/ What Is the Purdue Model for ICS Security?
What Is the Purdue Model for ICS Security?
What’s the Purpose of the Purdue Model?
The Purdue model, part of the Purdue Enterprise Reference Architecture (PERA), was designed as a reference model for data flows in computer-integrated manufacturing (CIM), where a plant’s processes are completely automated. It came to define the standard for building an ICS network architecture in a way that supports OT security, separating the layers of the network to maintain a hierarchical flow of data between them.
The model shows how the typical elements of an ICS architecture interconnect, dividing them into six zones that contain information technology (IT) and OT systems. Implemented correctly, it helps establish an “air gap” between ICS/OT and IT systems, isolating them so an organization can enforce effective access controls without hindering business.
Zones of the Purdue Model
OT systems occupy the lower levels of the model while IT systems occupy the upper levels, with a “demilitarized zone” of convergence between them.
Let’s take a look at each of the zones in the Purdue reference model, top to bottom.
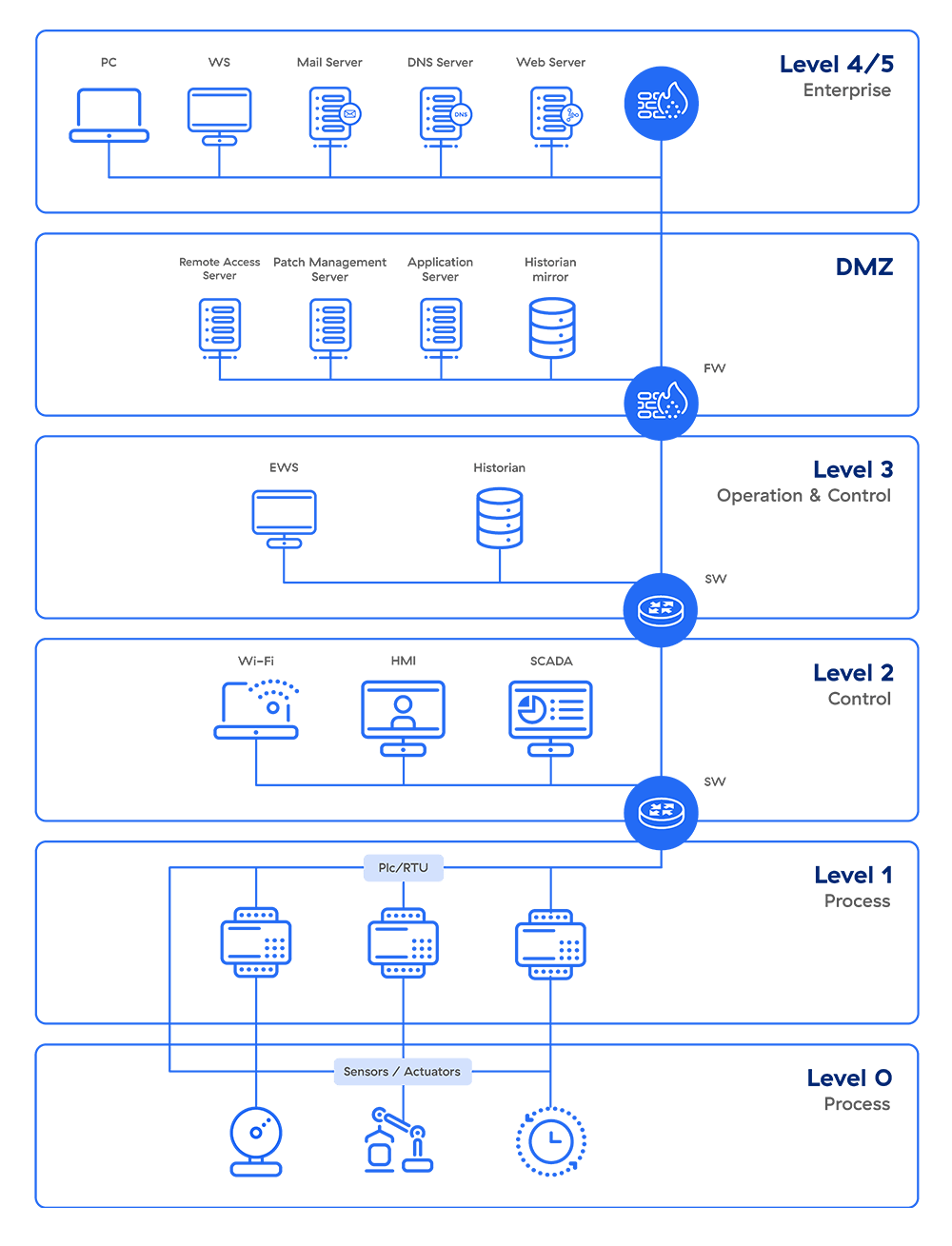
Figure 1: A basic render of the Purdue model
Level 4/5: Enterprise Zone
These zones house the typical IT network, where the primary business functions occur, including the orchestration of manufacturing operations. Enterprise resource planning (ERP) systems here drive plant production schedules, material use, shipping, and inventory levels.
