Blog Zscaler
Recevez les dernières mises à jour du blog de Zscaler dans votre boîte de réception
Identifying Phishing Attacks: Common Types, Key Tactics, and Prevention Tips
Phishing is no longer just a common cyber nuisance—it’s a constantly evolving threat that’s wreaking havoc on individuals and organizations worldwide. In 2023, phishing was the most widespread form of cybercrime, responsible for 300,000 incidents and billions in financial losses, according to the FBI’s Internet Crime Complaint Center (IC3). The real challenge isn’t just the sheer volume of attacks, but how quickly phishing tactics are evolving. Attackers are incorporating generative AI (GenAI) into their social engineering strategies to create highly sophisticated and personalized scams.
The Zscaler ThreatLabz 2024 Phishing Report highlights a 58.2% increase in phishing attacks year-over-year, fueled by techniques like vishing (voice phishing) and deepfake phishing, which allow cybercriminals to exploit new vulnerabilities by exploiting trusted voices and familiar scenarios with startling accuracy. These AI-driven tactics are transforming the phishing landscape, making traditional detection and protection methods far less effective.
Understanding current and emerging phishing threats is key to preventing potential damage. This blog post covers phishing tactics you should be aware of, the telltale signs of scams, the most common and trending types of phishing attacks, and guidance on how to minimize your exposure to these threats.
How does phishing work?
What makes phishing especially threatening is that it doesn’t just target individuals—it can be a gateway to larger security breaches, particularly when corporate accounts are involved.
The aim of phishing is usually twofold: deceive victims into revealing sensitive information, such as login credentials and credit card numbers, and install malware on the victim’s device, often leading to identity theft, financial fraud, or system compromise. Although phishing is commonly delivered through email, it can also happen via text messages (SMS), voice calls (vishing), or social media.
Here are some hallmark characteristics of phishing attacks:
- Impersonating trusted entities: Attackers often pose as reputable organizations, like banks or social media platforms, to lend credibility to their scams.
- Requests for sensitive information: Phishing attacks often include forms or prompts asking for personal details that are then used for unauthorized access, fraud, or identity theft.
- Malicious links and attachments: Victims are often tricked into clicking on links or downloading attachments, which direct them to fake websites or install malware.
- Emotional manipulation: Scammers exploit emotions excitement or fear by offering false rewards (e.g., Amazon gift cards) or alarming consequences (e.g., account closure) to provoke quick reactions.
Attackers are using GenAI to refine these techniques, making them even more effective. Staying informed about the latest strategies and elements of attacks is essential for protecting yourself and your organization.
How to spot email (and other) phishing scams
In the era of GenAI-powered phishing, the ability to identify phishing attempts has never been more critical. Phishing scams vary in sophistication, but they often display recognizable “warning signs,” such as:
- Poor grammar and spelling: In the past, phishing emails often contained misspellings or awkward phrasing. However, with GenAI, attackers can now craft more polished, grammatically correct copy, making it hard to spot errors. This shift means you should look for other inconsistencies in addition to spelling or grammar mistakes.
- Generic greetings: Phishing messages may address recipients with vague terms (e.g., “Dear Valued Customer”) instead of using their full name or account-specific details that legitimate organizations would use. However, GenAI enables attackers to personalize these greetings using publicly available information, making them seem more credible. You should still be suspicious if the greeting feels impersonal or lacks specific account details.
- Inconsistent domains: Attackers often use email addresses and domain names that closely mimic legitimate sources. For example, an email might come from [email protected] instead of [email protected]. Always inspect email addresses and hover over links before clicking to ensure they lead to the correct, secure domain.
- Suspicious attachments: Attachments in phishing emails can carry malware disguised as legitimate files. Common file types include .zip, .doc, .exe, and .pdf. Be extra cautious with unexpected attachments, and avoid opening them unless verified with the sender, as they remain a common phishing attack vector.
- Requests for sensitive information: Legitimate companies will never ask for sensitive information via email, so if an email requests such details, it is almost certainly a phishing attempt. These emails often contain links to fraudulent websites that look like the real thing but are designed to capture personal data.
