With identity becoming the next frontier of cyberattacks, Zscaler is introducing identity posture, hygiene management, and threat detection capabilities as the pillars of an identity-first approach to security that extends the tenets of zero trust to help create resilient IT environments.
Cyber defense in an identity-centric world
The end goal of all adversarial action is to leverage resources to get to the crown jewels. There are a variety of resources that could aid threat actors but the one with the highest effort-to-impact ratio is the identity of the user; and by extension, the credentials, privileges, and access rights associated with the identity.
There are two paradigm shifts happening right now. First, EDRs are approaching the tail end of the slope of enlightenment in Gartner's security operations hype cycle, meaning they are pervasive and widely used. As a result, organizations are more successful than ever in detecting malicious tools and code execution.
The second paradigm shift is the transition to zero trust. Gartner projects that at least 70% of new remote access deployments will be served mainly by ZTNA instead of VPN services by 2025—up from less than 10% at the end of 2021. As evidenced by Zscaler's 7000+ customers, organizations are adopting a zero trust architecture that minimizes their external attack surface, limits resource access, and verifies every user.
These two paradigm shifts have forced the hand of threat actors; as a result, they're now going after Identities. If the modus operandi of a threat operation is to get to the crown jewels, then what better way to do it than by assuming the identity of a legitimate user? By compromising users and leveraging valid credentials, attackers can circumvent traditional detection controls and zero trust policies and instead leverage access rights and privileges to move laterally.
In terms of the effort-to-impact ratio of an attack operation, network and host artifacts that comprise identity provider configuration, role-based access controls, and Windows credential stores sit in the middle of the Pyramid of Pain – annoying but not challenging or difficult.
