compromised employee information, and infiltrate AI/ML environments to steal sensitive data.
- Accidental data exposure: Without proper governance, shadow AI instances of these applications will always risk exposing sensitive data.
It is crucial for organizations to have well defined policies and security controls governing the use of generative AI models and applications in their environment, both for sanctioned and unsanctioned applications.
Zscaler Zero Trust Exchange Coverage – SSL Inspection, Data Loss Prevention, GenAI Security, Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall
Deep Dive into Xloader Versions 6 and 7
Zscaler ThreatLabz recently published the first part of a technical analysis that examines the latest obfuscation techniques used in Xloader versions 6 and 7. Xloader, a malware family that evolved from Formbook, targets web browsers, email clients, and FTP applications to steal information and deploy secondary payloads. Xloader establishes persistence on a victim’s system by copying itself to specific directories and creating registry entries. Xloader injects malicious code into processes using techniques like process hollowing and APC queue. The malware uses many encryption layers, including RC4 and byte subtraction algorithms, to decrypt dynamic code. This is shown below.
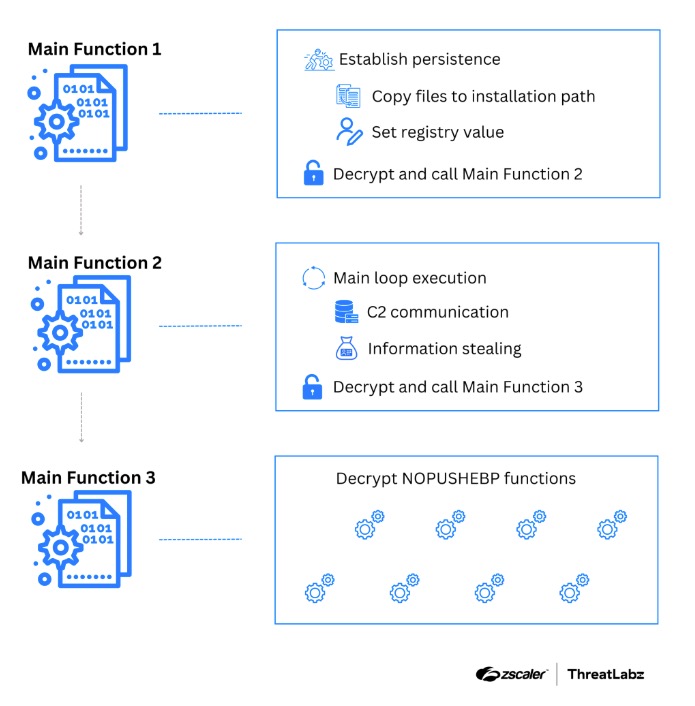
Figure 01: A high-level diagram for Xloader versions 6 and 7, which leverage three main functions to decrypt and execute critical parts of code.
Xloader has consistently introduced new layers of encryption and obfuscation with each release. Over time, the developer has added measures to decrypt critical information only when needed and has dispersed code and data across various sections. The encryption methods have evolved from an RC4 and subtraction algorithm with a lookup table to one that uses RC4 and subtraction. These changes are aimed at evading detection by endpoint security software and maintaining an advantage over security measures.
Stay tuned for Part 2 of our Xloader series, where we delve into how Xloader establishes network communication and uses fake servers to complicate analysis and detection.
Zscaler Zero Trust Exchange Coverage – Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection
Prevalent Threat Updates
Clop Ransomware Exploits Zero-Day Vulnerabilities in Secure File Transfer Platforms
The Clop ransomware group, which emerged in early 2019 and is linked to the larger TA505 threat group, has been specializing in exploiting vulnerabilities in secure file transfer platforms for data theft since 2020. In late 2024, the group was observed exploiting two vulnerabilities, CVE-2024-50623 and CVE-2024-55956, in Cleo Harmony, VLTrader, and LexiCom file transfer software. Cleo develops the managed file transfer platforms Cleo Harmony, VLTrader, and LexiCom, which enable companies to securely exchange files with others.
- CVE-2024-50623 is a flaw that affects all versions of Cleo Harmony, VLTrader, and LexiCom before 5.8.0.21. This vulnerability allows unauthenticated attackers to gain remote code execution on vulnerable servers exposed online. By exploiting this flaw, attackers can take control of affected systems without needing valid credentials. This issue has been addressed and fixed in version 5.8.0.21 of Cleo Harmony, VLTrader, and LexiCom.
