This post was co-authored by Nathan Howe, ZPA Architect at Zscaler, and Tony Fergusson, IT Infrastructure Architect at MAN Energy Solutions
The darknet might sound like Batman’s Batcave network, but in fact it can serve as a means of decoupling network access from private application access.
The term “darknet” was created in the 1970s to describe networks isolated from ARPANET, the predecessor to the internet. The concept was created to protect sensitive information by making the network invisible and preventing inbound pings or inquiries. In simple terms, it means your IT infrastructure is completely inaccessible—dark—to anyone who is not authorized to see or access it.
What if networking teams could apply this principle to the way users access applications?
Before we get into how it would work in the enterprise, let’s first consider the current enterprise network infrastructure. Being on a network today is like standing in the middle of a residential street. You have the ability to see everything on the street, including the individual houses (applications), buildings (data centers), yards (network segments), and cross streets (other networks).
You can even walk up and touch the buildings’ doors (ports) and try to open them and go in (inbound traffic). The illustration below represents network-centric approaches.
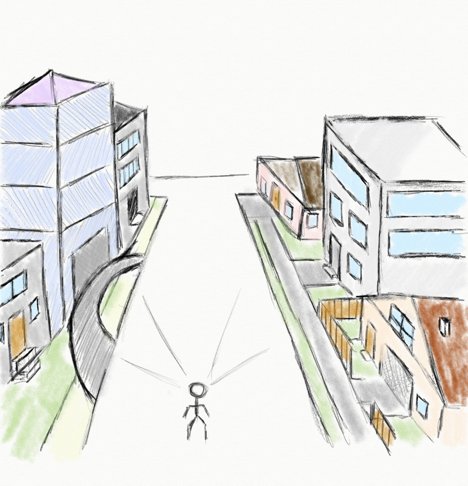
This model allows for over-privileged access and it assumes that everyone sharing the street can be trusted not to look at or break into private homes (internal/private apps). But, as we all know, trusting everyone can lead to an increased attack surface and stolen valuables.
In the old world, you put locks on your doors (passwords) and put up multiple fences, gates, and hedges (firewalls, ACLs, etc.) around your houses or buildings to protect them, and replaced those fences once they got too old. Sure, this made it harder for bad people to get in, but it still meant people could see into your windows. Wouldn't it be wonderful if people couldn't see into your house or, better yet, see your house at all?
The principles of the darknet can be used as a way to redefine private application access today. A new model in which no one is trusted and access is abstracted from the network/street layer, allowing teams to take a user- and app-centric approach. In this scenario, no one can even see that your house is there, let alone peep into your windows to see if there is anything worth taking. The analogy that MAN Energy Solution uses is that everyone is blindfolded, handcuffed, and completely restricted. They cannot do anything. Private application access begins to look like the image below. Only authorized users have visibility into specific houses (private applications), and all other houses remain invisible. Think of this approach to access as a dedicated, very temporary flashlight that can only light up the door or window that you have been allowed to see—and only for as long as allowed.

In this new model, the darknet (internet) acts as the corporate network. This doesn't mean anyone has access; it just means that the traditional corporate network, and the implicit trust that comes with it, becomes irrelevant.
Okay, so how do you apply this approach within the enterprise?
Adopting what Gartner calls a software-defined perimeter (SDP) solution can help bring the darknet to the enterprise. With SDP, your private apps and services become completely dark and only visible to the users you deem authorized to access them. Users are no longer placed on the network, IP addresses are never exposed to the internet, and the internet (via TLS encrypted tunnels) becomes the new connectivity mechanism. If you no longer need to expose anything to the outside world, you no longer need to worry about things like DDoS protection or the next Heartbleed vulnerability and subsequent attack.
With SDP, you can validate your users before granting any level of application access. By integrating with Azure AD, Okta, Ping, and others, you define which users access specific private applications—not the network. It essentially creates a secure segment consisting of a one-to-one relationship between a user and an app, and nothing more. Thus, SDP delivers dynamic and secure microsegmentation.
Creating that dynamic, secure segment for each user to only that requested (and allowed) application enables a true zero trust model. This concept of creating your own darknet (black cloud), where you can control and monitor application access, will enable you to create your own secure network fabric, regardless of the user´s or the application’s location.
You can’t attack what you can’t see
In this day and age, enterprises must reduce the attack surface. We can’t continue to worry about the next SSL/TLS vulnerability, and we need to make sure no parts of our ecosystems are exposed, let alone seen to be vulnerable. This is especially important in a world in which malware propagation is taking down enterprises and hackers are keen to profit using ransomware, cryptomining, supply-chain exploits, IoT botnets, and a range of other new and creative attacks they’ve been cooking up.