As a result, identity-based attacks that use valid credentials have quickly become the preferred strategy of not just organized threat actors (Lapsus$/Nobelium/BlackMatter/Vice Society), but have also been widely embraced by the cybercriminal community in general (80% of attacks in 2022 were identity-centric, 5/10 organizations suffered an Active Directory attack, and 90% of Mandiant IR engagements involved the use of Active Directory).
Current approaches are ineffective
Organizations typically use traditional threat detection and identity management approaches to mitigate the risk of identity attacks. However, these approaches often fall short because they were not built to deal with identity threats.
Detection controls to identify the use of malicious credentials have existed for ages (UEBA / SIEM analytics), however, they are prone to false positives, and invariably lack the context to allow threat detection teams to make decisions (e.g. is random user X actually allowed to change Y permission?).
Attacks such as 2FA MiTM, 2FA spamming, SIM cloning, session token hijacking/cookie stealing, etc. target IAM/PAM preventive controls, bypass MFA, and often rely on users to make smart decisions (historically, never a winning proposition).
Furthermore, many internal forms of identity and credentials do not lend themselves well to multifactor authentication, this includes service accounts, applications that don’t support multifactor authentication, certificates, session tokens, and keys.
These paradigm shifts, combined with the limited efficacy of existing solutions, necessitate an identity-centric approach to security.
Zscaler Identity Threat Detection and Response (ITDR) – Bringing identity-first security to zero trust
Zscaler’s vision for identity-first security is based on three fundamental pillars:
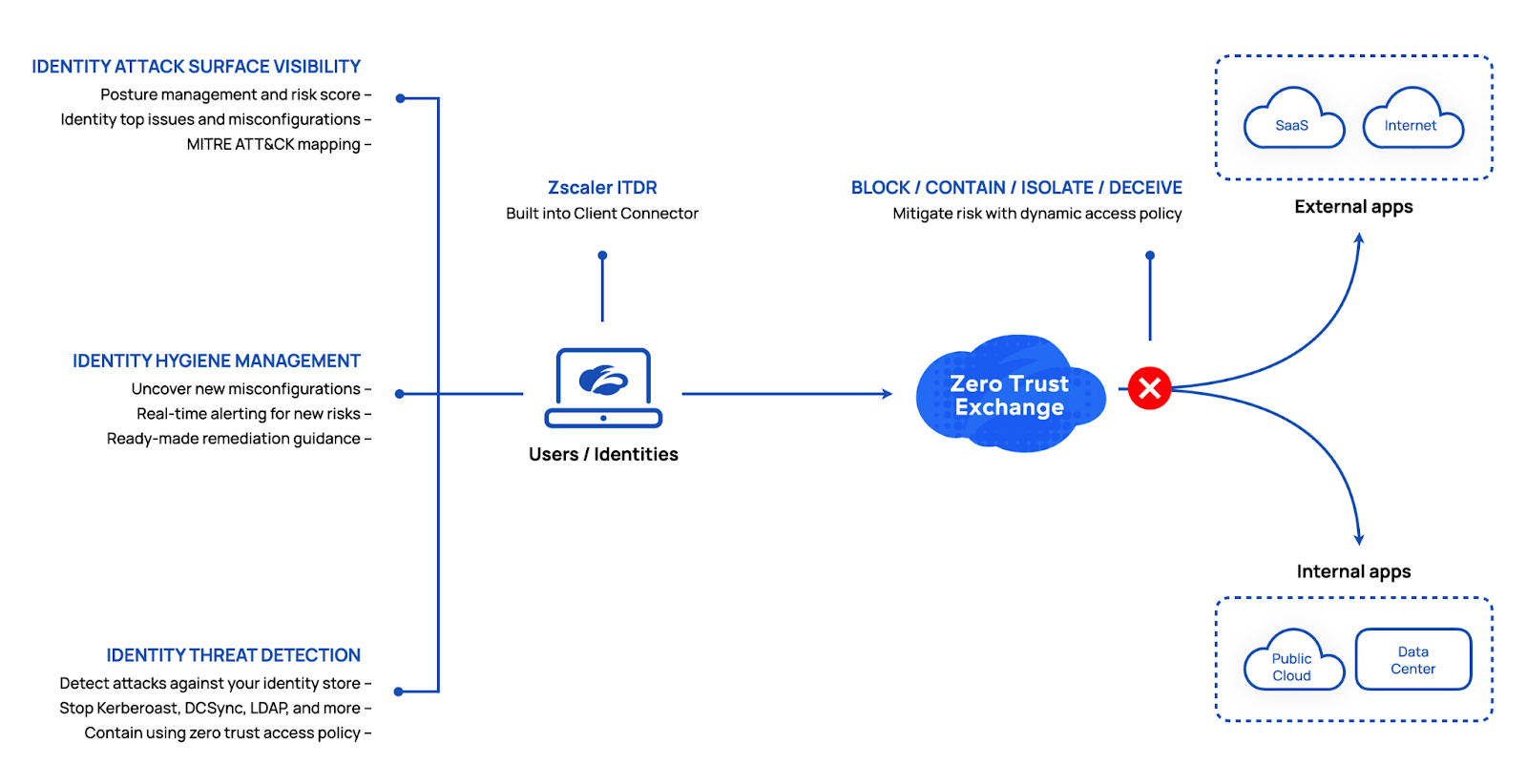
Identity attack surface visibility
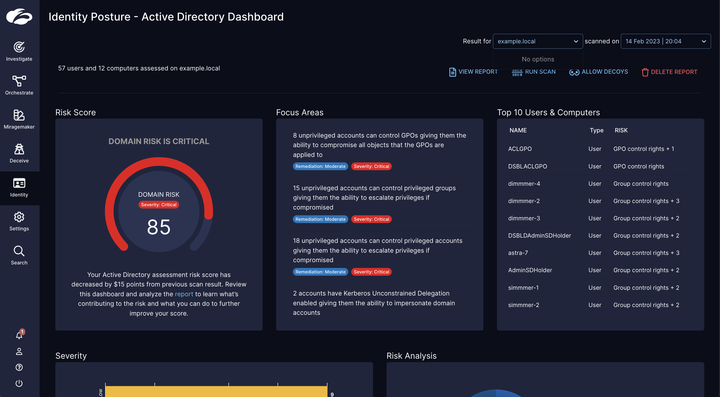
The first step toward securing identities is to audit your identity infrastructure thoroughly. Zscaler ITDR provides the ability to assess your on-prem Active Directory (support for additional identity stores coming soon) and get a comprehensive view of your identity posture, risky users and computers, misconfigurations and vulnerabilities that exist in Active Directory, and a MITRE ATT&CK mapping that helps you locate blind spots and prioritize where to focus.
