Zenith Live 2023 was chock full of announcements about new platform features to help our clients address important challenges and use cases, ranging from generative AI and advanced cyberthreat protection capabilities to innovations in connectivity and cloud resilience. As a cybersecurity and zero trust leader, our first and foremost priorities always revolve around continuing to ideate and bring to market the most innovative cybersecurity solutions.
This year at Zenith Live, we announced enhanced capabilities across the entire kill chain to add to the already robust offerings from Zscaler. Below is a summary of the cybersecurity advancements we announced.

Dhawal Sharma - SVP, Product Management at Zscaler talking about Zscaler’s cybersecurity advancements as part of an Innovation Keynote at Zenith Live ‘23 in Las Vegas
Discovery: automating exposure analysis
External Attack Surface Analysis Tool:
Regardless of the type of security incident, the first step is always about discovery. Threat actors are looking for ways and means to infiltrate and steal information, and it starts with knowing where the weak links lie. Sometimes, especially in large, complex organizations going through digital transformation, it's challenging for customers themselves to understand where their vulnerabilities might be due to unknown asset sprawl. In the past, we have helped customers by offering them an internet attack surface report which is a comprehensive point-in-time report that helps customers know where their apps are distributed and understand more about their exposed domain names, IPs, public cloud footprint, and more.
Now, we are excited to bring these capabilities as a standalone and automated external attack surface analysis web-based tool that will help customers understand their exposure to internet-facing threats in near-real time and understand the trends over time. Not only does this tool help customers understand their exposure, it’s also able to assess the severity of their vulnerabilities and map them directly to their application assets and servers on a continuous basis. The external attack surface analysis tool is offered today in limited availability and is expected to become generally available before end of august. Until then, please request your EASM report through your Zscaler account team. You can read more about this capability in this blog.
Preventing compromise: faster verdicts against threats without impacting user productivity
The next step in the kill chain is the compromise of users. Over the years, Zscaler has built several industry-leading technologies, including the world’s first inline malware prevention engine we call Zscaler Sandbox. At Zenith Live ‘23, we announced further enhancements that make it even better.
Zscaler Sandbox + Zscaler Browser Isolation integration:
With this unique integration, end users can now get read-only access to files even while the files undergo advanced sandbox analysis. Suspicious files are opened in an isolated container and the content is streamed to the end users while the file is being analyzed in the background. If deemed malicious, the threat is disarmed and Microsoft Word documents are flattened to PDFs before allowing the downloading of files.
AI/ML-based instant verdict capability:
Today, we are already able to determine—with a high level of accuracy—if a particular file is benign or not. With our announcement of the new AI/ML-based instant verdict capability, we can now leverage our advanced AI/ML algorithms to determine instantly if a file is malicious or borderline malicious while the file is still undergoing analysis in the Zscaler Sandbox.
These innovations are both slated for release before end of August, and will enable broader sandbox deployments to improve security without sacrificing user experience. You can read more details about this innovation in this blog.
Introducing Zscaler ITDRTM: Bringing identity-first security to zero trust
With identity becoming the next frontier of cyberattacks, Zscaler is introducing identity posture, hygiene management, and threat detection capabilities as the pillars of an identity-first approach to security that extends the tenets of zero trust to help create resilient IT environments. Organizations typically use traditional threat detection and identity management approaches to mitigate the risk of identity attacks. However, these approaches often fall short because they were not built to deal with identity threats.
For existing Zscaler customers, ITDR offers a unique value proposition.
- No additional agents/VMs required
- Integrated with access policy
- SOC integration with leading EDRs and SIEMs
With Zscaler ITDR, customers can now quantify identity-related risk, find misconfiguration in their active directory, remediate issues, monitor any deviation from baseline in real-time, and detect identity attacks as a second line of defense, all of which is vital to prevent compromise. Zscaler ITDR is now available in limited availability and will be generally available before end of August. Read the details in this blog.
Preventing lateral propagation: advancements to app segmentation, adaptive risk-based access termination, and private traffic inspection
CMDB file importing
Many of our customers start by moving all their sensitive applications behind ZPA to make them invisible to the external world. This certainly eliminates their external attack surface however, internal threats remain. Any malicious actor who might have gained access to internal resources is still able to access data that they might be necessarily entitled to. The easy wild card application segmentation does not necessarily cut it. Therefore, to make it a lot easier for customers to get started with effective application segmentation, we have introduced CMDB import capability for ZPA. With this, customers can upload details from their existing CMBD files. Once uploaded, ZPA is then able to make recommendations for application clusters based on user type, hosted locations, traffic patterns, and even the ports on which traffic is being transacted. This feature now offers an easy button for customers to get started on their app segmentation process and to continue shrinking their internal attack surface.
