Ninety percent of organizations are apprehensive that attackers will target them through third-party-owned VPNs. Not only that—user satisfaction and security will also take a beating. Read on to find out more.
A just-released 2023 survey report by Cybersecurity Insiders, accredited by Zscaler, highlights the many benefits to organizations when they move away from legacy solutions, spurring on any organization that may be delaying the adoption of zero trust network access (ZTNA) and its clear user productivity and security advantages.
Virtual private networks (VPNs), the de facto remote access solution for the last 30 years, have more recently been constant targets of sophisticated cyberattacks. In the world of hybrid work, where users and applications are distributed, traditional remote access solutions that backhaul traffic to a single data center hinder productivity with a poor user experience, connectivity issues, and inconsistent access experience. In addition, VPNs give all users—employees and third-party users alike—access to the full network to reach applications. This has resulted in many threats recently, even overcoming security measures of user credentials.
The 2023 VPN Risk Report details the challenges users and IT professionals face in using and maintaining VPNs, and examines new technologies that can help them overcome these challenges to support user efficiency and business growth.
Third-party security concerns with VPN access
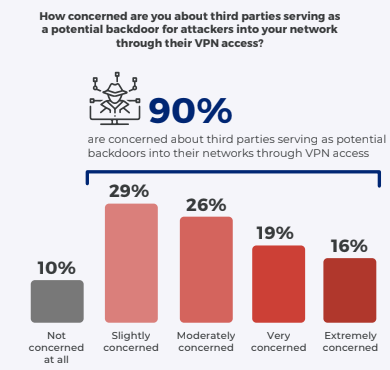
The report shows that 90% of organizations are concerned about attackers exploiting third-party vendors to gain backdoor access into their networks. Outside users like contractors and vendors remain integral to business growth, but they can put an organization at risk due to varied security standards, lack of visibility into their network security practices, and more, further complicating the job of managing third-party access and network security in general.
Poor user experience leads to poor user productivity
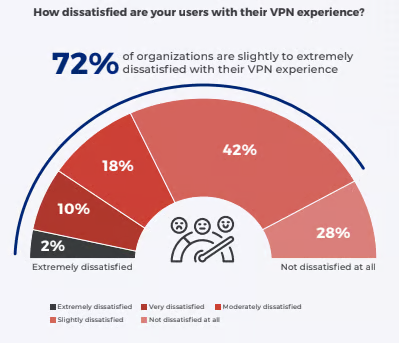
The 2023 report (and the 2021 and 2022 reports) shows that user experience is a big challenge for users connecting with VPN. Users see a constant drop in VPN connections, and sluggish application speeds hamper productivity.
Cyberattackers exploiting VPN vulnerabilities
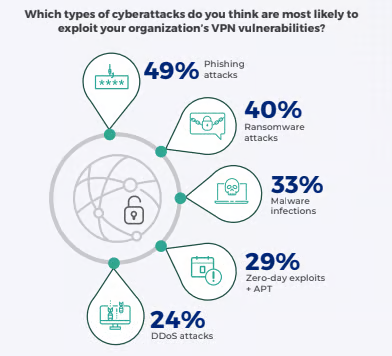
According to the report, nearly 1 in 2 organizations have experienced VPN-related attacks in the past 12 months and are aware of potential threats to their organizations opened up by VPNs. This underlines the need for a remote access tool that doesn’t expose organizations to external and internal threats.
The report also shows security and IT leaders are increasingly concerned about cyberattackers exploiting VPN vulnerabilities, emphasizing the urgent need to address the security of current VPN architectures.
Fortunately, as phishing, ransomware, credential theft, malware and application attacks increase in frequency and severity, organizations are swiftly replacing their VPNs with ZTNA.
The risks exposed in this report, including the growing threat of VPN exploits, should prompt organizations to completely rethink their remote access solutions, reevaluate their security posture, and migrate to a zero trust architecture. The push to quickly adapt to remote work at a large scale, especially during the COVID-19 pandemic, brought zero trust to the forefront of the conversation. This paradigm shift away from traditional security architecture has proven a robust way to connect remote users to applications securely.
The report strongly recommends organizations implement a zero trust architecture to effectively mitigate the risks associated with VPN vulnerabilities as well as protect their sensitive data and applications from cyberattacks. With 92% of organizations already considering, planning, or in the midst of a zero trust implementation, it’s clear that zero trust is the future of hybrid work.
Zscaler’s next-generation ZTNA solution, Zscaler Private Access (ZPA), enables secure access to private applications while ensuring users have the best experience to maintain high productivity. ZPA can help you:
- Minimize the attack surface: ZPA can replace your VPN infrastructure and provide direct access to internal applications. With these apps invisible to the internet, you minimize the visibility and accessibility of critical assets, making them more difficult for attackers to discover and target.
- Prevent compromise: ZPA analyzes network traffic for malicious content and data loss. Implementing inline traffic and content inspection mechanisms allows you to detect and block malicious activities, effectively shielding resources from unauthorized access or data exfiltration.
- Eliminate lateral movement: With ZPA, users connect directly to applications instead of the network. By isolating users from the internal network, you limit attackers’ opportunities for unauthorized access and lateral spread within your infrastructure.
Zscaler has helped thousands of organizations like Molson Coors, Southwest Gas, Colt Technology, and more migrate from their legacy VPN to our next-generation ZTNA to secure private access.