- CVE-2024-55956 is another significant vulnerability, though less severe than CVE-2024-50623. It allows attackers to write arbitrary files on the target system. While it does not enable remote code execution, the ability to write files can be exploited in various ways. This vulnerability has been fixed in version 5.8.0.24 of CleoHarmony, VLTrader, and LexiCom.
Most of the data currently archived on the Clop data leak website pertains to companies compromised during the MOVEit Transfer data theft attacks in 2023. However, the ransomware group has announced that they will be deleting data associated with past attacks from their data leak server and will focus exclusively on new breaches related to the Cleo attacks. According to the Clop ransomware leak website “...due to recent events (attack on CLEO), all links to data of all companies will be disabled, and the data will be permanently deleted from our servers. We will work only with new companies.”
The specific ransomware note related to these zero-day attacks in Cleo file transfer products has been uploaded to the ThreatLabz ransomware note repository in GitHub. In their ransom note, the Clop ransomware group claims to have gained complete access to Cleo’s networks and sensitive information. The group demands a ransom to prevent the public release of this confidential data, stating that if the ransom is paid, they will delete the data and cease any further actions against the organization. Notably, one of the groups targeted in this recent 2024 Cleo attack was also a victim of the MOVEit attack. Note that these attacks involved only data extortion without file encryption.
Zscaler Zero Trust Exchange Coverage – Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection
LockBit 4.0 Launches Attacks in 2025 Despite Law Enforcement Crackdown
LockBit first emerged in September 2019 and quickly gained notoriety due to its extensive ransomware affiliate network. By leveraging these affiliates, LockBit conducted breaches, exfiltrated data, and deployed its ransomware. On February 20, 2024, the FBI and UK law enforcement seized parts of LockBit's infrastructure, including approximately 7,000 victim decryption keys. However, within days of the takedown, ThreatLabz identified new ransomware attacks carried out by LockBit and a new data leak site. So despite law enforcement action, the group remained active, attacking dozens of new organizations after February 2024.
In July 2024, ThreatLabz predicted in our annual ransomware report that LockBit activity would continue despite the law enforcement takedown, and this has indeed occurred. Interestingly, LockBit has chosen not to rebrand, continuing to operate under the same name.
LockBit ransomware returned with its fourth iteration in late 2024. In 2025, the group remains active, launching new attacks and adding numerous victims to their leak site. A new LockBit 4.0 ransomware note has been uploaded to the ThreatLabz ransomware repository in GitHub.
Zscaler Zero Trust Exchange Coverage – Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection
Raspberry Robin Adds Support to Exploit CVE-2024-38196
Discovered in 2021, Raspberry Robin (also known as Roshtyak) is a malicious downloader that distributes second-stage malware payloads. Some of these malware families are used by threat actors that serve as initial access brokers for ransomware attacks. The developers of Raspberry Robin frequently use low-level Windows APIs and features, and continually add more obfuscation features. In January 2025, ThreatLabz documented recent updates including an exploit for CVE-2024-38196.
- CVE-2024-38196 is a vulnerability that arises from improper input validation in the Windows Common Log File System (CLFS) Driver. Exploiting this flaw allows local attackers to elevate their privileges, gaining unauthorized access that could potentially lead to a complete system compromise.
Raspberry Robin employs various obfuscation methods to evade detection. These include control flow flattening, bogus control flow, string obfuscation with unique decryption routines for each string, mixed Boolean-arithmetic operations (MBA), indirect calls combined with MBA obfuscation, and encryption and checksum algorithms.
The malware developers frequently update the codebase, continually adding more obfuscation techniques to make detection and analysis increasingly difficult for security professionals. To learn more, visit our comprehensive blog on Raspberry Robin obfuscation methods.
Visit the ThreatLabz X.com feed for the latest news on ransomware and other cybersecurity threats.
Zscaler Zero Trust Exchange Coverage – Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection
About ThreatLabz
ThreatLabz is the embedded research team at Zscaler. This global team includes security experts, researchers, and network engineers responsible for analyzing and eliminating threats across the Zscaler security cloud and investigating the global threat landscape. The team shares its research and cloud data with the industry at large to help promote a safer internet.
The Zscaler Zero Trust Exchange
Zscaler manages the world’s largest security cloud. Each day, Zscaler blocks over 150 million threats to its 7300+ customers, securing over 300 billion web transactions daily. The Zscaler ThreatLabz security research team uses state-of-the-art AI/ML and machine-learning technology to analyze Zscaler Zero Trust Exchange traffic and share its findings.
Recommended