- Urgent requests: Phishing attacks often create a sense of urgency, pressuring recipients to take immediate action or risk the consequences, such as account suspension. This is a common panic-inducing tactic that leads to impulsive clicks or sharing sensitive data.
Common types of phishing attacks
Phishing scams can take many forms, from simple to quite advanced, but many rely on familiar tactics to trick victims. Below are some of the most prevalent types of phishing attacks you should be aware of:
- Email phishing: One of the most widespread and age-old forms of phishing, attackers commonly use email to impersonate trusted organizations or individuals to con recipients into sharing sensitive data, clicking on malicious links, or downloading attachments.
- AI-powered vishing (voice phishing): Vishing involves attackers using phone calls to impersonate trusted individuals. With AI-powered voice replication, these calls sound highly realistic, allowing attackers to imitate public figures or corporate leaders, making it easier to defraud even savvy victims.
- Deepfake phishing: In this emerging threat, attackers use AI-generated deepfake technology to manipulate videos, images, or audio to impersonate known individuals, making phishing attacks even more convincing.
- Smishing (SMS phishing): Attackers use text messages that contain malicious links or phone numbers designated to harvest personal information or infect devices with malware.
- Spear phishing: A more targeted version of phishing, spear phishing attacks involves researching and tailoring emails to a specific individual or organization.
- Adversary-in-the-middle (AiTM) phishing: Attackers intercept and manipulate communication between two parties in real time. They can alter messages, redirect victims to malicious websites, and collect data without detection.
- Fake login pages: Attackers create websites that closely resemble legitimate login pages of popular brands or services to get users to enter their credentials. LLMs have made this significantly easier.
Here are some specific phishing scams associated with these types of attacks:
- Invoice scams: Attackers send emails that appear to be invoices from known companies or service providers, claiming you owe money for a product or service. The goal is to get you to click on a link to pay the invoice, which leads to a phishing site designed to steal your payment information.
- Email account upgrade or deactivation scams: These emails warn that your email account is about to be deactivated or requires an upgrade. They typically include a link to “verify” your information, which leads to a fake login page designed to capture your credentials.
- Amazon gift card scams: This scam involves messages that appear to come from Amazon claiming you’ve won a gift card and providing a link to claim your prize, once again leading to a phishing site that steals your Amazon login credentials.
Based on analysis of billions of phishing transactions blocked by the Zscaler cloud, Zscaler ThreatLabz researchers have identified several scams that are on the rise, including:
- QR code scams: Attackers are increasingly using QR codes to dupe victims into scanning them. A phishing email may claim to offer a discount or prompt a security check but uses a QR code that directs the victim to a phishing site designed to install malware or steal credentials.
- Typosquatting scams: Attackers proliferate phishing campaigns through typosquatting, which entails registering domains with misspelled versions of popular websites or brands to capitalize on user errors. ThreatLabz recently examined typosquatting in depth—read the findings in the blog post, Phishing Via Typosquatting and Brand Impersonation: Trends and Tactics.
- Recruitment scams: Cybercriminals impersonate external recruiters or members of HR departments claiming the need to verify employment details, complete training, or review a new policy. The goal is to trick the recipient into either clicking a malicious link or sharing personal information.