Identity hygiene management
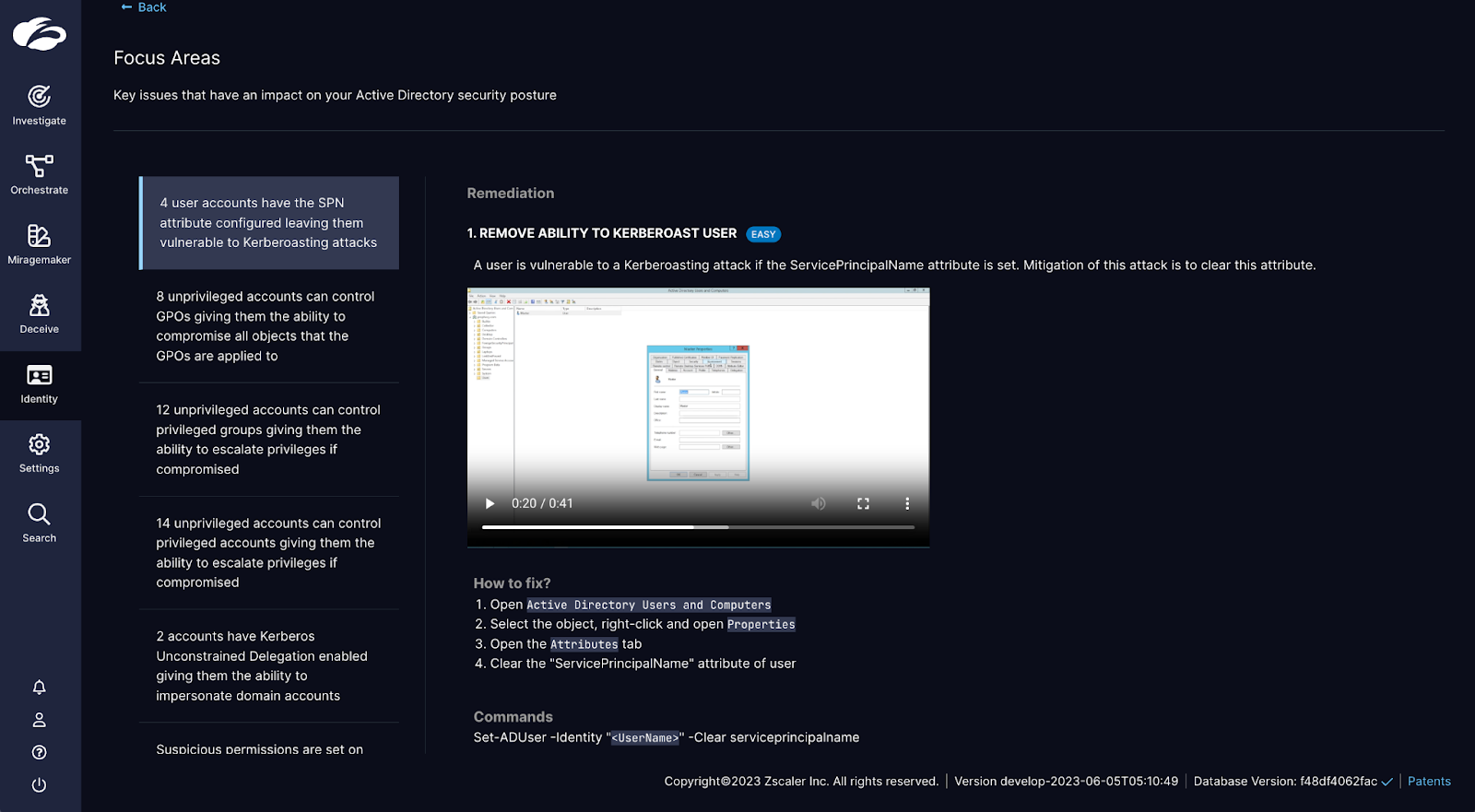
Once you have visibility into your Identity Attack Surface, the second step is to build identity hygiene. Zscaler ITDR provides real-time monitoring of critical changes in the Active Directory that introduce new risks and open up pathways for attackers to escalate privileges and move laterally. In addition to real-time alerting, you also get remediation guidance in the form of video tutorials, commands, and scripts that can be used to resolve issues.
