Firefox is an ideal browser platform for creating add-ons. Firefox plugins have access to the entire browser, without any restriction. This allowed me to release two plugins to improve the security of Firefox users (Search Engine Security, and BlackSheep), and a third one is in the works, but the power of Firefox plugins can also be used with malicious intent.
Full access to the browser and the computer
Firefox plugins have access to the entire browser, including HTTPS content and also to the operating system. This means that any add-on can:
There is no concept of permissions or sandboxing for Firefox plugins. Once a user installs a plugin, it has full access to the computer. This is why Firefox imposes a 3-second warning message before you install a plugin. You'd better be sure you trust it fully!
Firefox plugins have been created to steal credentials or insert advertising in web pages.
No permissions checks or sandboxing
Google Chrome, on the other hand, requires every plugin to stipulate which domain can be accessed. They are shown to the users before the plugin is installed. It also has more limited capacities, like the inability to listen to all HTTP connections, which ultimately makes Chrome plugins safer, but less versatile.
Firefox has no restrictions at all on what the a plugin can do, or access. Some versions of Windows or various security tools will ask permission from the user if a plugin access files outside of the Firefox folder, or tries to run an executables. However, this was not the case on my Windows 7 Home version.
The only security measure implemented in Firefox is to forbid the installation of plugins from websites other than the official Mozilla site, by default. Users must first allow a domain to install plugins from, then click on "Install" after a 3-second wait period.
Official Mozilla add-ons review cycle
All add-ons submitted to the official Mozilla Add-Ons site go through a manual source code review. This process attempts to ensure that the plugins are not malicious. Each update of the plugin also goes through a manual review. The down side is that it takes days, or weeks, for every little change to be approved.This is why I prefer to release plugins on our website first and wait until the add-on is stable to submit it to the Mozilla site.
The only way to be reasonably sure that a plugin is safe is to download it through the official website. There used to be a loop hole, though - add-ons used to be allowed to be listed on the site, but hosted somewhere else. In that case, the official reviewers could not guarantee that code downloaded by the users was the same as what they approved. This option is not available anymore. All add-ons and updates have to be hosted by Mozilla and be listed on their site - that is why BlackSheep is lot listed anymore.
Silent plugin installation
Whenever you install a new plugin, it takes effect only after you restart Firefox. Firefox also display a box showing which plugins were newly installed. However, there are ways to install a plugin silently.
An attacker could trick users into downloading a program that would do a silent installation of a malicious plugin in order to get full access to the user surfing data, including login and password information sent over encrypted channels.
New add-on
All the add-ons are stored under the Firefox profile, a known location, within their own sub-folder. A new folder can be created and filled with a malicious plugin. Firefox keeps information about the existing add-ons in three files: extensions.rdf, extensions.ini and extensions.cache. If any of these file are deleted, Firefox re-builds them automatically at the next start up, without informing the users.
After adding the malicious plugin to the Firefox profile, the three files should deleted. This will not prevent the current Firefox session from running or impact existing plugins. When Firefox is restarted, these files are re-generated, and the new plugin is added to the list without any notification to the user.
Add-on overwrite
Each plugin includes the file install.rdf, which contains metada data about the plugin: name, version, home page URL, etc. The parameter updateURL tells Firefox which URL to use to check for new updates. Malware can simply add or modify the updateURL value for existing add-ons, then remove extensions.rdf. The new updateURL can be used to force the update of a plugin with a version that contains the old add-on plus malicious code.
With this technique, the malicious installation is completely invisible.
The Firefox plugin framework is very powerful. There are not adequate protections put in place to ensure the integrity of plugins after they are installed. I hope some future version of Firefox will put additional protections in place to avoid tampering of installed plugins.
-- Julien
Full access to the browser and the computer
Firefox plugins have access to the entire browser, including HTTPS content and also to the operating system. This means that any add-on can:
- see login/password credentials in clear text, even over HTTPS connections
- send back the credentials to any website
- modify the web pages seen by the user (often done by Adware)
- add/delete/modify files on the computer (even outside of the Firefox directory)
- run executables, either embedded in the plugin or downloaded at any point
There is no concept of permissions or sandboxing for Firefox plugins. Once a user installs a plugin, it has full access to the computer. This is why Firefox imposes a 3-second warning message before you install a plugin. You'd better be sure you trust it fully!
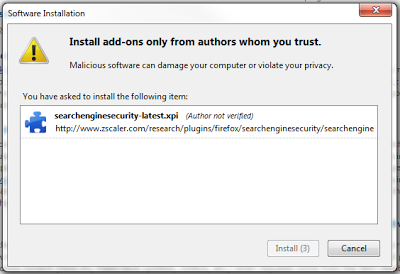 |
| Are you really sure you want to install this add-on? |
Firefox plugins have been created to steal credentials or insert advertising in web pages.
No permissions checks or sandboxing
Google Chrome, on the other hand, requires every plugin to stipulate which domain can be accessed. They are shown to the users before the plugin is installed. It also has more limited capacities, like the inability to listen to all HTTP connections, which ultimately makes Chrome plugins safer, but less versatile.
Firefox has no restrictions at all on what the a plugin can do, or access. Some versions of Windows or various security tools will ask permission from the user if a plugin access files outside of the Firefox folder, or tries to run an executables. However, this was not the case on my Windows 7 Home version.
The only security measure implemented in Firefox is to forbid the installation of plugins from websites other than the official Mozilla site, by default. Users must first allow a domain to install plugins from, then click on "Install" after a 3-second wait period.
 |
| Plugin installation is blocked by default |
Official Mozilla add-ons review cycle
All add-ons submitted to the official Mozilla Add-Ons site go through a manual source code review. This process attempts to ensure that the plugins are not malicious. Each update of the plugin also goes through a manual review. The down side is that it takes days, or weeks, for every little change to be approved.This is why I prefer to release plugins on our website first and wait until the add-on is stable to submit it to the Mozilla site.
 |
| Manual code reviews of Search Engine Security |
Silent plugin installation
Whenever you install a new plugin, it takes effect only after you restart Firefox. Firefox also display a box showing which plugins were newly installed. However, there are ways to install a plugin silently.
An attacker could trick users into downloading a program that would do a silent installation of a malicious plugin in order to get full access to the user surfing data, including login and password information sent over encrypted channels.
New add-on
All the add-ons are stored under the Firefox profile, a known location, within their own sub-folder. A new folder can be created and filled with a malicious plugin. Firefox keeps information about the existing add-ons in three files: extensions.rdf, extensions.ini and extensions.cache. If any of these file are deleted, Firefox re-builds them automatically at the next start up, without informing the users.
After adding the malicious plugin to the Firefox profile, the three files should deleted. This will not prevent the current Firefox session from running or impact existing plugins. When Firefox is restarted, these files are re-generated, and the new plugin is added to the list without any notification to the user.
Add-on overwrite
Each plugin includes the file install.rdf, which contains metada data about the plugin: name, version, home page URL, etc. The parameter updateURL tells Firefox which URL to use to check for new updates. Malware can simply add or modify the updateURL value for existing add-ons, then remove extensions.rdf. The new updateURL can be used to force the update of a plugin with a version that contains the old add-on plus malicious code.
With this technique, the malicious installation is completely invisible.
The Firefox plugin framework is very powerful. There are not adequate protections put in place to ensure the integrity of plugins after they are installed. I hope some future version of Firefox will put additional protections in place to avoid tampering of installed plugins.
-- Julien