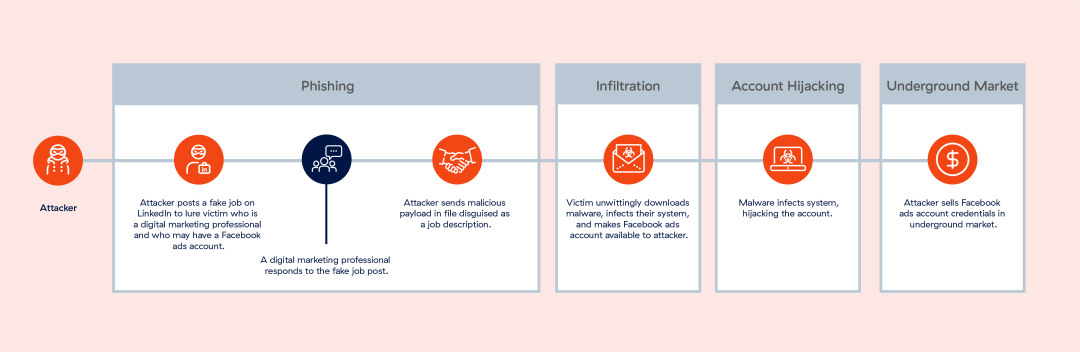
Impact of AI on phishing
AI in cybersecurity is increasing in prevalence, but it’s likewise taking on a pivotal role in the cyberthreat landscape, with its capabilities now embedded in various stages of attack execution. From AI-generated voice phishing attempts to the automation of phishing page creation, AI’s reach in the phishing world is especially apparent, and recent examples show just that:
- Vishing with AI-generated voice cloning:
- In a recent attempted vishing attack, AI-powered voice cloning technology was used to impersonate Zscaler’s CEO.
An attacker contacts a Zscaler employee via WhatsApp using AI-generated voice cloning to mimic the CEO’s voice. - The attacker quickly hung up after establishing contact to avoid prolonged conversation and reduce the risk of being exposed.
Immediately afterward, the attacker sent a follow-up text message, posing as the CEO, and claimed they had “poor network coverage.” - In the message, the attacker asked the employee to purchase gift cards for a specific amount.
- Finding the request suspicious, the employee reported it to the security team. Upon investigation, ThreatLabz researchers discovered it was part of a larger campaign targeting several tech companies.
- In a recent attempted vishing attack, AI-powered voice cloning technology was used to impersonate Zscaler’s CEO.
This example highlights how AI is being weaponized to enhance social engineering techniques like vishing, adding a layer of authenticity to fraudulent communications.
Creating a phishing login page in less than 10 ChatGPT queries: Generative AI models, such as LLMs (large language models) like ChatGPT, have made it significantly easier for even notice cybercriminals to carry out sophisticated phishing attacks, as demonstrated in this example from ThreatLabz.
With less than 10 prompts in ChatGPT, it’s possible to generate a convincing phishing login page designed to steal employee credential: Starting with a simple prompt to “create an HTML login page,” followed a short series of prompts to improve the page, ChatGPT rendered the following realistic Microsoft phishing login page:
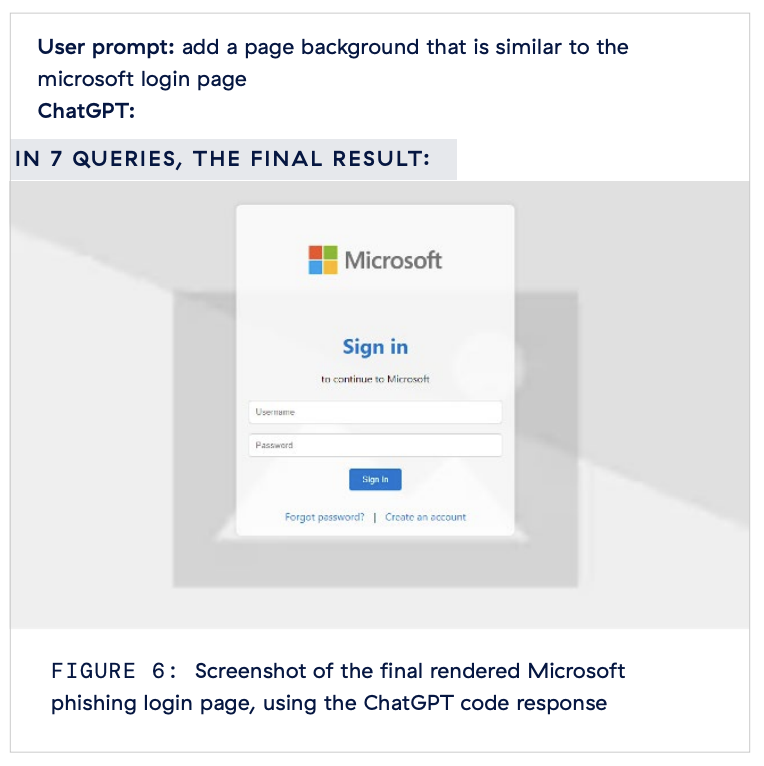
This is a stark example of how AI is lowering the barrier for cybercriminals to execute phishing attacks with less effort and technical knowledge.