Intelligent app segmentation: taking one step further
Last year we launched an AI/ML-powered intelligent application segmentation feature. This feature helps in generating app segment recommendations based on user access patterns. We now have the ability to quantify attack surface reduction for each app segment recommendation. Also, we can now look at the departments and list of users as part of each department for every recommendation. This capability is now generally available.
Pattern-based application segmentation: scaling your app segmentation initiative
As customers start application segmentation, configuration is expected to grow. To make the configuration more scalable, we have now added the ability for customers to define patterns instead of individual FQDN for each application, which is part of an application segment. This will make the configuration optimal and future-proof as you can now easily bring new servers online without having to make any changes to the app segment.
You can read more about updates to our application segmentation capabilities in this blog.
We are not done with our innovations to prevent lateral propagation threats. There are two other areas that we think add tremendous value in this endeavor:
Adaptive risk-based access termination
This new announcement takes our zero trust security capabilities to the next level. Staying true to the principles of continuous monitoring, we can now check for multiple factors including geographical location, user risk score, and status of end point posture before determining if access should be granted. What makes this unique is the ability now to not only use this to make a determination of allowing access but to also terminate access if the posture changes during a session. This new capability is planned for before end of August and we cannot wait for customers to start using this.
Inspection of private application traffic
Many times, even private applications carry threats embedded in them that can go unnoticed. Not anymore. With the addition of this capability, customers can now bring the same world-class inline inspection capabilities that Zscaler is renowned for to private applications as well. With the ability to simply select this from a drop down menu in your SSL inspection policy screen after setting up the application segment in ZPA for inspection, you can easily and effectively inspect all traffic flowing to your crown jewel applications as well.
