If you read the title of this blog and thought, “Great…another industry blog talking about zero trust,” I totally get it. But I promise you, this is different.
Earlier this year, Cybersecurity Insiders surveyed more than 315 IT and cybersecurity professionals from across the globe to develop the 2019 Zero Trust Adoption Report. Why is that a big deal? Well, this illuminating survey and supporting report are the first of their kind—providing an investigation into whether security teams were truly making investments in a zero trust model or if zero trust was just another industry buzzword created by vendors.
The findings from the report prove that zero trust is indeed important to security teams, as three of the top five security priorities for the next two years all revolve around zero trust. The list includes identity and privileged account management, anomalous activity detection and response, and securing access from unmanaged devices—all of which are key pillars of the model.
In addition to indicating a high level of interest among enterprises, the report highlights the factors driving adoption trends and identifies the top use cases for zero trust technologies.
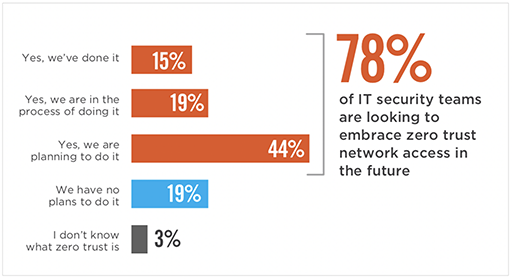
Some findings from the survey of 315 IT and cybersecurity professionals include:
- 78 percent are looking to adopt zero trust; 15 percent already have
- 47 percent admit they lack confidence in their existing technology
- 59 percent say they will adopt a ZTNA service within the next 12 months
- 62 percent said the biggest driver is the need to secure access to apps across hybrid environments
- 37 percent said their No. 1 use case is securing access to multicloud environments
Zero trust isn’t a fad or another technology buzzword. It’s a security model that is capturing the minds (and budgets) of executives around the world as the ideal way to operate in an increasingly cloud- and mobile-first world.
Anyone exploring the idea of adopting a zero trust model, or those already transitioning to one, should take a close look at this report. It provides key insights into what your peers (and competitors) are doing with their security and, perhaps, some guidance on what you should be doing with yours.
To explore more of Cybersecurity Insiders’ findings, download the full report.
View an infographic of the report's findings here.
Christopher Hines is the head of product marketing for Zscaler Private Access and Z App.