Strategies to prevent and mitigate phishing threats
Defending against phishing attacks requires a combination of vigilance, user education, and advanced security measures.
Here are some phishing prevention tips, best practices, and essential means of protection:
- Be cautious of unsolicited emails: Verify the legitimacy of unexpected emails by contacting the sender directly using trusted contact information, not the contact details provided in the email.
- Double-check URLs and emails: Always verify the legitimacy of email addresses, checking for small differences in spelling or domain names, and hover over links to inspect actual URLs.
- Enable phishing-resistant multifactor authentication (MFA): MFA adds a critical layer of security by requiring additional verification beyond passwords. However, it’s important to remember that attackers may target MFA users through methods like voice phishing or SMS—MFA must be combined with other security layers to mitigate these risks.
- Implement email scanning and filters: Use a cloud-based email scanning solution that filters incoming emails for suspicious content, attachments, and links in real time.
- Inspect encrypted traffic: With almost 86% of attacks utilizing encrypted channels, it’s essential to inspect encrypted traffic. Encrypted phishing attacks increased by almost 14% over 2023, driven by AI and phishing-as-a-service offerings. Ensure your security tools can inspect all traffic—encrypted or not—to thwart these threats early in the attack chain.
- Patch regularly: Keep all systems, applications, and security tools up to date by applying the latest patches, ultimately minimizing vulnerabilities and strengthening your defenses against potential phishing attacks.
- Adopt a zero trust architecture: Implementing a zero trust architecture limits your attack surface and reduces lateral movement within your network. Employing zero trust segmentation, enforcing least-privilege access policies, and continuously monitoring traffic to detect and respond to threats significantly lowers the risk of a breach caused by phishing.
- Use advanced threat protection: In addition to keeping antivirus software updated, use advanced threat protection solutions like AI-powered sandboxes and browser isolation tools to analyze suspicious files and prevent unknown malware from executing on devices. Stay on top of AI-driven security trends as well.
- Implement URL filtering: Enforce policy-based controls that restrict access to high-risk web content categories, including newly registered domains, reducing the chance of users encountering phishing websites.
- Use threat intelligence: Use real-time threat intelligence to keep track of phishing threats and make it easier to find them. Stay up-to-date on the latest signs of compromise (IOCs) and phishing tactics, techniques, and procedures (TTPs) to stop attacks better.
- Promote awareness and reporting: Implement employee training to help them recognize phishing attempts and report suspicious activity. Establish a playbook for investigating and addressing phishing incidents, and report serious threats to relevant authorities.
- Use Zscaler Safe Link Checker for free: Unsure about legitimacy of a URL? Enhance your protection against phishing by using the Zscaler Safe Link Checker, which allows you to check the safety of any link before clicking on it. Simply copy the link and paste it into the tool to analyze it for signs of malicious activity.
By combining these strategies, you can significantly reduce the risk of phishing attacks and strengthen protections against current and emerging threats.
Conclusion: Prioritize phishing awareness and zero trust
Phishing is no longer a static or predictable threat. As attacks grow more sophisticated and effective thanks to generative AI tools and cybercrime services, protecting against phishing attacks requires constant vigilance, adaptation, and a robust, multi-layered security strategy.
Staying proactive is key. This means implementing zero trust security solutions alongside continuous education on how to recognize and respond to phishing attacks. By fostering a culture of caution and ensuring that security measures are up to date and up to the task of fighting AI-powered threats, organizations can significantly reduce the risk of succumbing to even the most advanced phishing scams.