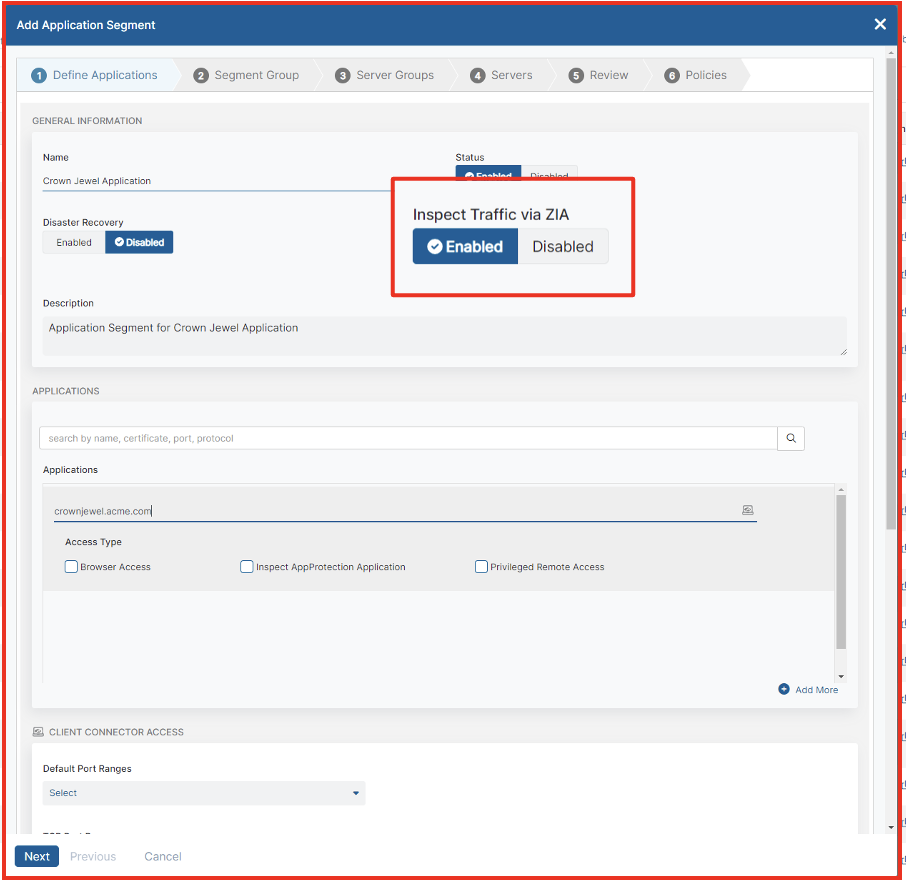
Set up application segments for inline traffic inspection
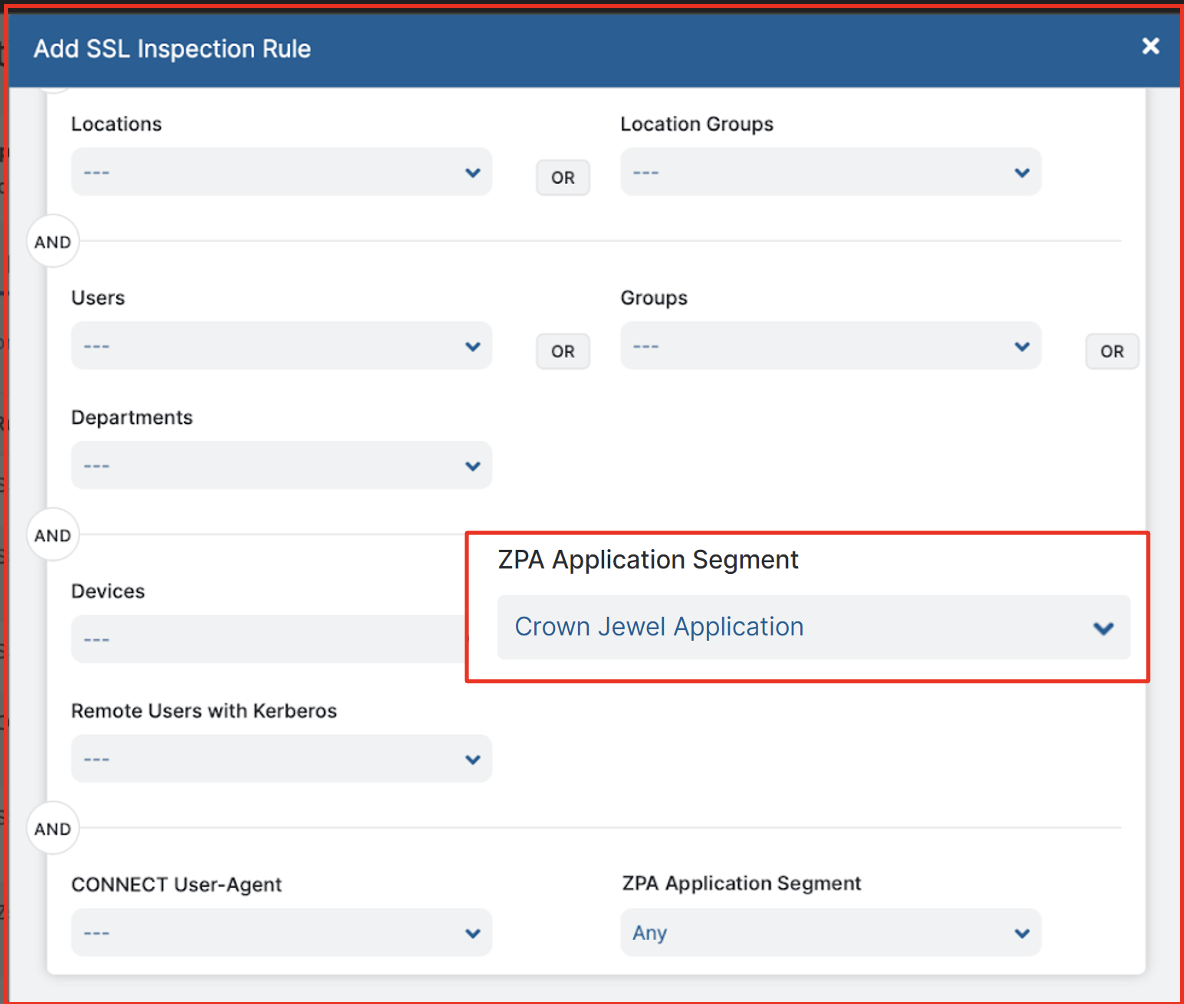
Easily select the ZPA application segment of choice for inspection
Analytics and visibility
Any good security team also needs the tools for holistic visibility into their organization's threat posture as well be able to analyze actions. We announced 2 new important tools to improve analytics and visibility into security incidents. These features include:
Zscaler traffic capture: Granular packet capture that allows incident responders and threat researchers to access raw traffic data in forensic activities.
Cybersecurity Insights dashboard: A SecOps dashboard that provides a unified view (with the ability to click deeper) into all security incidents and overall cybersecurity posture.
These innovations are both slated for release before end of August, and will make it even easier for security practitioners to understand and improve their security posture using the Zscaler Zero Trust Exchange. Read details about both these capabilities in this blog.
Unified identity across all Zscaler services
ZSLogin:
Zscaler recognized the opportunity to improve customer experience and increase efficiency in advancing both identity capabilities provided by Zscaler but also the other security capabilities of Zscaler products. By extracting identity into a common service, other Zscaler products can focus more attention in other areas. Today, adminstrators are able to seamlessly access all services across their organization for which the admins are entitled. They no longer need to keep track of different sets of credentials depending on which services they administer. In the near future (before end of August), Zscaler plans to bring similar capabilities to end users as well. Now that ZSLogin can ensure a guaranteed unique identity, it will make it much easier to share all context signals about users and related activities throughout the Zscaler ecosystem. You can read more about this capability in this blog.
We are proud of these innovations, and we are only getting started.
I hope many of you were able to join us at Zenith Live ‘23 in Las Vegas or Berlin where we celebrated innovation, collaboration, and joint success with customers and partners. If you missed it, you can still watch the recording here.