Disruptions here can lead to prolonged downtime, with the potential for economic damage, failure of critical infrastructure, or revenue loss.
Level 3.5: Demilitarized Zone (DMZ)
This zone includes security systems such as firewalls and proxies, used in an effort to prevent lateral threat movement between IT and OT. The rise of automation has increased the need for bidirectional data flows between OT and IT systems, so this IT-OT convergence layer can give organizations a competitive edge—but it can also increase their cyber risk if they adopt a flat network approach.
Level 3: Manufacturing Operations Systems Zone
This zone contains customized OT devices that manage production workflows on the shop floor:
- Manufacturing operations management (MOM) systems manage production operations.
- Manufacturing execution systems (MES) collect real-time data to help optimize production.
- Data historians store process data and (in modern solutions) perform contextual analysis.
As with Levels 4 and 5, disruptions here can lead to economic damage, failure of critical infrastructure, risk to people and plant safety, or lost revenue.
Level 2: Control Systems Zone
This zone contains systems that supervise, monitor, and control physical processes:
- Supervisory control and data acquisition (SCADA) software oversees and controls physical processes, locally or remotely, and aggregates data to send to historians.
- Distributed control systems (DCS) perform SCADA functions but are usually deployed locally.
- Human-machine interfaces (HMIs) connect to DCS and PLCs to allow for basic controls and monitoring.
Level 1: Intelligent Devices Zone
This zone contains instruments that send commands to the devices at Level 0:
- Programmable logic controllers (PLCs) monitor automated or human input in industrial processes and make output adjustments accordingly.
- Remote terminal units (RTUs) connect hardware in Level 0 to systems in Level 2.
Level 0: Physical Process Zone
This zone contains sensors, actuators, and other machinery directly responsible for assembly, lubrication, and other physical processes. Many modern sensors communicate directly with monitoring software in the cloud via cellular networks.
Figure 2 shows the workflow and the interactions between the different zones and systems.
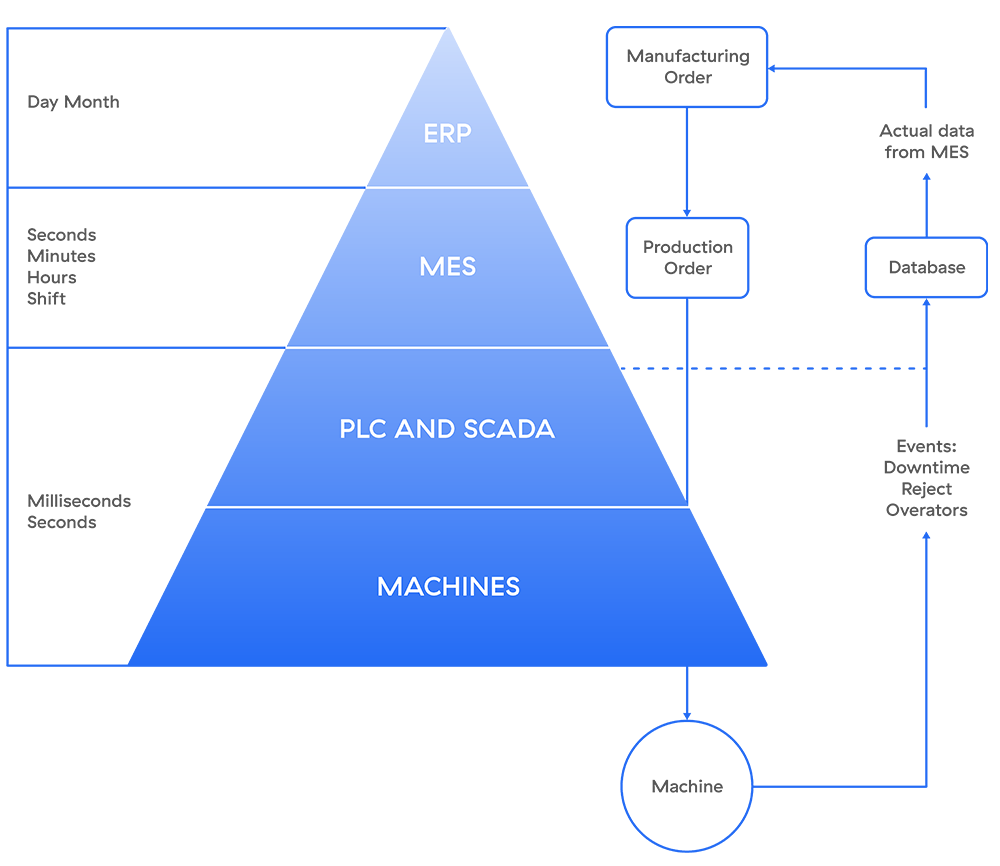
Figure 2: Purdue model workflow and interactions
Is the Purdue Model Still Relevant?