Identity threat detection and response
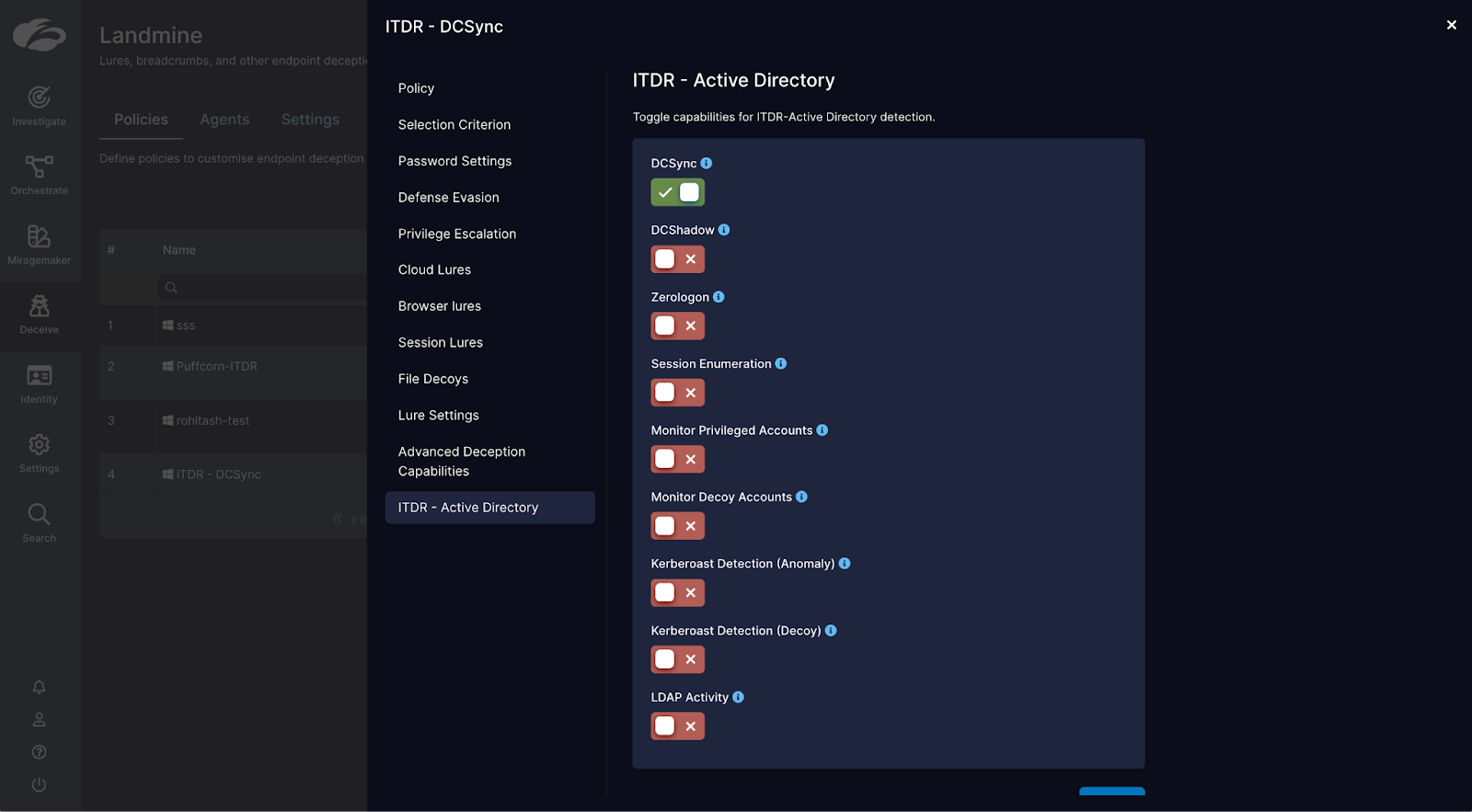
Not all identity issues and misconfigurations can be remediated. Some are business-critical and leave organizations open to exploitation in the event of a compromise. The last step is to be able to detect identity attacks that bypass existing defenses and leverage these misconfigurations to escalate privileges and move laterally. Zscaler ITDR provides high-fidelity detection for attacks like DCSync, DCShadow, LDAP enumeration, and more.
How it works
Zscaler ITDR takes a low-touch and operationally simple approach to identity security.
It’s built into Zscaler Client Connector, our unified agent that securely brokers connections between users and applications/resources.