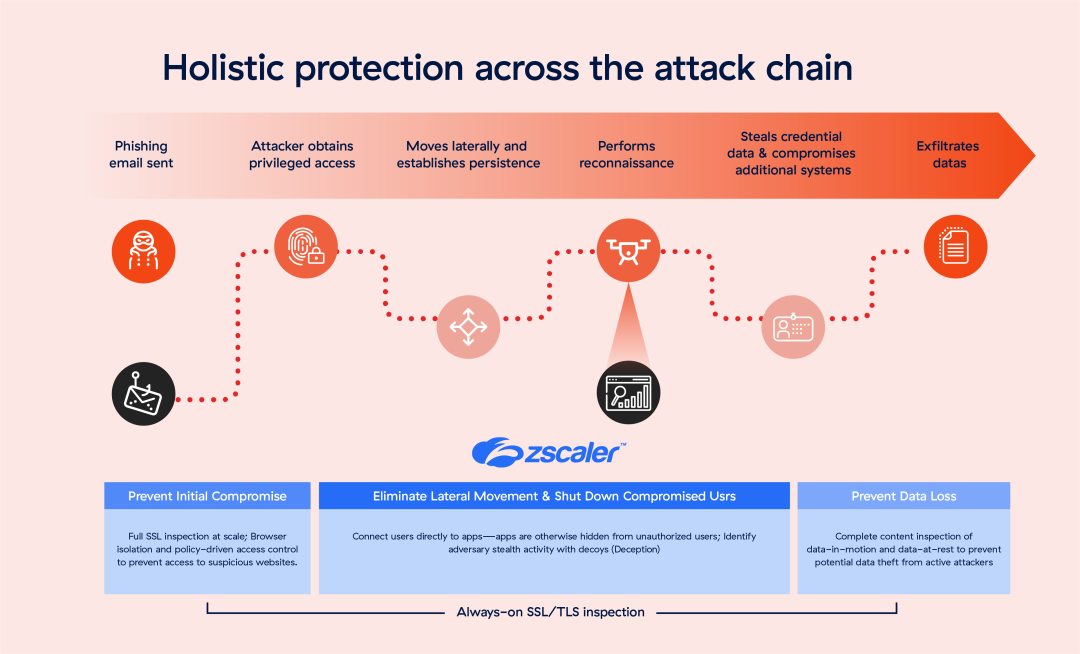
The Zscaler Zero Trust Exchange provides a comprehensive defense against phishing, rooted in a zero trust architecture designed to:
Prevent initial compromise: Through full TLS/SSL inspection at scale, browser isolation, and policy-driven access controls, Zscaler helps block access to suspicious websites before users can fall victim to phishing schemes.
Eliminate lateral movement: Zscaler’s zero trust approach connects users directly to applications, not the internet, minimizing the potential impact of compromised accounts. By segmenting access, Zscaler effectively reduces the blast radius in the event of a breach and removes the risk of widespread damage.
Shut down compromised users and insider threats: Inline inspection prevents private application exploits, while integrated deception helps detect and neutralize even the most sophisticated attackers.
Stop data loss: Zscaler inspects both data-in-motion and data-at-rest to prevent theft by active attackers, ensuring that sensitive information remains secure.
For a deeper dive into the latest phishing research, emerging tactics, and proven security strategies to combat phishing, download the Zscaler ThreatLabz 2024 Phishing Report.
Cet article a-t-il été utile ?
Clause de non-responsabilité : Cet article de blog a été créé par Zscaler à des fins d’information uniquement et est fourni « en l’état » sans aucune garantie d’exactitude, d’exhaustivité ou de fiabilité. Zscaler n’assume aucune responsabilité pour toute erreur ou omission ou pour toute action prise sur la base des informations fournies. Tous les sites Web ou ressources de tiers liés à cet artcile de blog sont fournis pour des raisons de commodité uniquement, et Zscaler n’est pas responsable de leur contenu ni de leurs pratiques. Tout le contenu peut être modifié sans préavis. En accédant à ce blog, vous acceptez ces conditions et reconnaissez qu’il est de votre responsabilité de vérifier et d’utiliser les informations en fonction de vos besoins.
Recevez les dernières mises à jour du blog de Zscaler dans votre boîte de réception
En envoyant le formulaire, vous acceptez notre politique de confidentialité.