When the Purdue model was introduced in 1992 by Theodore J. Williams and the Purdue University Consortium, few other models had yet outlined a clear information hierarchy for CIM, which began to take hold of the industry in the mid-to-late 1980s.
Today, with the industrial internet of things (IIoT) blurring the line between IT and OT, experts often wonder whether the Purdue model still applies to modern ICS networks. Its segmentation framework is often set aside, after all, as data from Level 0 is sent directly to the cloud. However, many suggest it’s not yet time to discard the model.
In 2020, Litmus CEO Vatsal Shah said, “The Purdue Model still serves the segmentation requirements for both wireless and wired networks and protects the operational technology (OT) network from unwarranted traffic and exploits.”¹
SANS Institute took a similar position in 2021, saying, “Even if its hierarchical layers can no longer be uniformly applied to modern architectures, sorting ICS and IT devices and systems into distinct functional layers helps administrators and security practitioners determine where to apply security measures effectively.”²
Forbes maintained that perspective in 2022: “The Purdue Model is dead. Long live the Purdue Model.”³
Industrial uptime requirements and budgets often mean that the new can’t yet replace the old, and that holds true for the Purdue model despite the rise of IoT. Instead, many are advocating for a hybrid approach of applying macro segmentation with zero trust to overcome the unique challenges of modern ICS security.
1. AutomationWorld, “Is the Purdue Model Still Relevant?,” May 2020.
2. SANS Institute, “Introduction to ICS Security Part 2,” July 2021.
3. Forbes, “A Reimagined Purdue Model For Industrial Security Is Possible,“ January 2022.
Cybersecurity Challenges Unique to ICS
Let’s take a look at a few of those challenges:
- The air gap doesn’t work anymore. The rise of IoT and cloud adoption across the industrial value chain has made many industrial networks so integrated that the traditional air gap simply isn’t effective.
- ICS devices were built to last, not to evolve. Stringent uptime requirements of many industrial devices make it difficult, costly, or risky to update or replace them, leaving many CIM devices vulnerable to modern attacks, yet still connected to the wider network.
- IT-OT convergence and new technologies increase risk. As digital transformation breaks down IT-OT barriers, advancements in networking and data analytics reshape processes, and new sophisticated cyberattacks appear, ICS frameworks are slow to adapt.
- Many ICS network owners hesitate to adopt zero trust. Concerns over downtime causing lost revenue, disrupting infrastructure, or even endangering people’s safety make industrial operators uncertain about potential tradeoffs in costs and complexity, even as zero trust remains the most effective strategy for securing modern networks.
The Need for Zero Trust in ICS
OT environments tend to use flat networks and equipment from multiple vendors. Yet deploying network-level microsegmentation with physical devices can mean significant downtime—especially if the ICS and SCADA systems are too outdated. Moreover, most OT professionals don’t know IT best practices or advanced network security concepts, and their job is to prioritize uptime and people safety, not security.
Ethernet is still the backbone of most factories and warehouses, but wireless connectivity is gaining traction as private cellular brings mobility, reliability, deterministic networking, and standardized technology. This will enable autonomous mobile robots, cobots, asset tracking, smart glasses, and other Industry 4.0 applications.
Today, manufacturers can collect data in real time and use it to run analytics in the cloud for immediate results. Applications and data-generating activities once reserved for local operations—PLCs, SCADA, and DCS for manufacturing, and warehouse management systems for logistics—are finding their way to the cloud as well, increasing OT network complexity.
Zero trust can simplify security for OT environments and solve key challenges such as secure remote access for ICS systems without requiring physical segmentation at each layer. The National Institute of Standards and Technology (NIST) proposed the zero trust architecture for industrial and enterprise networks, stating, “Perimeter-based network security has also been shown to be insufficient since once attackers breach the perimeter, further lateral movement is unhindered.”
Applying the zero trust guiding principles of IT networks for workflow, system design, and operations can simplify and improve OT network security posture and help accelerate digital transformation.
The Zscaler ICS Security Solution
A zero trust approach is the most effective way to ensure robust OT and ICS security, with adaptive, context-based application access that doesn’t depend on network access. With an effective zero trust architecture in place, any user can only access the applications and systems they need, with no complex firewall stacks or VPNs required, all while your apps and network stay invisible to the internet.
Zscaler Private Access™ (ZPA™) is the world’s most deployed zero trust network access (ZTNA) platform, providing:
- A powerful alternative to VPN: Replace risky, overloaded VPN with ZPA to eliminate unnecessary traffic backhauling and gain secure, low-latency access to private applications.
- Hybrid workforce security: Empower your users to securely access web apps and cloud services from any location or device, with a smooth user experience.
- Agentless access for third parties: Extend your secure private app access to vendors, contractors, suppliers, and more with support for unmanaged devices, with no endpoint agent.
- IIoT and OT connectivity: Provide fast, reliable, and secure remote access to IIoT and OT devices to facilitate maintenance and troubleshooting.