Attack surface visibility
Zscaler ITDR audits the Active Directory by running LDAP queries to build a map of schema, users, computers, OUs, and other objects in your identity store. It then runs checks against these objects to find misconfigurations and vulnerabilities that exist in your Active Directory.
- For assessing the Active Directory, Zscaler ITDR needs to run on a Client Connector installed on a domain-joined Windows machine.
- The security team sets up a scan by specifying the Active Directory domain they wish to access and selecting the Client Connector installed machine from which to run the scan.
- Depending on the size of the Active Directory, it takes anywhere between 15-30 minutes to complete the assessment.
- Once the assessment is complete, the results are available in the Dashboard.
- The assessment includes a domain risk score, focus areas to prioritize remediation, a list of the riskiest users and computers, a basic analysis of severity and risk categorizations, MITRE ATT&CK kill chain mapping, and a complete list of misconfigurations discovered.
For each misconfiguration, the solution provides the following:
- Risk categorization
- Severity
- Remediation effort
- MITRE ATT&CK ID and tactic
- Explanation of the issue
- Potential impact
- List of users, computers, and objects affected
- Remediation guidance
- Video tutorials
- Scripts
- Commands
Identity change detection
Once an assessment has been configured, security teams can turn on change detection for the Active Directory domain.
Change detection surfaces configuration changes that affect the security posture of Active Directory in near real-time, allowing security teams and directory admins to quickly respond and remediate.
- Zscaler ITDR runs a series of high-priority configuration checks against Active Directory.
- The scope of these checks targets the discovery of issues that have the highest possibility of abuse by adversaries.
- These checks run every 15 minutes from the Client Connector installed endpoint for the given domain.
- Changes are marked as having a good or bad impact.
- A good impact indicates that an issue has been resolved.
- A bad impact indicates a potential issue has been introduced.
Identity threat detection
Zscaler ITDR has a threat detection capability that alerts SOC teams and threat hunters of malicious activities directed toward potentially malicious misuse and theft of identities.
Identity threat detection can be turned on as an endpoint policy on designated Client Connector-installed machines.
- Available detectors include DCSync, DCShadow, Kerberoasting, session enumeration, privileged account access, LDAP enumeration, and more.
- Security teams can choose to turn on all or a combination of detectors on designated endpoints.
- If a pattern is noticed, Client Connector signals to Zscaler ITDR that a threat has been detected.
- Zscaler ITDR will enrich the threat signal with information relevant to the security team to perform an investigation.
- The security team can configure orchestration capabilities in Zscaler ITDR to take automated actions from alerting to forwarding, to remediation.
Why Zscaler ITDR?
No additional agents / VMs required
Built into the Zscaler Client Connector, Zscaler ITDR unlocks new capabilities and protections out-of-the-box.
Integrated with access policy
The Zscaler Zero Trust Exchange can dynamically apply access policy controls to block compromised users when an identity attack is detected.
SOC integrations
Strengthen investigation and response with Integrations that include leading EDRs and SIEMs. Our telemetry is OpenAPI compliant.
Benefits
Identity protection strengthens your zero trust posture by mitigating the risk of user compromise and privilege exploitation.
Quantify identity risk
Know where, how, and why you are at risk. An identity security assessment generates a risk score to quantify and track the posture of your identity attack surface.
Find misconfigurations
Uncover issues that allow attackers to gain the upper hand. Discover risky configurations like GPP password exposure, unconstrained delegation, and stale passwords that open up new attack paths.
Remediate issues
Build strong identity hygiene with remediation guidance. Understand the issue, impact, and who is affected. Leverage step-by-step remediation guidance along with video tutorials, scripts, and commands.
Monitor in real-time
Get alerts when configuration changes introduce risk. Identity stores are in constant flux with configuration and permission changes. Monitor in real-time and get alerted to new risks and issues.
Detect identity attacks
Stop privilege escalation with identity threat detection. Not all misconfigurations can be remediated. Detect and stop attacks like DCSync, DCShadow, kerberoasting, and more in case of a compromise.
In closing
Zscaler ITDR is a new class of Identity-centric security control that provides visibility into the identity attack surface, detects attacks against identities and identity systems, and mitigates risk by closing the loop on hygiene, containment, and remediation. With attackers using identity compromise as the preferred route to a breach, Zscaler ITDR provides a pragmatic approach to identity-first security to mitigate the risk of threats that bypass existing defenses.





